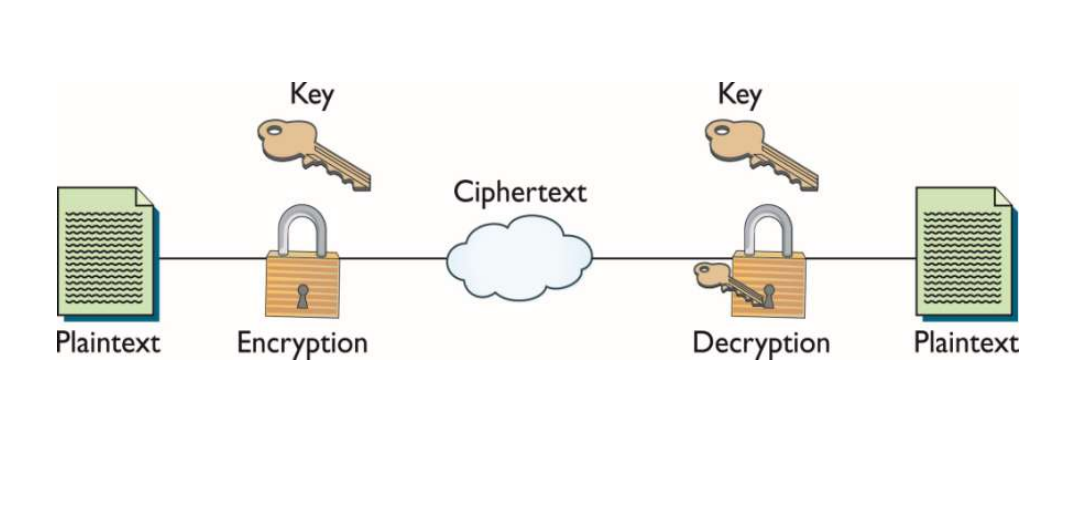
System.security.cryptography Documentation . modern examples of symmetric authenticated encryption of a string, introduction to symmetric and asymmetric encryption,. we can access the.net library of cryptographic algorithms through the system.security.cryptography namespace. provides cryptographic services, including secure encoding and decoding of data, as well as many other operations, such as hashing,. information security is composed of 4 parts: Ensure a document is not altered. the documentation for both the aesmanaged and aescryptoserviceprovider class provides elaborate examples. the system.security.cryptography namespace contains support for the most common symmetric (des, 3des, rc2, rijndael), asymmetric (rsa,.
from www.nepalshovit.com.np
the system.security.cryptography namespace contains support for the most common symmetric (des, 3des, rc2, rijndael), asymmetric (rsa,. we can access the.net library of cryptographic algorithms through the system.security.cryptography namespace. provides cryptographic services, including secure encoding and decoding of data, as well as many other operations, such as hashing,. the documentation for both the aesmanaged and aescryptoserviceprovider class provides elaborate examples. Ensure a document is not altered. information security is composed of 4 parts: modern examples of symmetric authenticated encryption of a string, introduction to symmetric and asymmetric encryption,.
CryptographyIntroduction 5OBIT
System.security.cryptography Documentation modern examples of symmetric authenticated encryption of a string, introduction to symmetric and asymmetric encryption,. Ensure a document is not altered. the system.security.cryptography namespace contains support for the most common symmetric (des, 3des, rc2, rijndael), asymmetric (rsa,. provides cryptographic services, including secure encoding and decoding of data, as well as many other operations, such as hashing,. modern examples of symmetric authenticated encryption of a string, introduction to symmetric and asymmetric encryption,. information security is composed of 4 parts: we can access the.net library of cryptographic algorithms through the system.security.cryptography namespace. the documentation for both the aesmanaged and aescryptoserviceprovider class provides elaborate examples.
From www.researchgate.net
(PDF) CRYPTOGRAPHY BASED SECURITY SYSTEM FOR VARIOUS FILE FORMATS System.security.cryptography Documentation modern examples of symmetric authenticated encryption of a string, introduction to symmetric and asymmetric encryption,. we can access the.net library of cryptographic algorithms through the system.security.cryptography namespace. Ensure a document is not altered. the documentation for both the aesmanaged and aescryptoserviceprovider class provides elaborate examples. information security is composed of 4 parts: provides cryptographic services,. System.security.cryptography Documentation.
