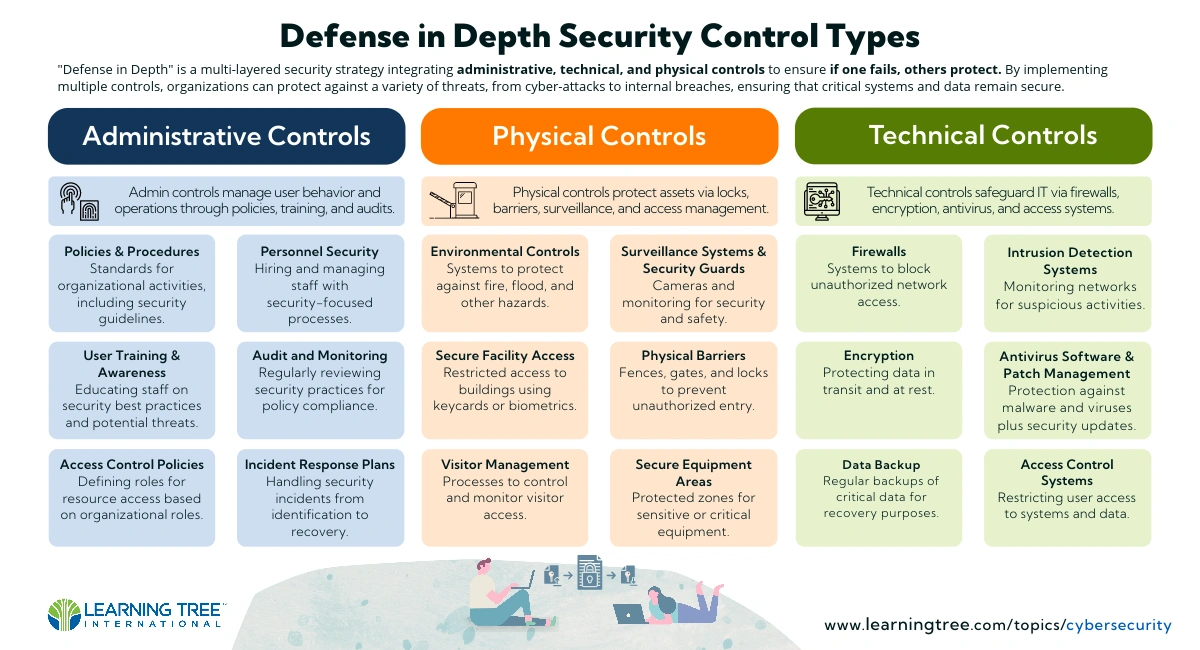
Defense In Depth Utilizes What Techniques To Assure Security . Defense in depth is a cybersecurity methodology that uses multiple mitigation techniques to prevent the same vulnerability. Defense in depth is a strategy that leverages multiple security measures to protect an organization's assets. Defense in depth defends your network security using a layered approach to prevent cybersecurity incidents. A talented hacker can get through an. The thinking is that if. Defense in depth is a security strategy in which multiple security tools, mechanisms, and policies are deployed in. Defense in depth is a cybersecurity strategy that utilizes multiple layers of security to holistically protect the confidentiality, integrity and availability of an organization’s data, networks, resources and other assets. Defense in depth involves multiple layers of security controls to protect systems, ensuring that if one layer fails, others continue to provide.
from www.learningtree.ca
A talented hacker can get through an. Defense in depth defends your network security using a layered approach to prevent cybersecurity incidents. Defense in depth is a cybersecurity strategy that utilizes multiple layers of security to holistically protect the confidentiality, integrity and availability of an organization’s data, networks, resources and other assets. Defense in depth is a cybersecurity methodology that uses multiple mitigation techniques to prevent the same vulnerability. Defense in depth is a strategy that leverages multiple security measures to protect an organization's assets. Defense in depth is a security strategy in which multiple security tools, mechanisms, and policies are deployed in. Defense in depth involves multiple layers of security controls to protect systems, ensuring that if one layer fails, others continue to provide. The thinking is that if.
Examples of Defense in Depth The Stealth Cybersecurity Essential
Defense In Depth Utilizes What Techniques To Assure Security A talented hacker can get through an. Defense in depth is a strategy that leverages multiple security measures to protect an organization's assets. Defense in depth defends your network security using a layered approach to prevent cybersecurity incidents. Defense in depth is a cybersecurity strategy that utilizes multiple layers of security to holistically protect the confidentiality, integrity and availability of an organization’s data, networks, resources and other assets. Defense in depth involves multiple layers of security controls to protect systems, ensuring that if one layer fails, others continue to provide. Defense in depth is a security strategy in which multiple security tools, mechanisms, and policies are deployed in. A talented hacker can get through an. Defense in depth is a cybersecurity methodology that uses multiple mitigation techniques to prevent the same vulnerability. The thinking is that if.
