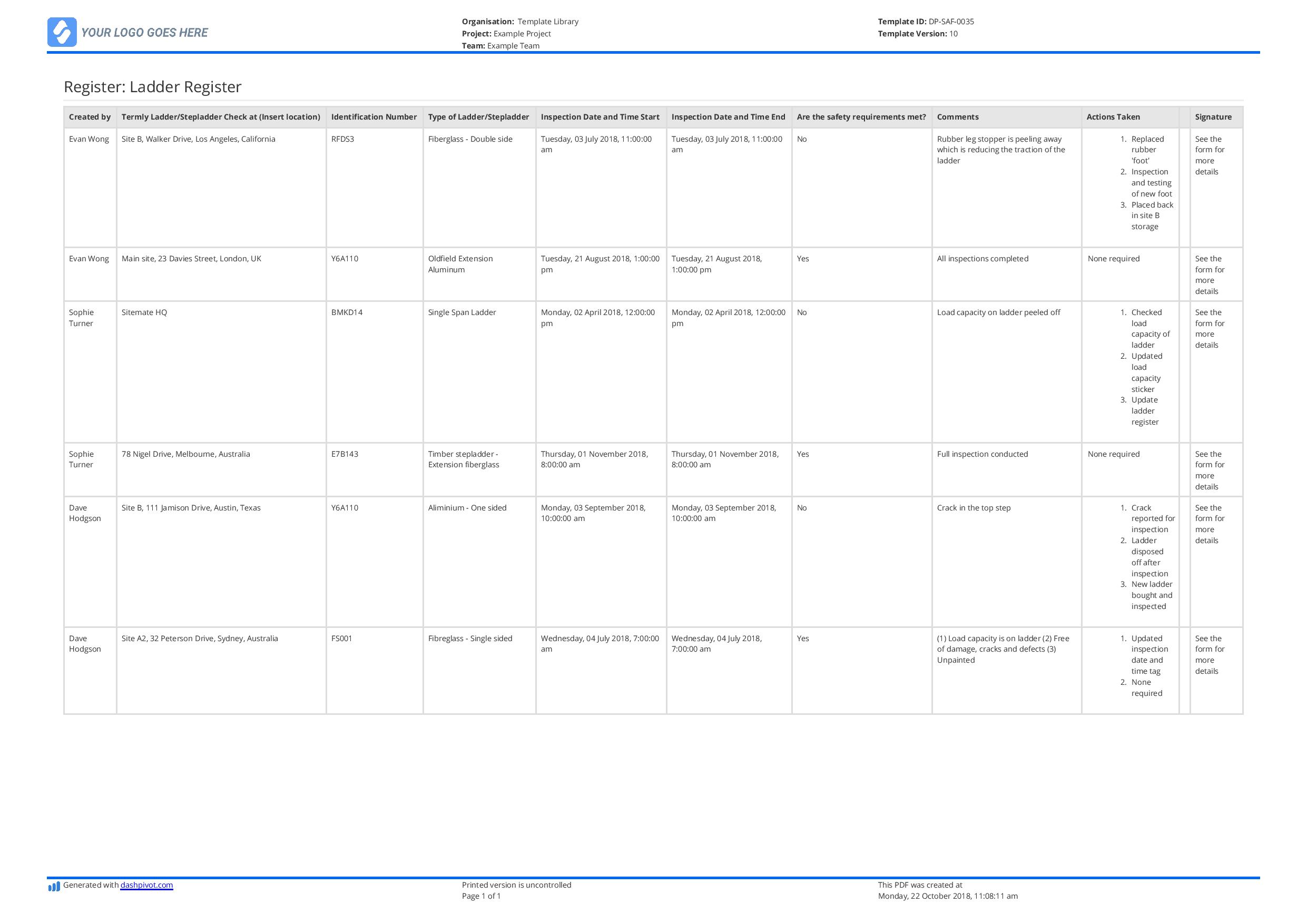
Access Control Register Example . Access control is a fundamental aspect of cybersecurity that safeguards sensitive data and protects against unauthorized access. Mandatory access control (mac) is a strict policy in which a central authority controls access rights. Access control is key in it and cybersecurity to minimize risks by allowing resource access only to authorized users and systems. An access control policy serves as a blueprint for managing access to systems, applications, and data within your organization. The ultimate guide includes an iso 27001 access control policy template, access control policy example and iso 27001 certification guide. Administrators decide which users can access specific resources, and users cannot.