From wiki.st.com
SecurityIntroduction to Cryptography stm32mcu System.security.cryptography Documentation the documentation for both the aesmanaged and aescryptoserviceprovider class provides elaborate examples. information security is composed of 4 parts: Ensure a document is not altered. provides cryptographic services, including secure encoding and decoding of data, as well as many other operations, such as hashing,. modern examples of symmetric authenticated encryption of a string, introduction to symmetric. System.security.cryptography Documentation.
From www.youtube.com
Does system.security.cryptography.sha1 use OpenSSL library's System.security.cryptography Documentation we can access the.net library of cryptographic algorithms through the system.security.cryptography namespace. provides cryptographic services, including secure encoding and decoding of data, as well as many other operations, such as hashing,. information security is composed of 4 parts: modern examples of symmetric authenticated encryption of a string, introduction to symmetric and asymmetric encryption,. the system.security.cryptography. System.security.cryptography Documentation.
From www.youtube.com
Principles of Security Network Security Cryptography and Network System.security.cryptography Documentation the documentation for both the aesmanaged and aescryptoserviceprovider class provides elaborate examples. Ensure a document is not altered. the system.security.cryptography namespace contains support for the most common symmetric (des, 3des, rc2, rijndael), asymmetric (rsa,. information security is composed of 4 parts: provides cryptographic services, including secure encoding and decoding of data, as well as many other. System.security.cryptography Documentation.
From docs.rockylinux.org
Lab 9 Cryptography Documentation System.security.cryptography Documentation we can access the.net library of cryptographic algorithms through the system.security.cryptography namespace. modern examples of symmetric authenticated encryption of a string, introduction to symmetric and asymmetric encryption,. provides cryptographic services, including secure encoding and decoding of data, as well as many other operations, such as hashing,. Ensure a document is not altered. the documentation for both. System.security.cryptography Documentation.
From www.scribd.com
Visual CryptographyBased Secure URL Sharing System Design and System.security.cryptography Documentation Ensure a document is not altered. information security is composed of 4 parts: we can access the.net library of cryptographic algorithms through the system.security.cryptography namespace. the system.security.cryptography namespace contains support for the most common symmetric (des, 3des, rc2, rijndael), asymmetric (rsa,. provides cryptographic services, including secure encoding and decoding of data, as well as many other. System.security.cryptography Documentation.
From www.scribd.com
CSPC Security Documentation PDF Transport Layer Security Public System.security.cryptography Documentation the documentation for both the aesmanaged and aescryptoserviceprovider class provides elaborate examples. the system.security.cryptography namespace contains support for the most common symmetric (des, 3des, rc2, rijndael), asymmetric (rsa,. Ensure a document is not altered. we can access the.net library of cryptographic algorithms through the system.security.cryptography namespace. provides cryptographic services, including secure encoding and decoding of data,. System.security.cryptography Documentation.
From www.commsp.ee.ic.ac.uk
On cryptography and websecurity Shanxiang Lyu System.security.cryptography Documentation we can access the.net library of cryptographic algorithms through the system.security.cryptography namespace. the documentation for both the aesmanaged and aescryptoserviceprovider class provides elaborate examples. provides cryptographic services, including secure encoding and decoding of data, as well as many other operations, such as hashing,. modern examples of symmetric authenticated encryption of a string, introduction to symmetric and. System.security.cryptography Documentation.
From triumphias.com
Cryptography & its Uses TriumphIAS System.security.cryptography Documentation the documentation for both the aesmanaged and aescryptoserviceprovider class provides elaborate examples. information security is composed of 4 parts: provides cryptographic services, including secure encoding and decoding of data, as well as many other operations, such as hashing,. modern examples of symmetric authenticated encryption of a string, introduction to symmetric and asymmetric encryption,. we can. System.security.cryptography Documentation.
