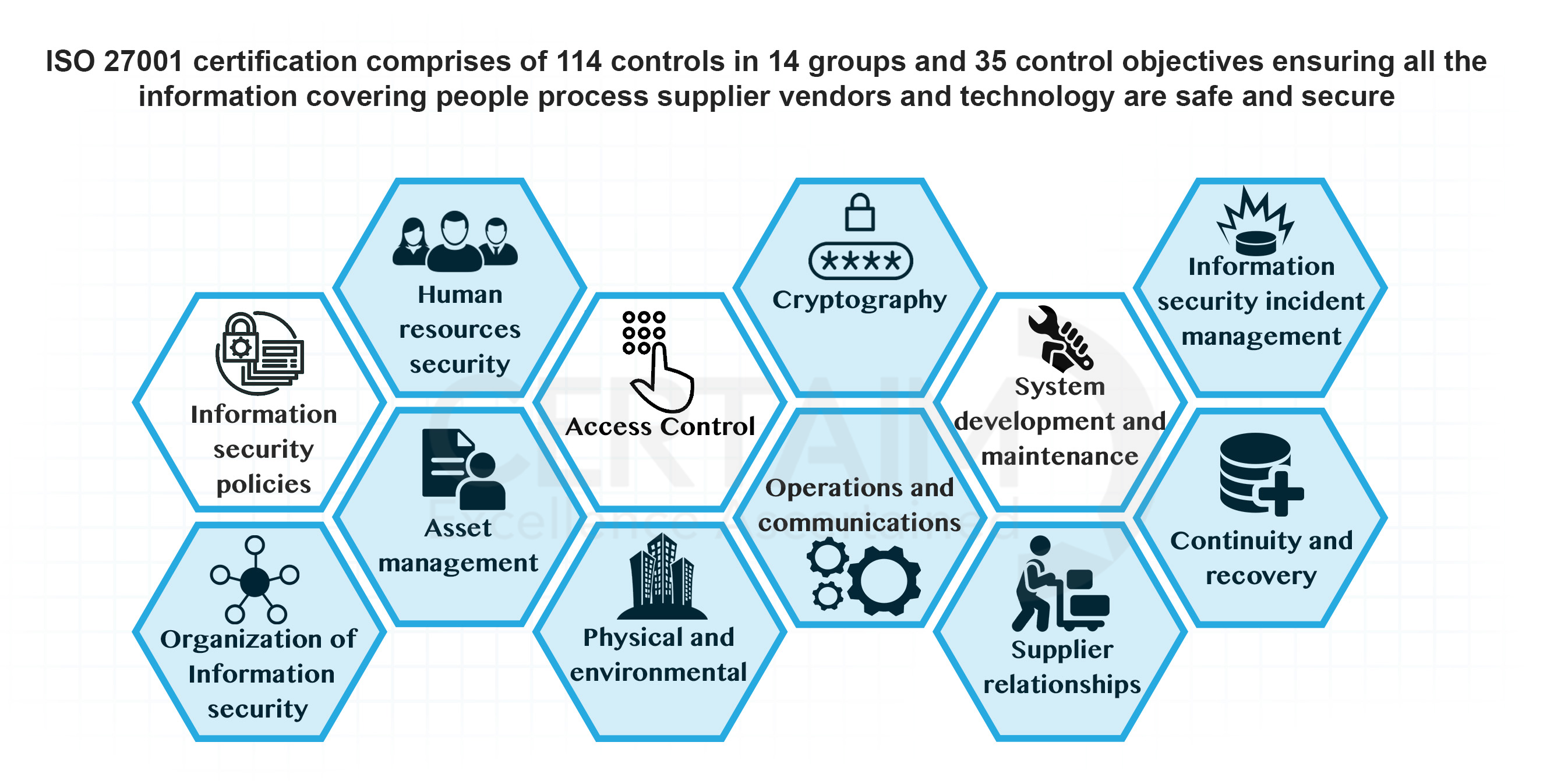
Physical Security Policy Iso 27001 . It ensures that organizations protect their information assets from digital, physical, and environmental threats. The physical protection policy in iso 27001 outlines measures and procedures to safeguard physical assets and facilities that house an organization's information. Information assets exist in physical space, leaving them vulnerable despite the most robust cyber security measures. Implementing and maintaining information security in an organization depends in large part on physical and environmental security. The iso 27001 standard includes. Iso 27001 annex a.11, titled “physical and environmental security,” is a crucial component of the iso/iec 27001 standard, which focuses on information security. Iso 27001 physical security ensures comprehensive protection for your organisation's assets. It covers key topics such as physical security, employee access, network access control, visitor access, etc. This blog covers the crucial aspects of iso 27001 physical security, covering. The physical and environmental security policy primarily lays emphasis on the prevention of unauthorized physical access to the organization’s data as well as its data processing facilities. Physical security is a key part of iso 27001. Protect your sensitive information and critical assets with iso 27001's robust physical and environmental security measures.
