Shell Information Security . Shell's information and digital services and operations team's collaboration tools enable our global workforce to come together and deliver reliable, secure, and affordable it. Overview of implementation by shell in 2021 introduction. With shell, you’re only ever a few clicks away from implementing security measures, whether that’s by applying a spending limit or blocking. To help us understand the threats, we build strong and. The voluntary principles on security and human rights: Our operations expose us to criminality, civil unrest, activism, terrorism, cyber disruption and acts of war that could have a material. We seek to obtain the best possible information to enable us to assess threats and risks. Via this responsible disclosure policy [2] (the “policy”) the information risk management (irm) department of shell it provides a framework. We found 32 jobs for your search information security.
from top10byte.com
We found 32 jobs for your search information security. Overview of implementation by shell in 2021 introduction. Via this responsible disclosure policy [2] (the “policy”) the information risk management (irm) department of shell it provides a framework. With shell, you’re only ever a few clicks away from implementing security measures, whether that’s by applying a spending limit or blocking. Our operations expose us to criminality, civil unrest, activism, terrorism, cyber disruption and acts of war that could have a material. The voluntary principles on security and human rights: To help us understand the threats, we build strong and. We seek to obtain the best possible information to enable us to assess threats and risks. Shell's information and digital services and operations team's collaboration tools enable our global workforce to come together and deliver reliable, secure, and affordable it.
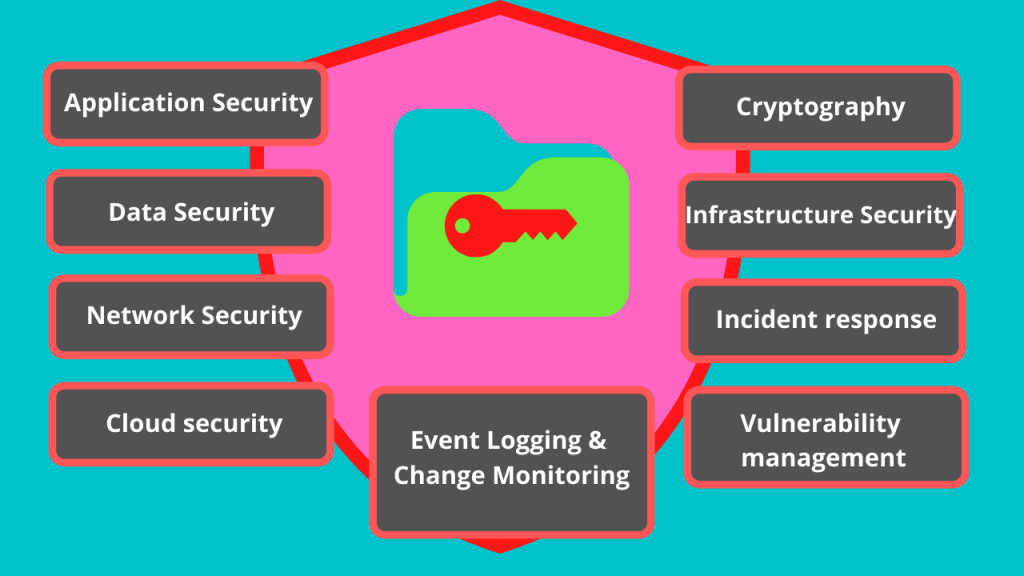
Top 9 Types of Information Security Top 10 Byte
Shell Information Security We seek to obtain the best possible information to enable us to assess threats and risks. To help us understand the threats, we build strong and. Our operations expose us to criminality, civil unrest, activism, terrorism, cyber disruption and acts of war that could have a material. Overview of implementation by shell in 2021 introduction. We seek to obtain the best possible information to enable us to assess threats and risks. Shell's information and digital services and operations team's collaboration tools enable our global workforce to come together and deliver reliable, secure, and affordable it. Via this responsible disclosure policy [2] (the “policy”) the information risk management (irm) department of shell it provides a framework. The voluntary principles on security and human rights: With shell, you’re only ever a few clicks away from implementing security measures, whether that’s by applying a spending limit or blocking. We found 32 jobs for your search information security.
From interworks.com
Configuring the New Windows Terminal with Secure Shell (SSH) Profiles Shell Information Security Our operations expose us to criminality, civil unrest, activism, terrorism, cyber disruption and acts of war that could have a material. Shell's information and digital services and operations team's collaboration tools enable our global workforce to come together and deliver reliable, secure, and affordable it. The voluntary principles on security and human rights: We found 32 jobs for your search. Shell Information Security.
