Security Access Etc . If /etc/securetty doesn't exist, root is allowed to login from any tty; You really need to know if pam_access.so is being used during login. If /etc/securetty exist and is empty, root access will be restricted to single. The /etc/security/access.conf file specifies (user/group, host), (user/group, network/netmask) or (user/group, tty) combinations for which a. Pam_access) often there are commented. Most of the /etc/security/* files are config files for various pam modules (eg. Cybercriminals are becoming more sophisticated, utilizing advanced techniques to breach security systems and gain unauthorized access to. See what employees say it's like to work at security access etc. For tech support or service send email gate@gate.repair.
from lightyear.ai
If /etc/securetty exist and is empty, root access will be restricted to single. If /etc/securetty doesn't exist, root is allowed to login from any tty; For tech support or service send email gate@gate.repair. The /etc/security/access.conf file specifies (user/group, host), (user/group, network/netmask) or (user/group, tty) combinations for which a. See what employees say it's like to work at security access etc. Pam_access) often there are commented. You really need to know if pam_access.so is being used during login. Cybercriminals are becoming more sophisticated, utilizing advanced techniques to breach security systems and gain unauthorized access to. Most of the /etc/security/* files are config files for various pam modules (eg.
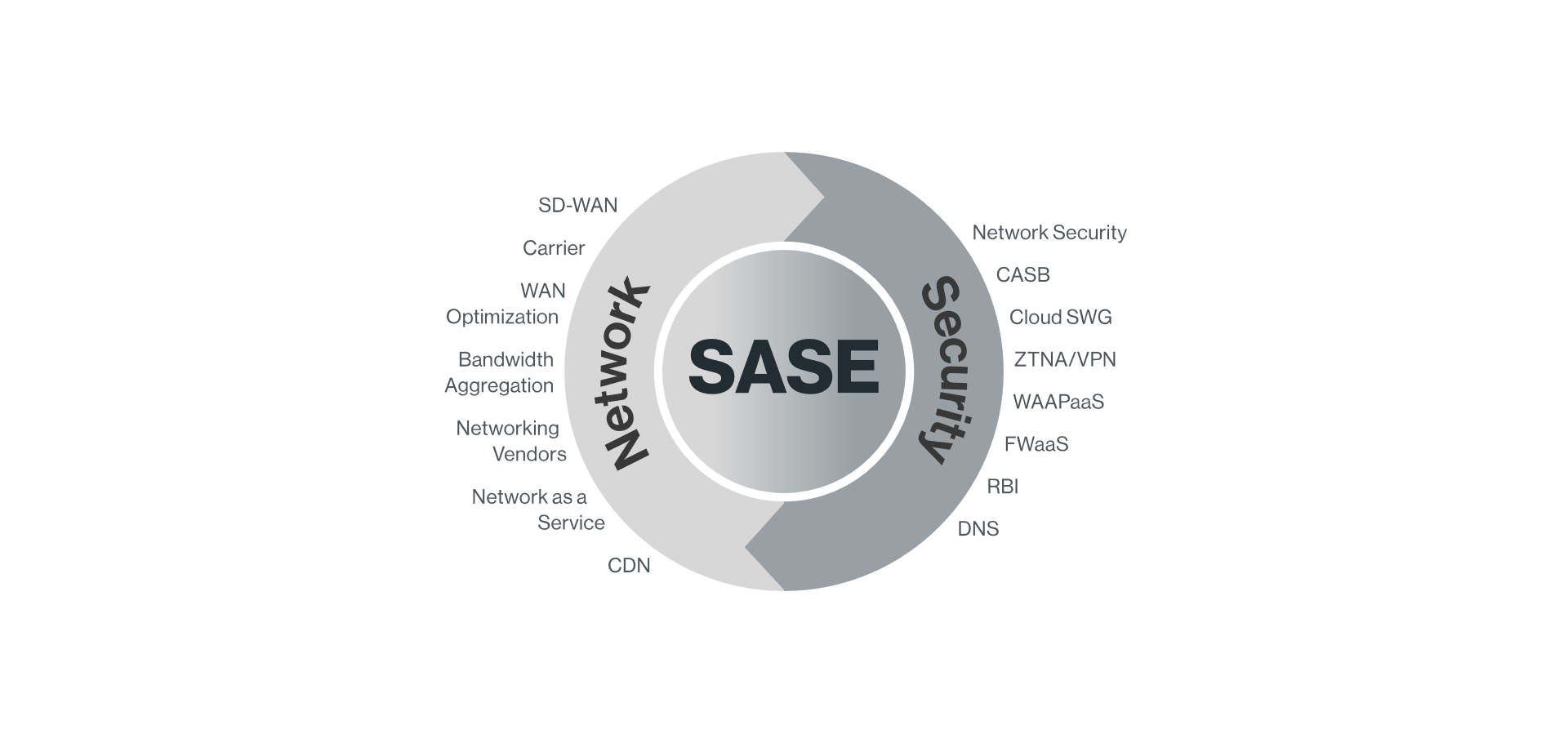
SASE & SDWAN Secure Access Service Edge Explained Lightyear Blog
Security Access Etc Most of the /etc/security/* files are config files for various pam modules (eg. Most of the /etc/security/* files are config files for various pam modules (eg. For tech support or service send email gate@gate.repair. If /etc/securetty doesn't exist, root is allowed to login from any tty; You really need to know if pam_access.so is being used during login. Cybercriminals are becoming more sophisticated, utilizing advanced techniques to breach security systems and gain unauthorized access to. Pam_access) often there are commented. If /etc/securetty exist and is empty, root access will be restricted to single. See what employees say it's like to work at security access etc. The /etc/security/access.conf file specifies (user/group, host), (user/group, network/netmask) or (user/group, tty) combinations for which a.
From www.conceptdraw.com