from mungfali.com
It ensures that organizations protect their information assets from digital, physical, and environmental threats. Implementing and maintaining information security in an organization depends in large part on physical and environmental security. Iso 27001 annex a.11, titled “physical and environmental security,” is a crucial component of the iso/iec 27001 standard, which focuses on information security. This blog covers the crucial aspects of iso 27001 physical security, covering. The physical and environmental security policy primarily lays emphasis on the prevention of unauthorized physical access to the organization’s data as well as its data processing facilities. Iso 27001 physical security ensures comprehensive protection for your organisation's assets. Physical security is a key part of iso 27001. Protect your sensitive information and critical assets with iso 27001's robust physical and environmental security measures. Information assets exist in physical space, leaving them vulnerable despite the most robust cyber security measures. It covers key topics such as physical security, employee access, network access control, visitor access, etc.
ISO 27001 RoadMap
Physical Security Policy Iso 27001 Protect your sensitive information and critical assets with iso 27001's robust physical and environmental security measures. It covers key topics such as physical security, employee access, network access control, visitor access, etc. Iso 27001 annex a.11, titled “physical and environmental security,” is a crucial component of the iso/iec 27001 standard, which focuses on information security. It ensures that organizations protect their information assets from digital, physical, and environmental threats. Implementing and maintaining information security in an organization depends in large part on physical and environmental security. Information assets exist in physical space, leaving them vulnerable despite the most robust cyber security measures. The physical protection policy in iso 27001 outlines measures and procedures to safeguard physical assets and facilities that house an organization's information. This blog covers the crucial aspects of iso 27001 physical security, covering. Physical security is a key part of iso 27001. The iso 27001 standard includes. Protect your sensitive information and critical assets with iso 27001's robust physical and environmental security measures. Iso 27001 physical security ensures comprehensive protection for your organisation's assets. The physical and environmental security policy primarily lays emphasis on the prevention of unauthorized physical access to the organization’s data as well as its data processing facilities.
From spectralops.io
ISO/IEC 27001 Compliance SelfAssessment The Ultimate ISO 27001 Physical Security Policy Iso 27001 Iso 27001 annex a.11, titled “physical and environmental security,” is a crucial component of the iso/iec 27001 standard, which focuses on information security. Physical security is a key part of iso 27001. The iso 27001 standard includes. Information assets exist in physical space, leaving them vulnerable despite the most robust cyber security measures. This blog covers the crucial aspects of. Physical Security Policy Iso 27001.
From www.it-procedure-template.com
Physical Security Policy IT Procedure Template Physical Security Policy Iso 27001 The physical protection policy in iso 27001 outlines measures and procedures to safeguard physical assets and facilities that house an organization's information. The physical and environmental security policy primarily lays emphasis on the prevention of unauthorized physical access to the organization’s data as well as its data processing facilities. This blog covers the crucial aspects of iso 27001 physical security,. Physical Security Policy Iso 27001.
