Keycloak Configuration Authentication . Finally, i'll show you how to configure keycloak to make it work with our web application and services. In this first part, we will focus on one of the most crucial steps in securing an application: The starting point in our process to. Configuring keycloak using oauth2 and openid connect (oidc). Keycloak can be configured to delegate authentication to one or more idps. Then, we will detail the installation and initial configuration of keycloak. For simplicity, the client_credentials grant type is used here,. How to configure keycloak to manage authentication and authorization for web applications or services. Social login via facebook or google is an example of identity provider federation. Keycloak can authenticate your client application in different ways. Creating realms, security roles, users and passwords.
from www.janua.fr
Then, we will detail the installation and initial configuration of keycloak. Finally, i'll show you how to configure keycloak to make it work with our web application and services. In this first part, we will focus on one of the most crucial steps in securing an application: Keycloak can be configured to delegate authentication to one or more idps. Configuring keycloak using oauth2 and openid connect (oidc). The starting point in our process to. For simplicity, the client_credentials grant type is used here,. Creating realms, security roles, users and passwords. How to configure keycloak to manage authentication and authorization for web applications or services. Keycloak can authenticate your client application in different ways.
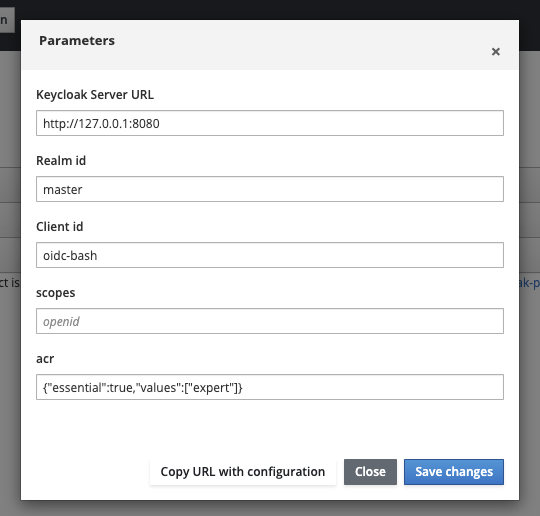
Authentication Context Class Reference and Level Of Authentication with
Keycloak Configuration Authentication Finally, i'll show you how to configure keycloak to make it work with our web application and services. Keycloak can be configured to delegate authentication to one or more idps. Social login via facebook or google is an example of identity provider federation. Configuring keycloak using oauth2 and openid connect (oidc). How to configure keycloak to manage authentication and authorization for web applications or services. For simplicity, the client_credentials grant type is used here,. Then, we will detail the installation and initial configuration of keycloak. Keycloak can authenticate your client application in different ways. In this first part, we will focus on one of the most crucial steps in securing an application: The starting point in our process to. Finally, i'll show you how to configure keycloak to make it work with our web application and services. Creating realms, security roles, users and passwords.
From community.ibm.com
Extending Keycloak's authentication capabilities by integrating with Keycloak Configuration Authentication Creating realms, security roles, users and passwords. The starting point in our process to. How to configure keycloak to manage authentication and authorization for web applications or services. Then, we will detail the installation and initial configuration of keycloak. Finally, i'll show you how to configure keycloak to make it work with our web application and services. Keycloak can be. Keycloak Configuration Authentication.
From www.olvid.io
Olvid Keycloak Configuration Guide Configuration of an External IdP Keycloak Configuration Authentication The starting point in our process to. Keycloak can authenticate your client application in different ways. Creating realms, security roles, users and passwords. Finally, i'll show you how to configure keycloak to make it work with our web application and services. For simplicity, the client_credentials grant type is used here,. Keycloak can be configured to delegate authentication to one or. Keycloak Configuration Authentication.
From www.thomasvitale.com
Keycloak Basic Configuration for Authentication and Authorization Keycloak Configuration Authentication The starting point in our process to. How to configure keycloak to manage authentication and authorization for web applications or services. In this first part, we will focus on one of the most crucial steps in securing an application: Creating realms, security roles, users and passwords. Social login via facebook or google is an example of identity provider federation. Configuring. Keycloak Configuration Authentication.
From docs.dominodatalab.com
Keycloak Upstream IDP Trust Keycloak Configuration Authentication For simplicity, the client_credentials grant type is used here,. Creating realms, security roles, users and passwords. Finally, i'll show you how to configure keycloak to make it work with our web application and services. Configuring keycloak using oauth2 and openid connect (oidc). Then, we will detail the installation and initial configuration of keycloak. The starting point in our process to.. Keycloak Configuration Authentication.