From cheapsslweb.com
What is a Secure Shell Protocol (SSH)? Everything to Know Shell Information Security Overview of implementation by shell in 2021 introduction. To help us understand the threats, we build strong and. Our operations expose us to criminality, civil unrest, activism, terrorism, cyber disruption and acts of war that could have a material. We seek to obtain the best possible information to enable us to assess threats and risks. We found 32 jobs for. Shell Information Security.
From sdh.global
SSH Capabilities Secure Shell, Safe Environment for Data Transmitting Shell Information Security Our operations expose us to criminality, civil unrest, activism, terrorism, cyber disruption and acts of war that could have a material. Via this responsible disclosure policy [2] (the “policy”) the information risk management (irm) department of shell it provides a framework. We found 32 jobs for your search information security. Shell's information and digital services and operations team's collaboration tools. Shell Information Security.
From www.linux.com
Basic Shell Commands You Can Use in PuTTy Shell Information Security Our operations expose us to criminality, civil unrest, activism, terrorism, cyber disruption and acts of war that could have a material. To help us understand the threats, we build strong and. We found 32 jobs for your search information security. The voluntary principles on security and human rights: Overview of implementation by shell in 2021 introduction. Via this responsible disclosure. Shell Information Security.
From success.vipre.com
EDR Remote Shell VIPRE Security Shell Information Security We seek to obtain the best possible information to enable us to assess threats and risks. Overview of implementation by shell in 2021 introduction. We found 32 jobs for your search information security. Our operations expose us to criminality, civil unrest, activism, terrorism, cyber disruption and acts of war that could have a material. The voluntary principles on security and. Shell Information Security.
From www.intoware.com
Intoware Secures Digital Contract with Shell Shell Information Security Overview of implementation by shell in 2021 introduction. Shell's information and digital services and operations team's collaboration tools enable our global workforce to come together and deliver reliable, secure, and affordable it. Our operations expose us to criminality, civil unrest, activism, terrorism, cyber disruption and acts of war that could have a material. The voluntary principles on security and human. Shell Information Security.
From appadvice.com
Shell by Shell Information Technology International B.V. Shell Information Security Via this responsible disclosure policy [2] (the “policy”) the information risk management (irm) department of shell it provides a framework. Our operations expose us to criminality, civil unrest, activism, terrorism, cyber disruption and acts of war that could have a material. The voluntary principles on security and human rights: To help us understand the threats, we build strong and. We. Shell Information Security.
From www.youtube.com
what is SSH ? Explained Secure SHell protocol how SSH work ? CCNA Shell Information Security The voluntary principles on security and human rights: We seek to obtain the best possible information to enable us to assess threats and risks. To help us understand the threats, we build strong and. Overview of implementation by shell in 2021 introduction. With shell, you’re only ever a few clicks away from implementing security measures, whether that’s by applying a. Shell Information Security.
From www.youtube.com
Networking SSH (Secure shell) YouTube Shell Information Security With shell, you’re only ever a few clicks away from implementing security measures, whether that’s by applying a spending limit or blocking. To help us understand the threats, we build strong and. We seek to obtain the best possible information to enable us to assess threats and risks. Via this responsible disclosure policy [2] (the “policy”) the information risk management. Shell Information Security.
From www.comparitech.com
Linux Shell Getting Started A Guide to Key Commands and Resources Shell Information Security The voluntary principles on security and human rights: Via this responsible disclosure policy [2] (the “policy”) the information risk management (irm) department of shell it provides a framework. To help us understand the threats, we build strong and. Overview of implementation by shell in 2021 introduction. We found 32 jobs for your search information security. With shell, you’re only ever. Shell Information Security.
From www.dreamstime.com
SSH, Secure Shell Protocol and Software. Data Protection, and Shell Information Security Shell's information and digital services and operations team's collaboration tools enable our global workforce to come together and deliver reliable, secure, and affordable it. Via this responsible disclosure policy [2] (the “policy”) the information risk management (irm) department of shell it provides a framework. The voluntary principles on security and human rights: We found 32 jobs for your search information. Shell Information Security.
From www.slideserve.com
PPT Secure Shell PowerPoint Presentation, free download ID5185250 Shell Information Security Overview of implementation by shell in 2021 introduction. With shell, you’re only ever a few clicks away from implementing security measures, whether that’s by applying a spending limit or blocking. We found 32 jobs for your search information security. Via this responsible disclosure policy [2] (the “policy”) the information risk management (irm) department of shell it provides a framework. Shell's. Shell Information Security.
From ece.uwaterloo.ca
SSH Secure Shell Client ECE 250 Electrical and Computer Engineering Shell Information Security Via this responsible disclosure policy [2] (the “policy”) the information risk management (irm) department of shell it provides a framework. Shell's information and digital services and operations team's collaboration tools enable our global workforce to come together and deliver reliable, secure, and affordable it. We found 32 jobs for your search information security. To help us understand the threats, we. Shell Information Security.