From thecyphere.com
What Is Defense In Depth Strategy In Cybersecurity? Defense In Depth Utilizes What Techniques To Assure Security Defense in depth is a cybersecurity methodology that uses multiple mitigation techniques to prevent the same vulnerability. Defense in depth is a cybersecurity strategy that utilizes multiple layers of security to holistically protect the confidentiality, integrity and availability of an organization’s data, networks, resources and other assets. The thinking is that if. Defense in depth involves multiple layers of security. Defense In Depth Utilizes What Techniques To Assure Security.
From thecyphere.com
What Is Defense In Depth Strategy In Cybersecurity? Defense In Depth Utilizes What Techniques To Assure Security Defense in depth is a cybersecurity strategy that utilizes multiple layers of security to holistically protect the confidentiality, integrity and availability of an organization’s data, networks, resources and other assets. Defense in depth is a security strategy in which multiple security tools, mechanisms, and policies are deployed in. Defense in depth involves multiple layers of security controls to protect systems,. Defense In Depth Utilizes What Techniques To Assure Security.
From www.thatcompany.com
DefenseInDepth Network Security Defense In Depth Utilizes What Techniques To Assure Security Defense in depth is a strategy that leverages multiple security measures to protect an organization's assets. Defense in depth is a cybersecurity strategy that utilizes multiple layers of security to holistically protect the confidentiality, integrity and availability of an organization’s data, networks, resources and other assets. Defense in depth involves multiple layers of security controls to protect systems, ensuring that. Defense In Depth Utilizes What Techniques To Assure Security.
From cstor.com
networksecuritydefensedepth cStor Defense In Depth Utilizes What Techniques To Assure Security Defense in depth defends your network security using a layered approach to prevent cybersecurity incidents. Defense in depth is a strategy that leverages multiple security measures to protect an organization's assets. Defense in depth is a cybersecurity strategy that utilizes multiple layers of security to holistically protect the confidentiality, integrity and availability of an organization’s data, networks, resources and other. Defense In Depth Utilizes What Techniques To Assure Security.
From www.youtube.com
Defence in Depth Definition & Relation to Layered Security Approach Defense In Depth Utilizes What Techniques To Assure Security The thinking is that if. Defense in depth involves multiple layers of security controls to protect systems, ensuring that if one layer fails, others continue to provide. A talented hacker can get through an. Defense in depth is a cybersecurity strategy that utilizes multiple layers of security to holistically protect the confidentiality, integrity and availability of an organization’s data, networks,. Defense In Depth Utilizes What Techniques To Assure Security.
From securiumsolutions.com
what is Defense in Depth? Securium Solutions Defense In Depth Utilizes What Techniques To Assure Security Defense in depth is a cybersecurity methodology that uses multiple mitigation techniques to prevent the same vulnerability. Defense in depth is a security strategy in which multiple security tools, mechanisms, and policies are deployed in. Defense in depth defends your network security using a layered approach to prevent cybersecurity incidents. Defense in depth is a strategy that leverages multiple security. Defense In Depth Utilizes What Techniques To Assure Security.
From www.traceable.ai
Defense in Depth A Guide to Layered Security Traceable API Security Defense In Depth Utilizes What Techniques To Assure Security Defense in depth is a strategy that leverages multiple security measures to protect an organization's assets. Defense in depth is a cybersecurity strategy that utilizes multiple layers of security to holistically protect the confidentiality, integrity and availability of an organization’s data, networks, resources and other assets. A talented hacker can get through an. The thinking is that if. Defense in. Defense In Depth Utilizes What Techniques To Assure Security.
From papers.govtech.com
Adopting a DefenseinDepth Approach to IT Security Defense In Depth Utilizes What Techniques To Assure Security Defense in depth is a cybersecurity methodology that uses multiple mitigation techniques to prevent the same vulnerability. Defense in depth is a security strategy in which multiple security tools, mechanisms, and policies are deployed in. Defense in depth is a cybersecurity strategy that utilizes multiple layers of security to holistically protect the confidentiality, integrity and availability of an organization’s data,. Defense In Depth Utilizes What Techniques To Assure Security.
