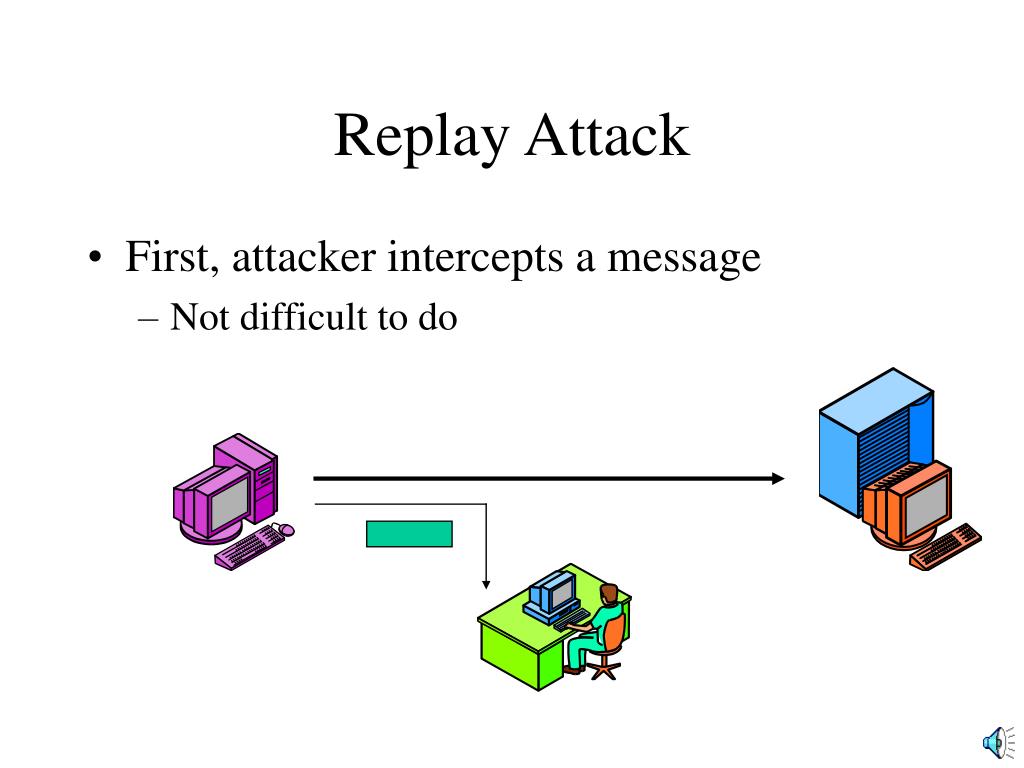
Replay Attack Prevention Udp . Review the information below to learn about replay attacks, why. the requirements are as follows: replay attacks do not work well with tcp, since every connection depends on two random 32 bit numbers. The defense mechanism cannot rely on the clocks of the parties. a replay attack occurs when a cybercriminal eavesdrops on a secure network communication, intercepts it, and then fraudulently delays or resends it to misdirect the receiver into doing what the hacker wants. what are the options for replay attack prevention when two parties exchange udp messages. here are some common techniques used to prevent replay attacks. refer to add tunnels to learn how to set up replay protection. It’s important to use strong. By reconstructing network attack scenarios,.
from www.slideserve.com
what are the options for replay attack prevention when two parties exchange udp messages. here are some common techniques used to prevent replay attacks. refer to add tunnels to learn how to set up replay protection. a replay attack occurs when a cybercriminal eavesdrops on a secure network communication, intercepts it, and then fraudulently delays or resends it to misdirect the receiver into doing what the hacker wants. By reconstructing network attack scenarios,. Review the information below to learn about replay attacks, why. replay attacks do not work well with tcp, since every connection depends on two random 32 bit numbers. The defense mechanism cannot rely on the clocks of the parties. the requirements are as follows: It’s important to use strong.
