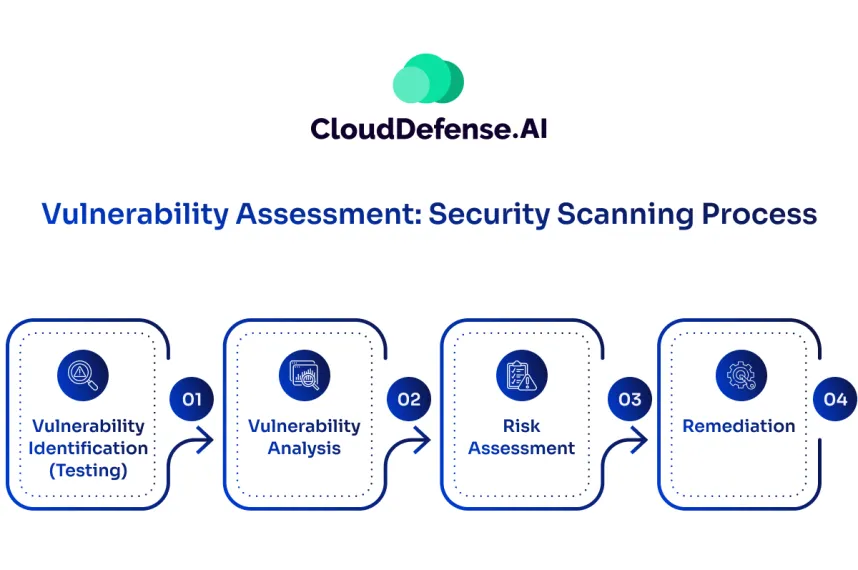
Security Scan Process . Testing, analysis, assessment and remediation. At the heart of a typical vulnerability management tool is a vulnerability scanner. The security scanning process consists of four steps: Understand how vulnerability scanning works, and discover 4 stages of the vulnerability. Vulnerability scanners are automated tools that allow organizations to check if their networks, systems and applications have security weaknesses that could expose them to attacks. Vulnerability scanning is the process of discovering, analysing, and reporting security flaws and vulnerabilities. The scan consists of four stages: Vulnerability scanning, also called “vulnerability assessment,” is the process of evaluating networks or it assets for security. Vulnerability scanning is an automated process to identify security flaws in networks, systems and applications, enabling remediation and enhancing. Alongside vulnerability assessment, vulnerability scanning is an.
from www.clouddefense.ai
Understand how vulnerability scanning works, and discover 4 stages of the vulnerability. Testing, analysis, assessment and remediation. Vulnerability scanning, also called “vulnerability assessment,” is the process of evaluating networks or it assets for security. At the heart of a typical vulnerability management tool is a vulnerability scanner. The scan consists of four stages: Alongside vulnerability assessment, vulnerability scanning is an. Vulnerability scanning is an automated process to identify security flaws in networks, systems and applications, enabling remediation and enhancing. Vulnerability scanning is the process of discovering, analysing, and reporting security flaws and vulnerabilities. Vulnerability scanners are automated tools that allow organizations to check if their networks, systems and applications have security weaknesses that could expose them to attacks. The security scanning process consists of four steps:
What is a Vulnerability Assessment?
Security Scan Process Understand how vulnerability scanning works, and discover 4 stages of the vulnerability. Alongside vulnerability assessment, vulnerability scanning is an. Testing, analysis, assessment and remediation. Vulnerability scanning, also called “vulnerability assessment,” is the process of evaluating networks or it assets for security. Vulnerability scanning is an automated process to identify security flaws in networks, systems and applications, enabling remediation and enhancing. At the heart of a typical vulnerability management tool is a vulnerability scanner. The security scanning process consists of four steps: Understand how vulnerability scanning works, and discover 4 stages of the vulnerability. The scan consists of four stages: Vulnerability scanning is the process of discovering, analysing, and reporting security flaws and vulnerabilities. Vulnerability scanners are automated tools that allow organizations to check if their networks, systems and applications have security weaknesses that could expose them to attacks.