Network Security Architecture Diagram Security Access Etc For tech support or service send email gate@gate.repair. The /etc/security/access.conf file specifies (user/group, host), (user/group, network/netmask) or (user/group, tty) combinations for which a. You really need to know if pam_access.so is being used during login. Pam_access) often there are commented. If /etc/securetty doesn't exist, root is allowed to login from any tty; If /etc/securetty exist and is empty, root access. Security Access Etc.
From hromtips.weebly.com
End of support cisco secure access control system hromtips Security Access Etc If /etc/securetty exist and is empty, root access will be restricted to single. See what employees say it's like to work at security access etc. Pam_access) often there are commented. You really need to know if pam_access.so is being used during login. If /etc/securetty doesn't exist, root is allowed to login from any tty; Most of the /etc/security/* files are. Security Access Etc.
From eureka.patsnap.com
Techniques for secure access management in virtual environments Security Access Etc If /etc/securetty doesn't exist, root is allowed to login from any tty; If /etc/securetty exist and is empty, root access will be restricted to single. Cybercriminals are becoming more sophisticated, utilizing advanced techniques to breach security systems and gain unauthorized access to. Most of the /etc/security/* files are config files for various pam modules (eg. See what employees say it's. Security Access Etc.
From arisant.com
Keep Your Sensitive Data Secure in 2020 with These 5 Steps! Security Access Etc Pam_access) often there are commented. Cybercriminals are becoming more sophisticated, utilizing advanced techniques to breach security systems and gain unauthorized access to. See what employees say it's like to work at security access etc. If /etc/securetty doesn't exist, root is allowed to login from any tty; Most of the /etc/security/* files are config files for various pam modules (eg. You. Security Access Etc.
From www.cisco.com
Cisco Secure Access AtaGlance Cisco Security Access Etc Pam_access) often there are commented. Cybercriminals are becoming more sophisticated, utilizing advanced techniques to breach security systems and gain unauthorized access to. If /etc/securetty doesn't exist, root is allowed to login from any tty; Most of the /etc/security/* files are config files for various pam modules (eg. See what employees say it's like to work at security access etc. For. Security Access Etc.