From iso27001.institute
Physical And Environmental Security Policy ISO 27001 Institute Physical Security Policy Iso 27001 The iso 27001 standard includes. The physical protection policy in iso 27001 outlines measures and procedures to safeguard physical assets and facilities that house an organization's information. Information assets exist in physical space, leaving them vulnerable despite the most robust cyber security measures. This blog covers the crucial aspects of iso 27001 physical security, covering. Iso 27001 annex a.11, titled. Physical Security Policy Iso 27001.
From info-savvy.com
ISO 27001 Annex A.11 Physical and Environmental Security Infosavvy Physical Security Policy Iso 27001 It ensures that organizations protect their information assets from digital, physical, and environmental threats. Iso 27001 annex a.11, titled “physical and environmental security,” is a crucial component of the iso/iec 27001 standard, which focuses on information security. Implementing and maintaining information security in an organization depends in large part on physical and environmental security. Physical security is a key part. Physical Security Policy Iso 27001.
From iso-docs.com
ISO 270012022 Physical Protection Policy Template Download ISO Physical Security Policy Iso 27001 Implementing and maintaining information security in an organization depends in large part on physical and environmental security. The physical and environmental security policy primarily lays emphasis on the prevention of unauthorized physical access to the organization’s data as well as its data processing facilities. It ensures that organizations protect their information assets from digital, physical, and environmental threats. Protect your. Physical Security Policy Iso 27001.
From hightable.io
ISO 27001 Physical and Environmental Security Policy Template Physical Security Policy Iso 27001 It ensures that organizations protect their information assets from digital, physical, and environmental threats. It covers key topics such as physical security, employee access, network access control, visitor access, etc. This blog covers the crucial aspects of iso 27001 physical security, covering. Iso 27001 annex a.11, titled “physical and environmental security,” is a crucial component of the iso/iec 27001 standard,. Physical Security Policy Iso 27001.
From www.kolide.com
The Business Guide to ISO 27001 Compliance and Certification Physical Security Policy Iso 27001 It covers key topics such as physical security, employee access, network access control, visitor access, etc. Implementing and maintaining information security in an organization depends in large part on physical and environmental security. Iso 27001 annex a.11, titled “physical and environmental security,” is a crucial component of the iso/iec 27001 standard, which focuses on information security. Protect your sensitive information. Physical Security Policy Iso 27001.
From www.complyassistant.com
ISO 27001 Compliance Software Userfriendly Compliance Software Physical Security Policy Iso 27001 Protect your sensitive information and critical assets with iso 27001's robust physical and environmental security measures. Implementing and maintaining information security in an organization depends in large part on physical and environmental security. Information assets exist in physical space, leaving them vulnerable despite the most robust cyber security measures. Iso 27001 physical security ensures comprehensive protection for your organisation's assets.. Physical Security Policy Iso 27001.
From isologyhub.com
ISO 27001 Physical Security Controls Course ISOlogy Hub Physical Security Policy Iso 27001 This blog covers the crucial aspects of iso 27001 physical security, covering. The physical and environmental security policy primarily lays emphasis on the prevention of unauthorized physical access to the organization’s data as well as its data processing facilities. It covers key topics such as physical security, employee access, network access control, visitor access, etc. Iso 27001 physical security ensures. Physical Security Policy Iso 27001.
From allbusinesstemplates.blogspot.com
Physical Security Policy Iso 27001 All Business Templates Physical Security Policy Iso 27001 Physical security is a key part of iso 27001. Protect your sensitive information and critical assets with iso 27001's robust physical and environmental security measures. The physical and environmental security policy primarily lays emphasis on the prevention of unauthorized physical access to the organization’s data as well as its data processing facilities. Iso 27001 physical security ensures comprehensive protection for. Physical Security Policy Iso 27001.