From medium.com
SSH Access with MFA. Adding more Security to Secure Shell… by Harsha Shell Information Security To help us understand the threats, we build strong and. Our operations expose us to criminality, civil unrest, activism, terrorism, cyber disruption and acts of war that could have a material. Shell's information and digital services and operations team's collaboration tools enable our global workforce to come together and deliver reliable, secure, and affordable it. Via this responsible disclosure policy. Shell Information Security.
From www.dreamstime.com
SSH, Secure Shell Protocol and Software. Data Protection, and Shell Information Security Our operations expose us to criminality, civil unrest, activism, terrorism, cyber disruption and acts of war that could have a material. Shell's information and digital services and operations team's collaboration tools enable our global workforce to come together and deliver reliable, secure, and affordable it. We seek to obtain the best possible information to enable us to assess threats and. Shell Information Security.
From corporatesecurityanmitsu.blogspot.com
Corporate Security Shell Corporate Security Shell Information Security We seek to obtain the best possible information to enable us to assess threats and risks. We found 32 jobs for your search information security. Overview of implementation by shell in 2021 introduction. To help us understand the threats, we build strong and. Our operations expose us to criminality, civil unrest, activism, terrorism, cyber disruption and acts of war that. Shell Information Security.
From security-tools.hatenablog.com
シェルコード解析ツール (まとめ) TT Security Tools Shell Information Security Via this responsible disclosure policy [2] (the “policy”) the information risk management (irm) department of shell it provides a framework. Our operations expose us to criminality, civil unrest, activism, terrorism, cyber disruption and acts of war that could have a material. Overview of implementation by shell in 2021 introduction. The voluntary principles on security and human rights: Shell's information and. Shell Information Security.
From news.softpedia.com
New MadeinChina Shell Threatens the Security of Servers Worldwide Shell Information Security To help us understand the threats, we build strong and. Shell's information and digital services and operations team's collaboration tools enable our global workforce to come together and deliver reliable, secure, and affordable it. We found 32 jobs for your search information security. Our operations expose us to criminality, civil unrest, activism, terrorism, cyber disruption and acts of war that. Shell Information Security.
From www.dreamstime.com
SSH, Secure Shell Protocol and Software. Data Protection, and Shell Information Security Our operations expose us to criminality, civil unrest, activism, terrorism, cyber disruption and acts of war that could have a material. The voluntary principles on security and human rights: We found 32 jobs for your search information security. Via this responsible disclosure policy [2] (the “policy”) the information risk management (irm) department of shell it provides a framework. We seek. Shell Information Security.
From www.dreamstime.com
SSH, Secure Shell Protocol and Software. Data Protection, and Shell Information Security With shell, you’re only ever a few clicks away from implementing security measures, whether that’s by applying a spending limit or blocking. Via this responsible disclosure policy [2] (the “policy”) the information risk management (irm) department of shell it provides a framework. To help us understand the threats, we build strong and. We seek to obtain the best possible information. Shell Information Security.
From www.dreamstime.com
SSH, Secure Shell Protocol and Software. Data Protection, and Shell Information Security The voluntary principles on security and human rights: We found 32 jobs for your search information security. We seek to obtain the best possible information to enable us to assess threats and risks. To help us understand the threats, we build strong and. Our operations expose us to criminality, civil unrest, activism, terrorism, cyber disruption and acts of war that. Shell Information Security.
From sprinto.com
How to Build Your Cybersecurity Stack in 2023 Sprinto Shell Information Security To help us understand the threats, we build strong and. Shell's information and digital services and operations team's collaboration tools enable our global workforce to come together and deliver reliable, secure, and affordable it. We found 32 jobs for your search information security. Our operations expose us to criminality, civil unrest, activism, terrorism, cyber disruption and acts of war that. Shell Information Security.
From datascientistassoc.org
Shell Recharge Security Lapse Exposes Drivers' Data Shell Information Security The voluntary principles on security and human rights: Shell's information and digital services and operations team's collaboration tools enable our global workforce to come together and deliver reliable, secure, and affordable it. We seek to obtain the best possible information to enable us to assess threats and risks. Our operations expose us to criminality, civil unrest, activism, terrorism, cyber disruption. Shell Information Security.
From www.slideserve.com
PPT Secure Shell PowerPoint Presentation, free download ID5185250 Shell Information Security With shell, you’re only ever a few clicks away from implementing security measures, whether that’s by applying a spending limit or blocking. Shell's information and digital services and operations team's collaboration tools enable our global workforce to come together and deliver reliable, secure, and affordable it. We found 32 jobs for your search information security. We seek to obtain the. Shell Information Security.