From blog.centretechnologies.com
Choosing the Best Type of Security Scan for your Business Security Scan Process At the heart of a typical vulnerability management tool is a vulnerability scanner. Vulnerability scanning is the process of discovering, analysing, and reporting security flaws and vulnerabilities. Understand how vulnerability scanning works, and discover 4 stages of the vulnerability. Alongside vulnerability assessment, vulnerability scanning is an. Vulnerability scanning is an automated process to identify security flaws in networks, systems and. Security Scan Process.
From www.amplework.com
Static Application Security Testing SAST Basics Security Scan Process The scan consists of four stages: Alongside vulnerability assessment, vulnerability scanning is an. Understand how vulnerability scanning works, and discover 4 stages of the vulnerability. Vulnerability scanning is the process of discovering, analysing, and reporting security flaws and vulnerabilities. The security scanning process consists of four steps: Vulnerability scanning, also called “vulnerability assessment,” is the process of evaluating networks or. Security Scan Process.
From purplesec.us
How Often Should You Perform A Network Vulnerability Scan? Security Scan Process Vulnerability scanning is the process of discovering, analysing, and reporting security flaws and vulnerabilities. The security scanning process consists of four steps: Vulnerability scanners are automated tools that allow organizations to check if their networks, systems and applications have security weaknesses that could expose them to attacks. At the heart of a typical vulnerability management tool is a vulnerability scanner.. Security Scan Process.
From sysdig.com
Top 20 Dockerfile best practices for security Sysdig Security Scan Process Vulnerability scanning is the process of discovering, analysing, and reporting security flaws and vulnerabilities. Understand how vulnerability scanning works, and discover 4 stages of the vulnerability. The scan consists of four stages: Vulnerability scanning is an automated process to identify security flaws in networks, systems and applications, enabling remediation and enhancing. Vulnerability scanners are automated tools that allow organizations to. Security Scan Process.
From www.manageengine.com
Vulnerability Assessment Tools & Checklists ManageEngine Security Scan Process Understand how vulnerability scanning works, and discover 4 stages of the vulnerability. Vulnerability scanners are automated tools that allow organizations to check if their networks, systems and applications have security weaknesses that could expose them to attacks. The security scanning process consists of four steps: Alongside vulnerability assessment, vulnerability scanning is an. Vulnerability scanning is the process of discovering, analysing,. Security Scan Process.
From www.tenable.com
Endpoint Security with Nessus® Agents Blog Tenable® Security Scan Process Understand how vulnerability scanning works, and discover 4 stages of the vulnerability. Vulnerability scanners are automated tools that allow organizations to check if their networks, systems and applications have security weaknesses that could expose them to attacks. At the heart of a typical vulnerability management tool is a vulnerability scanner. The security scanning process consists of four steps: Testing, analysis,. Security Scan Process.
From www.getastra.com
Vulnerability Scanning Process and Types Astra Security Blog Security Scan Process Understand how vulnerability scanning works, and discover 4 stages of the vulnerability. At the heart of a typical vulnerability management tool is a vulnerability scanner. The security scanning process consists of four steps: Testing, analysis, assessment and remediation. Alongside vulnerability assessment, vulnerability scanning is an. Vulnerability scanning is the process of discovering, analysing, and reporting security flaws and vulnerabilities. The. Security Scan Process.
From www.manageengine.com
Linux Vulnerability Scanner Scan Linux Server for Vulnerabilities Security Scan Process The security scanning process consists of four steps: Vulnerability scanning is the process of discovering, analysing, and reporting security flaws and vulnerabilities. Vulnerability scanners are automated tools that allow organizations to check if their networks, systems and applications have security weaknesses that could expose them to attacks. Vulnerability scanning is an automated process to identify security flaws in networks, systems. Security Scan Process.
From www.getastra.com
What is Network Vulnerability Scanning? The Ultimate Guide Security Scan Process Vulnerability scanning is the process of discovering, analysing, and reporting security flaws and vulnerabilities. The scan consists of four stages: At the heart of a typical vulnerability management tool is a vulnerability scanner. Vulnerability scanners are automated tools that allow organizations to check if their networks, systems and applications have security weaknesses that could expose them to attacks. Alongside vulnerability. Security Scan Process.
