Javascript String Hash Function . In javascript, there are various methods available to generate a hash from a string. This tutorial will show you a practical way to generate a hash for a string in javascript, and provide working code examples you can use in your own project. Creating a hash from a string is useful for ensuring data integrity, verifying data, and securely storing sensitive information such as passwords. In this comprehensive guide, we will. Here is how it works under the hood: When i need simple client side hashing without external libraries i use the browsers' built in atob() and btoa() functions.
from data-flair.training
In this comprehensive guide, we will. In javascript, there are various methods available to generate a hash from a string. This tutorial will show you a practical way to generate a hash for a string in javascript, and provide working code examples you can use in your own project. Creating a hash from a string is useful for ensuring data integrity, verifying data, and securely storing sensitive information such as passwords. Here is how it works under the hood: When i need simple client side hashing without external libraries i use the browsers' built in atob() and btoa() functions.
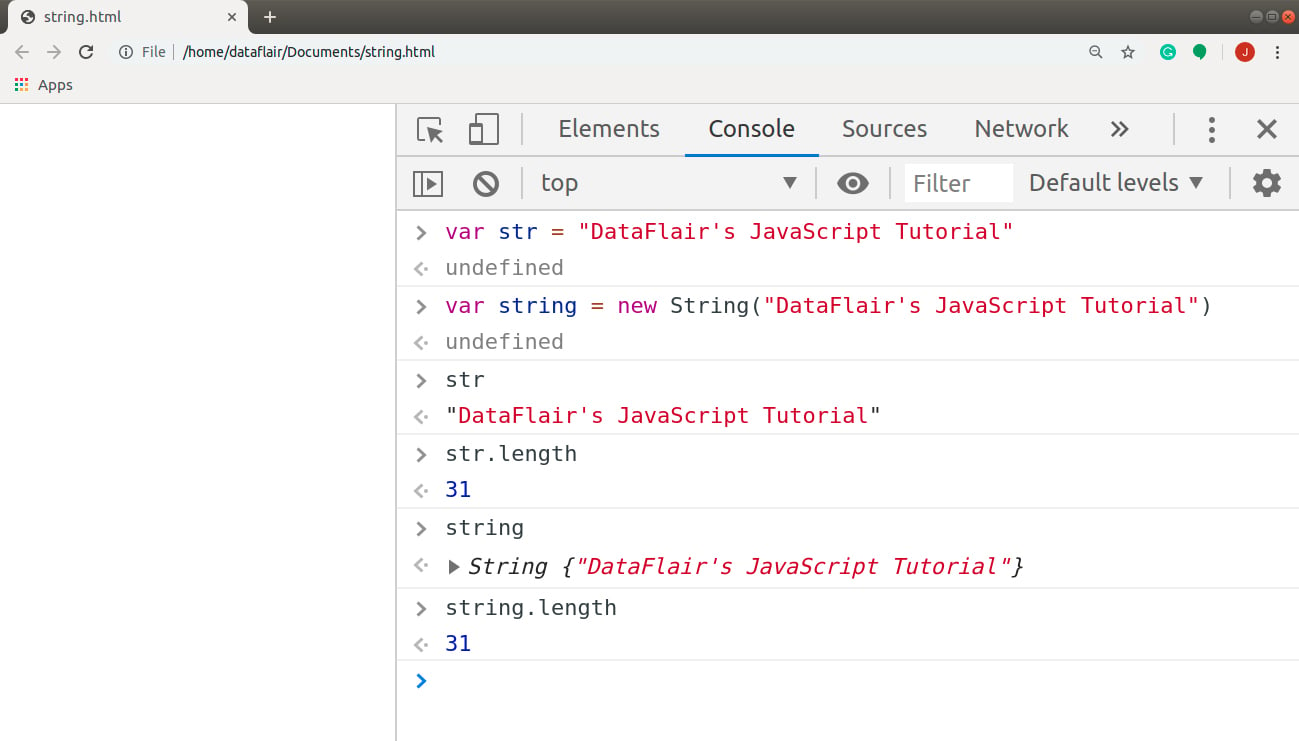
JavaScript Strings Find Out Different Methods of String Objects
Javascript String Hash Function Creating a hash from a string is useful for ensuring data integrity, verifying data, and securely storing sensitive information such as passwords. In javascript, there are various methods available to generate a hash from a string. This tutorial will show you a practical way to generate a hash for a string in javascript, and provide working code examples you can use in your own project. When i need simple client side hashing without external libraries i use the browsers' built in atob() and btoa() functions. Creating a hash from a string is useful for ensuring data integrity, verifying data, and securely storing sensitive information such as passwords. Here is how it works under the hood: In this comprehensive guide, we will.
