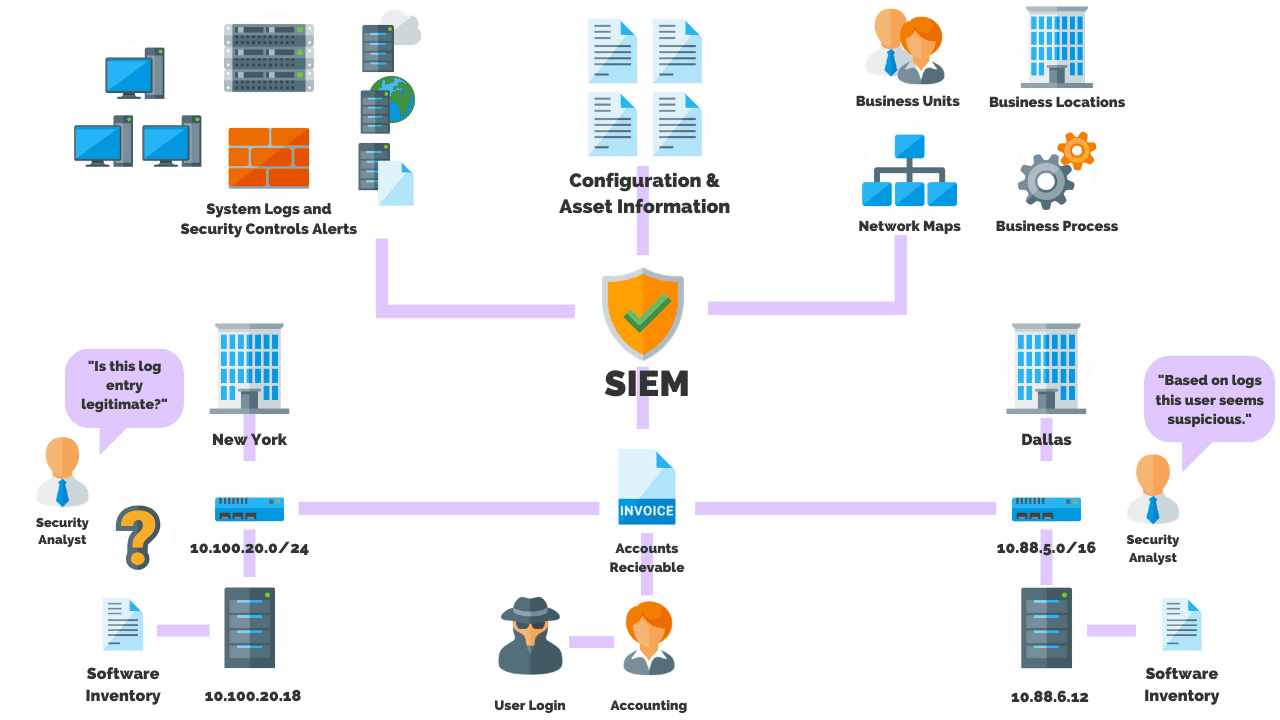
What Is Indexing In Siem . Indexes the various event logs to sort the data into categories and enable searches and event connections. Security information and event management (siem) solutions depend on logs to identify security. Siem technology examines all data, sorting the threat activity, and assigning it with a risk level to help security teams identify malicious actors and mitigate cyberattacks. The siem architecture refers to a structured framework that merges software and hardware components, which facilitates the. In this siem explainer, we explain how siem systems are built, how they go from raw event data to security insights, and how they manage event data on a huge scale.
from purplesec.us
Siem technology examines all data, sorting the threat activity, and assigning it with a risk level to help security teams identify malicious actors and mitigate cyberattacks. The siem architecture refers to a structured framework that merges software and hardware components, which facilitates the. In this siem explainer, we explain how siem systems are built, how they go from raw event data to security insights, and how they manage event data on a huge scale. Indexes the various event logs to sort the data into categories and enable searches and event connections. Security information and event management (siem) solutions depend on logs to identify security.
SIEM Solutions How It Works, Benefits, & Popular Tools PurpleSec
What Is Indexing In Siem Siem technology examines all data, sorting the threat activity, and assigning it with a risk level to help security teams identify malicious actors and mitigate cyberattacks. In this siem explainer, we explain how siem systems are built, how they go from raw event data to security insights, and how they manage event data on a huge scale. Siem technology examines all data, sorting the threat activity, and assigning it with a risk level to help security teams identify malicious actors and mitigate cyberattacks. Security information and event management (siem) solutions depend on logs to identify security. Indexes the various event logs to sort the data into categories and enable searches and event connections. The siem architecture refers to a structured framework that merges software and hardware components, which facilitates the.
