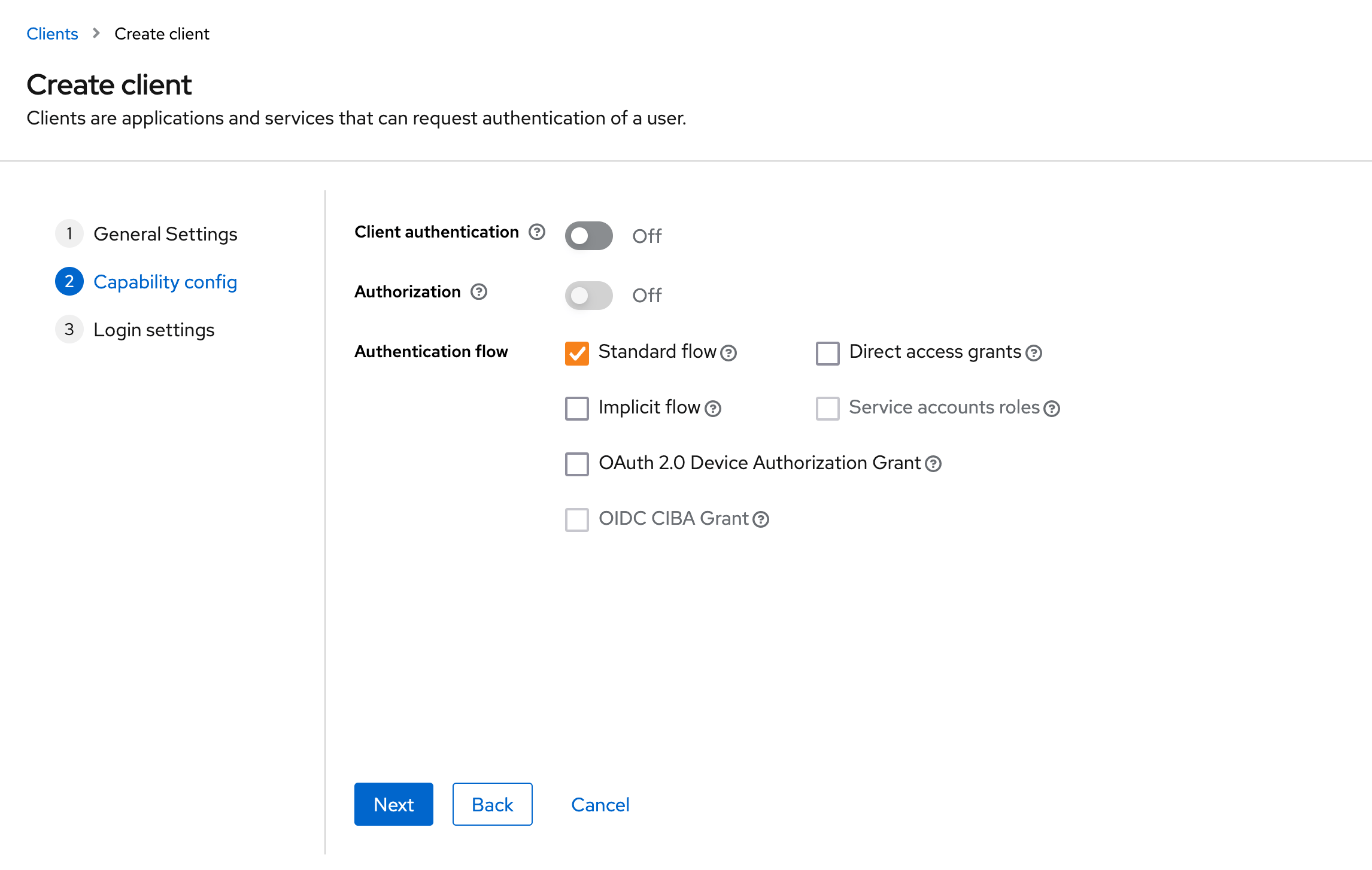
Keycloak Device Authentication . Learn how to go beyond the simple login api and enable the full force of keycloak's authentication and authorization features using the keycloak rest api. Therefore, we aim to leverage authentication flows suitable for such scenarios, such as the device authorization grant, and.
from docs.openfaas.com
Learn how to go beyond the simple login api and enable the full force of keycloak's authentication and authorization features using the keycloak rest api. Therefore, we aim to leverage authentication flows suitable for such scenarios, such as the device authorization grant, and.