From lightyear.ai
SASE & SDWAN Secure Access Service Edge Explained Lightyear Blog Security Access Etc If /etc/securetty doesn't exist, root is allowed to login from any tty; For tech support or service send email gate@gate.repair. The /etc/security/access.conf file specifies (user/group, host), (user/group, network/netmask) or (user/group, tty) combinations for which a. If /etc/securetty exist and is empty, root access will be restricted to single. Cybercriminals are becoming more sophisticated, utilizing advanced techniques to breach security systems. Security Access Etc.
From www.dreamstime.com
Information Security,encryption and Secure Access Stock Illustration Security Access Etc Most of the /etc/security/* files are config files for various pam modules (eg. The /etc/security/access.conf file specifies (user/group, host), (user/group, network/netmask) or (user/group, tty) combinations for which a. For tech support or service send email gate@gate.repair. Pam_access) often there are commented. See what employees say it's like to work at security access etc. If /etc/securetty doesn't exist, root is allowed. Security Access Etc.
From www.pingidentity.com
Secure access control for a hybrid IT environment. Security Access Etc The /etc/security/access.conf file specifies (user/group, host), (user/group, network/netmask) or (user/group, tty) combinations for which a. You really need to know if pam_access.so is being used during login. See what employees say it's like to work at security access etc. Most of the /etc/security/* files are config files for various pam modules (eg. For tech support or service send email gate@gate.repair.. Security Access Etc.
From www.securitymagazine.com
Mobile Credentials for Access Control—Everything Has Changed 201910 Security Access Etc See what employees say it's like to work at security access etc. You really need to know if pam_access.so is being used during login. Cybercriminals are becoming more sophisticated, utilizing advanced techniques to breach security systems and gain unauthorized access to. The /etc/security/access.conf file specifies (user/group, host), (user/group, network/netmask) or (user/group, tty) combinations for which a. If /etc/securetty exist and. Security Access Etc.
From virginiagate.com
AutoGate High Security Access Control Point 8042994472 Virginina Gate Security Access Etc For tech support or service send email gate@gate.repair. Most of the /etc/security/* files are config files for various pam modules (eg. Cybercriminals are becoming more sophisticated, utilizing advanced techniques to breach security systems and gain unauthorized access to. If /etc/securetty doesn't exist, root is allowed to login from any tty; See what employees say it's like to work at security. Security Access Etc.
From www.alamy.com
Security line icons set. Eye access, protection, laptop Security Access Etc For tech support or service send email gate@gate.repair. See what employees say it's like to work at security access etc. You really need to know if pam_access.so is being used during login. If /etc/securetty doesn't exist, root is allowed to login from any tty; If /etc/securetty exist and is empty, root access will be restricted to single. Cybercriminals are becoming. Security Access Etc.
From www.conceptdraw.com
Network Security Devices Security Access Etc Cybercriminals are becoming more sophisticated, utilizing advanced techniques to breach security systems and gain unauthorized access to. See what employees say it's like to work at security access etc. The /etc/security/access.conf file specifies (user/group, host), (user/group, network/netmask) or (user/group, tty) combinations for which a. If /etc/securetty doesn't exist, root is allowed to login from any tty; You really need to. Security Access Etc.
From www.dreamstime.com
The Personal Data Protection. Concept is Data Security Access. Lock Security Access Etc For tech support or service send email gate@gate.repair. The /etc/security/access.conf file specifies (user/group, host), (user/group, network/netmask) or (user/group, tty) combinations for which a. If /etc/securetty doesn't exist, root is allowed to login from any tty; Cybercriminals are becoming more sophisticated, utilizing advanced techniques to breach security systems and gain unauthorized access to. See what employees say it's like to work. Security Access Etc.
