Data Collection And Risk Management . With bits and bytes being. Safeguard your organization's data assets and enhance your security posture with proven strategies. data risk management roles include: This includes potential threats related to data privacy, data security, compliance risks, and business risks associated with improper data handling. war on data risk management? learn effective data risk management best practices for identifying and mitigating data risks, complying with regulations, and protecting sensitive information. It involves assessing the potential threats to data security and implementing measures to mitigate these risks. data risk management involves the identification, assessment, and mitigation of risks in data collection and. Do you have control over your data or is your data controlling you? By implementing such a framework, organizations can effectively safeguard their valuable information assets, ensuring confidentiality, availability, and integrity. a data risk management framework provides a structured approach to identify, assess, and mitigate risks related to data security, privacy, and integrity. data risk management encompasses the processes, policies, and technologies employed to protect sensitive data from unauthorized access, disclosure, alteration, or destruction. Proactively assessing security risks and vulnerabilities to minimize business risks related to.
from www.secjuice.com
With bits and bytes being. Proactively assessing security risks and vulnerabilities to minimize business risks related to. By implementing such a framework, organizations can effectively safeguard their valuable information assets, ensuring confidentiality, availability, and integrity. learn effective data risk management best practices for identifying and mitigating data risks, complying with regulations, and protecting sensitive information. data risk management encompasses the processes, policies, and technologies employed to protect sensitive data from unauthorized access, disclosure, alteration, or destruction. Do you have control over your data or is your data controlling you? data risk management roles include: This includes potential threats related to data privacy, data security, compliance risks, and business risks associated with improper data handling. Safeguard your organization's data assets and enhance your security posture with proven strategies. a data risk management framework provides a structured approach to identify, assess, and mitigate risks related to data security, privacy, and integrity.
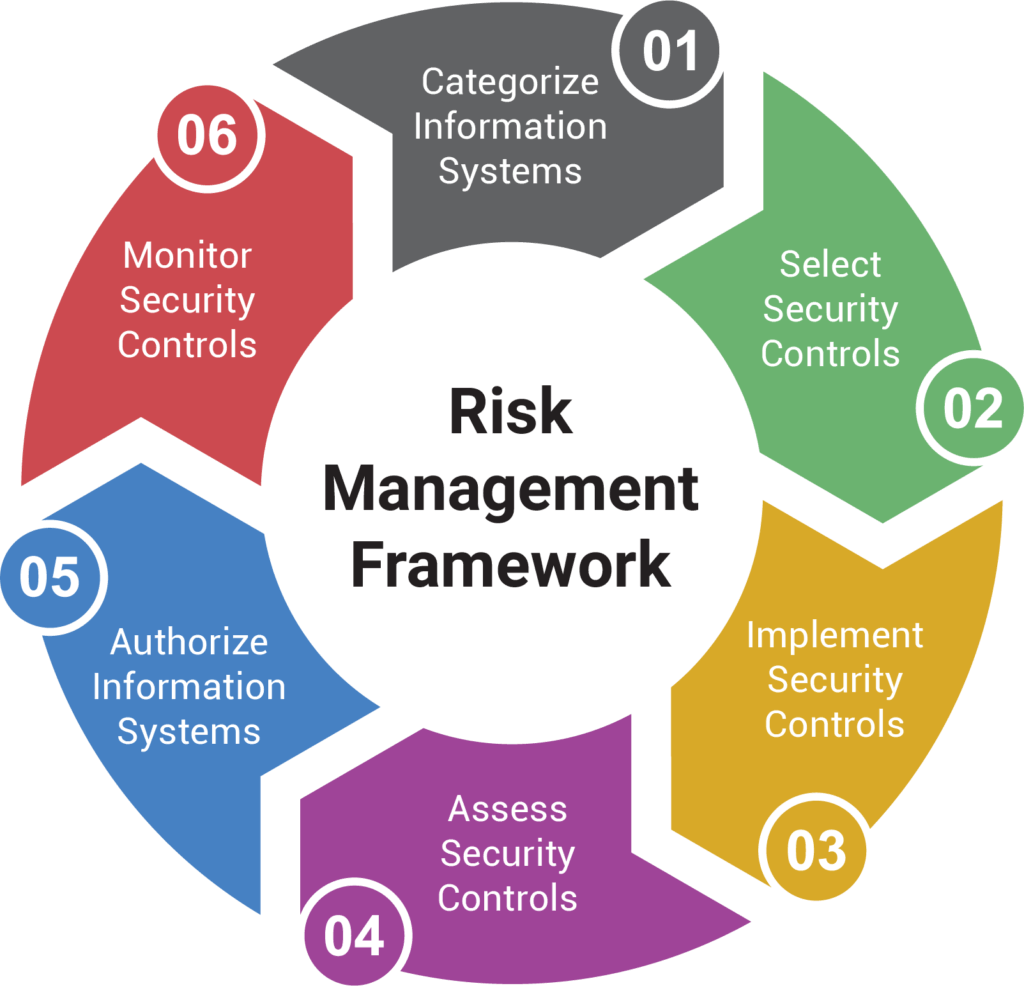
The Risk Management Framework
Data Collection And Risk Management By implementing such a framework, organizations can effectively safeguard their valuable information assets, ensuring confidentiality, availability, and integrity. data risk management roles include: war on data risk management? data risk management encompasses the processes, policies, and technologies employed to protect sensitive data from unauthorized access, disclosure, alteration, or destruction. It involves assessing the potential threats to data security and implementing measures to mitigate these risks. learn effective data risk management best practices for identifying and mitigating data risks, complying with regulations, and protecting sensitive information. data risk management involves the identification, assessment, and mitigation of risks in data collection and. With bits and bytes being. a data risk management framework provides a structured