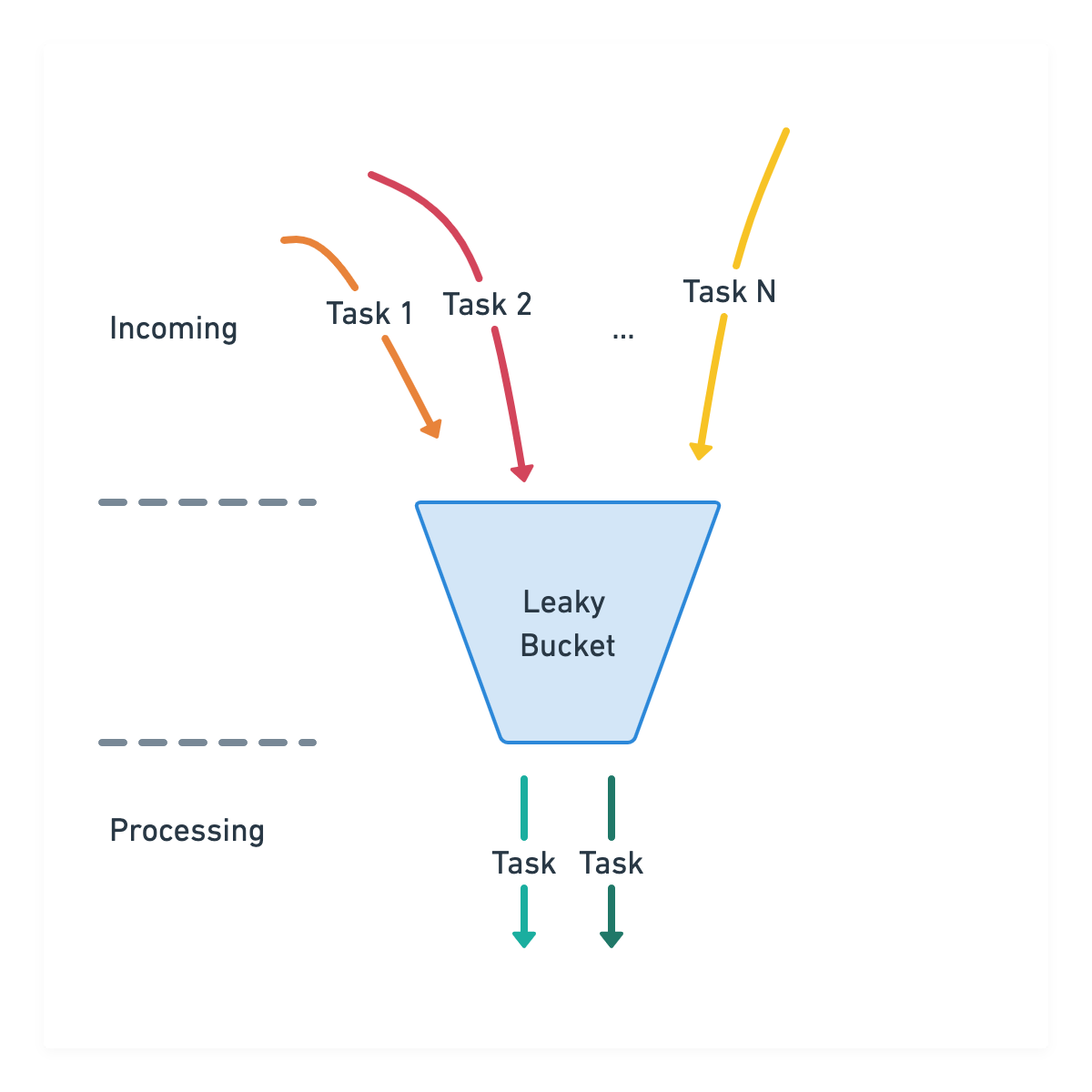
Use Of Leaky Bucket Algorithm . The leaky bucket algorithm is a method of congestion control where multiple packets are stored temporarily. It is commonly used in network environments to regulate data flow, prevent congestion, and ensure fair resource allocation. The leaky bucket algorithm is designed to handle bursty data traffic by allowing packets to flow at a regulated rate, which helps maintain consistent. Enter the leaky bucket algorithm — a simple yet effective strategy for traffic shaping and rate limiting. One of the most effective ways to control congestion is trying to reduce the load that transport layer is placing on the network. The leaky bucket is used to implement traffic policing and traffic shaping in ethernet and cellular data networks. The leaky bucket algorithm finds applications in various scenarios, including traffic shaping, rate limiting, and quality of service (qos) management. In this blog post, we’ll delve.