From www.typingdna.com
Add twofactor authentication to your web app using Keycloak & Node.js Keycloak Configuration Authentication How to configure keycloak to manage authentication and authorization for web applications or services. Configuring keycloak using oauth2 and openid connect (oidc). Then, we will detail the installation and initial configuration of keycloak. In this first part, we will focus on one of the most crucial steps in securing an application: Creating realms, security roles, users and passwords. Finally, i'll. Keycloak Configuration Authentication.
From baptistout.net
Passwordless authentication with Authn, Keycloak and Istio Keycloak Configuration Authentication Configuring keycloak using oauth2 and openid connect (oidc). In this first part, we will focus on one of the most crucial steps in securing an application: Creating realms, security roles, users and passwords. Social login via facebook or google is an example of identity provider federation. For simplicity, the client_credentials grant type is used here,. The starting point in our. Keycloak Configuration Authentication.
From www.thomasvitale.com
Keycloak Authentication Flows, SSO Protocols and Client Configuration Keycloak Configuration Authentication For simplicity, the client_credentials grant type is used here,. Social login via facebook or google is an example of identity provider federation. Then, we will detail the installation and initial configuration of keycloak. How to configure keycloak to manage authentication and authorization for web applications or services. In this first part, we will focus on one of the most crucial. Keycloak Configuration Authentication.
From younite.us
Configuring SSO and OAuth with Keycloak Keycloak Configuration Authentication Social login via facebook or google is an example of identity provider federation. Then, we will detail the installation and initial configuration of keycloak. How to configure keycloak to manage authentication and authorization for web applications or services. Keycloak can authenticate your client application in different ways. The starting point in our process to. Keycloak can be configured to delegate. Keycloak Configuration Authentication.
From docs.getunleash.io
How to set up Keycloak and Unleash to sync user groups Unleash Keycloak Configuration Authentication How to configure keycloak to manage authentication and authorization for web applications or services. Social login via facebook or google is an example of identity provider federation. Configuring keycloak using oauth2 and openid connect (oidc). The starting point in our process to. Finally, i'll show you how to configure keycloak to make it work with our web application and services.. Keycloak Configuration Authentication.
From blog.tharinduhasthika.com
Authenticating Jitsi Meetings using Keycloak Keycloak Configuration Authentication Creating realms, security roles, users and passwords. Keycloak can authenticate your client application in different ways. For simplicity, the client_credentials grant type is used here,. Social login via facebook or google is an example of identity provider federation. The starting point in our process to. Then, we will detail the installation and initial configuration of keycloak. In this first part,. Keycloak Configuration Authentication.
From sis-cc.gitlab.io
Keycloak configuration .Stat Suite documentation Keycloak Configuration Authentication Keycloak can be configured to delegate authentication to one or more idps. How to configure keycloak to manage authentication and authorization for web applications or services. Then, we will detail the installation and initial configuration of keycloak. In this first part, we will focus on one of the most crucial steps in securing an application: Finally, i'll show you how. Keycloak Configuration Authentication.
From www.thomasvitale.com
Keycloak Basic Configuration for Authentication and Authorization Keycloak Configuration Authentication The starting point in our process to. In this first part, we will focus on one of the most crucial steps in securing an application: Keycloak can authenticate your client application in different ways. Finally, i'll show you how to configure keycloak to make it work with our web application and services. How to configure keycloak to manage authentication and. Keycloak Configuration Authentication.
From www.thomasvitale.com
Keycloak Basic Configuration for Authentication and Authorization Keycloak Configuration Authentication Keycloak can be configured to delegate authentication to one or more idps. Configuring keycloak using oauth2 and openid connect (oidc). Social login via facebook or google is an example of identity provider federation. In this first part, we will focus on one of the most crucial steps in securing an application: Creating realms, security roles, users and passwords. For simplicity,. Keycloak Configuration Authentication.
From developers.redhat.com
Keycloak Core concepts of open source identity and access management Keycloak Configuration Authentication Finally, i'll show you how to configure keycloak to make it work with our web application and services. Social login via facebook or google is an example of identity provider federation. Then, we will detail the installation and initial configuration of keycloak. For simplicity, the client_credentials grant type is used here,. Configuring keycloak using oauth2 and openid connect (oidc). Keycloak. Keycloak Configuration Authentication.