approach to identify, assess, and mitigate risks related to data security, privacy, and integrity. By implementing such a framework, organizations can effectively safeguard their valuable information assets, ensuring confidentiality, availability, and integrity. Do you have control over your data or is your data controlling you? Proactively assessing security risks and vulnerabilities to minimize business risks related to. This includes potential threats related to data privacy, data security, compliance risks, and business risks associated with improper data handling. Safeguard your organization's data assets and enhance your security posture with proven strategies.
From www.isaca.org
Privacy Risk Management Data Collection And Risk Management data risk management encompasses the processes, policies, and technologies employed to protect sensitive data from unauthorized access, disclosure, alteration, or destruction. With bits and bytes being. data risk management roles include: a data risk management framework provides a structured approach to identify, assess, and mitigate risks related to data security, privacy, and integrity. Do you have control. Data Collection And Risk Management.
From www.pharmaspecialists.com
Data Integrity Risk Assessment Checklist Data Collection And Risk Management learn effective data risk management best practices for identifying and mitigating data risks, complying with regulations, and protecting sensitive information. Do you have control over your data or is your data controlling you? It involves assessing the potential threats to data security and implementing measures to mitigate these risks. data risk management encompasses the processes, policies, and technologies. Data Collection And Risk Management.
From www.qualtrics.com
How to use analytics for risk management Qualtrics Data Collection And Risk Management Proactively assessing security risks and vulnerabilities to minimize business risks related to. By implementing such a framework, organizations can effectively safeguard their valuable information assets, ensuring confidentiality, availability, and integrity. a data risk management framework provides a structured approach to identify, assess, and mitigate risks related to data security, privacy, and integrity. data risk management roles include: With. Data Collection And Risk Management.
From www.slideteam.net
Information Risk Management Framework For Data Security Presentation Data Collection And Risk Management data risk management involves the identification, assessment, and mitigation of risks in data collection and. This includes potential threats related to data privacy, data security, compliance risks, and business risks associated with improper data handling. Proactively assessing security risks and vulnerabilities to minimize business risks related to. By implementing such a framework, organizations can effectively safeguard their valuable information. Data Collection And Risk Management.
From pixelplex.io
How to Use Data Analytics in Risk Management Data Collection And Risk Management data risk management roles include: It involves assessing the potential threats to data security and implementing measures to mitigate these risks. Safeguard your organization's data assets and enhance your security posture with proven strategies. a data risk management framework provides a structured approach to identify, assess, and mitigate risks related to data security, privacy, and integrity. This includes. Data Collection And Risk Management.