from itnext.io
In this blog post, we’ll delve. The leaky bucket is used to implement traffic policing and traffic shaping in ethernet and cellular data networks. The leaky bucket algorithm finds applications in various scenarios, including traffic shaping, rate limiting, and quality of service (qos) management. One of the most effective ways to control congestion is trying to reduce the load that transport layer is placing on the network. Enter the leaky bucket algorithm — a simple yet effective strategy for traffic shaping and rate limiting. The leaky bucket algorithm is a method of congestion control where multiple packets are stored temporarily. The leaky bucket algorithm is designed to handle bursty data traffic by allowing packets to flow at a regulated rate, which helps maintain consistent. It is commonly used in network environments to regulate data flow, prevent congestion, and ensure fair resource allocation.
Rate limiting with leaky bucket algorithm by Codejitsu ITNEXT
Use Of Leaky Bucket Algorithm One of the most effective ways to control congestion is trying to reduce the load that transport layer is placing on the network. The leaky bucket algorithm finds applications in various scenarios, including traffic shaping, rate limiting, and quality of service (qos) management. The leaky bucket algorithm is a method of congestion control where multiple packets are stored temporarily. In this blog post, we’ll delve. The leaky bucket is used to implement traffic policing and traffic shaping in ethernet and cellular data networks. Enter the leaky bucket algorithm — a simple yet effective strategy for traffic shaping and rate limiting. One of the most effective ways to control congestion is trying to reduce the load that transport layer is placing on the network. The leaky bucket algorithm is designed to handle bursty data traffic by allowing packets to flow at a regulated rate, which helps maintain consistent. It is commonly used in network environments to regulate data flow, prevent congestion, and ensure fair resource allocation.
From www.youtube.com
Token and Leaky Bucket Algorithm YouTube Use Of Leaky Bucket Algorithm One of the most effective ways to control congestion is trying to reduce the load that transport layer is placing on the network. The leaky bucket is used to implement traffic policing and traffic shaping in ethernet and cellular data networks. Enter the leaky bucket algorithm — a simple yet effective strategy for traffic shaping and rate limiting. It is. Use Of Leaky Bucket Algorithm.
From in.pinterest.com
Leaky Bucket Algorithm educlick Algorithm, Computer network Use Of Leaky Bucket Algorithm One of the most effective ways to control congestion is trying to reduce the load that transport layer is placing on the network. The leaky bucket is used to implement traffic policing and traffic shaping in ethernet and cellular data networks. The leaky bucket algorithm is designed to handle bursty data traffic by allowing packets to flow at a regulated. Use Of Leaky Bucket Algorithm.
From www.researchgate.net
The Packet leaky Bucket Algorithm marked with low priority (maximum Use Of Leaky Bucket Algorithm One of the most effective ways to control congestion is trying to reduce the load that transport layer is placing on the network. In this blog post, we’ll delve. It is commonly used in network environments to regulate data flow, prevent congestion, and ensure fair resource allocation. The leaky bucket algorithm is a method of congestion control where multiple packets. Use Of Leaky Bucket Algorithm.
