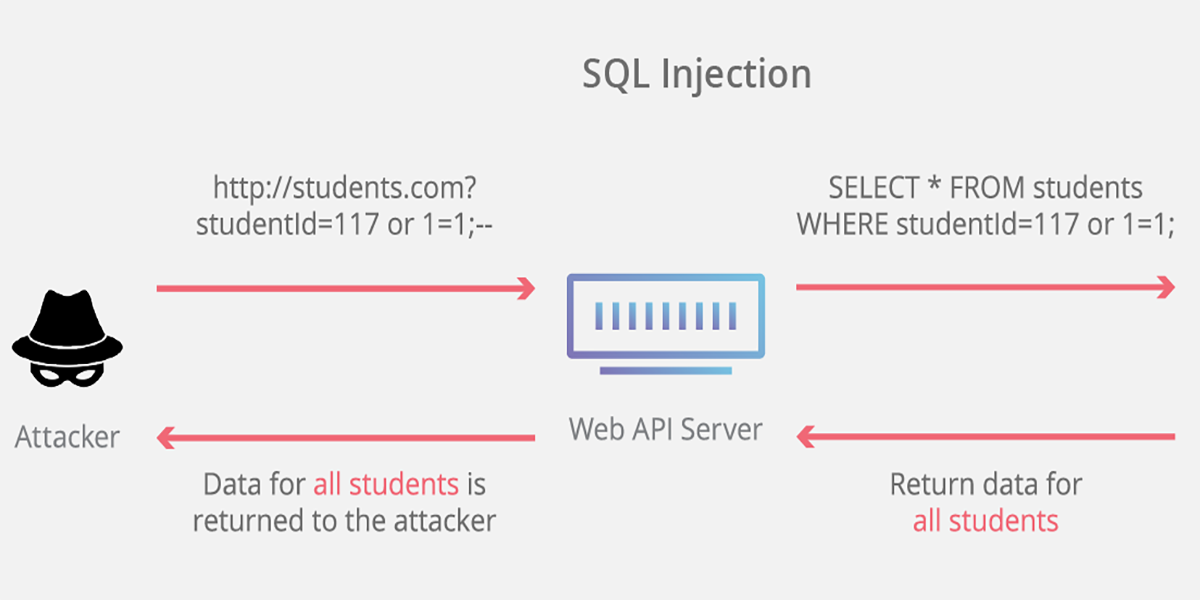
Sql Injection Sample site . Let’s look at two common examples of sql injection attacks. sql injection code examples. in this series we will be showing step by step examples of common attacks. In this tutorial, you will learn about sql. Learn how queries are manipulated without connecting to a. sql injection usually occurs when you ask a user for input, like their username/userid, and instead of a name/id, the user gives you. this sql injection cheat sheet contains examples of useful syntax that you can use to perform a variety of tasks that often. a sql injection attack consists of insertion or “injection” of a sql query via the input data from the client to the application. sql injection is a technique where sql commands are executed from the form input fields or url query parameters. explore sql vulnerabilities safely with the sql injection playground.
from mavink.com
in this series we will be showing step by step examples of common attacks. Let’s look at two common examples of sql injection attacks. a sql injection attack consists of insertion or “injection” of a sql query via the input data from the client to the application. Learn how queries are manipulated without connecting to a. this sql injection cheat sheet contains examples of useful syntax that you can use to perform a variety of tasks that often. sql injection code examples. explore sql vulnerabilities safely with the sql injection playground. sql injection is a technique where sql commands are executed from the form input fields or url query parameters. In this tutorial, you will learn about sql. sql injection usually occurs when you ask a user for input, like their username/userid, and instead of a name/id, the user gives you.
Sql Injection Types
Sql Injection Sample site Learn how queries are manipulated without connecting to a. this sql injection cheat sheet contains examples of useful syntax that you can use to perform a variety of tasks that often. In this tutorial, you will learn about sql. Learn how queries are manipulated without connecting to a. in this series we will be showing step by step examples of common attacks. a sql injection attack consists of insertion or “injection” of a sql query via the input data from the client to the application. sql injection usually occurs when you ask a user for input, like their username/userid, and instead of a name/id, the user gives you. explore sql vulnerabilities safely with the sql injection playground. sql injection code examples. sql injection is a technique where sql commands are executed from the form input fields or url query parameters. Let’s look at two common examples of sql injection attacks.