From www.softpedia.com
Norton Security Scan 4.7.0.181 Download, Review, Screenshots Security Scan Process At the heart of a typical vulnerability management tool is a vulnerability scanner. Understand how vulnerability scanning works, and discover 4 stages of the vulnerability. Vulnerability scanning is the process of discovering, analysing, and reporting security flaws and vulnerabilities. Testing, analysis, assessment and remediation. Vulnerability scanners are automated tools that allow organizations to check if their networks, systems and applications. Security Scan Process.
From thecyphere.com
Managed Vulnerabilityscanning Cyphere Security Scan Process The scan consists of four stages: Vulnerability scanning is an automated process to identify security flaws in networks, systems and applications, enabling remediation and enhancing. Testing, analysis, assessment and remediation. Vulnerability scanning, also called “vulnerability assessment,” is the process of evaluating networks or it assets for security. Vulnerability scanning is the process of discovering, analysing, and reporting security flaws and. Security Scan Process.
From www.google.de
Patent USH2110 Automated security scanning process Google Patentsuche Security Scan Process Vulnerability scanning is an automated process to identify security flaws in networks, systems and applications, enabling remediation and enhancing. Vulnerability scanning is the process of discovering, analysing, and reporting security flaws and vulnerabilities. The security scanning process consists of four steps: At the heart of a typical vulnerability management tool is a vulnerability scanner. Understand how vulnerability scanning works, and. Security Scan Process.
From faun.pub
Amazon Inspector — Continuous Security (automated CVE scanning) by Security Scan Process Vulnerability scanning is an automated process to identify security flaws in networks, systems and applications, enabling remediation and enhancing. Vulnerability scanning, also called “vulnerability assessment,” is the process of evaluating networks or it assets for security. Testing, analysis, assessment and remediation. Vulnerability scanners are automated tools that allow organizations to check if their networks, systems and applications have security weaknesses. Security Scan Process.
From www.researchgate.net
Vulnerability Scanner System Diagram Download Scientific Diagram Security Scan Process Alongside vulnerability assessment, vulnerability scanning is an. Vulnerability scanners are automated tools that allow organizations to check if their networks, systems and applications have security weaknesses that could expose them to attacks. At the heart of a typical vulnerability management tool is a vulnerability scanner. The security scanning process consists of four steps: The scan consists of four stages: Vulnerability. Security Scan Process.
From www.clouddefense.ai
What is a Vulnerability Assessment? Security Scan Process Understand how vulnerability scanning works, and discover 4 stages of the vulnerability. Alongside vulnerability assessment, vulnerability scanning is an. Vulnerability scanning is an automated process to identify security flaws in networks, systems and applications, enabling remediation and enhancing. The scan consists of four stages: At the heart of a typical vulnerability management tool is a vulnerability scanner. Vulnerability scanning is. Security Scan Process.
From aws.amazon.com
How USAA built an Amazon S3 malware scanning solution AWS Security Scan Process The scan consists of four stages: At the heart of a typical vulnerability management tool is a vulnerability scanner. Vulnerability scanning is the process of discovering, analysing, and reporting security flaws and vulnerabilities. Vulnerability scanning is an automated process to identify security flaws in networks, systems and applications, enabling remediation and enhancing. Vulnerability scanning, also called “vulnerability assessment,” is the. Security Scan Process.
From www.rootshellsecurity.net
Vulnerability Management Process Flow Chart Rootshell Security Scan Process Understand how vulnerability scanning works, and discover 4 stages of the vulnerability. The security scanning process consists of four steps: Testing, analysis, assessment and remediation. Vulnerability scanning is an automated process to identify security flaws in networks, systems and applications, enabling remediation and enhancing. The scan consists of four stages: Vulnerability scanning is the process of discovering, analysing, and reporting. Security Scan Process.
From jfrog.com
Security vulnerability detection scan for CI/CD pipeline with JFrog Xray Security Scan Process Vulnerability scanning is an automated process to identify security flaws in networks, systems and applications, enabling remediation and enhancing. Vulnerability scanning, also called “vulnerability assessment,” is the process of evaluating networks or it assets for security. The scan consists of four stages: Vulnerability scanners are automated tools that allow organizations to check if their networks, systems and applications have security. Security Scan Process.