From www.imperva.com
Defense in depth, layered security architecture Defense In Depth Utilizes What Techniques To Assure Security Defense in depth is a security strategy in which multiple security tools, mechanisms, and policies are deployed in. Defense in depth defends your network security using a layered approach to prevent cybersecurity incidents. The thinking is that if. Defense in depth is a cybersecurity strategy that utilizes multiple layers of security to holistically protect the confidentiality, integrity and availability of. Defense In Depth Utilizes What Techniques To Assure Security.
From www.slideserve.com
PPT Defense in Depth PowerPoint Presentation, free download ID3898700 Defense In Depth Utilizes What Techniques To Assure Security Defense in depth is a strategy that leverages multiple security measures to protect an organization's assets. Defense in depth is a security strategy in which multiple security tools, mechanisms, and policies are deployed in. The thinking is that if. Defense in depth is a cybersecurity strategy that utilizes multiple layers of security to holistically protect the confidentiality, integrity and availability. Defense In Depth Utilizes What Techniques To Assure Security.
From prolion.com
Defense in Depth The Importance of MultiLayered Security Prolion Defense In Depth Utilizes What Techniques To Assure Security Defense in depth is a security strategy in which multiple security tools, mechanisms, and policies are deployed in. Defense in depth involves multiple layers of security controls to protect systems, ensuring that if one layer fails, others continue to provide. Defense in depth is a cybersecurity methodology that uses multiple mitigation techniques to prevent the same vulnerability. Defense in depth. Defense In Depth Utilizes What Techniques To Assure Security.
From thecyphere.com
What Is Defense In Depth Strategy In Cybersecurity? Defense In Depth Utilizes What Techniques To Assure Security Defense in depth is a cybersecurity strategy that utilizes multiple layers of security to holistically protect the confidentiality, integrity and availability of an organization’s data, networks, resources and other assets. Defense in depth is a cybersecurity methodology that uses multiple mitigation techniques to prevent the same vulnerability. The thinking is that if. Defense in depth defends your network security using. Defense In Depth Utilizes What Techniques To Assure Security.
From dokumen.tips
(PPT) WE16 Defense in Depth Top 10 Critical Security Controls Defense In Depth Utilizes What Techniques To Assure Security Defense in depth defends your network security using a layered approach to prevent cybersecurity incidents. A talented hacker can get through an. Defense in depth is a cybersecurity strategy that utilizes multiple layers of security to holistically protect the confidentiality, integrity and availability of an organization’s data, networks, resources and other assets. Defense in depth is a strategy that leverages. Defense In Depth Utilizes What Techniques To Assure Security.
From thecyphere.com
Defense In Depth Definition & Relation To Layered Security Approach Defense In Depth Utilizes What Techniques To Assure Security Defense in depth is a security strategy in which multiple security tools, mechanisms, and policies are deployed in. Defense in depth is a strategy that leverages multiple security measures to protect an organization's assets. The thinking is that if. Defense in depth defends your network security using a layered approach to prevent cybersecurity incidents. Defense in depth involves multiple layers. Defense In Depth Utilizes What Techniques To Assure Security.
From www.buffaloamericas.com
Defense in Depth A Comprehensive Strategy for Evolving Cyberthreats Defense In Depth Utilizes What Techniques To Assure Security Defense in depth involves multiple layers of security controls to protect systems, ensuring that if one layer fails, others continue to provide. Defense in depth is a cybersecurity strategy that utilizes multiple layers of security to holistically protect the confidentiality, integrity and availability of an organization’s data, networks, resources and other assets. Defense in depth defends your network security using. Defense In Depth Utilizes What Techniques To Assure Security.
From www.kiteworks.com
Defense in Depth Key Concepts, Risks & Implementation Best Practices Defense In Depth Utilizes What Techniques To Assure Security Defense in depth is a security strategy in which multiple security tools, mechanisms, and policies are deployed in. Defense in depth is a cybersecurity strategy that utilizes multiple layers of security to holistically protect the confidentiality, integrity and availability of an organization’s data, networks, resources and other assets. A talented hacker can get through an. Defense in depth involves multiple. Defense In Depth Utilizes What Techniques To Assure Security.
From www.youtube.com
What is Defense in Depth? Cyber Security Course for Beginners YouTube Defense In Depth Utilizes What Techniques To Assure Security The thinking is that if. Defense in depth is a strategy that leverages multiple security measures to protect an organization's assets. A talented hacker can get through an. Defense in depth is a security strategy in which multiple security tools, mechanisms, and policies are deployed in. Defense in depth is a cybersecurity strategy that utilizes multiple layers of security to. Defense In Depth Utilizes What Techniques To Assure Security.