from sitemate.com
Access control is a fundamental aspect of cybersecurity that safeguards sensitive data and protects against unauthorized access. Mandatory access control (mac) is a strict policy in which a central authority controls access rights. The ultimate guide includes an iso 27001 access control policy template, access control policy example and iso 27001 certification guide. Access control is key in it and cybersecurity to minimize risks by allowing resource access only to authorized users and systems. Administrators decide which users can access specific resources, and users cannot. An access control policy serves as a blueprint for managing access to systems, applications, and data within your organization.
Free Ladder Register template Better than excel and editable
Access Control Register Example An access control policy serves as a blueprint for managing access to systems, applications, and data within your organization. Access control is key in it and cybersecurity to minimize risks by allowing resource access only to authorized users and systems. Mandatory access control (mac) is a strict policy in which a central authority controls access rights. The ultimate guide includes an iso 27001 access control policy template, access control policy example and iso 27001 certification guide. An access control policy serves as a blueprint for managing access to systems, applications, and data within your organization. Access control is a fundamental aspect of cybersecurity that safeguards sensitive data and protects against unauthorized access. Administrators decide which users can access specific resources, and users cannot.
From slidesdocs.com
Free Access Registration Form Templates For Google Sheets And Microsoft Access Control Register Example The ultimate guide includes an iso 27001 access control policy template, access control policy example and iso 27001 certification guide. Mandatory access control (mac) is a strict policy in which a central authority controls access rights. Administrators decide which users can access specific resources, and users cannot. An access control policy serves as a blueprint for managing access to systems,. Access Control Register Example.
From armymunitions.tpub.com
Figure 32. An example of a completed DA Form 5513R (Key Control Access Control Register Example Access control is key in it and cybersecurity to minimize risks by allowing resource access only to authorized users and systems. Administrators decide which users can access specific resources, and users cannot. Mandatory access control (mac) is a strict policy in which a central authority controls access rights. Access control is a fundamental aspect of cybersecurity that safeguards sensitive data. Access Control Register Example.
From www.matrixaccesscontrol.com
An Easy Guide to Selecting Access Control Readers for your Organization Access Control Register Example Mandatory access control (mac) is a strict policy in which a central authority controls access rights. Administrators decide which users can access specific resources, and users cannot. Access control is a fundamental aspect of cybersecurity that safeguards sensitive data and protects against unauthorized access. An access control policy serves as a blueprint for managing access to systems, applications, and data. Access Control Register Example.
From www.inpaspages.com
Key control Register Access Control Register Example Mandatory access control (mac) is a strict policy in which a central authority controls access rights. An access control policy serves as a blueprint for managing access to systems, applications, and data within your organization. Access control is a fundamental aspect of cybersecurity that safeguards sensitive data and protects against unauthorized access. The ultimate guide includes an iso 27001 access. Access Control Register Example.
From www.youtube.com
Microsoft Access Check Register Database Lessons and Template Access Control Register Example An access control policy serves as a blueprint for managing access to systems, applications, and data within your organization. Access control is a fundamental aspect of cybersecurity that safeguards sensitive data and protects against unauthorized access. Access control is key in it and cybersecurity to minimize risks by allowing resource access only to authorized users and systems. The ultimate guide. Access Control Register Example.
From slidesdocs.com
Free Access Registration Form Templates For Google Sheets And Microsoft Access Control Register Example Administrators decide which users can access specific resources, and users cannot. Access control is key in it and cybersecurity to minimize risks by allowing resource access only to authorized users and systems. Mandatory access control (mac) is a strict policy in which a central authority controls access rights. The ultimate guide includes an iso 27001 access control policy template, access. Access Control Register Example.