From admin.dominodatalab.com
keycloak 1 4 2 additional saml settings Keycloak Configuration Authentication The starting point in our process to. How to configure keycloak to manage authentication and authorization for web applications or services. Finally, i'll show you how to configure keycloak to make it work with our web application and services. Then, we will detail the installation and initial configuration of keycloak. Creating realms, security roles, users and passwords. For simplicity, the. Keycloak Configuration Authentication.
From www.thomasvitale.com
Keycloak Basic Configuration for Authentication and Authorization Keycloak Configuration Authentication For simplicity, the client_credentials grant type is used here,. In this first part, we will focus on one of the most crucial steps in securing an application: Social login via facebook or google is an example of identity provider federation. Keycloak can be configured to delegate authentication to one or more idps. Creating realms, security roles, users and passwords. How. Keycloak Configuration Authentication.
From ultimatesecurity.pro
Keycloak TwoFactor Authentication · Ultimate Security Professional Blog Keycloak Configuration Authentication Then, we will detail the installation and initial configuration of keycloak. For simplicity, the client_credentials grant type is used here,. In this first part, we will focus on one of the most crucial steps in securing an application: Configuring keycloak using oauth2 and openid connect (oidc). Keycloak can be configured to delegate authentication to one or more idps. Social login. Keycloak Configuration Authentication.
From scalac.io
User Authentication with Keycloak Part 1 React frontend Keycloak Configuration Authentication Keycloak can be configured to delegate authentication to one or more idps. Then, we will detail the installation and initial configuration of keycloak. Social login via facebook or google is an example of identity provider federation. Configuring keycloak using oauth2 and openid connect (oidc). The starting point in our process to. Finally, i'll show you how to configure keycloak to. Keycloak Configuration Authentication.
From help.hcltechsw.com
Sample KeyCloak configuration as an OIDC provider for Domino Keycloak Configuration Authentication Creating realms, security roles, users and passwords. The starting point in our process to. Then, we will detail the installation and initial configuration of keycloak. Configuring keycloak using oauth2 and openid connect (oidc). How to configure keycloak to manage authentication and authorization for web applications or services. Social login via facebook or google is an example of identity provider federation.. Keycloak Configuration Authentication.
From www.typingdna.com
Add twofactor authentication to your web app using Keycloak & Node.js Keycloak Configuration Authentication For simplicity, the client_credentials grant type is used here,. Keycloak can authenticate your client application in different ways. How to configure keycloak to manage authentication and authorization for web applications or services. Finally, i'll show you how to configure keycloak to make it work with our web application and services. The starting point in our process to. In this first. Keycloak Configuration Authentication.
From www.thomasvitale.com
Keycloak Authentication Flows, SSO Protocols and Client Configuration Keycloak Configuration Authentication Keycloak can authenticate your client application in different ways. Finally, i'll show you how to configure keycloak to make it work with our web application and services. Keycloak can be configured to delegate authentication to one or more idps. Then, we will detail the installation and initial configuration of keycloak. Creating realms, security roles, users and passwords. For simplicity, the. Keycloak Configuration Authentication.
From www.springcloud.io
Unified authentication authorization platform keycloak Introduction Keycloak Configuration Authentication Finally, i'll show you how to configure keycloak to make it work with our web application and services. How to configure keycloak to manage authentication and authorization for web applications or services. Configuring keycloak using oauth2 and openid connect (oidc). Keycloak can authenticate your client application in different ways. Social login via facebook or google is an example of identity. Keycloak Configuration Authentication.
From www.thomasvitale.com
Keycloak Basic Configuration for Authentication and Authorization Keycloak Configuration Authentication Keycloak can be configured to delegate authentication to one or more idps. Social login via facebook or google is an example of identity provider federation. Configuring keycloak using oauth2 and openid connect (oidc). In this first part, we will focus on one of the most crucial steps in securing an application: Keycloak can authenticate your client application in different ways.. Keycloak Configuration Authentication.
From ahus1.github.io
Configuring realms Keycloak Docs Keycloak Configuration Authentication The starting point in our process to. Configuring keycloak using oauth2 and openid connect (oidc). Finally, i'll show you how to configure keycloak to make it work with our web application and services. Then, we will detail the installation and initial configuration of keycloak. How to configure keycloak to manage authentication and authorization for web applications or services. For simplicity,. Keycloak Configuration Authentication.
From ultimatesecurity.pro
Keycloak TwoFactor Authentication · Ultimate Security Professional Blog Keycloak Configuration Authentication Keycloak can be configured to delegate authentication to one or more idps. The starting point in our process to. Then, we will detail the installation and initial configuration of keycloak. How to configure keycloak to manage authentication and authorization for web applications or services. Creating realms, security roles, users and passwords. Social login via facebook or google is an example. Keycloak Configuration Authentication.
