Email Harvesting Attack . When spammers want to send out a designated message, they obviously need an audience to send to. Given how both users and email providers have gotten smarter about spam over the years, a successful spam campaign needs to get past the defenses set up against it. credential harvesting is a cyberattack technique where cybercriminals gather user credentials — such as user. credential harvesting is an approach hackers use to attack an organization and get access to its. what is email harvesting? email harvesting involves gathering email addresses from various sources without permission. do you use email in your business?
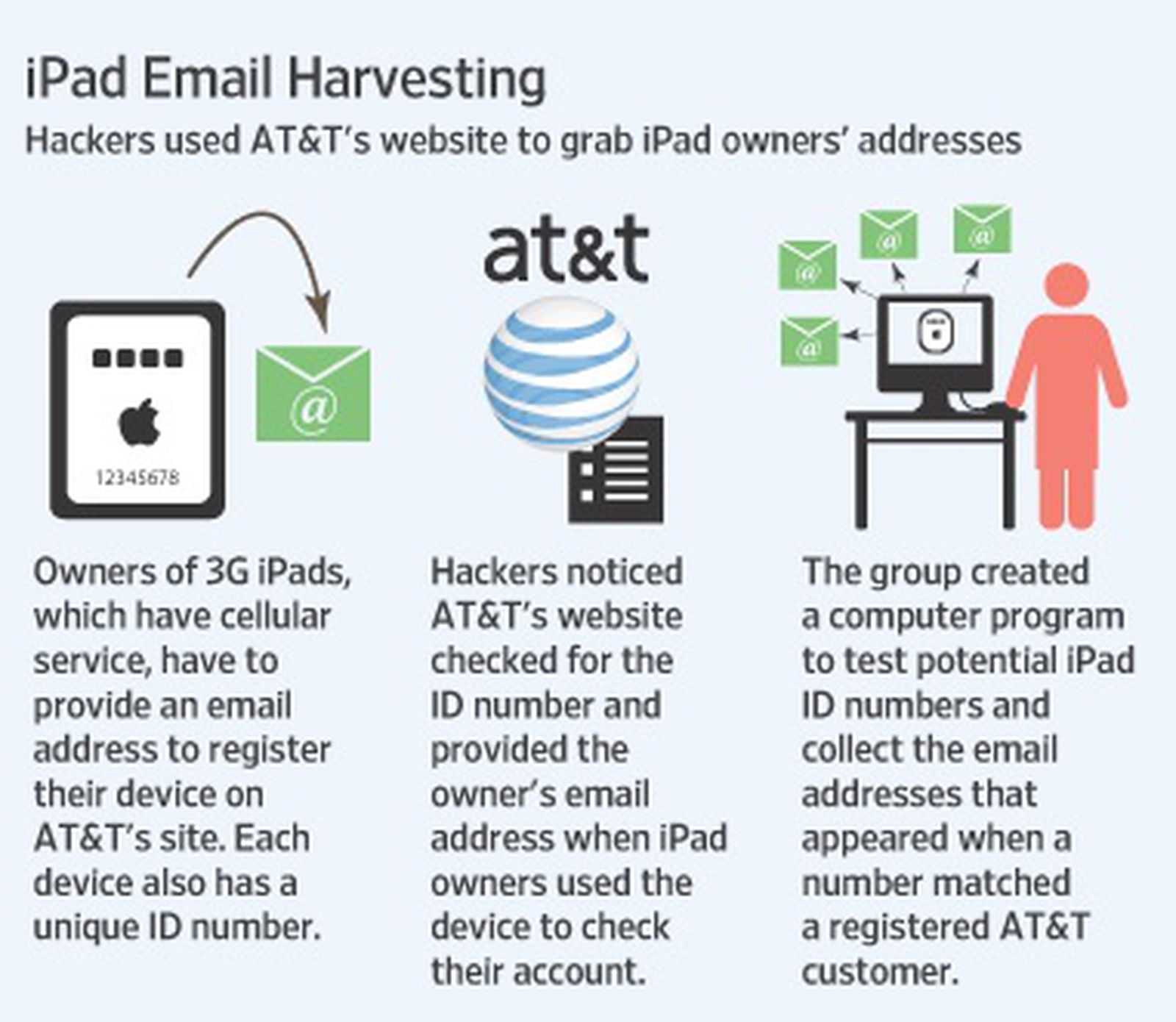
from www.macrumors.com
email harvesting involves gathering email addresses from various sources without permission. Given how both users and email providers have gotten smarter about spam over the years, a successful spam campaign needs to get past the defenses set up against it. what is email harvesting? do you use email in your business? When spammers want to send out a designated message, they obviously need an audience to send to. credential harvesting is a cyberattack technique where cybercriminals gather user credentials — such as user. credential harvesting is an approach hackers use to attack an organization and get access to its.