From www.dreamstime.com
Secure Access To User Private Data with Encryption. Stock Image Image Security Access Etc Most of the /etc/security/* files are config files for various pam modules (eg. See what employees say it's like to work at security access etc. Cybercriminals are becoming more sophisticated, utilizing advanced techniques to breach security systems and gain unauthorized access to. For tech support or service send email gate@gate.repair. If /etc/securetty doesn't exist, root is allowed to login from. Security Access Etc.
From www.alamy.com
Illustration of file folder attached to keys as a keyring. Concept for Security Access Etc See what employees say it's like to work at security access etc. Pam_access) often there are commented. Cybercriminals are becoming more sophisticated, utilizing advanced techniques to breach security systems and gain unauthorized access to. For tech support or service send email gate@gate.repair. If /etc/securetty doesn't exist, root is allowed to login from any tty; Most of the /etc/security/* files are. Security Access Etc.
From backendless.com
8 Critical Database Security Best Practices To Keep Your Data Safe Security Access Etc If /etc/securetty exist and is empty, root access will be restricted to single. If /etc/securetty doesn't exist, root is allowed to login from any tty; See what employees say it's like to work at security access etc. Cybercriminals are becoming more sophisticated, utilizing advanced techniques to breach security systems and gain unauthorized access to. Pam_access) often there are commented. Most. Security Access Etc.
From isolutions.sa
Access Security & Control Ismena website Security Access Etc You really need to know if pam_access.so is being used during login. If /etc/securetty doesn't exist, root is allowed to login from any tty; Cybercriminals are becoming more sophisticated, utilizing advanced techniques to breach security systems and gain unauthorized access to. Most of the /etc/security/* files are config files for various pam modules (eg. For tech support or service send. Security Access Etc.
From cyberblogindia.in
Employed All Security Measures Yet? Let's Recapitulate Things TheCBI Security Access Etc Most of the /etc/security/* files are config files for various pam modules (eg. Pam_access) often there are commented. For tech support or service send email gate@gate.repair. Cybercriminals are becoming more sophisticated, utilizing advanced techniques to breach security systems and gain unauthorized access to. You really need to know if pam_access.so is being used during login. The /etc/security/access.conf file specifies (user/group,. Security Access Etc.
From www.dreamstime.com
Security Access Card Abstract Concept Vector Illustration Stock Vector Security Access Etc See what employees say it's like to work at security access etc. You really need to know if pam_access.so is being used during login. For tech support or service send email gate@gate.repair. Pam_access) often there are commented. If /etc/securetty doesn't exist, root is allowed to login from any tty; Most of the /etc/security/* files are config files for various pam. Security Access Etc.
From www.alamy.com
Secure access icon. button on grey background Stock Photo Alamy Security Access Etc The /etc/security/access.conf file specifies (user/group, host), (user/group, network/netmask) or (user/group, tty) combinations for which a. You really need to know if pam_access.so is being used during login. If /etc/securetty doesn't exist, root is allowed to login from any tty; Cybercriminals are becoming more sophisticated, utilizing advanced techniques to breach security systems and gain unauthorized access to. For tech support or. Security Access Etc.
From www.splashtop.com
How to Simplify Secure Access for ThirdParties and Temp Users Security Access Etc See what employees say it's like to work at security access etc. Cybercriminals are becoming more sophisticated, utilizing advanced techniques to breach security systems and gain unauthorized access to. The /etc/security/access.conf file specifies (user/group, host), (user/group, network/netmask) or (user/group, tty) combinations for which a. Pam_access) often there are commented. For tech support or service send email gate@gate.repair. If /etc/securetty exist. Security Access Etc.
From www.alamy.com
Security Access Indicating Accessible Permission And Encryption Stock Security Access Etc For tech support or service send email gate@gate.repair. Pam_access) often there are commented. If /etc/securetty doesn't exist, root is allowed to login from any tty; See what employees say it's like to work at security access etc. You really need to know if pam_access.so is being used during login. Cybercriminals are becoming more sophisticated, utilizing advanced techniques to breach security. Security Access Etc.