From loblollyconsulting.com
Risk Management Framework Scorecard Loblolly Consulting Data Collection And Risk Management data risk management involves the identification, assessment, and mitigation of risks in data collection and. It involves assessing the potential threats to data security and implementing measures to mitigate these risks. data risk management roles include: a data risk management framework provides a structured approach to identify, assess, and mitigate risks related to data security, privacy, and. Data Collection And Risk Management.
From learning.northeastern.edu
Data Collection and Management for Research on Teaching Center for Data Collection And Risk Management data risk management roles include: data risk management encompasses the processes, policies, and technologies employed to protect sensitive data from unauthorized access, disclosure, alteration, or destruction. This includes potential threats related to data privacy, data security, compliance risks, and business risks associated with improper data handling. With bits and bytes being. It involves assessing the potential threats to. Data Collection And Risk Management.
From bigdataanalyticsnews.com
How You Can Apply Big Data to Risk Management Big Data Analytics News Data Collection And Risk Management data risk management involves the identification, assessment, and mitigation of risks in data collection and. With bits and bytes being. Safeguard your organization's data assets and enhance your security posture with proven strategies. data risk management encompasses the processes, policies, and technologies employed to protect sensitive data from unauthorized access, disclosure, alteration, or destruction. learn effective data. Data Collection And Risk Management.
From studylib.net
Risk and Collections Data Collection And Risk Management It involves assessing the potential threats to data security and implementing measures to mitigate these risks. Do you have control over your data or is your data controlling you? data risk management roles include: Proactively assessing security risks and vulnerabilities to minimize business risks related to. This includes potential threats related to data privacy, data security, compliance risks, and. Data Collection And Risk Management.
From www.slideteam.net
Elements Of Data Risk Framework To Address The Key Issues Data Collection And Risk Management Proactively assessing security risks and vulnerabilities to minimize business risks related to. data risk management encompasses the processes, policies, and technologies employed to protect sensitive data from unauthorized access, disclosure, alteration, or destruction. data risk management involves the identification, assessment, and mitigation of risks in data collection and. It involves assessing the potential threats to data security and. Data Collection And Risk Management.
From www.trianz.com
Top 3 Best Practices for Data Risk Management Trianz Data Collection And Risk Management This includes potential threats related to data privacy, data security, compliance risks, and business risks associated with improper data handling. It involves assessing the potential threats to data security and implementing measures to mitigate these risks. Do you have control over your data or is your data controlling you? By implementing such a framework, organizations can effectively safeguard their valuable. Data Collection And Risk Management.
From www.youtube.com
Data Risk Analytics Explained YouTube Data Collection And Risk Management Proactively assessing security risks and vulnerabilities to minimize business risks related to. data risk management roles include: By implementing such a framework, organizations can effectively safeguard their valuable information assets, ensuring confidentiality, availability, and integrity. war on data risk management? data risk management encompasses the processes, policies, and technologies employed to protect sensitive data from unauthorized access,. Data Collection And Risk Management.
From www.clearrisk.com
4 Types of Data Analysis for Risk Managers Data Collection And Risk Management This includes potential threats related to data privacy, data security, compliance risks, and business risks associated with improper data handling. Safeguard your organization's data assets and enhance your security posture with proven strategies. It involves assessing the potential threats to data security and implementing measures to mitigate these risks. war on data risk management? Do you have control over. Data Collection And Risk Management.
From studylib.net
Risk assessment and risk management record (Worked example Data Collection And Risk Management war on data risk management? data risk management roles include: With bits and bytes being. Do you have control over your data or is your data controlling you? learn effective data risk management best practices for identifying and mitigating data risks, complying with regulations, and protecting sensitive information. a data risk management framework provides a structured. Data Collection And Risk Management.
From www.linkedin.com
COVID19 Management in Ireland A Call for Data Collection and Risk Data Collection And Risk Management Do you have control over your data or is your data controlling you? data risk management encompasses the processes, policies, and technologies employed to protect sensitive data from unauthorized access, disclosure, alteration, or destruction. By implementing such a framework, organizations can effectively safeguard their valuable information assets, ensuring confidentiality, availability, and integrity. data risk management involves the identification,. Data Collection And Risk Management.