FBI Investigating AT&T iPad 3G Security Breach MacRumors
Email Harvesting Attack credential harvesting is an approach hackers use to attack an organization and get access to its. what is email harvesting? do you use email in your business? email harvesting involves gathering email addresses from various sources without permission. When spammers want to send out a designated message, they obviously need an audience to send to. credential harvesting is a cyberattack technique where cybercriminals gather user credentials — such as user. credential harvesting is an approach hackers use to attack an organization and get access to its. Given how both users and email providers have gotten smarter about spam over the years, a successful spam campaign needs to get past the defenses set up against it.
From www.interwijs.nl
Bescherm je emailadres tegen email harvesting Interwijs B.V. Email Harvesting Attack credential harvesting is a cyberattack technique where cybercriminals gather user credentials — such as user. credential harvesting is an approach hackers use to attack an organization and get access to its. what is email harvesting? When spammers want to send out a designated message, they obviously need an audience to send to. email harvesting involves gathering. Email Harvesting Attack.
From ironscales.com
Analysis of a Credential Harvesting Attack Blog IRONSCALES Email Harvesting Attack do you use email in your business? When spammers want to send out a designated message, they obviously need an audience to send to. email harvesting involves gathering email addresses from various sources without permission. Given how both users and email providers have gotten smarter about spam over the years, a successful spam campaign needs to get past. Email Harvesting Attack.
From www.macrumors.com
FBI Investigating AT&T iPad 3G Security Breach MacRumors Email Harvesting Attack do you use email in your business? credential harvesting is an approach hackers use to attack an organization and get access to its. what is email harvesting? credential harvesting is a cyberattack technique where cybercriminals gather user credentials — such as user. When spammers want to send out a designated message, they obviously need an audience. Email Harvesting Attack.
From www.interwijs.nl
Bescherm je emailadres tegen email harvesting Interwijs B.V. Email Harvesting Attack credential harvesting is a cyberattack technique where cybercriminals gather user credentials — such as user. Given how both users and email providers have gotten smarter about spam over the years, a successful spam campaign needs to get past the defenses set up against it. do you use email in your business? When spammers want to send out a. Email Harvesting Attack.
From simplybuiltsites.com
Security Alert New Phishing Email Scam Simply Built Email Harvesting Attack email harvesting involves gathering email addresses from various sources without permission. Given how both users and email providers have gotten smarter about spam over the years, a successful spam campaign needs to get past the defenses set up against it. do you use email in your business? When spammers want to send out a designated message, they obviously. Email Harvesting Attack.
From www.wallarm.com
What is Credential Stuffing Attack Definition & Prevention ️ Email Harvesting Attack email harvesting involves gathering email addresses from various sources without permission. credential harvesting is a cyberattack technique where cybercriminals gather user credentials — such as user. credential harvesting is an approach hackers use to attack an organization and get access to its. When spammers want to send out a designated message, they obviously need an audience to. Email Harvesting Attack.
From techgenix.com
How Can You Protect Your Business from Credential Harvesting Attacks? Email Harvesting Attack do you use email in your business? email harvesting involves gathering email addresses from various sources without permission. what is email harvesting? credential harvesting is a cyberattack technique where cybercriminals gather user credentials — such as user. credential harvesting is an approach hackers use to attack an organization and get access to its. When spammers. Email Harvesting Attack.
From www.techradar.com
Email eradication and security How Facebook wants to change the way Email Harvesting Attack email harvesting involves gathering email addresses from various sources without permission. credential harvesting is a cyberattack technique where cybercriminals gather user credentials — such as user. When spammers want to send out a designated message, they obviously need an audience to send to. Given how both users and email providers have gotten smarter about spam over the years,. Email Harvesting Attack.
From cyware.com
Credential Harvesting Attack Uses Legitimate Video Sharing Platform to Email Harvesting Attack what is email harvesting? email harvesting involves gathering email addresses from various sources without permission. Given how both users and email providers have gotten smarter about spam over the years, a successful spam campaign needs to get past the defenses set up against it. credential harvesting is an approach hackers use to attack an organization and get. Email Harvesting Attack.
From getwemail.io
Email Harvesting Everything You Need to Know About It weMail Email Harvesting Attack email harvesting involves gathering email addresses from various sources without permission. what is email harvesting? When spammers want to send out a designated message, they obviously need an audience to send to. Given how both users and email providers have gotten smarter about spam over the years, a successful spam campaign needs to get past the defenses set. Email Harvesting Attack.