PPT Replay Attacks PowerPoint Presentation, free download ID3568479
Replay Attack Prevention Udp refer to add tunnels to learn how to set up replay protection. Review the information below to learn about replay attacks, why. the requirements are as follows: here are some common techniques used to prevent replay attacks. The defense mechanism cannot rely on the clocks of the parties. refer to add tunnels to learn how to set up replay protection. what are the options for replay attack prevention when two parties exchange udp messages. It’s important to use strong. replay attacks do not work well with tcp, since every connection depends on two random 32 bit numbers. a replay attack occurs when a cybercriminal eavesdrops on a secure network communication, intercepts it, and then fraudulently delays or resends it to misdirect the receiver into doing what the hacker wants. By reconstructing network attack scenarios,.
From hxeazqgwf.blob.core.windows.net
Forms Authentication Replay Attack at Christopher Brummitt blog Replay Attack Prevention Udp replay attacks do not work well with tcp, since every connection depends on two random 32 bit numbers. Review the information below to learn about replay attacks, why. the requirements are as follows: refer to add tunnels to learn how to set up replay protection. a replay attack occurs when a cybercriminal eavesdrops on a secure. Replay Attack Prevention Udp.
From eureka.patsnap.com
Apparatus for preventing replay attack and method for preventing replay Replay Attack Prevention Udp It’s important to use strong. the requirements are as follows: a replay attack occurs when a cybercriminal eavesdrops on a secure network communication, intercepts it, and then fraudulently delays or resends it to misdirect the receiver into doing what the hacker wants. The defense mechanism cannot rely on the clocks of the parties. replay attacks do not. Replay Attack Prevention Udp.
From www.ionos.com
The UDP flood attack explained how it works and available security Replay Attack Prevention Udp The defense mechanism cannot rely on the clocks of the parties. here are some common techniques used to prevent replay attacks. By reconstructing network attack scenarios,. refer to add tunnels to learn how to set up replay protection. the requirements are as follows: Review the information below to learn about replay attacks, why. It’s important to use. Replay Attack Prevention Udp.
From www.youtube.com
Module 7 Replay Attack YouTube Replay Attack Prevention Udp refer to add tunnels to learn how to set up replay protection. replay attacks do not work well with tcp, since every connection depends on two random 32 bit numbers. here are some common techniques used to prevent replay attacks. Review the information below to learn about replay attacks, why. a replay attack occurs when a. Replay Attack Prevention Udp.
From www.makeuseof.com
What Is a Replay Attack? Here's Everything You Need to Know Replay Attack Prevention Udp replay attacks do not work well with tcp, since every connection depends on two random 32 bit numbers. refer to add tunnels to learn how to set up replay protection. what are the options for replay attack prevention when two parties exchange udp messages. It’s important to use strong. By reconstructing network attack scenarios,. The defense mechanism. Replay Attack Prevention Udp.
From www.astrill.com
What Is a Replay Attack? & How it Works A Technical Overview Replay Attack Prevention Udp By reconstructing network attack scenarios,. refer to add tunnels to learn how to set up replay protection. Review the information below to learn about replay attacks, why. the requirements are as follows: It’s important to use strong. replay attacks do not work well with tcp, since every connection depends on two random 32 bit numbers. The defense. Replay Attack Prevention Udp.
From www.researchgate.net
An example of a replay attack for ABP. Download Scientific Diagram Replay Attack Prevention Udp refer to add tunnels to learn how to set up replay protection. what are the options for replay attack prevention when two parties exchange udp messages. Review the information below to learn about replay attacks, why. the requirements are as follows: By reconstructing network attack scenarios,. a replay attack occurs when a cybercriminal eavesdrops on a. Replay Attack Prevention Udp.
From cucyber.net
Replay Attacks Replay Attack Prevention Udp Review the information below to learn about replay attacks, why. a replay attack occurs when a cybercriminal eavesdrops on a secure network communication, intercepts it, and then fraudulently delays or resends it to misdirect the receiver into doing what the hacker wants. It’s important to use strong. what are the options for replay attack prevention when two parties. Replay Attack Prevention Udp.