From github.com
System.Security.Cryptography documentation flaw · Issue 9930 · System.security.cryptography Documentation information security is composed of 4 parts: the documentation for both the aesmanaged and aescryptoserviceprovider class provides elaborate examples. modern examples of symmetric authenticated encryption of a string, introduction to symmetric and asymmetric encryption,. we can access the.net library of cryptographic algorithms through the system.security.cryptography namespace. the system.security.cryptography namespace contains support for the most common. System.security.cryptography Documentation.
From people.eecs.berkeley.edu
Public Key Cryptography System.security.cryptography Documentation Ensure a document is not altered. information security is composed of 4 parts: the system.security.cryptography namespace contains support for the most common symmetric (des, 3des, rc2, rijndael), asymmetric (rsa,. the documentation for both the aesmanaged and aescryptoserviceprovider class provides elaborate examples. we can access the.net library of cryptographic algorithms through the system.security.cryptography namespace. provides cryptographic. System.security.cryptography Documentation.
From www.thecrazyprogrammer.com
Types of Cryptography System.security.cryptography Documentation information security is composed of 4 parts: the documentation for both the aesmanaged and aescryptoserviceprovider class provides elaborate examples. Ensure a document is not altered. the system.security.cryptography namespace contains support for the most common symmetric (des, 3des, rc2, rijndael), asymmetric (rsa,. modern examples of symmetric authenticated encryption of a string, introduction to symmetric and asymmetric encryption,.. System.security.cryptography Documentation.
From www.scribd.com
Unit 4 PDF Transport Layer Security Cryptography System.security.cryptography Documentation information security is composed of 4 parts: Ensure a document is not altered. the documentation for both the aesmanaged and aescryptoserviceprovider class provides elaborate examples. modern examples of symmetric authenticated encryption of a string, introduction to symmetric and asymmetric encryption,. provides cryptographic services, including secure encoding and decoding of data, as well as many other operations,. System.security.cryptography Documentation.
From www.scaler.com
Cryptography and Network Security Scaler Topics System.security.cryptography Documentation the system.security.cryptography namespace contains support for the most common symmetric (des, 3des, rc2, rijndael), asymmetric (rsa,. provides cryptographic services, including secure encoding and decoding of data, as well as many other operations, such as hashing,. we can access the.net library of cryptographic algorithms through the system.security.cryptography namespace. information security is composed of 4 parts: the. System.security.cryptography Documentation.
From illumin.usc.edu
Cryptography and Communication Security in a Digital Age USC Viterbi System.security.cryptography Documentation provides cryptographic services, including secure encoding and decoding of data, as well as many other operations, such as hashing,. information security is composed of 4 parts: we can access the.net library of cryptographic algorithms through the system.security.cryptography namespace. the documentation for both the aesmanaged and aescryptoserviceprovider class provides elaborate examples. the system.security.cryptography namespace contains support. System.security.cryptography Documentation.
From alexbenson466buzz.blogspot.com
Cryptography Definition In Network Security System.security.cryptography Documentation provides cryptographic services, including secure encoding and decoding of data, as well as many other operations, such as hashing,. modern examples of symmetric authenticated encryption of a string, introduction to symmetric and asymmetric encryption,. Ensure a document is not altered. information security is composed of 4 parts: the system.security.cryptography namespace contains support for the most common. System.security.cryptography Documentation.
From thebestvpn.com
Introduction to Cryptography Simple Guide for Beginners System.security.cryptography Documentation Ensure a document is not altered. the documentation for both the aesmanaged and aescryptoserviceprovider class provides elaborate examples. the system.security.cryptography namespace contains support for the most common symmetric (des, 3des, rc2, rijndael), asymmetric (rsa,. modern examples of symmetric authenticated encryption of a string, introduction to symmetric and asymmetric encryption,. provides cryptographic services, including secure encoding and. System.security.cryptography Documentation.
From omiyagames.github.io
Domain List Cryptography documentation System.security.cryptography Documentation modern examples of symmetric authenticated encryption of a string, introduction to symmetric and asymmetric encryption,. provides cryptographic services, including secure encoding and decoding of data, as well as many other operations, such as hashing,. the system.security.cryptography namespace contains support for the most common symmetric (des, 3des, rc2, rijndael), asymmetric (rsa,. the documentation for both the aesmanaged. System.security.cryptography Documentation.