From app.gumroad.com
[FREE] JavaScript String methods cheathseet Javascript String Hash Function When i need simple client side hashing without external libraries i use the browsers' built in atob() and btoa() functions. In this comprehensive guide, we will. This tutorial will show you a practical way to generate a hash for a string in javascript, and provide working code examples you can use in your own project. Creating a hash from a. Javascript String Hash Function.
From vhudyma-blog.eu
Data Structures Hash Table In JavaScript FrontEnd Expert Javascript String Hash Function In this comprehensive guide, we will. In javascript, there are various methods available to generate a hash from a string. Here is how it works under the hood: Creating a hash from a string is useful for ensuring data integrity, verifying data, and securely storing sensitive information such as passwords. This tutorial will show you a practical way to generate. Javascript String Hash Function.
From codetopology.com
15 Useful JavaScript String Methods Javascript String Hash Function This tutorial will show you a practical way to generate a hash for a string in javascript, and provide working code examples you can use in your own project. Here is how it works under the hood: In javascript, there are various methods available to generate a hash from a string. When i need simple client side hashing without external. Javascript String Hash Function.
From slideplayer.com
CSE 373 Data Structures and Algorithms ppt download Javascript String Hash Function In javascript, there are various methods available to generate a hash from a string. Here is how it works under the hood: Creating a hash from a string is useful for ensuring data integrity, verifying data, and securely storing sensitive information such as passwords. When i need simple client side hashing without external libraries i use the browsers' built in. Javascript String Hash Function.
From www.youtube.com
Array Hashing array of strings in javascript YouTube Javascript String Hash Function In this comprehensive guide, we will. When i need simple client side hashing without external libraries i use the browsers' built in atob() and btoa() functions. Creating a hash from a string is useful for ensuring data integrity, verifying data, and securely storing sensitive information such as passwords. In javascript, there are various methods available to generate a hash from. Javascript String Hash Function.
From www.cs.colostate.edu
Hasher.java Javascript String Hash Function In this comprehensive guide, we will. In javascript, there are various methods available to generate a hash from a string. Here is how it works under the hood: This tutorial will show you a practical way to generate a hash for a string in javascript, and provide working code examples you can use in your own project. When i need. Javascript String Hash Function.
From www.toolsqa.com
What is a String in JavaScript and different operations on JavaScript Javascript String Hash Function Here is how it works under the hood: In this comprehensive guide, we will. Creating a hash from a string is useful for ensuring data integrity, verifying data, and securely storing sensitive information such as passwords. When i need simple client side hashing without external libraries i use the browsers' built in atob() and btoa() functions. This tutorial will show. Javascript String Hash Function.
From isdanni.com
Hashflooding DoS isdanni Javascript String Hash Function Creating a hash from a string is useful for ensuring data integrity, verifying data, and securely storing sensitive information such as passwords. In javascript, there are various methods available to generate a hash from a string. When i need simple client side hashing without external libraries i use the browsers' built in atob() and btoa() functions. This tutorial will show. Javascript String Hash Function.
From morioh.com
JavaScript String Methods Explained with Examples Javascript String Hash Function In javascript, there are various methods available to generate a hash from a string. Creating a hash from a string is useful for ensuring data integrity, verifying data, and securely storing sensitive information such as passwords. This tutorial will show you a practical way to generate a hash for a string in javascript, and provide working code examples you can. Javascript String Hash Function.
From www.youtube.com
JavaScript String Functions YouTube Javascript String Hash Function Here is how it works under the hood: When i need simple client side hashing without external libraries i use the browsers' built in atob() and btoa() functions. Creating a hash from a string is useful for ensuring data integrity, verifying data, and securely storing sensitive information such as passwords. In this comprehensive guide, we will. In javascript, there are. Javascript String Hash Function.
From www.tutorialstonight.com
Javascript String Methods List (with Examples) Javascript String Hash Function Here is how it works under the hood: This tutorial will show you a practical way to generate a hash for a string in javascript, and provide working code examples you can use in your own project. In javascript, there are various methods available to generate a hash from a string. In this comprehensive guide, we will. Creating a hash. Javascript String Hash Function.
From 9to5answer.com
[Solved] Hash function for a string 9to5Answer Javascript String Hash Function Here is how it works under the hood: In javascript, there are various methods available to generate a hash from a string. When i need simple client side hashing without external libraries i use the browsers' built in atob() and btoa() functions. Creating a hash from a string is useful for ensuring data integrity, verifying data, and securely storing sensitive. Javascript String Hash Function.