From www.trendmicro.com
Phishing Campaign Steals Credentials Via Watering Hole Trend Micro (US) Email Harvesting Attack Given how both users and email providers have gotten smarter about spam over the years, a successful spam campaign needs to get past the defenses set up against it. credential harvesting is a cyberattack technique where cybercriminals gather user credentials — such as user. credential harvesting is an approach hackers use to attack an organization and get access. Email Harvesting Attack.
From contentsecurity.com.au
Ransomware, phishing & compromised credentials perpetual cyber Email Harvesting Attack credential harvesting is an approach hackers use to attack an organization and get access to its. what is email harvesting? do you use email in your business? credential harvesting is a cyberattack technique where cybercriminals gather user credentials — such as user. When spammers want to send out a designated message, they obviously need an audience. Email Harvesting Attack.
From www.ionos.at
EmailAdresse Ihrer site vor Spam schützen IONOS AT Email Harvesting Attack When spammers want to send out a designated message, they obviously need an audience to send to. Given how both users and email providers have gotten smarter about spam over the years, a successful spam campaign needs to get past the defenses set up against it. email harvesting involves gathering email addresses from various sources without permission. do. Email Harvesting Attack.
From twitter.com
andrew kaczynski on Twitter "Mail harvesting also known as people voting" Email Harvesting Attack When spammers want to send out a designated message, they obviously need an audience to send to. credential harvesting is a cyberattack technique where cybercriminals gather user credentials — such as user. what is email harvesting? do you use email in your business? Given how both users and email providers have gotten smarter about spam over the. Email Harvesting Attack.
From getwemail.io
Email Harvesting Everything You Need to Know About It weMail Email Harvesting Attack Given how both users and email providers have gotten smarter about spam over the years, a successful spam campaign needs to get past the defenses set up against it. what is email harvesting? When spammers want to send out a designated message, they obviously need an audience to send to. credential harvesting is a cyberattack technique where cybercriminals. Email Harvesting Attack.
From www.yanmar.com
「ヤンマー大玉トマト収穫ロボット」試作機を「2022国際ロボット展」へ出展|2022年|ニュース|ヤンマー Email Harvesting Attack When spammers want to send out a designated message, they obviously need an audience to send to. what is email harvesting? do you use email in your business? Given how both users and email providers have gotten smarter about spam over the years, a successful spam campaign needs to get past the defenses set up against it. . Email Harvesting Attack.
From www.cayosoft.com
Strategic Guide for Active Directory Security Email Harvesting Attack Given how both users and email providers have gotten smarter about spam over the years, a successful spam campaign needs to get past the defenses set up against it. what is email harvesting? do you use email in your business? credential harvesting is a cyberattack technique where cybercriminals gather user credentials — such as user. email. Email Harvesting Attack.
From www.trendmicro.com
TeamTNT’s Extended Credential Harvester Targets Cloud Services, Other Email Harvesting Attack Given how both users and email providers have gotten smarter about spam over the years, a successful spam campaign needs to get past the defenses set up against it. credential harvesting is an approach hackers use to attack an organization and get access to its. what is email harvesting? email harvesting involves gathering email addresses from various. Email Harvesting Attack.
From www.cloudflare.com
What is a phishing attack? Cloudflare Email Harvesting Attack do you use email in your business? email harvesting involves gathering email addresses from various sources without permission. When spammers want to send out a designated message, they obviously need an audience to send to. Given how both users and email providers have gotten smarter about spam over the years, a successful spam campaign needs to get past. Email Harvesting Attack.
From www.lumificyber.com
Credential Harvesting Attack Examples, Phishing Emails SOC Method Email Harvesting Attack do you use email in your business? what is email harvesting? credential harvesting is a cyberattack technique where cybercriminals gather user credentials — such as user. email harvesting involves gathering email addresses from various sources without permission. Given how both users and email providers have gotten smarter about spam over the years, a successful spam campaign. Email Harvesting Attack.
From timesofindia.indiatimes.com
Cyber Crooks Harvesting Data To Decrypt Later Hyderabad News Times Email Harvesting Attack do you use email in your business? email harvesting involves gathering email addresses from various sources without permission. what is email harvesting? Given how both users and email providers have gotten smarter about spam over the years, a successful spam campaign needs to get past the defenses set up against it. credential harvesting is an approach. Email Harvesting Attack.
From getwemail.io
Email Harvesting Everything You Need to Know About It weMail Email Harvesting Attack Given how both users and email providers have gotten smarter about spam over the years, a successful spam campaign needs to get past the defenses set up against it. credential harvesting is an approach hackers use to attack an organization and get access to its. what is email harvesting? credential harvesting is a cyberattack technique where cybercriminals. Email Harvesting Attack.