From www.eetimes.eu
London Heathrow Airport to Deploy mmWave Passenger Security Scanners Security Scan Process Vulnerability scanners are automated tools that allow organizations to check if their networks, systems and applications have security weaknesses that could expose them to attacks. The scan consists of four stages: Testing, analysis, assessment and remediation. The security scanning process consists of four steps: Alongside vulnerability assessment, vulnerability scanning is an. Vulnerability scanning is an automated process to identify security. Security Scan Process.
From www.intechopen.com
Android Application Security Scanning Process IntechOpen Security Scan Process At the heart of a typical vulnerability management tool is a vulnerability scanner. Alongside vulnerability assessment, vulnerability scanning is an. Understand how vulnerability scanning works, and discover 4 stages of the vulnerability. The scan consists of four stages: Testing, analysis, assessment and remediation. The security scanning process consists of four steps: Vulnerability scanners are automated tools that allow organizations to. Security Scan Process.
From www.alamy.com
woman face scan process security vector illustration Stock Vector Image Security Scan Process Vulnerability scanning, also called “vulnerability assessment,” is the process of evaluating networks or it assets for security. Vulnerability scanning is an automated process to identify security flaws in networks, systems and applications, enabling remediation and enhancing. Testing, analysis, assessment and remediation. The scan consists of four stages: Alongside vulnerability assessment, vulnerability scanning is an. Understand how vulnerability scanning works, and. Security Scan Process.
From www.dreamstime.com
Hi Tech Biometric Security Scan, Close Up of Woman Eye in Process of Security Scan Process The security scanning process consists of four steps: Vulnerability scanning is the process of discovering, analysing, and reporting security flaws and vulnerabilities. The scan consists of four stages: At the heart of a typical vulnerability management tool is a vulnerability scanner. Testing, analysis, assessment and remediation. Vulnerability scanners are automated tools that allow organizations to check if their networks, systems. Security Scan Process.
From www.scanforsecurity.com
Testing for GDPR Scan For Security Security Scan Process The security scanning process consists of four steps: The scan consists of four stages: Vulnerability scanning is the process of discovering, analysing, and reporting security flaws and vulnerabilities. At the heart of a typical vulnerability management tool is a vulnerability scanner. Alongside vulnerability assessment, vulnerability scanning is an. Testing, analysis, assessment and remediation. Vulnerability scanners are automated tools that allow. Security Scan Process.
From virtualarmour.com
7 Common Types of Cybersecurity Scans (& What They Tell You) Security Scan Process Vulnerability scanning is the process of discovering, analysing, and reporting security flaws and vulnerabilities. The security scanning process consists of four steps: Vulnerability scanners are automated tools that allow organizations to check if their networks, systems and applications have security weaknesses that could expose them to attacks. Alongside vulnerability assessment, vulnerability scanning is an. Vulnerability scanning, also called “vulnerability assessment,”. Security Scan Process.
From www.pandasecurity.com
What is a Vulnerability Assessment? Panda Security Security Scan Process Vulnerability scanning is the process of discovering, analysing, and reporting security flaws and vulnerabilities. Testing, analysis, assessment and remediation. Vulnerability scanning is an automated process to identify security flaws in networks, systems and applications, enabling remediation and enhancing. Understand how vulnerability scanning works, and discover 4 stages of the vulnerability. Vulnerability scanning, also called “vulnerability assessment,” is the process of. Security Scan Process.
From pentestmag.com
Vulnerability Assessment Security Scanning Process Pentestmag Security Scan Process Vulnerability scanners are automated tools that allow organizations to check if their networks, systems and applications have security weaknesses that could expose them to attacks. Vulnerability scanning is an automated process to identify security flaws in networks, systems and applications, enabling remediation and enhancing. Vulnerability scanning, also called “vulnerability assessment,” is the process of evaluating networks or it assets for. Security Scan Process.