From www.slideserve.com
PPT Secure Site Design PowerPoint Presentation, free download Sql Injection Sample site sql injection is a technique where sql commands are executed from the form input fields or url query parameters. this sql injection cheat sheet contains examples of useful syntax that you can use to perform a variety of tasks that often. Let’s look at two common examples of sql injection attacks. in this series we will be. Sql Injection Sample site.
From data-flair.training
What is SQL Injection (SQLi) SQL Injection Example DataFlair Sql Injection Sample site Let’s look at two common examples of sql injection attacks. in this series we will be showing step by step examples of common attacks. this sql injection cheat sheet contains examples of useful syntax that you can use to perform a variety of tasks that often. sql injection code examples. sql injection is a technique where. Sql Injection Sample site.
From indiancybersecuritysolutions.com
What is SQL Injection Indian Cyber Security Solutions Sql Injection Sample site explore sql vulnerabilities safely with the sql injection playground. sql injection code examples. Learn how queries are manipulated without connecting to a. this sql injection cheat sheet contains examples of useful syntax that you can use to perform a variety of tasks that often. in this series we will be showing step by step examples of. Sql Injection Sample site.
From whatismyipaddress.com
SQL Injection What It Is and How Does It Work Sql Injection Sample site sql injection code examples. explore sql vulnerabilities safely with the sql injection playground. Learn how queries are manipulated without connecting to a. this sql injection cheat sheet contains examples of useful syntax that you can use to perform a variety of tasks that often. sql injection is a technique where sql commands are executed from the. Sql Injection Sample site.
From user-meta.com
SQL Injection in WordPress sites User Meta Pro Sql Injection Sample site explore sql vulnerabilities safely with the sql injection playground. Let’s look at two common examples of sql injection attacks. Learn how queries are manipulated without connecting to a. In this tutorial, you will learn about sql. sql injection is a technique where sql commands are executed from the form input fields or url query parameters. a sql. Sql Injection Sample site.
From www.slideserve.com
PPT Secure Site Design PowerPoint Presentation, free download Sql Injection Sample site sql injection code examples. Learn how queries are manipulated without connecting to a. in this series we will be showing step by step examples of common attacks. In this tutorial, you will learn about sql. Let’s look at two common examples of sql injection attacks. sql injection usually occurs when you ask a user for input, like. Sql Injection Sample site.
From www.acunetix.com
Exploiting SQL Injection a Handson Example Sql Injection Sample site this sql injection cheat sheet contains examples of useful syntax that you can use to perform a variety of tasks that often. Learn how queries are manipulated without connecting to a. Let’s look at two common examples of sql injection attacks. sql injection is a technique where sql commands are executed from the form input fields or url. Sql Injection Sample site.
From www.one.com
What is SQL injection, and how to prevent SQL injection attacks? Sql Injection Sample site sql injection usually occurs when you ask a user for input, like their username/userid, and instead of a name/id, the user gives you. explore sql vulnerabilities safely with the sql injection playground. In this tutorial, you will learn about sql. in this series we will be showing step by step examples of common attacks. Let’s look at. Sql Injection Sample site.
From www.eccouncil.org
Guide to What is SQL Injection SQL Injection Example, Prevention and Sql Injection Sample site sql injection is a technique where sql commands are executed from the form input fields or url query parameters. this sql injection cheat sheet contains examples of useful syntax that you can use to perform a variety of tasks that often. Let’s look at two common examples of sql injection attacks. sql injection usually occurs when you. Sql Injection Sample site.
From thehackerish.com
SQL injection examples for practice thehackerish Sql Injection Sample site explore sql vulnerabilities safely with the sql injection playground. a sql injection attack consists of insertion or “injection” of a sql query via the input data from the client to the application. Let’s look at two common examples of sql injection attacks. in this series we will be showing step by step examples of common attacks. In. Sql Injection Sample site.
From kratikal.com
SQL Injection in ERP Applications Kratikal Blogs Sql Injection Sample site in this series we will be showing step by step examples of common attacks. this sql injection cheat sheet contains examples of useful syntax that you can use to perform a variety of tasks that often. sql injection usually occurs when you ask a user for input, like their username/userid, and instead of a name/id, the user. Sql Injection Sample site.
From www.programiz.com
SQL Injection (With Examples) Sql Injection Sample site sql injection code examples. sql injection is a technique where sql commands are executed from the form input fields or url query parameters. In this tutorial, you will learn about sql. explore sql vulnerabilities safely with the sql injection playground. a sql injection attack consists of insertion or “injection” of a sql query via the input. Sql Injection Sample site.