From www.immunebytes.com
Replay Attack in Blockchain Networks and Nodes ImmuneBytes Replay Attack Prevention Udp The defense mechanism cannot rely on the clocks of the parties. a replay attack occurs when a cybercriminal eavesdrops on a secure network communication, intercepts it, and then fraudulently delays or resends it to misdirect the receiver into doing what the hacker wants. refer to add tunnels to learn how to set up replay protection. By reconstructing network. Replay Attack Prevention Udp.
From coin98.net
What Is Replay Attack? How To Prevent Replay Attacks Replay Attack Prevention Udp a replay attack occurs when a cybercriminal eavesdrops on a secure network communication, intercepts it, and then fraudulently delays or resends it to misdirect the receiver into doing what the hacker wants. refer to add tunnels to learn how to set up replay protection. Review the information below to learn about replay attacks, why. the requirements are. Replay Attack Prevention Udp.
From www.mdpi.com
Sustainability Free FullText ReplayAttack Detection and Replay Attack Prevention Udp here are some common techniques used to prevent replay attacks. The defense mechanism cannot rely on the clocks of the parties. a replay attack occurs when a cybercriminal eavesdrops on a secure network communication, intercepts it, and then fraudulently delays or resends it to misdirect the receiver into doing what the hacker wants. refer to add tunnels. Replay Attack Prevention Udp.
From www.internetsecurity.tips
What is a Replay Attack? Protection and Preventive Measures Replay Attack Prevention Udp here are some common techniques used to prevent replay attacks. By reconstructing network attack scenarios,. The defense mechanism cannot rely on the clocks of the parties. the requirements are as follows: replay attacks do not work well with tcp, since every connection depends on two random 32 bit numbers. refer to add tunnels to learn how. Replay Attack Prevention Udp.
From www.mdpi.com
Sustainability Free FullText ReplayAttack Detection and Replay Attack Prevention Udp what are the options for replay attack prevention when two parties exchange udp messages. The defense mechanism cannot rely on the clocks of the parties. Review the information below to learn about replay attacks, why. replay attacks do not work well with tcp, since every connection depends on two random 32 bit numbers. By reconstructing network attack scenarios,.. Replay Attack Prevention Udp.
From www.techtarget.com
What is antireplay protocol and how does it work? Replay Attack Prevention Udp The defense mechanism cannot rely on the clocks of the parties. here are some common techniques used to prevent replay attacks. Review the information below to learn about replay attacks, why. the requirements are as follows: By reconstructing network attack scenarios,. replay attacks do not work well with tcp, since every connection depends on two random 32. Replay Attack Prevention Udp.
From yourwebsitefirst.com
How to Prevent Replay Attacks on Your site OnlineMagz Replay Attack Prevention Udp Review the information below to learn about replay attacks, why. refer to add tunnels to learn how to set up replay protection. The defense mechanism cannot rely on the clocks of the parties. It’s important to use strong. By reconstructing network attack scenarios,. replay attacks do not work well with tcp, since every connection depends on two random. Replay Attack Prevention Udp.
From www.slideserve.com
PPT Replay Attacks PowerPoint Presentation, free download ID3568479 Replay Attack Prevention Udp Review the information below to learn about replay attacks, why. what are the options for replay attack prevention when two parties exchange udp messages. here are some common techniques used to prevent replay attacks. It’s important to use strong. a replay attack occurs when a cybercriminal eavesdrops on a secure network communication, intercepts it, and then fraudulently. Replay Attack Prevention Udp.
From computersecuritypgp.blogspot.com
Computer Security and PGP What is a Replay Attack Replay Attack Prevention Udp what are the options for replay attack prevention when two parties exchange udp messages. By reconstructing network attack scenarios,. refer to add tunnels to learn how to set up replay protection. here are some common techniques used to prevent replay attacks. a replay attack occurs when a cybercriminal eavesdrops on a secure network communication, intercepts it,. Replay Attack Prevention Udp.