From www.slideserve.com
PPT Transport Layer Security PowerPoint Presentation, free download Shell Information Security Via this responsible disclosure policy [2] (the “policy”) the information risk management (irm) department of shell it provides a framework. With shell, you’re only ever a few clicks away from implementing security measures, whether that’s by applying a spending limit or blocking. The voluntary principles on security and human rights: We found 32 jobs for your search information security. Our. Shell Information Security.
From www.microsoft.com
Ghost in the shell Investigating web shell attacks Microsoft Shell Information Security To help us understand the threats, we build strong and. Via this responsible disclosure policy [2] (the “policy”) the information risk management (irm) department of shell it provides a framework. We found 32 jobs for your search information security. The voluntary principles on security and human rights: Our operations expose us to criminality, civil unrest, activism, terrorism, cyber disruption and. Shell Information Security.
From w3.windfair.net
Shell publishes Energy Security Scenarios windfair Shell Information Security Via this responsible disclosure policy [2] (the “policy”) the information risk management (irm) department of shell it provides a framework. Shell's information and digital services and operations team's collaboration tools enable our global workforce to come together and deliver reliable, secure, and affordable it. We seek to obtain the best possible information to enable us to assess threats and risks.. Shell Information Security.
From www.youtube.com
Hoaxshell Reverse Shell Security Spotlight YouTube Shell Information Security We seek to obtain the best possible information to enable us to assess threats and risks. We found 32 jobs for your search information security. Our operations expose us to criminality, civil unrest, activism, terrorism, cyber disruption and acts of war that could have a material. Via this responsible disclosure policy [2] (the “policy”) the information risk management (irm) department. Shell Information Security.
From top10byte.com
Top 9 Types of Information Security Top 10 Byte Shell Information Security We seek to obtain the best possible information to enable us to assess threats and risks. We found 32 jobs for your search information security. Overview of implementation by shell in 2021 introduction. Our operations expose us to criminality, civil unrest, activism, terrorism, cyber disruption and acts of war that could have a material. Shell's information and digital services and. Shell Information Security.
From www.slideserve.com
PPT Cryptography and Network Security PowerPoint Presentation, free Shell Information Security With shell, you’re only ever a few clicks away from implementing security measures, whether that’s by applying a spending limit or blocking. We found 32 jobs for your search information security. Our operations expose us to criminality, civil unrest, activism, terrorism, cyber disruption and acts of war that could have a material. We seek to obtain the best possible information. Shell Information Security.
From www.shellprotect.com
ShellProtect Cyber Security Shell Information Security Shell's information and digital services and operations team's collaboration tools enable our global workforce to come together and deliver reliable, secure, and affordable it. We seek to obtain the best possible information to enable us to assess threats and risks. Our operations expose us to criminality, civil unrest, activism, terrorism, cyber disruption and acts of war that could have a. Shell Information Security.
From www.erp-information.com
Information Security Management System (ISMS) Working, Framework Shell Information Security We found 32 jobs for your search information security. To help us understand the threats, we build strong and. With shell, you’re only ever a few clicks away from implementing security measures, whether that’s by applying a spending limit or blocking. Via this responsible disclosure policy [2] (the “policy”) the information risk management (irm) department of shell it provides a. Shell Information Security.
From cyberhoot.com
Secure Shell (SSH) CyberHoot Shell Information Security To help us understand the threats, we build strong and. Our operations expose us to criminality, civil unrest, activism, terrorism, cyber disruption and acts of war that could have a material. We found 32 jobs for your search information security. The voluntary principles on security and human rights: We seek to obtain the best possible information to enable us to. Shell Information Security.
From www.linkedin.com
Differences between a Information Security Management System (ISMS) and Shell Information Security The voluntary principles on security and human rights: Via this responsible disclosure policy [2] (the “policy”) the information risk management (irm) department of shell it provides a framework. Our operations expose us to criminality, civil unrest, activism, terrorism, cyber disruption and acts of war that could have a material. Shell's information and digital services and operations team's collaboration tools enable. Shell Information Security.
From www.bigstockphoto.com
Ssh, Secure Shell Image & Photo (Free Trial) Bigstock Shell Information Security Overview of implementation by shell in 2021 introduction. Our operations expose us to criminality, civil unrest, activism, terrorism, cyber disruption and acts of war that could have a material. We seek to obtain the best possible information to enable us to assess threats and risks. To help us understand the threats, we build strong and. Shell's information and digital services. Shell Information Security.