From www.geeksforgeeks.org
What is SQL Injection? SQLI Attack Example & Prevention Methods Sql Injection Sample site Learn how queries are manipulated without connecting to a. in this series we will be showing step by step examples of common attacks. Let’s look at two common examples of sql injection attacks. a sql injection attack consists of insertion or “injection” of a sql query via the input data from the client to the application. sql. Sql Injection Sample site.
From hackispower.blogspot.com
Hack Site’s Admin login Using Havij Sql Injection Tool Full Detailed Sql Injection Sample site sql injection code examples. a sql injection attack consists of insertion or “injection” of a sql query via the input data from the client to the application. In this tutorial, you will learn about sql. explore sql vulnerabilities safely with the sql injection playground. Learn how queries are manipulated without connecting to a. this sql injection. Sql Injection Sample site.
From www.slideserve.com
PPT Secure Site Design PowerPoint Presentation, free download Sql Injection Sample site sql injection code examples. explore sql vulnerabilities safely with the sql injection playground. sql injection is a technique where sql commands are executed from the form input fields or url query parameters. this sql injection cheat sheet contains examples of useful syntax that you can use to perform a variety of tasks that often. sql. Sql Injection Sample site.
From thehackerish.com
SQL injection examples for practice thehackerish Sql Injection Sample site a sql injection attack consists of insertion or “injection” of a sql query via the input data from the client to the application. Learn how queries are manipulated without connecting to a. sql injection code examples. this sql injection cheat sheet contains examples of useful syntax that you can use to perform a variety of tasks that. Sql Injection Sample site.
From www.veracode.com
What is SQL Injection? SQL Injection Prevention Veracode Sql Injection Sample site sql injection is a technique where sql commands are executed from the form input fields or url query parameters. Learn how queries are manipulated without connecting to a. this sql injection cheat sheet contains examples of useful syntax that you can use to perform a variety of tasks that often. in this series we will be showing. Sql Injection Sample site.
From www.secpoint.com
SQL Injection Find out if your site is Secure Sql Injection Sample site Learn how queries are manipulated without connecting to a. in this series we will be showing step by step examples of common attacks. Let’s look at two common examples of sql injection attacks. In this tutorial, you will learn about sql. sql injection usually occurs when you ask a user for input, like their username/userid, and instead of. Sql Injection Sample site.
From www.cloudflare.com
What is SQL injection? Cloudflare Sql Injection Sample site sql injection usually occurs when you ask a user for input, like their username/userid, and instead of a name/id, the user gives you. Learn how queries are manipulated without connecting to a. sql injection code examples. sql injection is a technique where sql commands are executed from the form input fields or url query parameters. In this. Sql Injection Sample site.
From www.slideshare.net
SQL Injection Attacks Sql Injection Sample site In this tutorial, you will learn about sql. a sql injection attack consists of insertion or “injection” of a sql query via the input data from the client to the application. this sql injection cheat sheet contains examples of useful syntax that you can use to perform a variety of tasks that often. explore sql vulnerabilities safely. Sql Injection Sample site.
From www.slideserve.com
PPT Secure Site Design PowerPoint Presentation, free download Sql Injection Sample site a sql injection attack consists of insertion or “injection” of a sql query via the input data from the client to the application. sql injection is a technique where sql commands are executed from the form input fields or url query parameters. this sql injection cheat sheet contains examples of useful syntax that you can use to. Sql Injection Sample site.
From www.slideserve.com
PPT Secure Site Design PowerPoint Presentation, free download Sql Injection Sample site sql injection code examples. sql injection usually occurs when you ask a user for input, like their username/userid, and instead of a name/id, the user gives you. sql injection is a technique where sql commands are executed from the form input fields or url query parameters. explore sql vulnerabilities safely with the sql injection playground. Learn. Sql Injection Sample site.
From www.youtube.com
SQL Injection Explained with Demonstration YouTube Sql Injection Sample site In this tutorial, you will learn about sql. sql injection usually occurs when you ask a user for input, like their username/userid, and instead of a name/id, the user gives you. sql injection is a technique where sql commands are executed from the form input fields or url query parameters. Let’s look at two common examples of sql. Sql Injection Sample site.