From www.linuxscrew.com
Generate a Hash from String in Javascript, with Examples Javascript String Hash Function In this comprehensive guide, we will. Creating a hash from a string is useful for ensuring data integrity, verifying data, and securely storing sensitive information such as passwords. In javascript, there are various methods available to generate a hash from a string. When i need simple client side hashing without external libraries i use the browsers' built in atob() and. Javascript String Hash Function.
From codeburst.io
Objects and Hash Tables in Javascript codeburst Javascript String Hash Function In javascript, there are various methods available to generate a hash from a string. Creating a hash from a string is useful for ensuring data integrity, verifying data, and securely storing sensitive information such as passwords. This tutorial will show you a practical way to generate a hash for a string in javascript, and provide working code examples you can. Javascript String Hash Function.
From codingbootcampguides.com
How to Build a Hash Table in JavaScript Coding Bootcamp Guides Javascript String Hash Function Creating a hash from a string is useful for ensuring data integrity, verifying data, and securely storing sensitive information such as passwords. Here is how it works under the hood: In javascript, there are various methods available to generate a hash from a string. When i need simple client side hashing without external libraries i use the browsers' built in. Javascript String Hash Function.
From www.freecodecamp.org
How to implement a simple hash table in JavaScript Javascript String Hash Function In this comprehensive guide, we will. Here is how it works under the hood: When i need simple client side hashing without external libraries i use the browsers' built in atob() and btoa() functions. This tutorial will show you a practical way to generate a hash for a string in javascript, and provide working code examples you can use in. Javascript String Hash Function.
From linuxhint.com
Hash Tables in JavaScript Explained Javascript String Hash Function In javascript, there are various methods available to generate a hash from a string. In this comprehensive guide, we will. When i need simple client side hashing without external libraries i use the browsers' built in atob() and btoa() functions. This tutorial will show you a practical way to generate a hash for a string in javascript, and provide working. Javascript String Hash Function.
From www.codingninjas.com
Hash Function in Data Structure Coding Ninjas Javascript String Hash Function Here is how it works under the hood: Creating a hash from a string is useful for ensuring data integrity, verifying data, and securely storing sensitive information such as passwords. In this comprehensive guide, we will. In javascript, there are various methods available to generate a hash from a string. When i need simple client side hashing without external libraries. Javascript String Hash Function.
From data-flair.training
JavaScript Strings Find Out Different Methods of String Objects Javascript String Hash Function In javascript, there are various methods available to generate a hash from a string. In this comprehensive guide, we will. When i need simple client side hashing without external libraries i use the browsers' built in atob() and btoa() functions. Creating a hash from a string is useful for ensuring data integrity, verifying data, and securely storing sensitive information such. Javascript String Hash Function.
From www.youtube.com
JavaScript How can I get the sha1 hash of a string in node.js? YouTube Javascript String Hash Function In javascript, there are various methods available to generate a hash from a string. In this comprehensive guide, we will. Creating a hash from a string is useful for ensuring data integrity, verifying data, and securely storing sensitive information such as passwords. Here is how it works under the hood: This tutorial will show you a practical way to generate. Javascript String Hash Function.
From slideplayer.com
CSE 373 Data Structures and Algorithms ppt download Javascript String Hash Function Here is how it works under the hood: In javascript, there are various methods available to generate a hash from a string. When i need simple client side hashing without external libraries i use the browsers' built in atob() and btoa() functions. This tutorial will show you a practical way to generate a hash for a string in javascript, and. Javascript String Hash Function.
From www.freecodecamp.org
Tabella hash di JavaScript Hashing associativo di array in JS Javascript String Hash Function When i need simple client side hashing without external libraries i use the browsers' built in atob() and btoa() functions. This tutorial will show you a practical way to generate a hash for a string in javascript, and provide working code examples you can use in your own project. In javascript, there are various methods available to generate a hash. Javascript String Hash Function.
From github.com
GitHub darkskyapp/stringhash Fast string hashing function for Node.JS. Javascript String Hash Function When i need simple client side hashing without external libraries i use the browsers' built in atob() and btoa() functions. Creating a hash from a string is useful for ensuring data integrity, verifying data, and securely storing sensitive information such as passwords. In javascript, there are various methods available to generate a hash from a string. This tutorial will show. Javascript String Hash Function.