Keycloak OpenFaaS
Keycloak Device Authentication Therefore, we aim to leverage authentication flows suitable for such scenarios, such as the device authorization grant, and. Learn how to go beyond the simple login api and enable the full force of keycloak's authentication and authorization features using the keycloak rest api. Therefore, we aim to leverage authentication flows suitable for such scenarios, such as the device authorization grant, and.
From apisix.apache.org
Accessing APISIXDashboard from Everywhere with Keycloak Authentication Keycloak Device Authentication Learn how to go beyond the simple login api and enable the full force of keycloak's authentication and authorization features using the keycloak rest api. Therefore, we aim to leverage authentication flows suitable for such scenarios, such as the device authorization grant, and. Keycloak Device Authentication.
From phasetwo.io
Authn Phase Two Keycloak Hosting Support Migration Keycloak Device Authentication Learn how to go beyond the simple login api and enable the full force of keycloak's authentication and authorization features using the keycloak rest api. Therefore, we aim to leverage authentication flows suitable for such scenarios, such as the device authorization grant, and. Keycloak Device Authentication.
From www.springcloud.io
Unified authentication authorization platform keycloak Introduction Keycloak Device Authentication Learn how to go beyond the simple login api and enable the full force of keycloak's authentication and authorization features using the keycloak rest api. Therefore, we aim to leverage authentication flows suitable for such scenarios, such as the device authorization grant, and. Keycloak Device Authentication.
From documentation.censhare.com
Configure Keycloak with SAML Keycloak Device Authentication Learn how to go beyond the simple login api and enable the full force of keycloak's authentication and authorization features using the keycloak rest api. Therefore, we aim to leverage authentication flows suitable for such scenarios, such as the device authorization grant, and. Keycloak Device Authentication.
From www.mdpi.com
Sensors Free FullText Applying Spring Security Framework with Keycloak Device Authentication Learn how to go beyond the simple login api and enable the full force of keycloak's authentication and authorization features using the keycloak rest api. Therefore, we aim to leverage authentication flows suitable for such scenarios, such as the device authorization grant, and. Keycloak Device Authentication.
From apicurio-studio.readme.io
Setting up Keycloak for use with Apicurio Keycloak Device Authentication Therefore, we aim to leverage authentication flows suitable for such scenarios, such as the device authorization grant, and. Learn how to go beyond the simple login api and enable the full force of keycloak's authentication and authorization features using the keycloak rest api. Keycloak Device Authentication.
From scalac.io
User Authentication with Keycloak Part 1 React frontend Keycloak Device Authentication Therefore, we aim to leverage authentication flows suitable for such scenarios, such as the device authorization grant, and. Learn how to go beyond the simple login api and enable the full force of keycloak's authentication and authorization features using the keycloak rest api. Keycloak Device Authentication.
From www.thomasvitale.com
Keycloak Authentication Flows, SSO Protocols and Client Configuration Keycloak Device Authentication Therefore, we aim to leverage authentication flows suitable for such scenarios, such as the device authorization grant, and. Learn how to go beyond the simple login api and enable the full force of keycloak's authentication and authorization features using the keycloak rest api. Keycloak Device Authentication.
From www.keycloak.org
Authorization Services Guide Keycloak Device Authentication Learn how to go beyond the simple login api and enable the full force of keycloak's authentication and authorization features using the keycloak rest api. Therefore, we aim to leverage authentication flows suitable for such scenarios, such as the device authorization grant, and. Keycloak Device Authentication.
From community.grafana.com
Invalid redirect uri in keycloak after after clicking on sign in with Keycloak Device Authentication Learn how to go beyond the simple login api and enable the full force of keycloak's authentication and authorization features using the keycloak rest api. Therefore, we aim to leverage authentication flows suitable for such scenarios, such as the device authorization grant, and. Keycloak Device Authentication.
From blog.beachgeek.co.uk
Integrating Keycloak as my Identity Provider for IAM Identity Centre Keycloak Device Authentication Therefore, we aim to leverage authentication flows suitable for such scenarios, such as the device authorization grant, and. Learn how to go beyond the simple login api and enable the full force of keycloak's authentication and authorization features using the keycloak rest api. Keycloak Device Authentication.