From inverifi.com
ISO 27001 Controls Physical Security Inverifi Physical Security Policy Iso 27001 Iso 27001 annex a.11, titled “physical and environmental security,” is a crucial component of the iso/iec 27001 standard, which focuses on information security. It ensures that organizations protect their information assets from digital, physical, and environmental threats. Protect your sensitive information and critical assets with iso 27001's robust physical and environmental security measures. The physical and environmental security policy primarily. Physical Security Policy Iso 27001.
From sabtrax.ca
How to Implement an ISO 27001 Information Security Management System Physical Security Policy Iso 27001 It covers key topics such as physical security, employee access, network access control, visitor access, etc. It ensures that organizations protect their information assets from digital, physical, and environmental threats. Iso 27001 physical security ensures comprehensive protection for your organisation's assets. The physical and environmental security policy primarily lays emphasis on the prevention of unauthorized physical access to the organization’s. Physical Security Policy Iso 27001.
From data1.skinnyms.com
Iso 27001 Security Policy Template Physical Security Policy Iso 27001 It covers key topics such as physical security, employee access, network access control, visitor access, etc. It ensures that organizations protect their information assets from digital, physical, and environmental threats. Iso 27001 physical security ensures comprehensive protection for your organisation's assets. Protect your sensitive information and critical assets with iso 27001's robust physical and environmental security measures. The physical and. Physical Security Policy Iso 27001.
From iso-docs.com
ISO 270012022 Physical Protection Policy Template Download ISO Physical Security Policy Iso 27001 It ensures that organizations protect their information assets from digital, physical, and environmental threats. Physical security is a key part of iso 27001. The physical and environmental security policy primarily lays emphasis on the prevention of unauthorized physical access to the organization’s data as well as its data processing facilities. Iso 27001 physical security ensures comprehensive protection for your organisation's. Physical Security Policy Iso 27001.
From www.pivotpointsecurity.com
ISO 27001 Security Policies What They Are? Physical Security Policy Iso 27001 This blog covers the crucial aspects of iso 27001 physical security, covering. Protect your sensitive information and critical assets with iso 27001's robust physical and environmental security measures. It covers key topics such as physical security, employee access, network access control, visitor access, etc. Iso 27001 annex a.11, titled “physical and environmental security,” is a crucial component of the iso/iec. Physical Security Policy Iso 27001.
From sprinto.com
Complete List of ISO 27001 Policies Sprinto Physical Security Policy Iso 27001 Information assets exist in physical space, leaving them vulnerable despite the most robust cyber security measures. The physical protection policy in iso 27001 outlines measures and procedures to safeguard physical assets and facilities that house an organization's information. Iso 27001 physical security ensures comprehensive protection for your organisation's assets. This blog covers the crucial aspects of iso 27001 physical security,. Physical Security Policy Iso 27001.
From ezddies.com
ISO 27001 Controls Explained A Detailed Guide Secureframe (2022) Physical Security Policy Iso 27001 Iso 27001 annex a.11, titled “physical and environmental security,” is a crucial component of the iso/iec 27001 standard, which focuses on information security. This blog covers the crucial aspects of iso 27001 physical security, covering. The physical protection policy in iso 27001 outlines measures and procedures to safeguard physical assets and facilities that house an organization's information. Iso 27001 physical. Physical Security Policy Iso 27001.
From advisera.com
ISO 27001 Information Security Policy How to write it yourself Physical Security Policy Iso 27001 It ensures that organizations protect their information assets from digital, physical, and environmental threats. The physical protection policy in iso 27001 outlines measures and procedures to safeguard physical assets and facilities that house an organization's information. This blog covers the crucial aspects of iso 27001 physical security, covering. Physical security is a key part of iso 27001. Implementing and maintaining. Physical Security Policy Iso 27001.