From templates.esad.edu.br
Traffic Control Plan Template Access Control Register Example Access control is key in it and cybersecurity to minimize risks by allowing resource access only to authorized users and systems. Mandatory access control (mac) is a strict policy in which a central authority controls access rights. An access control policy serves as a blueprint for managing access to systems, applications, and data within your organization. Access control is a. Access Control Register Example.
From flevy.com
Excel Template Access Register Template (Excel template (XLS)) Flevy Access Control Register Example An access control policy serves as a blueprint for managing access to systems, applications, and data within your organization. Access control is key in it and cybersecurity to minimize risks by allowing resource access only to authorized users and systems. Mandatory access control (mac) is a strict policy in which a central authority controls access rights. Administrators decide which users. Access Control Register Example.
From templates.udlvirtual.edu.pe
Document Control Register Template Free Printable Templates Access Control Register Example Access control is a fundamental aspect of cybersecurity that safeguards sensitive data and protects against unauthorized access. An access control policy serves as a blueprint for managing access to systems, applications, and data within your organization. Access control is key in it and cybersecurity to minimize risks by allowing resource access only to authorized users and systems. The ultimate guide. Access Control Register Example.
From www.bizmanualz.com
IT Access Control Policy Access Control Policies And Procedures Access Control Register Example Mandatory access control (mac) is a strict policy in which a central authority controls access rights. The ultimate guide includes an iso 27001 access control policy template, access control policy example and iso 27001 certification guide. Access control is a fundamental aspect of cybersecurity that safeguards sensitive data and protects against unauthorized access. An access control policy serves as a. Access Control Register Example.
From flevy.com
Excel Template Access card register form (Excel template XLS) Flevy Access Control Register Example An access control policy serves as a blueprint for managing access to systems, applications, and data within your organization. The ultimate guide includes an iso 27001 access control policy template, access control policy example and iso 27001 certification guide. Access control is key in it and cybersecurity to minimize risks by allowing resource access only to authorized users and systems.. Access Control Register Example.
From sitemate.com
Free Ladder Register template Better than excel and editable Access Control Register Example Access control is a fundamental aspect of cybersecurity that safeguards sensitive data and protects against unauthorized access. The ultimate guide includes an iso 27001 access control policy template, access control policy example and iso 27001 certification guide. Access control is key in it and cybersecurity to minimize risks by allowing resource access only to authorized users and systems. An access. Access Control Register Example.
From www.slideserve.com
PPT Access Control Matrix PowerPoint Presentation, free download ID Access Control Register Example Administrators decide which users can access specific resources, and users cannot. The ultimate guide includes an iso 27001 access control policy template, access control policy example and iso 27001 certification guide. Access control is a fundamental aspect of cybersecurity that safeguards sensitive data and protects against unauthorized access. Access control is key in it and cybersecurity to minimize risks by. Access Control Register Example.
From www.dochub.com
Key register template Fill out & sign online DocHub Access Control Register Example Mandatory access control (mac) is a strict policy in which a central authority controls access rights. Administrators decide which users can access specific resources, and users cannot. Access control is key in it and cybersecurity to minimize risks by allowing resource access only to authorized users and systems. Access control is a fundamental aspect of cybersecurity that safeguards sensitive data. Access Control Register Example.
From www.zkteco.in
Selfservice Visitor Registration and Access Control Management Solution Access Control Register Example Mandatory access control (mac) is a strict policy in which a central authority controls access rights. Access control is key in it and cybersecurity to minimize risks by allowing resource access only to authorized users and systems. Access control is a fundamental aspect of cybersecurity that safeguards sensitive data and protects against unauthorized access. The ultimate guide includes an iso. Access Control Register Example.