From www.typingdna.com
Add twofactor authentication to your web app using Keycloak & Node.js Keycloak Device Authentication Learn how to go beyond the simple login api and enable the full force of keycloak's authentication and authorization features using the keycloak rest api. Therefore, we aim to leverage authentication flows suitable for such scenarios, such as the device authorization grant, and. Keycloak Device Authentication.
From community.ibm.com
Extending Keycloak's authentication capabilities by integrating with Keycloak Device Authentication Learn how to go beyond the simple login api and enable the full force of keycloak's authentication and authorization features using the keycloak rest api. Therefore, we aim to leverage authentication flows suitable for such scenarios, such as the device authorization grant, and. Keycloak Device Authentication.
From infocenter.nokia.com
LDAP authentication process Keycloak Device Authentication Therefore, we aim to leverage authentication flows suitable for such scenarios, such as the device authorization grant, and. Learn how to go beyond the simple login api and enable the full force of keycloak's authentication and authorization features using the keycloak rest api. Keycloak Device Authentication.
From lightrun.com
Order of Authenticator executions depends on credential order but not Keycloak Device Authentication Therefore, we aim to leverage authentication flows suitable for such scenarios, such as the device authorization grant, and. Learn how to go beyond the simple login api and enable the full force of keycloak's authentication and authorization features using the keycloak rest api. Keycloak Device Authentication.
From refactorfirst.com
FIDO2 Passwordless Authentication With Keycloak Part 2 RefactorFirst Keycloak Device Authentication Therefore, we aim to leverage authentication flows suitable for such scenarios, such as the device authorization grant, and. Learn how to go beyond the simple login api and enable the full force of keycloak's authentication and authorization features using the keycloak rest api. Keycloak Device Authentication.
From www.thomasvitale.com
Keycloak Authentication Flows, SSO Protocols and Client Configuration Keycloak Device Authentication Therefore, we aim to leverage authentication flows suitable for such scenarios, such as the device authorization grant, and. Learn how to go beyond the simple login api and enable the full force of keycloak's authentication and authorization features using the keycloak rest api. Keycloak Device Authentication.
From www.janua.fr
Client Initiated Backchannel Authentication and Keycloak JANUA Keycloak Device Authentication Learn how to go beyond the simple login api and enable the full force of keycloak's authentication and authorization features using the keycloak rest api. Therefore, we aim to leverage authentication flows suitable for such scenarios, such as the device authorization grant, and. Keycloak Device Authentication.
From www.drupal.org
Keycloak OAuth OpenID Connect Single SignOn Drupal OAuth OIDC Login Keycloak Device Authentication Therefore, we aim to leverage authentication flows suitable for such scenarios, such as the device authorization grant, and. Learn how to go beyond the simple login api and enable the full force of keycloak's authentication and authorization features using the keycloak rest api. Keycloak Device Authentication.
From guides.micronaut.io
Secure a Micronaut application with Keycloak Keycloak Device Authentication Therefore, we aim to leverage authentication flows suitable for such scenarios, such as the device authorization grant, and. Learn how to go beyond the simple login api and enable the full force of keycloak's authentication and authorization features using the keycloak rest api. Keycloak Device Authentication.
From www.linkedin.com
Simplify User Access with Keycloak Single SignOn (SSO) Keycloak Device Authentication Learn how to go beyond the simple login api and enable the full force of keycloak's authentication and authorization features using the keycloak rest api. Therefore, we aim to leverage authentication flows suitable for such scenarios, such as the device authorization grant, and. Keycloak Device Authentication.
From stackoverflow.com
rest Keycloak Oauth2 Authentication Flow Stack Overflow Keycloak Device Authentication Learn how to go beyond the simple login api and enable the full force of keycloak's authentication and authorization features using the keycloak rest api. Therefore, we aim to leverage authentication flows suitable for such scenarios, such as the device authorization grant, and. Keycloak Device Authentication.
From github.com
Supporting Authn Conditional UI · keycloak keycloak · Discussion Keycloak Device Authentication Learn how to go beyond the simple login api and enable the full force of keycloak's authentication and authorization features using the keycloak rest api. Therefore, we aim to leverage authentication flows suitable for such scenarios, such as the device authorization grant, and. Keycloak Device Authentication.