From www.lepide.com
What is SIEM and How Does It Work? A Complete Guide What Is Indexing In Siem In this siem explainer, we explain how siem systems are built, how they go from raw event data to security insights, and how they manage event data on a huge scale. Security information and event management (siem) solutions depend on logs to identify security. Siem technology examines all data, sorting the threat activity, and assigning it with a risk level. What Is Indexing In Siem.
From www.varonis.com
What is SIEM? A Beginner’s Guide What Is Indexing In Siem The siem architecture refers to a structured framework that merges software and hardware components, which facilitates the. In this siem explainer, we explain how siem systems are built, how they go from raw event data to security insights, and how they manage event data on a huge scale. Security information and event management (siem) solutions depend on logs to identify. What Is Indexing In Siem.
From www.vc3.com
What Is Security Information and Event Management (SIEM), and Why Is It What Is Indexing In Siem The siem architecture refers to a structured framework that merges software and hardware components, which facilitates the. In this siem explainer, we explain how siem systems are built, how they go from raw event data to security insights, and how they manage event data on a huge scale. Siem technology examines all data, sorting the threat activity, and assigning it. What Is Indexing In Siem.
From www.devopsschool.com
What is SIEM and Why is it so Important? What Is Indexing In Siem The siem architecture refers to a structured framework that merges software and hardware components, which facilitates the. Indexes the various event logs to sort the data into categories and enable searches and event connections. Siem technology examines all data, sorting the threat activity, and assigning it with a risk level to help security teams identify malicious actors and mitigate cyberattacks.. What Is Indexing In Siem.
From learn.g2.com
What Is SIEM Software? (+The Best Tools for Your Business) What Is Indexing In Siem Siem technology examines all data, sorting the threat activity, and assigning it with a risk level to help security teams identify malicious actors and mitigate cyberattacks. Indexes the various event logs to sort the data into categories and enable searches and event connections. In this siem explainer, we explain how siem systems are built, how they go from raw event. What Is Indexing In Siem.
From www.devstringx.com
SIEM Definition, Importance, Use, Components, and Capabilities What Is Indexing In Siem The siem architecture refers to a structured framework that merges software and hardware components, which facilitates the. Security information and event management (siem) solutions depend on logs to identify security. In this siem explainer, we explain how siem systems are built, how they go from raw event data to security insights, and how they manage event data on a huge. What Is Indexing In Siem.
From la-technologiesindia.com
No 1. Security Information and Event Management system What Is Indexing In Siem Siem technology examines all data, sorting the threat activity, and assigning it with a risk level to help security teams identify malicious actors and mitigate cyberattacks. Indexes the various event logs to sort the data into categories and enable searches and event connections. Security information and event management (siem) solutions depend on logs to identify security. In this siem explainer,. What Is Indexing In Siem.
From subscription.packtpub.com
Understanding SIEM Artificial Intelligence for Big Data What Is Indexing In Siem Siem technology examines all data, sorting the threat activity, and assigning it with a risk level to help security teams identify malicious actors and mitigate cyberattacks. The siem architecture refers to a structured framework that merges software and hardware components, which facilitates the. In this siem explainer, we explain how siem systems are built, how they go from raw event. What Is Indexing In Siem.
From www.youtube.com
SIEM Solution Data Normalization and Indexing YouTube What Is Indexing In Siem Security information and event management (siem) solutions depend on logs to identify security. In this siem explainer, we explain how siem systems are built, how they go from raw event data to security insights, and how they manage event data on a huge scale. Siem technology examines all data, sorting the threat activity, and assigning it with a risk level. What Is Indexing In Siem.
From www.cybertechvt.com
Security Information and Event Management (SIEM) Technology CyberTech What Is Indexing In Siem Siem technology examines all data, sorting the threat activity, and assigning it with a risk level to help security teams identify malicious actors and mitigate cyberattacks. Security information and event management (siem) solutions depend on logs to identify security. Indexes the various event logs to sort the data into categories and enable searches and event connections. In this siem explainer,. What Is Indexing In Siem.
From grafana.com
Reduce compliance TCO by using Grafana Loki for nonSIEM logs Grafana What Is Indexing In Siem Indexes the various event logs to sort the data into categories and enable searches and event connections. In this siem explainer, we explain how siem systems are built, how they go from raw event data to security insights, and how they manage event data on a huge scale. The siem architecture refers to a structured framework that merges software and. What Is Indexing In Siem.
From nerdiv.com
Key Benefits of Implementing a SIEM System Nerdiv What Is Indexing In Siem Indexes the various event logs to sort the data into categories and enable searches and event connections. The siem architecture refers to a structured framework that merges software and hardware components, which facilitates the. In this siem explainer, we explain how siem systems are built, how they go from raw event data to security insights, and how they manage event. What Is Indexing In Siem.