From ledgersystems.co.za
Visitors Vehicle Entry Control Register Ledger Systems Access Control Register Example The ultimate guide includes an iso 27001 access control policy template, access control policy example and iso 27001 certification guide. Mandatory access control (mac) is a strict policy in which a central authority controls access rights. Access control is a fundamental aspect of cybersecurity that safeguards sensitive data and protects against unauthorized access. An access control policy serves as a. Access Control Register Example.
From www.techtarget.com
What is RoleBased Access Control (RBAC)? Definition from TechTarget Access Control Register Example An access control policy serves as a blueprint for managing access to systems, applications, and data within your organization. Access control is key in it and cybersecurity to minimize risks by allowing resource access only to authorized users and systems. Mandatory access control (mac) is a strict policy in which a central authority controls access rights. The ultimate guide includes. Access Control Register Example.
From www.formsbirds.com
Standard Access Control Policy Template Free Download Access Control Register Example An access control policy serves as a blueprint for managing access to systems, applications, and data within your organization. Administrators decide which users can access specific resources, and users cannot. Mandatory access control (mac) is a strict policy in which a central authority controls access rights. Access control is key in it and cybersecurity to minimize risks by allowing resource. Access Control Register Example.
From www.networkeducator.com
What Is Access Control List (ACL) & How It Works Network Educator Access Control Register Example Administrators decide which users can access specific resources, and users cannot. The ultimate guide includes an iso 27001 access control policy template, access control policy example and iso 27001 certification guide. Access control is a fundamental aspect of cybersecurity that safeguards sensitive data and protects against unauthorized access. An access control policy serves as a blueprint for managing access to. Access Control Register Example.
From www.slideserve.com
PPT Lecture 7 Access Control PowerPoint Presentation, free download Access Control Register Example Administrators decide which users can access specific resources, and users cannot. Access control is a fundamental aspect of cybersecurity that safeguards sensitive data and protects against unauthorized access. Mandatory access control (mac) is a strict policy in which a central authority controls access rights. The ultimate guide includes an iso 27001 access control policy template, access control policy example and. Access Control Register Example.
From slidesdocs.com
Free Access Registration Form Templates For Google Sheets And Microsoft Access Control Register Example Access control is key in it and cybersecurity to minimize risks by allowing resource access only to authorized users and systems. Mandatory access control (mac) is a strict policy in which a central authority controls access rights. An access control policy serves as a blueprint for managing access to systems, applications, and data within your organization. The ultimate guide includes. Access Control Register Example.
From www.bizmanualz.com
It Access Control Log Template Access Control Register Example An access control policy serves as a blueprint for managing access to systems, applications, and data within your organization. The ultimate guide includes an iso 27001 access control policy template, access control policy example and iso 27001 certification guide. Mandatory access control (mac) is a strict policy in which a central authority controls access rights. Access control is a fundamental. Access Control Register Example.
From www.qualads.com
Access Control Log Template Qualads Access Control Register Example Access control is key in it and cybersecurity to minimize risks by allowing resource access only to authorized users and systems. The ultimate guide includes an iso 27001 access control policy template, access control policy example and iso 27001 certification guide. Administrators decide which users can access specific resources, and users cannot. An access control policy serves as a blueprint. Access Control Register Example.
From www.childforallseasons.com
Iso 27001 Access Control Policy Sample Template 1 Resume Examples Access Control Register Example Access control is a fundamental aspect of cybersecurity that safeguards sensitive data and protects against unauthorized access. An access control policy serves as a blueprint for managing access to systems, applications, and data within your organization. The ultimate guide includes an iso 27001 access control policy template, access control policy example and iso 27001 certification guide. Administrators decide which users. Access Control Register Example.
From www.slideserve.com
PPT C Programming in Embedded Systems PowerPoint Presentation, free Access Control Register Example Mandatory access control (mac) is a strict policy in which a central authority controls access rights. Access control is key in it and cybersecurity to minimize risks by allowing resource access only to authorized users and systems. The ultimate guide includes an iso 27001 access control policy template, access control policy example and iso 27001 certification guide. Access control is. Access Control Register Example.