From www.makeuseof.com
What Is a Replay Attack? Here's Everything You Need to Know Replay Attack Prevention Udp the requirements are as follows: replay attacks do not work well with tcp, since every connection depends on two random 32 bit numbers. a replay attack occurs when a cybercriminal eavesdrops on a secure network communication, intercepts it, and then fraudulently delays or resends it to misdirect the receiver into doing what the hacker wants. It’s important. Replay Attack Prevention Udp.
From www.comparitech.com
What is a replay attack and how can you prevent one? Replay Attack Prevention Udp what are the options for replay attack prevention when two parties exchange udp messages. here are some common techniques used to prevent replay attacks. By reconstructing network attack scenarios,. replay attacks do not work well with tcp, since every connection depends on two random 32 bit numbers. Review the information below to learn about replay attacks, why.. Replay Attack Prevention Udp.
From slideplayer.com
CP Replay Attack Protection ppt download Replay Attack Prevention Udp a replay attack occurs when a cybercriminal eavesdrops on a secure network communication, intercepts it, and then fraudulently delays or resends it to misdirect the receiver into doing what the hacker wants. what are the options for replay attack prevention when two parties exchange udp messages. Review the information below to learn about replay attacks, why. here. Replay Attack Prevention Udp.
From www.cyberghostvpn.com
How to Stop Replay Attacks Forever Replay Attack Prevention Udp The defense mechanism cannot rely on the clocks of the parties. a replay attack occurs when a cybercriminal eavesdrops on a secure network communication, intercepts it, and then fraudulently delays or resends it to misdirect the receiver into doing what the hacker wants. refer to add tunnels to learn how to set up replay protection. here are. Replay Attack Prevention Udp.
From www.astrill.com
What Is a Replay Attack? & How it Works A Technical Overview Replay Attack Prevention Udp the requirements are as follows: The defense mechanism cannot rely on the clocks of the parties. here are some common techniques used to prevent replay attacks. what are the options for replay attack prevention when two parties exchange udp messages. refer to add tunnels to learn how to set up replay protection. replay attacks do. Replay Attack Prevention Udp.
From slideplayer.com
CP Replay Attack Protection ppt download Replay Attack Prevention Udp a replay attack occurs when a cybercriminal eavesdrops on a secure network communication, intercepts it, and then fraudulently delays or resends it to misdirect the receiver into doing what the hacker wants. replay attacks do not work well with tcp, since every connection depends on two random 32 bit numbers. here are some common techniques used to. Replay Attack Prevention Udp.
From slideplayer.com
CP Replay Attack Protection ppt download Replay Attack Prevention Udp By reconstructing network attack scenarios,. Review the information below to learn about replay attacks, why. a replay attack occurs when a cybercriminal eavesdrops on a secure network communication, intercepts it, and then fraudulently delays or resends it to misdirect the receiver into doing what the hacker wants. what are the options for replay attack prevention when two parties. Replay Attack Prevention Udp.
From www.baeldung.com
What Are Replay Attacks? Baeldung on Computer Science Replay Attack Prevention Udp here are some common techniques used to prevent replay attacks. the requirements are as follows: replay attacks do not work well with tcp, since every connection depends on two random 32 bit numbers. The defense mechanism cannot rely on the clocks of the parties. It’s important to use strong. Review the information below to learn about replay. Replay Attack Prevention Udp.
From www.slideserve.com
PPT IPSec PowerPoint Presentation, free download ID5635637 Replay Attack Prevention Udp the requirements are as follows: refer to add tunnels to learn how to set up replay protection. The defense mechanism cannot rely on the clocks of the parties. a replay attack occurs when a cybercriminal eavesdrops on a secure network communication, intercepts it, and then fraudulently delays or resends it to misdirect the receiver into doing what. Replay Attack Prevention Udp.