From blog.twinstate.com
Defense in Depth The Secret to a Successful Security Strategy Defense In Depth Utilizes What Techniques To Assure Security The thinking is that if. A talented hacker can get through an. Defense in depth is a cybersecurity strategy that utilizes multiple layers of security to holistically protect the confidentiality, integrity and availability of an organization’s data, networks, resources and other assets. Defense in depth is a cybersecurity methodology that uses multiple mitigation techniques to prevent the same vulnerability. Defense. Defense In Depth Utilizes What Techniques To Assure Security.
From www.powermag.com
Securing Industrial Control Systems A Holistic DefenseInDepth Approach Defense In Depth Utilizes What Techniques To Assure Security Defense in depth is a cybersecurity strategy that utilizes multiple layers of security to holistically protect the confidentiality, integrity and availability of an organization’s data, networks, resources and other assets. A talented hacker can get through an. Defense in depth involves multiple layers of security controls to protect systems, ensuring that if one layer fails, others continue to provide. Defense. Defense In Depth Utilizes What Techniques To Assure Security.
From soundcomputers.net
7 Advantages of a DefenseInDepth Cybersecurity Strategy Defense In Depth Utilizes What Techniques To Assure Security Defense in depth defends your network security using a layered approach to prevent cybersecurity incidents. The thinking is that if. Defense in depth is a strategy that leverages multiple security measures to protect an organization's assets. Defense in depth involves multiple layers of security controls to protect systems, ensuring that if one layer fails, others continue to provide. A talented. Defense In Depth Utilizes What Techniques To Assure Security.
From adarshds.medium.com
What is Defense in Depth?. Defense in depth defined by adarsh ds Medium Defense In Depth Utilizes What Techniques To Assure Security Defense in depth is a security strategy in which multiple security tools, mechanisms, and policies are deployed in. Defense in depth defends your network security using a layered approach to prevent cybersecurity incidents. Defense in depth is a cybersecurity methodology that uses multiple mitigation techniques to prevent the same vulnerability. Defense in depth is a cybersecurity strategy that utilizes multiple. Defense In Depth Utilizes What Techniques To Assure Security.
From www.learningtree.ca
Examples of Defense in Depth The Stealth Cybersecurity Essential Defense In Depth Utilizes What Techniques To Assure Security Defense in depth involves multiple layers of security controls to protect systems, ensuring that if one layer fails, others continue to provide. Defense in depth is a cybersecurity methodology that uses multiple mitigation techniques to prevent the same vulnerability. The thinking is that if. Defense in depth defends your network security using a layered approach to prevent cybersecurity incidents. Defense. Defense In Depth Utilizes What Techniques To Assure Security.
From thecyphere.com
What Is Defense In Depth Strategy In Cybersecurity? Defense In Depth Utilizes What Techniques To Assure Security Defense in depth is a cybersecurity methodology that uses multiple mitigation techniques to prevent the same vulnerability. Defense in depth involves multiple layers of security controls to protect systems, ensuring that if one layer fails, others continue to provide. Defense in depth is a strategy that leverages multiple security measures to protect an organization's assets. Defense in depth is a. Defense In Depth Utilizes What Techniques To Assure Security.
From www.govtech.com
How SLTTs Can Implement a DefenseinDepth Cybersecurity Strategy Defense In Depth Utilizes What Techniques To Assure Security The thinking is that if. Defense in depth is a strategy that leverages multiple security measures to protect an organization's assets. Defense in depth defends your network security using a layered approach to prevent cybersecurity incidents. Defense in depth involves multiple layers of security controls to protect systems, ensuring that if one layer fails, others continue to provide. A talented. Defense In Depth Utilizes What Techniques To Assure Security.
From www.nsi1.com
Building Your Most Efficient Security "Machine" Defense In Depth Utilizes What Techniques To Assure Security Defense in depth is a security strategy in which multiple security tools, mechanisms, and policies are deployed in. Defense in depth is a cybersecurity methodology that uses multiple mitigation techniques to prevent the same vulnerability. A talented hacker can get through an. Defense in depth is a strategy that leverages multiple security measures to protect an organization's assets. Defense in. Defense In Depth Utilizes What Techniques To Assure Security.
From csolutionsit.com
How Can a DefenseinDepth Cybersecurity Strategy Benefit You? C Defense In Depth Utilizes What Techniques To Assure Security Defense in depth is a cybersecurity strategy that utilizes multiple layers of security to holistically protect the confidentiality, integrity and availability of an organization’s data, networks, resources and other assets. Defense in depth is a strategy that leverages multiple security measures to protect an organization's assets. A talented hacker can get through an. Defense in depth is a cybersecurity methodology. Defense In Depth Utilizes What Techniques To Assure Security.