From fahrulroup.blogspot.com
Cryptography FahrulRoup System.security.cryptography Documentation the documentation for both the aesmanaged and aescryptoserviceprovider class provides elaborate examples. provides cryptographic services, including secure encoding and decoding of data, as well as many other operations, such as hashing,. we can access the.net library of cryptographic algorithms through the system.security.cryptography namespace. modern examples of symmetric authenticated encryption of a string, introduction to symmetric and. System.security.cryptography Documentation.
From www.youtube.com
CISSP Communications and Network Security Cryptography Defined YouTube System.security.cryptography Documentation the documentation for both the aesmanaged and aescryptoserviceprovider class provides elaborate examples. information security is composed of 4 parts: modern examples of symmetric authenticated encryption of a string, introduction to symmetric and asymmetric encryption,. Ensure a document is not altered. we can access the.net library of cryptographic algorithms through the system.security.cryptography namespace. provides cryptographic services,. System.security.cryptography Documentation.
From jessicaletitia.blogspot.com
Cryptography JessicaLetitia System.security.cryptography Documentation the documentation for both the aesmanaged and aescryptoserviceprovider class provides elaborate examples. provides cryptographic services, including secure encoding and decoding of data, as well as many other operations, such as hashing,. modern examples of symmetric authenticated encryption of a string, introduction to symmetric and asymmetric encryption,. we can access the.net library of cryptographic algorithms through the. System.security.cryptography Documentation.
From www.simplilearn.com.cach3.com
What is Cryptography And How Does It Protect Data? System.security.cryptography Documentation Ensure a document is not altered. information security is composed of 4 parts: we can access the.net library of cryptographic algorithms through the system.security.cryptography namespace. the system.security.cryptography namespace contains support for the most common symmetric (des, 3des, rc2, rijndael), asymmetric (rsa,. the documentation for both the aesmanaged and aescryptoserviceprovider class provides elaborate examples. provides cryptographic. System.security.cryptography Documentation.
From encryptionconsulting.com
What is Cryptography in security? What are the different types of System.security.cryptography Documentation modern examples of symmetric authenticated encryption of a string, introduction to symmetric and asymmetric encryption,. Ensure a document is not altered. the documentation for both the aesmanaged and aescryptoserviceprovider class provides elaborate examples. the system.security.cryptography namespace contains support for the most common symmetric (des, 3des, rc2, rijndael), asymmetric (rsa,. information security is composed of 4 parts:. System.security.cryptography Documentation.
From bitcoinik.com
Cryptography Simply Explained Bitcoinik System.security.cryptography Documentation Ensure a document is not altered. the documentation for both the aesmanaged and aescryptoserviceprovider class provides elaborate examples. information security is composed of 4 parts: provides cryptographic services, including secure encoding and decoding of data, as well as many other operations, such as hashing,. the system.security.cryptography namespace contains support for the most common symmetric (des, 3des,. System.security.cryptography Documentation.
From www.nepalshovit.com.np
CryptographyIntroduction 5OBIT System.security.cryptography Documentation provides cryptographic services, including secure encoding and decoding of data, as well as many other operations, such as hashing,. Ensure a document is not altered. we can access the.net library of cryptographic algorithms through the system.security.cryptography namespace. the documentation for both the aesmanaged and aescryptoserviceprovider class provides elaborate examples. the system.security.cryptography namespace contains support for the. System.security.cryptography Documentation.
From www.slideserve.com
PPT System Security Cryptography Technologies PowerPoint System.security.cryptography Documentation the documentation for both the aesmanaged and aescryptoserviceprovider class provides elaborate examples. modern examples of symmetric authenticated encryption of a string, introduction to symmetric and asymmetric encryption,. Ensure a document is not altered. provides cryptographic services, including secure encoding and decoding of data, as well as many other operations, such as hashing,. the system.security.cryptography namespace contains. System.security.cryptography Documentation.
From intellizpress.com
Applied Cryptography for Cyber Security System.security.cryptography Documentation the documentation for both the aesmanaged and aescryptoserviceprovider class provides elaborate examples. information security is composed of 4 parts: the system.security.cryptography namespace contains support for the most common symmetric (des, 3des, rc2, rijndael), asymmetric (rsa,. we can access the.net library of cryptographic algorithms through the system.security.cryptography namespace. Ensure a document is not altered. provides cryptographic. System.security.cryptography Documentation.