From songhayoung.github.io
[System Design] Leaky bucket / token bucket SUMFIのBlog Use Of Leaky Bucket Algorithm The leaky bucket algorithm is a method of congestion control where multiple packets are stored temporarily. One of the most effective ways to control congestion is trying to reduce the load that transport layer is placing on the network. It is commonly used in network environments to regulate data flow, prevent congestion, and ensure fair resource allocation. The leaky bucket. Use Of Leaky Bucket Algorithm.
From www.linqz.io
Leaky/Token bucket algorithm for flow control Learn INQuiZitively Use Of Leaky Bucket Algorithm Enter the leaky bucket algorithm — a simple yet effective strategy for traffic shaping and rate limiting. The leaky bucket algorithm is a method of congestion control where multiple packets are stored temporarily. In this blog post, we’ll delve. The leaky bucket is used to implement traffic policing and traffic shaping in ethernet and cellular data networks. The leaky bucket. Use Of Leaky Bucket Algorithm.
From www.researchgate.net
Leaky bucket algorithm Download Scientific Diagram Use Of Leaky Bucket Algorithm It is commonly used in network environments to regulate data flow, prevent congestion, and ensure fair resource allocation. In this blog post, we’ll delve. The leaky bucket is used to implement traffic policing and traffic shaping in ethernet and cellular data networks. The leaky bucket algorithm finds applications in various scenarios, including traffic shaping, rate limiting, and quality of service. Use Of Leaky Bucket Algorithm.
From www.slideserve.com
PPT Lecture 10 PowerPoint Presentation, free download ID4737649 Use Of Leaky Bucket Algorithm In this blog post, we’ll delve. One of the most effective ways to control congestion is trying to reduce the load that transport layer is placing on the network. Enter the leaky bucket algorithm — a simple yet effective strategy for traffic shaping and rate limiting. The leaky bucket algorithm finds applications in various scenarios, including traffic shaping, rate limiting,. Use Of Leaky Bucket Algorithm.
From botpenguin.com
What is Leaky Bucket Theory & its Applications? Use Of Leaky Bucket Algorithm It is commonly used in network environments to regulate data flow, prevent congestion, and ensure fair resource allocation. The leaky bucket algorithm finds applications in various scenarios, including traffic shaping, rate limiting, and quality of service (qos) management. One of the most effective ways to control congestion is trying to reduce the load that transport layer is placing on the. Use Of Leaky Bucket Algorithm.
From www.pdffiller.com
Fillable Online LEAKY BUCKET ALGORITHM Fax Email Print pdfFiller Use Of Leaky Bucket Algorithm The leaky bucket algorithm is a method of congestion control where multiple packets are stored temporarily. The leaky bucket algorithm finds applications in various scenarios, including traffic shaping, rate limiting, and quality of service (qos) management. It is commonly used in network environments to regulate data flow, prevent congestion, and ensure fair resource allocation. The leaky bucket is used to. Use Of Leaky Bucket Algorithm.
From www.slideshare.net
Chap24 Use Of Leaky Bucket Algorithm It is commonly used in network environments to regulate data flow, prevent congestion, and ensure fair resource allocation. The leaky bucket algorithm finds applications in various scenarios, including traffic shaping, rate limiting, and quality of service (qos) management. In this blog post, we’ll delve. The leaky bucket is used to implement traffic policing and traffic shaping in ethernet and cellular. Use Of Leaky Bucket Algorithm.
From www.researchgate.net
Leaky bucket approach. Download Scientific Diagram Use Of Leaky Bucket Algorithm The leaky bucket algorithm is a method of congestion control where multiple packets are stored temporarily. Enter the leaky bucket algorithm — a simple yet effective strategy for traffic shaping and rate limiting. One of the most effective ways to control congestion is trying to reduce the load that transport layer is placing on the network. The leaky bucket algorithm. Use Of Leaky Bucket Algorithm.