From courses.cs.washington.edu
Good Hash Function for Strings? Javascript String Hash Function When i need simple client side hashing without external libraries i use the browsers' built in atob() and btoa() functions. In javascript, there are various methods available to generate a hash from a string. In this comprehensive guide, we will. This tutorial will show you a practical way to generate a hash for a string in javascript, and provide working. Javascript String Hash Function.
From codeahoy.com
Hash Functions CodeAhoy Javascript String Hash Function Creating a hash from a string is useful for ensuring data integrity, verifying data, and securely storing sensitive information such as passwords. In javascript, there are various methods available to generate a hash from a string. Here is how it works under the hood: When i need simple client side hashing without external libraries i use the browsers' built in. Javascript String Hash Function.
From www.ionos.ca
Hash functions definition, usage, and examples IONOS CA Javascript String Hash Function In javascript, there are various methods available to generate a hash from a string. When i need simple client side hashing without external libraries i use the browsers' built in atob() and btoa() functions. Creating a hash from a string is useful for ensuring data integrity, verifying data, and securely storing sensitive information such as passwords. Here is how it. Javascript String Hash Function.
From hxebndydg.blob.core.windows.net
StringHash Github at Laura Bray blog Javascript String Hash Function In this comprehensive guide, we will. When i need simple client side hashing without external libraries i use the browsers' built in atob() and btoa() functions. Here is how it works under the hood: Creating a hash from a string is useful for ensuring data integrity, verifying data, and securely storing sensitive information such as passwords. This tutorial will show. Javascript String Hash Function.
From www.youtube.com
Important JavaScript built in string functions YouTube Javascript String Hash Function In javascript, there are various methods available to generate a hash from a string. When i need simple client side hashing without external libraries i use the browsers' built in atob() and btoa() functions. Creating a hash from a string is useful for ensuring data integrity, verifying data, and securely storing sensitive information such as passwords. Here is how it. Javascript String Hash Function.
From www.youtube.com
Hash function YouTube Javascript String Hash Function Creating a hash from a string is useful for ensuring data integrity, verifying data, and securely storing sensitive information such as passwords. This tutorial will show you a practical way to generate a hash for a string in javascript, and provide working code examples you can use in your own project. When i need simple client side hashing without external. Javascript String Hash Function.
From velog.io
Hash Table Javascript String Hash Function Here is how it works under the hood: In this comprehensive guide, we will. Creating a hash from a string is useful for ensuring data integrity, verifying data, and securely storing sensitive information such as passwords. When i need simple client side hashing without external libraries i use the browsers' built in atob() and btoa() functions. This tutorial will show. Javascript String Hash Function.
From slidetodoc.com
Hash Table 88621159 Data Structures and Algorithms 22561 Javascript String Hash Function When i need simple client side hashing without external libraries i use the browsers' built in atob() and btoa() functions. In javascript, there are various methods available to generate a hash from a string. Here is how it works under the hood: In this comprehensive guide, we will. This tutorial will show you a practical way to generate a hash. Javascript String Hash Function.
From devsmitra.medium.com
Javascript String Methods A Cheat Sheet for Developer by Rahul Javascript String Hash Function Here is how it works under the hood: This tutorial will show you a practical way to generate a hash for a string in javascript, and provide working code examples you can use in your own project. In javascript, there are various methods available to generate a hash from a string. When i need simple client side hashing without external. Javascript String Hash Function.
From www.slideserve.com
PPT Hash Tables Motivation PowerPoint Presentation, free download Javascript String Hash Function In javascript, there are various methods available to generate a hash from a string. In this comprehensive guide, we will. This tutorial will show you a practical way to generate a hash for a string in javascript, and provide working code examples you can use in your own project. Creating a hash from a string is useful for ensuring data. Javascript String Hash Function.
From www.saksenengku.com
Apa itu Hashing? Cara kerja, Jenis, dan Pengaplikasiannya Saksenengku Javascript String Hash Function This tutorial will show you a practical way to generate a hash for a string in javascript, and provide working code examples you can use in your own project. Creating a hash from a string is useful for ensuring data integrity, verifying data, and securely storing sensitive information such as passwords. In this comprehensive guide, we will. Here is how. Javascript String Hash Function.
From www.scaler.com
Hashing and its Use Cases in Java Scaler Topics Javascript String Hash Function When i need simple client side hashing without external libraries i use the browsers' built in atob() and btoa() functions. Here is how it works under the hood: This tutorial will show you a practical way to generate a hash for a string in javascript, and provide working code examples you can use in your own project. In this comprehensive. Javascript String Hash Function.