From www.researchgate.net
Existing malware detection techniques. Download Scientific Diagram Security Scan Process Alongside vulnerability assessment, vulnerability scanning is an. Vulnerability scanning, also called “vulnerability assessment,” is the process of evaluating networks or it assets for security. At the heart of a typical vulnerability management tool is a vulnerability scanner. Testing, analysis, assessment and remediation. Understand how vulnerability scanning works, and discover 4 stages of the vulnerability. Vulnerability scanners are automated tools that. Security Scan Process.
From www.alamy.com
Fingerprint safety technology. Cyber security. Electrical board for Security Scan Process The security scanning process consists of four steps: Testing, analysis, assessment and remediation. Vulnerability scanning, also called “vulnerability assessment,” is the process of evaluating networks or it assets for security. Vulnerability scanners are automated tools that allow organizations to check if their networks, systems and applications have security weaknesses that could expose them to attacks. At the heart of a. Security Scan Process.
From www.researchgate.net
Barcode scanning in the dispensing process Download Scientific Diagram Security Scan Process Vulnerability scanning is the process of discovering, analysing, and reporting security flaws and vulnerabilities. Vulnerability scanners are automated tools that allow organizations to check if their networks, systems and applications have security weaknesses that could expose them to attacks. Understand how vulnerability scanning works, and discover 4 stages of the vulnerability. The scan consists of four stages: Vulnerability scanning, also. Security Scan Process.
From www.sapphire.net
Network Vulnerability Scanning Types & Tools Sapphire Security Scan Process Understand how vulnerability scanning works, and discover 4 stages of the vulnerability. Vulnerability scanning is an automated process to identify security flaws in networks, systems and applications, enabling remediation and enhancing. Vulnerability scanners are automated tools that allow organizations to check if their networks, systems and applications have security weaknesses that could expose them to attacks. Testing, analysis, assessment and. Security Scan Process.
From sysdig.com
12 Container Image Scanning Best Practices to Adopt Sysdig Security Scan Process Vulnerability scanners are automated tools that allow organizations to check if their networks, systems and applications have security weaknesses that could expose them to attacks. The scan consists of four stages: Understand how vulnerability scanning works, and discover 4 stages of the vulnerability. At the heart of a typical vulnerability management tool is a vulnerability scanner. Alongside vulnerability assessment, vulnerability. Security Scan Process.
From reconshell.com
Vulnerability Assessment and Security Scanning Process Security Scan Process Understand how vulnerability scanning works, and discover 4 stages of the vulnerability. Vulnerability scanners are automated tools that allow organizations to check if their networks, systems and applications have security weaknesses that could expose them to attacks. Testing, analysis, assessment and remediation. At the heart of a typical vulnerability management tool is a vulnerability scanner. The security scanning process consists. Security Scan Process.
From www.intruder.io
How To Perform A Vulnerability Assessment StepbyStep Security Scan Process Vulnerability scanning, also called “vulnerability assessment,” is the process of evaluating networks or it assets for security. The scan consists of four stages: Testing, analysis, assessment and remediation. At the heart of a typical vulnerability management tool is a vulnerability scanner. Vulnerability scanning is the process of discovering, analysing, and reporting security flaws and vulnerabilities. Alongside vulnerability assessment, vulnerability scanning. Security Scan Process.
From www.getastra.com
Vulnerability Scanning Process and Types Astra Security Blog Security Scan Process Vulnerability scanning is the process of discovering, analysing, and reporting security flaws and vulnerabilities. The scan consists of four stages: Alongside vulnerability assessment, vulnerability scanning is an. Vulnerability scanning is an automated process to identify security flaws in networks, systems and applications, enabling remediation and enhancing. Vulnerability scanning, also called “vulnerability assessment,” is the process of evaluating networks or it. Security Scan Process.
From www.splunk.com
Vulnerability Scanning The Complete Guide Splunk Security Scan Process At the heart of a typical vulnerability management tool is a vulnerability scanner. The scan consists of four stages: Alongside vulnerability assessment, vulnerability scanning is an. The security scanning process consists of four steps: Vulnerability scanning is the process of discovering, analysing, and reporting security flaws and vulnerabilities. Testing, analysis, assessment and remediation. Vulnerability scanning is an automated process to. Security Scan Process.