From www.studypool.com
SOLUTION Leaky Bucket Algorithm C Program Studypool Use Of Leaky Bucket Algorithm The leaky bucket algorithm finds applications in various scenarios, including traffic shaping, rate limiting, and quality of service (qos) management. Enter the leaky bucket algorithm — a simple yet effective strategy for traffic shaping and rate limiting. One of the most effective ways to control congestion is trying to reduce the load that transport layer is placing on the network.. Use Of Leaky Bucket Algorithm.
From www.youtube.com
Leaky Bucket Algorithm YouTube Use Of Leaky Bucket Algorithm It is commonly used in network environments to regulate data flow, prevent congestion, and ensure fair resource allocation. One of the most effective ways to control congestion is trying to reduce the load that transport layer is placing on the network. The leaky bucket algorithm is designed to handle bursty data traffic by allowing packets to flow at a regulated. Use Of Leaky Bucket Algorithm.
From www.geeksforgeeks.org
Rate Limiting Algorithms System Design Use Of Leaky Bucket Algorithm The leaky bucket algorithm is designed to handle bursty data traffic by allowing packets to flow at a regulated rate, which helps maintain consistent. One of the most effective ways to control congestion is trying to reduce the load that transport layer is placing on the network. The leaky bucket algorithm is a method of congestion control where multiple packets. Use Of Leaky Bucket Algorithm.
From itnext.io
Rate limiting with leaky bucket algorithm by Codejitsu ITNEXT Use Of Leaky Bucket Algorithm The leaky bucket algorithm is designed to handle bursty data traffic by allowing packets to flow at a regulated rate, which helps maintain consistent. In this blog post, we’ll delve. One of the most effective ways to control congestion is trying to reduce the load that transport layer is placing on the network. The leaky bucket is used to implement. Use Of Leaky Bucket Algorithm.
From www.researchgate.net
Illustration of the GCRA (i,l) Algorithm as Leaky Bucket Download Use Of Leaky Bucket Algorithm The leaky bucket is used to implement traffic policing and traffic shaping in ethernet and cellular data networks. It is commonly used in network environments to regulate data flow, prevent congestion, and ensure fair resource allocation. The leaky bucket algorithm finds applications in various scenarios, including traffic shaping, rate limiting, and quality of service (qos) management. The leaky bucket algorithm. Use Of Leaky Bucket Algorithm.
From www.slideshare.net
Mini Project final report on " LEAKY BUCKET ALGORITHM Use Of Leaky Bucket Algorithm In this blog post, we’ll delve. Enter the leaky bucket algorithm — a simple yet effective strategy for traffic shaping and rate limiting. One of the most effective ways to control congestion is trying to reduce the load that transport layer is placing on the network. The leaky bucket algorithm is a method of congestion control where multiple packets are. Use Of Leaky Bucket Algorithm.
From www.researchgate.net
Flowchart of the conventional leaky bucket algorithm. Download Use Of Leaky Bucket Algorithm One of the most effective ways to control congestion is trying to reduce the load that transport layer is placing on the network. Enter the leaky bucket algorithm — a simple yet effective strategy for traffic shaping and rate limiting. The leaky bucket algorithm is designed to handle bursty data traffic by allowing packets to flow at a regulated rate,. Use Of Leaky Bucket Algorithm.
From www.youtube.com
leaky bucket algorithm traffic shaping in computer networks 2021 Use Of Leaky Bucket Algorithm The leaky bucket algorithm is designed to handle bursty data traffic by allowing packets to flow at a regulated rate, which helps maintain consistent. The leaky bucket is used to implement traffic policing and traffic shaping in ethernet and cellular data networks. The leaky bucket algorithm finds applications in various scenarios, including traffic shaping, rate limiting, and quality of service. Use Of Leaky Bucket Algorithm.