From getwemail.io
Email Harvesting Everything You Need to Know About It weMail Email Harvesting Attack email harvesting involves gathering email addresses from various sources without permission. do you use email in your business? When spammers want to send out a designated message, they obviously need an audience to send to. credential harvesting is an approach hackers use to attack an organization and get access to its. credential harvesting is a cyberattack. Email Harvesting Attack.
From www.valimail.com
7+ Phishing Prevention Best Practices in 2023 Valimail Email Harvesting Attack do you use email in your business? credential harvesting is a cyberattack technique where cybercriminals gather user credentials — such as user. email harvesting involves gathering email addresses from various sources without permission. credential harvesting is an approach hackers use to attack an organization and get access to its. what is email harvesting? When spammers. Email Harvesting Attack.
From www.hoxhunt.com
Embedded Email Credential Harvesting Hoxhunt Email Harvesting Attack credential harvesting is a cyberattack technique where cybercriminals gather user credentials — such as user. what is email harvesting? do you use email in your business? When spammers want to send out a designated message, they obviously need an audience to send to. credential harvesting is an approach hackers use to attack an organization and get. Email Harvesting Attack.
From getwemail.io
Email Harvesting Everything You Need to Know About It weMail Email Harvesting Attack Given how both users and email providers have gotten smarter about spam over the years, a successful spam campaign needs to get past the defenses set up against it. credential harvesting is an approach hackers use to attack an organization and get access to its. do you use email in your business? credential harvesting is a cyberattack. Email Harvesting Attack.
From www.youtube.com
Passive Reconnaissance Email Harvesting With theHarvester YouTube Email Harvesting Attack credential harvesting is an approach hackers use to attack an organization and get access to its. Given how both users and email providers have gotten smarter about spam over the years, a successful spam campaign needs to get past the defenses set up against it. email harvesting involves gathering email addresses from various sources without permission. credential. Email Harvesting Attack.
From getwemail.io
Email Harvesting Everything You Need to Know About It weMail Email Harvesting Attack Given how both users and email providers have gotten smarter about spam over the years, a successful spam campaign needs to get past the defenses set up against it. credential harvesting is an approach hackers use to attack an organization and get access to its. do you use email in your business? email harvesting involves gathering email. Email Harvesting Attack.
From getwemail.io
Email Harvesting Everything You Need to Know About It weMail Email Harvesting Attack what is email harvesting? Given how both users and email providers have gotten smarter about spam over the years, a successful spam campaign needs to get past the defenses set up against it. credential harvesting is a cyberattack technique where cybercriminals gather user credentials — such as user. When spammers want to send out a designated message, they. Email Harvesting Attack.
From www.slideserve.com
PPT 1What Is Email Scraping Or Email Harvesting PowerPoint Email Harvesting Attack email harvesting involves gathering email addresses from various sources without permission. credential harvesting is a cyberattack technique where cybercriminals gather user credentials — such as user. do you use email in your business? Given how both users and email providers have gotten smarter about spam over the years, a successful spam campaign needs to get past the. Email Harvesting Attack.
From www.techradar.com
5 steps to take if your business gets hacked TechRadar Email Harvesting Attack what is email harvesting? credential harvesting is a cyberattack technique where cybercriminals gather user credentials — such as user. Given how both users and email providers have gotten smarter about spam over the years, a successful spam campaign needs to get past the defenses set up against it. credential harvesting is an approach hackers use to attack. Email Harvesting Attack.
From datadome.co
What is Credential Harvesting? Examples & Prevention Methods Email Harvesting Attack When spammers want to send out a designated message, they obviously need an audience to send to. email harvesting involves gathering email addresses from various sources without permission. do you use email in your business? credential harvesting is a cyberattack technique where cybercriminals gather user credentials — such as user. what is email harvesting? Given how. Email Harvesting Attack.
From emotionstudios.net
"Get that bot away from me!" solutions to stop email harvesting Email Harvesting Attack what is email harvesting? When spammers want to send out a designated message, they obviously need an audience to send to. do you use email in your business? Given how both users and email providers have gotten smarter about spam over the years, a successful spam campaign needs to get past the defenses set up against it. . Email Harvesting Attack.
From pc-solucion.es
Email Harvesting Email Harvesting Attack email harvesting involves gathering email addresses from various sources without permission. do you use email in your business? what is email harvesting? credential harvesting is an approach hackers use to attack an organization and get access to its. When spammers want to send out a designated message, they obviously need an audience to send to. Given. Email Harvesting Attack.
From www.pearsonitcertification.com
Researching Attack Vectors and Performing Attacks on Cloud Technologies Email Harvesting Attack email harvesting involves gathering email addresses from various sources without permission. what is email harvesting? Given how both users and email providers have gotten smarter about spam over the years, a successful spam campaign needs to get past the defenses set up against it. When spammers want to send out a designated message, they obviously need an audience. Email Harvesting Attack.