From andrevianna-1662831931436.hashnode.dev
Understanding the Powerful Keycloak Tool Keycloak Configuration Authentication For simplicity, the client_credentials grant type is used here,. Keycloak can be configured to delegate authentication to one or more idps. In this first part, we will focus on one of the most crucial steps in securing an application: Configuring keycloak using oauth2 and openid connect (oidc). The starting point in our process to. Social login via facebook or google. Keycloak Configuration Authentication.
From documentation.censhare.com
Configure Keycloak with SAML Keycloak Configuration Authentication Finally, i'll show you how to configure keycloak to make it work with our web application and services. How to configure keycloak to manage authentication and authorization for web applications or services. The starting point in our process to. Keycloak can be configured to delegate authentication to one or more idps. For simplicity, the client_credentials grant type is used here,.. Keycloak Configuration Authentication.
From walkingtree.tech
Keycloak Identity Access Management Solutions WalkingTree Technologies Keycloak Configuration Authentication Social login via facebook or google is an example of identity provider federation. Then, we will detail the installation and initial configuration of keycloak. Finally, i'll show you how to configure keycloak to make it work with our web application and services. Creating realms, security roles, users and passwords. The starting point in our process to. Keycloak can be configured. Keycloak Configuration Authentication.
From docs.openfaas.com
Keycloak OpenFaaS Keycloak Configuration Authentication Finally, i'll show you how to configure keycloak to make it work with our web application and services. Keycloak can authenticate your client application in different ways. Creating realms, security roles, users and passwords. Keycloak can be configured to delegate authentication to one or more idps. Configuring keycloak using oauth2 and openid connect (oidc). Social login via facebook or google. Keycloak Configuration Authentication.
From docs.openfaas.com
Keycloak OpenFaaS Keycloak Configuration Authentication For simplicity, the client_credentials grant type is used here,. How to configure keycloak to manage authentication and authorization for web applications or services. Then, we will detail the installation and initial configuration of keycloak. Social login via facebook or google is an example of identity provider federation. The starting point in our process to. Finally, i'll show you how to. Keycloak Configuration Authentication.
From walkingtree.tech
Keycloak and MultiFactor Authentication (MFA) Strengthening Security Keycloak Configuration Authentication In this first part, we will focus on one of the most crucial steps in securing an application: For simplicity, the client_credentials grant type is used here,. Keycloak can be configured to delegate authentication to one or more idps. Social login via facebook or google is an example of identity provider federation. Keycloak can authenticate your client application in different. Keycloak Configuration Authentication.
From github.com
GitHub 5stones/keycloakemailotp A Keycloak Authentication step Keycloak Configuration Authentication Finally, i'll show you how to configure keycloak to make it work with our web application and services. How to configure keycloak to manage authentication and authorization for web applications or services. In this first part, we will focus on one of the most crucial steps in securing an application: Creating realms, security roles, users and passwords. The starting point. Keycloak Configuration Authentication.
From www.janua.fr
Authentication Context Class Reference and Level Of Authentication with Keycloak Configuration Authentication Social login via facebook or google is an example of identity provider federation. Keycloak can authenticate your client application in different ways. Configuring keycloak using oauth2 and openid connect (oidc). The starting point in our process to. Creating realms, security roles, users and passwords. How to configure keycloak to manage authentication and authorization for web applications or services. Keycloak can. Keycloak Configuration Authentication.
From www.thomasvitale.com
Keycloak Authentication Flows, SSO Protocols and Client Configuration Keycloak Configuration Authentication Keycloak can be configured to delegate authentication to one or more idps. Creating realms, security roles, users and passwords. How to configure keycloak to manage authentication and authorization for web applications or services. Configuring keycloak using oauth2 and openid connect (oidc). Keycloak can authenticate your client application in different ways. For simplicity, the client_credentials grant type is used here,. Social. Keycloak Configuration Authentication.
From www.thomasvitale.com
Keycloak Basic Configuration for Authentication and Authorization Keycloak Configuration Authentication Social login via facebook or google is an example of identity provider federation. Creating realms, security roles, users and passwords. How to configure keycloak to manage authentication and authorization for web applications or services. The starting point in our process to. Finally, i'll show you how to configure keycloak to make it work with our web application and services. In. Keycloak Configuration Authentication.