From www.slideserve.com
PPT Chapter 13 PowerPoint Presentation, free download ID3009018 Use Of Leaky Bucket Algorithm The leaky bucket algorithm is designed to handle bursty data traffic by allowing packets to flow at a regulated rate, which helps maintain consistent. In this blog post, we’ll delve. One of the most effective ways to control congestion is trying to reduce the load that transport layer is placing on the network. The leaky bucket is used to implement. Use Of Leaky Bucket Algorithm.
From awstip.com
AWS CDK & Leaky Bucket Manage Traffic Congestion AWS Tip Use Of Leaky Bucket Algorithm In this blog post, we’ll delve. Enter the leaky bucket algorithm — a simple yet effective strategy for traffic shaping and rate limiting. The leaky bucket algorithm finds applications in various scenarios, including traffic shaping, rate limiting, and quality of service (qos) management. The leaky bucket algorithm is a method of congestion control where multiple packets are stored temporarily. One. Use Of Leaky Bucket Algorithm.
From www.slideshare.net
Leaky bucket algorithm Use Of Leaky Bucket Algorithm Enter the leaky bucket algorithm — a simple yet effective strategy for traffic shaping and rate limiting. The leaky bucket algorithm finds applications in various scenarios, including traffic shaping, rate limiting, and quality of service (qos) management. The leaky bucket algorithm is a method of congestion control where multiple packets are stored temporarily. In this blog post, we’ll delve. The. Use Of Leaky Bucket Algorithm.
From www.youtube.com
Leaky Bucket vs Token Bucket Algorithm Leaky Bucket and Token Bucket Use Of Leaky Bucket Algorithm The leaky bucket algorithm is designed to handle bursty data traffic by allowing packets to flow at a regulated rate, which helps maintain consistent. One of the most effective ways to control congestion is trying to reduce the load that transport layer is placing on the network. It is commonly used in network environments to regulate data flow, prevent congestion,. Use Of Leaky Bucket Algorithm.
From www.youtube.com
Leaky Bucket Algorithm Token Bucket Algorithm Leaky Bucket Vs Token Use Of Leaky Bucket Algorithm It is commonly used in network environments to regulate data flow, prevent congestion, and ensure fair resource allocation. In this blog post, we’ll delve. The leaky bucket is used to implement traffic policing and traffic shaping in ethernet and cellular data networks. Enter the leaky bucket algorithm — a simple yet effective strategy for traffic shaping and rate limiting. The. Use Of Leaky Bucket Algorithm.
From www.researchgate.net
Algorithm to Implement the Leaky Bucket and the Token Bucket Download Use Of Leaky Bucket Algorithm The leaky bucket is used to implement traffic policing and traffic shaping in ethernet and cellular data networks. The leaky bucket algorithm finds applications in various scenarios, including traffic shaping, rate limiting, and quality of service (qos) management. The leaky bucket algorithm is designed to handle bursty data traffic by allowing packets to flow at a regulated rate, which helps. Use Of Leaky Bucket Algorithm.
From www.slideserve.com
PPT Quality of Service Support PowerPoint Presentation, free download Use Of Leaky Bucket Algorithm The leaky bucket algorithm finds applications in various scenarios, including traffic shaping, rate limiting, and quality of service (qos) management. Enter the leaky bucket algorithm — a simple yet effective strategy for traffic shaping and rate limiting. One of the most effective ways to control congestion is trying to reduce the load that transport layer is placing on the network.. Use Of Leaky Bucket Algorithm.
From api7.ai
How to Deal with Bursty Traffic Leaky Bucket and Token Bucket Use Of Leaky Bucket Algorithm The leaky bucket algorithm finds applications in various scenarios, including traffic shaping, rate limiting, and quality of service (qos) management. Enter the leaky bucket algorithm — a simple yet effective strategy for traffic shaping and rate limiting. One of the most effective ways to control congestion is trying to reduce the load that transport layer is placing on the network.. Use Of Leaky Bucket Algorithm.