From walkingtree.tech
Keycloak and MultiFactor Authentication (MFA) Strengthening Security Keycloak Device Authentication Therefore, we aim to leverage authentication flows suitable for such scenarios, such as the device authorization grant, and. Learn how to go beyond the simple login api and enable the full force of keycloak's authentication and authorization features using the keycloak rest api. Keycloak Device Authentication.
From phasetwo.io
Authn Phase Two Keycloak Hosting Support Migration Keycloak Device Authentication Therefore, we aim to leverage authentication flows suitable for such scenarios, such as the device authorization grant, and. Learn how to go beyond the simple login api and enable the full force of keycloak's authentication and authorization features using the keycloak rest api. Keycloak Device Authentication.
From www.n-k.de
KEYCLOAK Recovery Authentication Codes Niko Köbler Experte für Keycloak Device Authentication Therefore, we aim to leverage authentication flows suitable for such scenarios, such as the device authorization grant, and. Learn how to go beyond the simple login api and enable the full force of keycloak's authentication and authorization features using the keycloak rest api. Keycloak Device Authentication.
From walkingtree.tech
Keycloak Identity Access Management Solutions WalkingTree Technologies Keycloak Device Authentication Therefore, we aim to leverage authentication flows suitable for such scenarios, such as the device authorization grant, and. Learn how to go beyond the simple login api and enable the full force of keycloak's authentication and authorization features using the keycloak rest api. Keycloak Device Authentication.
From docs.openfaas.com
Keycloak OpenFaaS Keycloak Device Authentication Therefore, we aim to leverage authentication flows suitable for such scenarios, such as the device authorization grant, and. Learn how to go beyond the simple login api and enable the full force of keycloak's authentication and authorization features using the keycloak rest api. Keycloak Device Authentication.
From www.keycloak.org
Authorization Services Guide Keycloak Device Authentication Learn how to go beyond the simple login api and enable the full force of keycloak's authentication and authorization features using the keycloak rest api. Therefore, we aim to leverage authentication flows suitable for such scenarios, such as the device authorization grant, and. Keycloak Device Authentication.
From walkingtree.tech
Keycloak and MultiFactor Authentication (MFA) Strengthening Security Keycloak Device Authentication Learn how to go beyond the simple login api and enable the full force of keycloak's authentication and authorization features using the keycloak rest api. Therefore, we aim to leverage authentication flows suitable for such scenarios, such as the device authorization grant, and. Keycloak Device Authentication.
From docs.wundergraph.com
Keycloak OpenID Connect Authentication Example WunderGraph Docs Keycloak Device Authentication Therefore, we aim to leverage authentication flows suitable for such scenarios, such as the device authorization grant, and. Learn how to go beyond the simple login api and enable the full force of keycloak's authentication and authorization features using the keycloak rest api. Keycloak Device Authentication.
From github.com
Quarkus Keycloak client authentication using x509 · keycloak keycloak Keycloak Device Authentication Therefore, we aim to leverage authentication flows suitable for such scenarios, such as the device authorization grant, and. Learn how to go beyond the simple login api and enable the full force of keycloak's authentication and authorization features using the keycloak rest api. Keycloak Device Authentication.
From help.hcltechsw.com
Sample KeyCloak configuration as an OIDC provider for Domino Keycloak Device Authentication Learn how to go beyond the simple login api and enable the full force of keycloak's authentication and authorization features using the keycloak rest api. Therefore, we aim to leverage authentication flows suitable for such scenarios, such as the device authorization grant, and. Keycloak Device Authentication.
From www.janua.fr
Device code flow in keycloak JANUA Keycloak Device Authentication Learn how to go beyond the simple login api and enable the full force of keycloak's authentication and authorization features using the keycloak rest api. Therefore, we aim to leverage authentication flows suitable for such scenarios, such as the device authorization grant, and. Keycloak Device Authentication.
From andrevianna-1662831931436.hashnode.dev
Understanding the Powerful Keycloak Tool Keycloak Device Authentication Learn how to go beyond the simple login api and enable the full force of keycloak's authentication and authorization features using the keycloak rest api. Therefore, we aim to leverage authentication flows suitable for such scenarios, such as the device authorization grant, and. Keycloak Device Authentication.