From www.kolide.com
The Business Guide to ISO 27001 Compliance and Certification Physical Security Policy Iso 27001 It ensures that organizations protect their information assets from digital, physical, and environmental threats. The physical protection policy in iso 27001 outlines measures and procedures to safeguard physical assets and facilities that house an organization's information. Iso 27001 annex a.11, titled “physical and environmental security,” is a crucial component of the iso/iec 27001 standard, which focuses on information security. The. Physical Security Policy Iso 27001.
From positivethinking.tech
ISO 27001 Certification Why your organization should implement it? Physical Security Policy Iso 27001 The iso 27001 standard includes. Iso 27001 annex a.11, titled “physical and environmental security,” is a crucial component of the iso/iec 27001 standard, which focuses on information security. The physical and environmental security policy primarily lays emphasis on the prevention of unauthorized physical access to the organization’s data as well as its data processing facilities. Iso 27001 physical security ensures. Physical Security Policy Iso 27001.
From allbusinesstemplates.blogspot.com
Physical Security Policy Iso 27001 All Business Templates Physical Security Policy Iso 27001 Information assets exist in physical space, leaving them vulnerable despite the most robust cyber security measures. It covers key topics such as physical security, employee access, network access control, visitor access, etc. Iso 27001 annex a.11, titled “physical and environmental security,” is a crucial component of the iso/iec 27001 standard, which focuses on information security. Implementing and maintaining information security. Physical Security Policy Iso 27001.
From www.etsy.com
Easy Physical Security Policy Template Cybersecurity for Your Business Physical Security Policy Iso 27001 Iso 27001 physical security ensures comprehensive protection for your organisation's assets. Implementing and maintaining information security in an organization depends in large part on physical and environmental security. Physical security is a key part of iso 27001. The physical and environmental security policy primarily lays emphasis on the prevention of unauthorized physical access to the organization’s data as well as. Physical Security Policy Iso 27001.
From inspiredelearning.com
What is ISO27001? Key Considerations for Businesses Physical Security Policy Iso 27001 It ensures that organizations protect their information assets from digital, physical, and environmental threats. Physical security is a key part of iso 27001. Information assets exist in physical space, leaving them vulnerable despite the most robust cyber security measures. The physical and environmental security policy primarily lays emphasis on the prevention of unauthorized physical access to the organization’s data as. Physical Security Policy Iso 27001.
From webframes.org
Iso 27001 Framework Ppt Physical Security Policy Iso 27001 Information assets exist in physical space, leaving them vulnerable despite the most robust cyber security measures. Physical security is a key part of iso 27001. It ensures that organizations protect their information assets from digital, physical, and environmental threats. This blog covers the crucial aspects of iso 27001 physical security, covering. Protect your sensitive information and critical assets with iso. Physical Security Policy Iso 27001.
From cashier.mijndomein.nl
Iso 27001 Security Policy Template Physical Security Policy Iso 27001 The physical protection policy in iso 27001 outlines measures and procedures to safeguard physical assets and facilities that house an organization's information. This blog covers the crucial aspects of iso 27001 physical security, covering. Iso 27001 physical security ensures comprehensive protection for your organisation's assets. The iso 27001 standard includes. It ensures that organizations protect their information assets from digital,. Physical Security Policy Iso 27001.
From www.imsm.com
Does ISO 27001 cover physical security? IMSM PH Physical Security Policy Iso 27001 Iso 27001 annex a.11, titled “physical and environmental security,” is a crucial component of the iso/iec 27001 standard, which focuses on information security. Physical security is a key part of iso 27001. It covers key topics such as physical security, employee access, network access control, visitor access, etc. Iso 27001 physical security ensures comprehensive protection for your organisation's assets. Implementing. Physical Security Policy Iso 27001.
From sprinto.com
Guide to ISO 27001 Annex A Controls (Updated) Sprinto Physical Security Policy Iso 27001 This blog covers the crucial aspects of iso 27001 physical security, covering. The iso 27001 standard includes. It ensures that organizations protect their information assets from digital, physical, and environmental threats. Implementing and maintaining information security in an organization depends in large part on physical and environmental security. Information assets exist in physical space, leaving them vulnerable despite the most. Physical Security Policy Iso 27001.