From www.researchgate.net
Layers of defense in depth architecture. Download Scientific Diagram Defense In Depth Utilizes What Techniques To Assure Security Defense in depth is a strategy that leverages multiple security measures to protect an organization's assets. Defense in depth is a security strategy in which multiple security tools, mechanisms, and policies are deployed in. Defense in depth involves multiple layers of security controls to protect systems, ensuring that if one layer fails, others continue to provide. Defense in depth defends. Defense In Depth Utilizes What Techniques To Assure Security.
From thehackernews.com
Implementing Defense in Depth to Prevent and Mitigate Cyber Attacks Defense In Depth Utilizes What Techniques To Assure Security Defense in depth is a strategy that leverages multiple security measures to protect an organization's assets. Defense in depth is a cybersecurity methodology that uses multiple mitigation techniques to prevent the same vulnerability. Defense in depth involves multiple layers of security controls to protect systems, ensuring that if one layer fails, others continue to provide. A talented hacker can get. Defense In Depth Utilizes What Techniques To Assure Security.
From aws.amazon.com
Architect defenseindepth security for generative AI applications Defense In Depth Utilizes What Techniques To Assure Security A talented hacker can get through an. Defense in depth is a cybersecurity methodology that uses multiple mitigation techniques to prevent the same vulnerability. Defense in depth is a strategy that leverages multiple security measures to protect an organization's assets. Defense in depth involves multiple layers of security controls to protect systems, ensuring that if one layer fails, others continue. Defense In Depth Utilizes What Techniques To Assure Security.
From www.wallarm.com
What is Defense in Depth? Architecture and Examples Defense In Depth Utilizes What Techniques To Assure Security Defense in depth is a security strategy in which multiple security tools, mechanisms, and policies are deployed in. Defense in depth involves multiple layers of security controls to protect systems, ensuring that if one layer fails, others continue to provide. The thinking is that if. Defense in depth is a strategy that leverages multiple security measures to protect an organization's. Defense In Depth Utilizes What Techniques To Assure Security.
From geek911.com
How Can a DefenseinDepth Approach Improve Your Cybersecurity? GEEK911 Defense In Depth Utilizes What Techniques To Assure Security Defense in depth is a cybersecurity strategy that utilizes multiple layers of security to holistically protect the confidentiality, integrity and availability of an organization’s data, networks, resources and other assets. Defense in depth involves multiple layers of security controls to protect systems, ensuring that if one layer fails, others continue to provide. The thinking is that if. Defense in depth. Defense In Depth Utilizes What Techniques To Assure Security.
From ussignal.com
DefenseInDepth Cybersecurity Guide Defense In Depth Utilizes What Techniques To Assure Security The thinking is that if. Defense in depth is a strategy that leverages multiple security measures to protect an organization's assets. Defense in depth is a cybersecurity strategy that utilizes multiple layers of security to holistically protect the confidentiality, integrity and availability of an organization’s data, networks, resources and other assets. A talented hacker can get through an. Defense in. Defense In Depth Utilizes What Techniques To Assure Security.
From www.powermag.com
Securing Industrial Control Systems A Holistic DefenseInDepth Approach Defense In Depth Utilizes What Techniques To Assure Security A talented hacker can get through an. The thinking is that if. Defense in depth is a security strategy in which multiple security tools, mechanisms, and policies are deployed in. Defense in depth is a cybersecurity methodology that uses multiple mitigation techniques to prevent the same vulnerability. Defense in depth is a strategy that leverages multiple security measures to protect. Defense In Depth Utilizes What Techniques To Assure Security.
From seqred.pl
Defense in Depth strategies Part 2 SEQRED Defense In Depth Utilizes What Techniques To Assure Security Defense in depth involves multiple layers of security controls to protect systems, ensuring that if one layer fails, others continue to provide. Defense in depth is a security strategy in which multiple security tools, mechanisms, and policies are deployed in. Defense in depth defends your network security using a layered approach to prevent cybersecurity incidents. Defense in depth is a. Defense In Depth Utilizes What Techniques To Assure Security.
From www.slideserve.com
PPT Defense in Depth PowerPoint Presentation, free download ID3898700 Defense In Depth Utilizes What Techniques To Assure Security Defense in depth involves multiple layers of security controls to protect systems, ensuring that if one layer fails, others continue to provide. The thinking is that if. Defense in depth is a cybersecurity strategy that utilizes multiple layers of security to holistically protect the confidentiality, integrity and availability of an organization’s data, networks, resources and other assets. Defense in depth. Defense In Depth Utilizes What Techniques To Assure Security.