From computersecuritypgp.blogspot.com
Computer Security and PGP What is an SQL Injection Attack Sql Injection Sample site explore sql vulnerabilities safely with the sql injection playground. sql injection usually occurs when you ask a user for input, like their username/userid, and instead of a name/id, the user gives you. Learn how queries are manipulated without connecting to a. sql injection code examples. a sql injection attack consists of insertion or “injection” of a. Sql Injection Sample site.
From www.slideserve.com
PPT Secure Site Design PowerPoint Presentation, free download Sql Injection Sample site a sql injection attack consists of insertion or “injection” of a sql query via the input data from the client to the application. Let’s look at two common examples of sql injection attacks. in this series we will be showing step by step examples of common attacks. sql injection usually occurs when you ask a user for. Sql Injection Sample site.
From thehackerish.com
SQL injection examples for practice thehackerish Sql Injection Sample site sql injection code examples. Learn how queries are manipulated without connecting to a. Let’s look at two common examples of sql injection attacks. a sql injection attack consists of insertion or “injection” of a sql query via the input data from the client to the application. In this tutorial, you will learn about sql. sql injection is. Sql Injection Sample site.
From www.spiceworks.com
What Is an SQL Injection? Cheatsheet and Examples Sql Injection Sample site in this series we will be showing step by step examples of common attacks. sql injection usually occurs when you ask a user for input, like their username/userid, and instead of a name/id, the user gives you. explore sql vulnerabilities safely with the sql injection playground. this sql injection cheat sheet contains examples of useful syntax. Sql Injection Sample site.
From thereviewstories.com
Sql Injection Sql Injection Sample site this sql injection cheat sheet contains examples of useful syntax that you can use to perform a variety of tasks that often. explore sql vulnerabilities safely with the sql injection playground. a sql injection attack consists of insertion or “injection” of a sql query via the input data from the client to the application. In this tutorial,. Sql Injection Sample site.
From absolutestuffz.blogspot.com
SQL Injection Attack Sql Injection Sample site Let’s look at two common examples of sql injection attacks. In this tutorial, you will learn about sql. this sql injection cheat sheet contains examples of useful syntax that you can use to perform a variety of tasks that often. sql injection usually occurs when you ask a user for input, like their username/userid, and instead of a. Sql Injection Sample site.
From www.slideserve.com
PPT SQL Injection PowerPoint Presentation, free download ID6662917 Sql Injection Sample site Let’s look at two common examples of sql injection attacks. sql injection usually occurs when you ask a user for input, like their username/userid, and instead of a name/id, the user gives you. sql injection is a technique where sql commands are executed from the form input fields or url query parameters. In this tutorial, you will learn. Sql Injection Sample site.
From www.opentechinfo.com
Sql injection Tutorials Beginners Guide website hacking Sql Injection Sample site Let’s look at two common examples of sql injection attacks. a sql injection attack consists of insertion or “injection” of a sql query via the input data from the client to the application. In this tutorial, you will learn about sql. sql injection is a technique where sql commands are executed from the form input fields or url. Sql Injection Sample site.
From brightsec.com
SQL Injection Attack How It Works, Examples and Prevention Sql Injection Sample site Learn how queries are manipulated without connecting to a. sql injection is a technique where sql commands are executed from the form input fields or url query parameters. sql injection usually occurs when you ask a user for input, like their username/userid, and instead of a name/id, the user gives you. in this series we will be. Sql Injection Sample site.
From mavink.com
Sql Injection Types Sql Injection Sample site In this tutorial, you will learn about sql. sql injection is a technique where sql commands are executed from the form input fields or url query parameters. sql injection code examples. this sql injection cheat sheet contains examples of useful syntax that you can use to perform a variety of tasks that often. a sql injection. Sql Injection Sample site.
From www.guru99.com
SQL Injection Tutorial How to Learn with Example Sql Injection Sample site In this tutorial, you will learn about sql. a sql injection attack consists of insertion or “injection” of a sql query via the input data from the client to the application. sql injection is a technique where sql commands are executed from the form input fields or url query parameters. sql injection code examples. explore sql. Sql Injection Sample site.
From www.youtube.com
Tutorial 26 SQL injection dasar YouTube Sql Injection Sample site in this series we will be showing step by step examples of common attacks. a sql injection attack consists of insertion or “injection” of a sql query via the input data from the client to the application. explore sql vulnerabilities safely with the sql injection playground. this sql injection cheat sheet contains examples of useful syntax. Sql Injection Sample site.