From shop.handwrittennotes.in
Cryptography & Network Security Notes PDF Shop Handwritten Notes (SHN) System.security.cryptography Documentation we can access the.net library of cryptographic algorithms through the system.security.cryptography namespace. Ensure a document is not altered. modern examples of symmetric authenticated encryption of a string, introduction to symmetric and asymmetric encryption,. provides cryptographic services, including secure encoding and decoding of data, as well as many other operations, such as hashing,. the documentation for both. System.security.cryptography Documentation.
From www.ntirawen.com
Public Key Cryptography Decoded What is Cryptography? Ntirawen System.security.cryptography Documentation modern examples of symmetric authenticated encryption of a string, introduction to symmetric and asymmetric encryption,. information security is composed of 4 parts: provides cryptographic services, including secure encoding and decoding of data, as well as many other operations, such as hashing,. the documentation for both the aesmanaged and aescryptoserviceprovider class provides elaborate examples. we can. System.security.cryptography Documentation.
From www.youtube.com
Cryptography as a Security ToolOperating Systems20A05402TUNIT 5 System.security.cryptography Documentation provides cryptographic services, including secure encoding and decoding of data, as well as many other operations, such as hashing,. we can access the.net library of cryptographic algorithms through the system.security.cryptography namespace. Ensure a document is not altered. the documentation for both the aesmanaged and aescryptoserviceprovider class provides elaborate examples. the system.security.cryptography namespace contains support for the. System.security.cryptography Documentation.
From www.studocu.com
cryptography and network security notes CRYPTOGRAPHY AND NETWORK System.security.cryptography Documentation modern examples of symmetric authenticated encryption of a string, introduction to symmetric and asymmetric encryption,. we can access the.net library of cryptographic algorithms through the system.security.cryptography namespace. information security is composed of 4 parts: the documentation for both the aesmanaged and aescryptoserviceprovider class provides elaborate examples. provides cryptographic services, including secure encoding and decoding of. System.security.cryptography Documentation.
From preyproject.com
Encrypting data best practices for security Prey System.security.cryptography Documentation the system.security.cryptography namespace contains support for the most common symmetric (des, 3des, rc2, rijndael), asymmetric (rsa,. the documentation for both the aesmanaged and aescryptoserviceprovider class provides elaborate examples. information security is composed of 4 parts: we can access the.net library of cryptographic algorithms through the system.security.cryptography namespace. provides cryptographic services, including secure encoding and decoding. System.security.cryptography Documentation.
From www.cloud4u.com
What is Cryptography? Cloud4U System.security.cryptography Documentation Ensure a document is not altered. modern examples of symmetric authenticated encryption of a string, introduction to symmetric and asymmetric encryption,. provides cryptographic services, including secure encoding and decoding of data, as well as many other operations, such as hashing,. the documentation for both the aesmanaged and aescryptoserviceprovider class provides elaborate examples. information security is composed. System.security.cryptography Documentation.
From spark.spit.ac.in
Cryptography The Art of Encryption SPark System.security.cryptography Documentation the documentation for both the aesmanaged and aescryptoserviceprovider class provides elaborate examples. information security is composed of 4 parts: we can access the.net library of cryptographic algorithms through the system.security.cryptography namespace. provides cryptographic services, including secure encoding and decoding of data, as well as many other operations, such as hashing,. the system.security.cryptography namespace contains support. System.security.cryptography Documentation.
From shikamaru119.hashnode.dev
Elliptic Curve Cryptography in Blockchain Basic Introduction System.security.cryptography Documentation the system.security.cryptography namespace contains support for the most common symmetric (des, 3des, rc2, rijndael), asymmetric (rsa,. the documentation for both the aesmanaged and aescryptoserviceprovider class provides elaborate examples. provides cryptographic services, including secure encoding and decoding of data, as well as many other operations, such as hashing,. Ensure a document is not altered. we can access. System.security.cryptography Documentation.