From www.slideserve.com
PPT Leaky Bucket Algorithm PowerPoint Presentation, free download Use Of Leaky Bucket Algorithm The leaky bucket algorithm is a method of congestion control where multiple packets are stored temporarily. Enter the leaky bucket algorithm — a simple yet effective strategy for traffic shaping and rate limiting. The leaky bucket is used to implement traffic policing and traffic shaping in ethernet and cellular data networks. It is commonly used in network environments to regulate. Use Of Leaky Bucket Algorithm.
From www.studypool.com
SOLUTION Leaky Bucket Algorithm C Program Studypool Use Of Leaky Bucket Algorithm The leaky bucket algorithm is designed to handle bursty data traffic by allowing packets to flow at a regulated rate, which helps maintain consistent. The leaky bucket algorithm finds applications in various scenarios, including traffic shaping, rate limiting, and quality of service (qos) management. The leaky bucket algorithm is a method of congestion control where multiple packets are stored temporarily.. Use Of Leaky Bucket Algorithm.
From www.youtube.com
congestion control algorithm Leaky Bucket Algorithm (open loop and Use Of Leaky Bucket Algorithm In this blog post, we’ll delve. One of the most effective ways to control congestion is trying to reduce the load that transport layer is placing on the network. It is commonly used in network environments to regulate data flow, prevent congestion, and ensure fair resource allocation. The leaky bucket algorithm is designed to handle bursty data traffic by allowing. Use Of Leaky Bucket Algorithm.
From www.rdiachenko.com
Exploring and Implementing the Leaky Bucket Rate Limiting Algorithm Use Of Leaky Bucket Algorithm In this blog post, we’ll delve. One of the most effective ways to control congestion is trying to reduce the load that transport layer is placing on the network. The leaky bucket algorithm finds applications in various scenarios, including traffic shaping, rate limiting, and quality of service (qos) management. Enter the leaky bucket algorithm — a simple yet effective strategy. Use Of Leaky Bucket Algorithm.
From www.slideserve.com
PPT Chapter 13 PowerPoint Presentation, free download ID569119 Use Of Leaky Bucket Algorithm One of the most effective ways to control congestion is trying to reduce the load that transport layer is placing on the network. The leaky bucket is used to implement traffic policing and traffic shaping in ethernet and cellular data networks. Enter the leaky bucket algorithm — a simple yet effective strategy for traffic shaping and rate limiting. The leaky. Use Of Leaky Bucket Algorithm.
From www.youtube.com
Leaky bucket and Token bucket with GATE PYQs. Clear Explanation YouTube Use Of Leaky Bucket Algorithm It is commonly used in network environments to regulate data flow, prevent congestion, and ensure fair resource allocation. The leaky bucket algorithm is designed to handle bursty data traffic by allowing packets to flow at a regulated rate, which helps maintain consistent. The leaky bucket algorithm finds applications in various scenarios, including traffic shaping, rate limiting, and quality of service. Use Of Leaky Bucket Algorithm.
From www.scaler.com
Leaky Bucket Algorithm Scalar Topics Use Of Leaky Bucket Algorithm One of the most effective ways to control congestion is trying to reduce the load that transport layer is placing on the network. The leaky bucket algorithm is a method of congestion control where multiple packets are stored temporarily. The leaky bucket is used to implement traffic policing and traffic shaping in ethernet and cellular data networks. The leaky bucket. Use Of Leaky Bucket Algorithm.
From www.slideserve.com
PPT Bandwidth Management PowerPoint Presentation, free download ID Use Of Leaky Bucket Algorithm The leaky bucket algorithm finds applications in various scenarios, including traffic shaping, rate limiting, and quality of service (qos) management. The leaky bucket algorithm is designed to handle bursty data traffic by allowing packets to flow at a regulated rate, which helps maintain consistent. Enter the leaky bucket algorithm — a simple yet effective strategy for traffic shaping and rate. Use Of Leaky Bucket Algorithm.