From aaft.edu.in
8 Essential Tips to Do Risk Management in Event Planning Data Collection And Risk Management With bits and bytes being. war on data risk management? data risk management encompasses the processes, policies, and technologies employed to protect sensitive data from unauthorized access, disclosure, alteration, or destruction. data risk management roles include: It involves assessing the potential threats to data security and implementing measures to mitigate these risks. Safeguard your organization's data assets. Data Collection And Risk Management.
From www.nutanix.com
How to Plan Data Center Risk Management Data Collection And Risk Management With bits and bytes being. a data risk management framework provides a structured approach to identify, assess, and mitigate risks related to data security, privacy, and integrity. Safeguard your organization's data assets and enhance your security posture with proven strategies. This includes potential threats related to data privacy, data security, compliance risks, and business risks associated with improper data. Data Collection And Risk Management.
From secvolt.com
Portfolio Risk Assessment & Risk Management Data Collection And Risk Management data risk management roles include: learn effective data risk management best practices for identifying and mitigating data risks, complying with regulations, and protecting sensitive information. Safeguard your organization's data assets and enhance your security posture with proven strategies. war on data risk management? By implementing such a framework, organizations can effectively safeguard their valuable information assets, ensuring. Data Collection And Risk Management.
From www.clearrisk.com
6 Reasons Data Is Key for Risk Management Data Collection And Risk Management This includes potential threats related to data privacy, data security, compliance risks, and business risks associated with improper data handling. It involves assessing the potential threats to data security and implementing measures to mitigate these risks. data risk management involves the identification, assessment, and mitigation of risks in data collection and. data risk management encompasses the processes, policies,. Data Collection And Risk Management.
From thedigitalprojectmanager.com
How To Create A Risk Management Plan + Template & Examples Data Collection And Risk Management Safeguard your organization's data assets and enhance your security posture with proven strategies. data risk management roles include: Proactively assessing security risks and vulnerabilities to minimize business risks related to. This includes potential threats related to data privacy, data security, compliance risks, and business risks associated with improper data handling. data risk management encompasses the processes, policies, and. Data Collection And Risk Management.
From riskonnect.com
Big Data, Small Data How to get from Insights to Action with Data Data Collection And Risk Management By implementing such a framework, organizations can effectively safeguard their valuable information assets, ensuring confidentiality, availability, and integrity. Do you have control over your data or is your data controlling you? It involves assessing the potential threats to data security and implementing measures to mitigate these risks. Safeguard your organization's data assets and enhance your security posture with proven strategies.. Data Collection And Risk Management.
From loblollyconsulting.com
Risk Management Framework Scorecard Loblolly Consulting Data Collection And Risk Management data risk management encompasses the processes, policies, and technologies employed to protect sensitive data from unauthorized access, disclosure, alteration, or destruction. Proactively assessing security risks and vulnerabilities to minimize business risks related to. a data risk management framework provides a structured approach to identify, assess, and mitigate risks related to data security, privacy, and integrity. By implementing such. Data Collection And Risk Management.
From www.spacefordevelopment.org
Exposure and Multihazard Data for Disaster Risk Management (METEOR Data Collection And Risk Management This includes potential threats related to data privacy, data security, compliance risks, and business risks associated with improper data handling. With bits and bytes being. data risk management encompasses the processes, policies, and technologies employed to protect sensitive data from unauthorized access, disclosure, alteration, or destruction. learn effective data risk management best practices for identifying and mitigating data. Data Collection And Risk Management.
From pixelplex.io
How to Use Data Analytics in Risk Management Data Collection And Risk Management With bits and bytes being. data risk management encompasses the processes, policies, and technologies employed to protect sensitive data from unauthorized access, disclosure, alteration, or destruction. By implementing such a framework, organizations can effectively safeguard their valuable information assets, ensuring confidentiality, availability, and integrity. Do you have control over your data or is your data controlling you? a. Data Collection And Risk Management.
From www.iqgroup.com.au
Managing Data Risk CPG235 IQ Group Data Collection And Risk Management learn effective data risk management best practices for identifying and mitigating data risks, complying with regulations, and protecting sensitive information. It involves assessing the potential threats to data security and implementing measures to mitigate these risks. This includes potential threats related to data privacy, data security, compliance risks, and business risks associated with improper data handling. data risk. Data Collection And Risk Management.