From hightable.io
ISO 27001 Information Security Policy Template Physical Security Policy Iso 27001 Information assets exist in physical space, leaving them vulnerable despite the most robust cyber security measures. The physical and environmental security policy primarily lays emphasis on the prevention of unauthorized physical access to the organization’s data as well as its data processing facilities. Protect your sensitive information and critical assets with iso 27001's robust physical and environmental security measures. Iso. Physical Security Policy Iso 27001.
From mungfali.com
ISO 27001 RoadMap Physical Security Policy Iso 27001 The physical and environmental security policy primarily lays emphasis on the prevention of unauthorized physical access to the organization’s data as well as its data processing facilities. Protect your sensitive information and critical assets with iso 27001's robust physical and environmental security measures. Iso 27001 annex a.11, titled “physical and environmental security,” is a crucial component of the iso/iec 27001. Physical Security Policy Iso 27001.
From www.douglasthornton.co.uk
ISO 27001 Controls List DTC Consulting Physical Security Policy Iso 27001 It ensures that organizations protect their information assets from digital, physical, and environmental threats. Information assets exist in physical space, leaving them vulnerable despite the most robust cyber security measures. The iso 27001 standard includes. The physical and environmental security policy primarily lays emphasis on the prevention of unauthorized physical access to the organization’s data as well as its data. Physical Security Policy Iso 27001.
From www.imsm.com
Does ISO 27001 cover physical security? IMSM KE Physical Security Policy Iso 27001 It covers key topics such as physical security, employee access, network access control, visitor access, etc. Implementing and maintaining information security in an organization depends in large part on physical and environmental security. Iso 27001 physical security ensures comprehensive protection for your organisation's assets. Physical security is a key part of iso 27001. The physical and environmental security policy primarily. Physical Security Policy Iso 27001.
From iso-docs.com
ISO 270012022 Physical Protection Policy Template Download ISO Physical Security Policy Iso 27001 Implementing and maintaining information security in an organization depends in large part on physical and environmental security. The physical protection policy in iso 27001 outlines measures and procedures to safeguard physical assets and facilities that house an organization's information. It ensures that organizations protect their information assets from digital, physical, and environmental threats. Iso 27001 annex a.11, titled “physical and. Physical Security Policy Iso 27001.
From drata.com
ISO 27001 Controls A Guide to Annex A Drata Physical Security Policy Iso 27001 The physical protection policy in iso 27001 outlines measures and procedures to safeguard physical assets and facilities that house an organization's information. This blog covers the crucial aspects of iso 27001 physical security, covering. It ensures that organizations protect their information assets from digital, physical, and environmental threats. Iso 27001 physical security ensures comprehensive protection for your organisation's assets. The. Physical Security Policy Iso 27001.
From www.scribd.com
ISO 27001 Project Template Pbmnpd (1) Information Security Risk Physical Security Policy Iso 27001 The physical protection policy in iso 27001 outlines measures and procedures to safeguard physical assets and facilities that house an organization's information. Implementing and maintaining information security in an organization depends in large part on physical and environmental security. The iso 27001 standard includes. Physical security is a key part of iso 27001. Iso 27001 physical security ensures comprehensive protection. Physical Security Policy Iso 27001.
From www.vrogue.co
Iso 27001 Cyber Security Framework frames Org vrogue.co Physical Security Policy Iso 27001 Physical security is a key part of iso 27001. Protect your sensitive information and critical assets with iso 27001's robust physical and environmental security measures. It ensures that organizations protect their information assets from digital, physical, and environmental threats. It covers key topics such as physical security, employee access, network access control, visitor access, etc. Iso 27001 physical security ensures. Physical Security Policy Iso 27001.