From www.starburst.io
Rethinking SIEM Solutions Starburst What Is Indexing In Siem Siem technology examines all data, sorting the threat activity, and assigning it with a risk level to help security teams identify malicious actors and mitigate cyberattacks. Security information and event management (siem) solutions depend on logs to identify security. The siem architecture refers to a structured framework that merges software and hardware components, which facilitates the. Indexes the various event. What Is Indexing In Siem.
From www.redlegg.com
Security Information and Event Management (SIEM) RedLegg What Is Indexing In Siem The siem architecture refers to a structured framework that merges software and hardware components, which facilitates the. Siem technology examines all data, sorting the threat activity, and assigning it with a risk level to help security teams identify malicious actors and mitigate cyberattacks. In this siem explainer, we explain how siem systems are built, how they go from raw event. What Is Indexing In Siem.
From www.coresecurity.com
What Is SIEM? Core Security What Is Indexing In Siem The siem architecture refers to a structured framework that merges software and hardware components, which facilitates the. In this siem explainer, we explain how siem systems are built, how they go from raw event data to security insights, and how they manage event data on a huge scale. Security information and event management (siem) solutions depend on logs to identify. What Is Indexing In Siem.
From ltssecure.com
SIEM Security SIEM Tools SIEM Solution LTS Secure What Is Indexing In Siem The siem architecture refers to a structured framework that merges software and hardware components, which facilitates the. In this siem explainer, we explain how siem systems are built, how they go from raw event data to security insights, and how they manage event data on a huge scale. Indexes the various event logs to sort the data into categories and. What Is Indexing In Siem.
From www.youtube.com
What is a SIEM solution? How SIEM works and Architecture? YouTube What Is Indexing In Siem The siem architecture refers to a structured framework that merges software and hardware components, which facilitates the. Security information and event management (siem) solutions depend on logs to identify security. In this siem explainer, we explain how siem systems are built, how they go from raw event data to security insights, and how they manage event data on a huge. What Is Indexing In Siem.
From www.comparitech.com
Ultimate SIEM Guide What is it? How it works? NextGen & More What Is Indexing In Siem Indexes the various event logs to sort the data into categories and enable searches and event connections. The siem architecture refers to a structured framework that merges software and hardware components, which facilitates the. Security information and event management (siem) solutions depend on logs to identify security. In this siem explainer, we explain how siem systems are built, how they. What Is Indexing In Siem.
From www.computertechreviews.com
What is SIEM? Definition, Advantages, and More What Is Indexing In Siem In this siem explainer, we explain how siem systems are built, how they go from raw event data to security insights, and how they manage event data on a huge scale. Siem technology examines all data, sorting the threat activity, and assigning it with a risk level to help security teams identify malicious actors and mitigate cyberattacks. The siem architecture. What Is Indexing In Siem.
From www.precisely.com
Security Information and Event Management (SIEM) solutions What Is Indexing In Siem The siem architecture refers to a structured framework that merges software and hardware components, which facilitates the. Indexes the various event logs to sort the data into categories and enable searches and event connections. In this siem explainer, we explain how siem systems are built, how they go from raw event data to security insights, and how they manage event. What Is Indexing In Siem.
From www.spiceworks.com
What Is Security Information and Event Management (SIEM)? Definition What Is Indexing In Siem Security information and event management (siem) solutions depend on logs to identify security. In this siem explainer, we explain how siem systems are built, how they go from raw event data to security insights, and how they manage event data on a huge scale. The siem architecture refers to a structured framework that merges software and hardware components, which facilitates. What Is Indexing In Siem.
From cloudserverindia.wordpress.com
A Guide to Understanding the Difference Between SIEM and SOC Solution What Is Indexing In Siem Security information and event management (siem) solutions depend on logs to identify security. The siem architecture refers to a structured framework that merges software and hardware components, which facilitates the. In this siem explainer, we explain how siem systems are built, how they go from raw event data to security insights, and how they manage event data on a huge. What Is Indexing In Siem.
From www.blusapphire.com
NextGen SIEM 101 What Is SIEM, And Why Do You Need It? What Is Indexing In Siem Indexes the various event logs to sort the data into categories and enable searches and event connections. The siem architecture refers to a structured framework that merges software and hardware components, which facilitates the. In this siem explainer, we explain how siem systems are built, how they go from raw event data to security insights, and how they manage event. What Is Indexing In Siem.