From content-1606--budibase.netlify.app
RoleBased Access Control Ultimate Guide Access Control Register Example Access control is a fundamental aspect of cybersecurity that safeguards sensitive data and protects against unauthorized access. The ultimate guide includes an iso 27001 access control policy template, access control policy example and iso 27001 certification guide. Mandatory access control (mac) is a strict policy in which a central authority controls access rights. Administrators decide which users can access specific. Access Control Register Example.
From advisera.com
ISO 27001 access control Top tips on how to comply Access Control Register Example Access control is key in it and cybersecurity to minimize risks by allowing resource access only to authorized users and systems. Mandatory access control (mac) is a strict policy in which a central authority controls access rights. The ultimate guide includes an iso 27001 access control policy template, access control policy example and iso 27001 certification guide. An access control. Access Control Register Example.
From slidesdocs.com
Free Access Registration Form Templates For Google Sheets And Microsoft Access Control Register Example Access control is key in it and cybersecurity to minimize risks by allowing resource access only to authorized users and systems. The ultimate guide includes an iso 27001 access control policy template, access control policy example and iso 27001 certification guide. Mandatory access control (mac) is a strict policy in which a central authority controls access rights. Access control is. Access Control Register Example.
From klariti.com
Data Access Control Form Word Template Software Testing Access Control Register Example Mandatory access control (mac) is a strict policy in which a central authority controls access rights. An access control policy serves as a blueprint for managing access to systems, applications, and data within your organization. The ultimate guide includes an iso 27001 access control policy template, access control policy example and iso 27001 certification guide. Administrators decide which users can. Access Control Register Example.
From www.sampletemplates.com
FREE 8+ Sample Key Log Templates in PDF MS Word Excel Access Control Register Example Administrators decide which users can access specific resources, and users cannot. Mandatory access control (mac) is a strict policy in which a central authority controls access rights. Access control is key in it and cybersecurity to minimize risks by allowing resource access only to authorized users and systems. The ultimate guide includes an iso 27001 access control policy template, access. Access Control Register Example.
From www.etsy.com
Document Control Register Health and Safety Template Excel Template Access Control Register Example The ultimate guide includes an iso 27001 access control policy template, access control policy example and iso 27001 certification guide. An access control policy serves as a blueprint for managing access to systems, applications, and data within your organization. Mandatory access control (mac) is a strict policy in which a central authority controls access rights. Access control is key in. Access Control Register Example.
From templates.rjuuc.edu.np
Role Based Access Control Matrix Template Access Control Register Example Administrators decide which users can access specific resources, and users cannot. Mandatory access control (mac) is a strict policy in which a central authority controls access rights. The ultimate guide includes an iso 27001 access control policy template, access control policy example and iso 27001 certification guide. Access control is a fundamental aspect of cybersecurity that safeguards sensitive data and. Access Control Register Example.
From cie-group.com
How to design an Access Control system Access Control Register Example The ultimate guide includes an iso 27001 access control policy template, access control policy example and iso 27001 certification guide. Access control is a fundamental aspect of cybersecurity that safeguards sensitive data and protects against unauthorized access. Mandatory access control (mac) is a strict policy in which a central authority controls access rights. Administrators decide which users can access specific. Access Control Register Example.
From www.manycaps.com
Document Control Register Template Blog Access Control Register Example Access control is a fundamental aspect of cybersecurity that safeguards sensitive data and protects against unauthorized access. Mandatory access control (mac) is a strict policy in which a central authority controls access rights. An access control policy serves as a blueprint for managing access to systems, applications, and data within your organization. Access control is key in it and cybersecurity. Access Control Register Example.
From flevy.com
Excel Template Access Register Template (Excel template XLS) Flevy Access Control Register Example Administrators decide which users can access specific resources, and users cannot. Access control is key in it and cybersecurity to minimize risks by allowing resource access only to authorized users and systems. Access control is a fundamental aspect of cybersecurity that safeguards sensitive data and protects against unauthorized access. Mandatory access control (mac) is a strict policy in which a. Access Control Register Example.