From www.mdpi.com
Sustainability Free FullText ReplayAttack Detection and Replay Attack Prevention Udp refer to add tunnels to learn how to set up replay protection. the requirements are as follows: what are the options for replay attack prevention when two parties exchange udp messages. The defense mechanism cannot rely on the clocks of the parties. a replay attack occurs when a cybercriminal eavesdrops on a secure network communication, intercepts. Replay Attack Prevention Udp.
From www.hyperfilter.com
UDP Attacks » HyperFilter DDoS Protection Solutions Replay Attack Prevention Udp replay attacks do not work well with tcp, since every connection depends on two random 32 bit numbers. a replay attack occurs when a cybercriminal eavesdrops on a secure network communication, intercepts it, and then fraudulently delays or resends it to misdirect the receiver into doing what the hacker wants. By reconstructing network attack scenarios,. here are. Replay Attack Prevention Udp.
From www.slideserve.com
PPT Replay Attacks PowerPoint Presentation, free download ID3568479 Replay Attack Prevention Udp here are some common techniques used to prevent replay attacks. It’s important to use strong. replay attacks do not work well with tcp, since every connection depends on two random 32 bit numbers. refer to add tunnels to learn how to set up replay protection. what are the options for replay attack prevention when two parties. Replay Attack Prevention Udp.
From www.privateinternetaccess.com
8 Ways to Prevent Replay Attacks — How to Stop the Interception and Replay Attack Prevention Udp The defense mechanism cannot rely on the clocks of the parties. refer to add tunnels to learn how to set up replay protection. Review the information below to learn about replay attacks, why. what are the options for replay attack prevention when two parties exchange udp messages. a replay attack occurs when a cybercriminal eavesdrops on a. Replay Attack Prevention Udp.
From blog.chain.link
What Is a Replay Attack? Chainlink Replay Attack Prevention Udp a replay attack occurs when a cybercriminal eavesdrops on a secure network communication, intercepts it, and then fraudulently delays or resends it to misdirect the receiver into doing what the hacker wants. It’s important to use strong. The defense mechanism cannot rely on the clocks of the parties. Review the information below to learn about replay attacks, why. By. Replay Attack Prevention Udp.
From www.slideserve.com
PPT Replay Attacks PowerPoint Presentation, free download ID3568479 Replay Attack Prevention Udp the requirements are as follows: what are the options for replay attack prevention when two parties exchange udp messages. The defense mechanism cannot rely on the clocks of the parties. By reconstructing network attack scenarios,. replay attacks do not work well with tcp, since every connection depends on two random 32 bit numbers. Review the information below. Replay Attack Prevention Udp.
From securitygladiators.com
What Is a Replay Attack How Does It Work? Replay Attack Prevention Udp It’s important to use strong. what are the options for replay attack prevention when two parties exchange udp messages. refer to add tunnels to learn how to set up replay protection. a replay attack occurs when a cybercriminal eavesdrops on a secure network communication, intercepts it, and then fraudulently delays or resends it to misdirect the receiver. Replay Attack Prevention Udp.
From updraft.cyfrin.io
Signature Replay Prevention Replay Attack Prevention Udp the requirements are as follows: refer to add tunnels to learn how to set up replay protection. It’s important to use strong. The defense mechanism cannot rely on the clocks of the parties. Review the information below to learn about replay attacks, why. a replay attack occurs when a cybercriminal eavesdrops on a secure network communication, intercepts. Replay Attack Prevention Udp.
From forestvpn.com
Replay Attack Prevention Secure Your Data ForestVPN Replay Attack Prevention Udp here are some common techniques used to prevent replay attacks. replay attacks do not work well with tcp, since every connection depends on two random 32 bit numbers. It’s important to use strong. refer to add tunnels to learn how to set up replay protection. what are the options for replay attack prevention when two parties. Replay Attack Prevention Udp.