From www.kiteworks.com
What Is Security Information and Event Management (SIEM)? What Is Indexing In Siem In this siem explainer, we explain how siem systems are built, how they go from raw event data to security insights, and how they manage event data on a huge scale. The siem architecture refers to a structured framework that merges software and hardware components, which facilitates the. Siem technology examines all data, sorting the threat activity, and assigning it. What Is Indexing In Siem.
From firewall.firm.in
SIEM,SIEM India,SIEMSecurity Monitoring Software in India What Is Indexing In Siem Siem technology examines all data, sorting the threat activity, and assigning it with a risk level to help security teams identify malicious actors and mitigate cyberattacks. Indexes the various event logs to sort the data into categories and enable searches and event connections. In this siem explainer, we explain how siem systems are built, how they go from raw event. What Is Indexing In Siem.
From icon.community
What is indexing and how it works for ICON ICON Community What Is Indexing In Siem Security information and event management (siem) solutions depend on logs to identify security. The siem architecture refers to a structured framework that merges software and hardware components, which facilitates the. In this siem explainer, we explain how siem systems are built, how they go from raw event data to security insights, and how they manage event data on a huge. What Is Indexing In Siem.
From www.esds.co.in
Understanding the Difference Between SIEM and SOC Solution What Is Indexing In Siem Security information and event management (siem) solutions depend on logs to identify security. Indexes the various event logs to sort the data into categories and enable searches and event connections. The siem architecture refers to a structured framework that merges software and hardware components, which facilitates the. In this siem explainer, we explain how siem systems are built, how they. What Is Indexing In Siem.
From purplesec.us
SIEM Solutions How It Works, Benefits, & Popular Tools PurpleSec What Is Indexing In Siem Indexes the various event logs to sort the data into categories and enable searches and event connections. Security information and event management (siem) solutions depend on logs to identify security. In this siem explainer, we explain how siem systems are built, how they go from raw event data to security insights, and how they manage event data on a huge. What Is Indexing In Siem.
From scaleoutsean.github.io
Elasticsearch performance with ESeries Acting Technologist What Is Indexing In Siem Indexes the various event logs to sort the data into categories and enable searches and event connections. The siem architecture refers to a structured framework that merges software and hardware components, which facilitates the. Siem technology examines all data, sorting the threat activity, and assigning it with a risk level to help security teams identify malicious actors and mitigate cyberattacks.. What Is Indexing In Siem.
From www.bitlyft.com
MDR vs SIEM A Comparative Guide What Is Indexing In Siem Security information and event management (siem) solutions depend on logs to identify security. In this siem explainer, we explain how siem systems are built, how they go from raw event data to security insights, and how they manage event data on a huge scale. Siem technology examines all data, sorting the threat activity, and assigning it with a risk level. What Is Indexing In Siem.
From www.educba.com
What is SIEM How does SIEM Works? Advantages Tools What Is Indexing In Siem Security information and event management (siem) solutions depend on logs to identify security. Indexes the various event logs to sort the data into categories and enable searches and event connections. In this siem explainer, we explain how siem systems are built, how they go from raw event data to security insights, and how they manage event data on a huge. What Is Indexing In Siem.
From cybermeteoroid.com
What Is SIEM Tools Why It Is Important For Security? cybermeteoroid What Is Indexing In Siem Security information and event management (siem) solutions depend on logs to identify security. In this siem explainer, we explain how siem systems are built, how they go from raw event data to security insights, and how they manage event data on a huge scale. The siem architecture refers to a structured framework that merges software and hardware components, which facilitates. What Is Indexing In Siem.
From thecyphere.com
What Is SIEM In Security Tools & How It Works What Is Indexing In Siem Security information and event management (siem) solutions depend on logs to identify security. Indexes the various event logs to sort the data into categories and enable searches and event connections. In this siem explainer, we explain how siem systems are built, how they go from raw event data to security insights, and how they manage event data on a huge. What Is Indexing In Siem.
From www.iconis.co.za
What Is SIEM And How IT Works? Iconis What Is Indexing In Siem Indexes the various event logs to sort the data into categories and enable searches and event connections. The siem architecture refers to a structured framework that merges software and hardware components, which facilitates the. Siem technology examines all data, sorting the threat activity, and assigning it with a risk level to help security teams identify malicious actors and mitigate cyberattacks.. What Is Indexing In Siem.
From gridinsoft.com
What is Security Information and Event Management (SIEM)? Gridinsoft What Is Indexing In Siem Siem technology examines all data, sorting the threat activity, and assigning it with a risk level to help security teams identify malicious actors and mitigate cyberattacks. Indexes the various event logs to sort the data into categories and enable searches and event connections. In this siem explainer, we explain how siem systems are built, how they go from raw event. What Is Indexing In Siem.