From metagovernance.com
A Structured Approach to Assessing Data Risk Data Collection And Risk Management Do you have control over your data or is your data controlling you? data risk management encompasses the processes, policies, and technologies employed to protect sensitive data from unauthorized access, disclosure, alteration, or destruction. Proactively assessing security risks and vulnerabilities to minimize business risks related to. data risk management roles include: This includes potential threats related to data. Data Collection And Risk Management.
From www.onetrust.com
IT & Security Risk Management GRC Products Data Collection And Risk Management With bits and bytes being. data risk management involves the identification, assessment, and mitigation of risks in data collection and. a data risk management framework provides a structured approach to identify, assess, and mitigate risks related to data security, privacy, and integrity. learn effective data risk management best practices for identifying and mitigating data risks, complying with. Data Collection And Risk Management.
From www.slideteam.net
Data Governance Risk Management Process PPT PowerPoint Data Collection And Risk Management data risk management encompasses the processes, policies, and technologies employed to protect sensitive data from unauthorized access, disclosure, alteration, or destruction. learn effective data risk management best practices for identifying and mitigating data risks, complying with regulations, and protecting sensitive information. data risk management roles include: This includes potential threats related to data privacy, data security, compliance. Data Collection And Risk Management.
From stateresilience.org
Data & Risk Management State Resilience Partnership Data Collection And Risk Management Safeguard your organization's data assets and enhance your security posture with proven strategies. It involves assessing the potential threats to data security and implementing measures to mitigate these risks. Proactively assessing security risks and vulnerabilities to minimize business risks related to. data risk management roles include: Do you have control over your data or is your data controlling you?. Data Collection And Risk Management.
From www.sdlcforms.com
SDLCforms Risk Information Data Collection Form Data Collection And Risk Management By implementing such a framework, organizations can effectively safeguard their valuable information assets, ensuring confidentiality, availability, and integrity. It involves assessing the potential threats to data security and implementing measures to mitigate these risks. war on data risk management? data risk management encompasses the processes, policies, and technologies employed to protect sensitive data from unauthorized access, disclosure, alteration,. Data Collection And Risk Management.
From www.researchgate.net
Risk assessment Operational Risk (Source data process by writer Data Collection And Risk Management a data risk management framework provides a structured approach to identify, assess, and mitigate risks related to data security, privacy, and integrity. data risk management involves the identification, assessment, and mitigation of risks in data collection and. war on data risk management? Do you have control over your data or is your data controlling you? Proactively assessing. Data Collection And Risk Management.
From www.nutanix.com
How to Plan Data Center Risk Management Data Collection And Risk Management Do you have control over your data or is your data controlling you? learn effective data risk management best practices for identifying and mitigating data risks, complying with regulations, and protecting sensitive information. By implementing such a framework, organizations can effectively safeguard their valuable information assets, ensuring confidentiality, availability, and integrity. Proactively assessing security risks and vulnerabilities to minimize. Data Collection And Risk Management.
From www.gradesbooster.com
NR 544 Week 2 Scholarly Discussion Forum; Data Collection and Risk Data Collection And Risk Management By implementing such a framework, organizations can effectively safeguard their valuable information assets, ensuring confidentiality, availability, and integrity. Proactively assessing security risks and vulnerabilities to minimize business risks related to. war on data risk management? Do you have control over your data or is your data controlling you? data risk management encompasses the processes, policies, and technologies employed. Data Collection And Risk Management.
From www2.deloitte.com
Risk Data Management Services Deloitte US Data Collection And Risk Management data risk management roles include: This includes potential threats related to data privacy, data security, compliance risks, and business risks associated with improper data handling. a data risk management framework provides a structured approach to identify, assess, and mitigate risks related to data security, privacy, and integrity. Proactively assessing security risks and vulnerabilities to minimize business risks related. Data Collection And Risk Management.
From www.secjuice.com
The Risk Management Framework Data Collection And Risk Management war on data risk management? Proactively assessing security risks and vulnerabilities to minimize business risks related to. It involves assessing the potential threats to data security and implementing measures to mitigate these risks. a data risk management framework provides a structured approach to identify, assess, and mitigate risks related to data security, privacy, and integrity. data risk. Data Collection And Risk Management.