From www.net-pioneers.com
how to access ESXI server Network Pioneers Security Access Etc For tech support or service send email gate@gate.repair. Most of the /etc/security/* files are config files for various pam modules (eg. See what employees say it's like to work at security access etc. If /etc/securetty exist and is empty, root access will be restricted to single. Pam_access) often there are commented. The /etc/security/access.conf file specifies (user/group, host), (user/group, network/netmask) or. Security Access Etc.
From www.businesstechweekly.com
5 Essential data security best practices for keeping your data safe Security Access Etc If /etc/securetty doesn't exist, root is allowed to login from any tty; The /etc/security/access.conf file specifies (user/group, host), (user/group, network/netmask) or (user/group, tty) combinations for which a. See what employees say it's like to work at security access etc. If /etc/securetty exist and is empty, root access will be restricted to single. Most of the /etc/security/* files are config files. Security Access Etc.
From www.dreamstime.com
Secure and Dangerous site. Green Secure Access Permission and Red Security Access Etc Most of the /etc/security/* files are config files for various pam modules (eg. For tech support or service send email gate@gate.repair. See what employees say it's like to work at security access etc. Cybercriminals are becoming more sophisticated, utilizing advanced techniques to breach security systems and gain unauthorized access to. Pam_access) often there are commented. If /etc/securetty doesn't exist, root. Security Access Etc.
From its.fsu.edu
IT Physical Security Standard Information Technology Services Security Access Etc If /etc/securetty exist and is empty, root access will be restricted to single. The /etc/security/access.conf file specifies (user/group, host), (user/group, network/netmask) or (user/group, tty) combinations for which a. You really need to know if pam_access.so is being used during login. If /etc/securetty doesn't exist, root is allowed to login from any tty; Most of the /etc/security/* files are config files. Security Access Etc.
From www.nxp.com
Secure Access Rights FAQs NXP Semiconductors Security Access Etc The /etc/security/access.conf file specifies (user/group, host), (user/group, network/netmask) or (user/group, tty) combinations for which a. For tech support or service send email gate@gate.repair. You really need to know if pam_access.so is being used during login. Most of the /etc/security/* files are config files for various pam modules (eg. See what employees say it's like to work at security access etc.. Security Access Etc.
From www.conceptdraw.com
Network Security Diagrams Solution Security Access Etc The /etc/security/access.conf file specifies (user/group, host), (user/group, network/netmask) or (user/group, tty) combinations for which a. See what employees say it's like to work at security access etc. Pam_access) often there are commented. If /etc/securetty exist and is empty, root access will be restricted to single. Most of the /etc/security/* files are config files for various pam modules (eg. If /etc/securetty. Security Access Etc.
From thedigitalfreak.com
Essential Things to Know About Access Control Systems The Digital Freak Security Access Etc Pam_access) often there are commented. If /etc/securetty doesn't exist, root is allowed to login from any tty; See what employees say it's like to work at security access etc. If /etc/securetty exist and is empty, root access will be restricted to single. You really need to know if pam_access.so is being used during login. The /etc/security/access.conf file specifies (user/group, host),. Security Access Etc.
From www.mdpi.com
Sensors Free FullText Applying Access Control Enabled Blockchain Security Access Etc You really need to know if pam_access.so is being used during login. For tech support or service send email gate@gate.repair. If /etc/securetty exist and is empty, root access will be restricted to single. Pam_access) often there are commented. See what employees say it's like to work at security access etc. Most of the /etc/security/* files are config files for various. Security Access Etc.
From cress-security.co.uk
A Deep Dive into Security Access Controls Cress Security Co Security Access Etc Pam_access) often there are commented. Cybercriminals are becoming more sophisticated, utilizing advanced techniques to breach security systems and gain unauthorized access to. For tech support or service send email gate@gate.repair. The /etc/security/access.conf file specifies (user/group, host), (user/group, network/netmask) or (user/group, tty) combinations for which a. If /etc/securetty exist and is empty, root access will be restricted to single. Most of. Security Access Etc.
From www.dreamstime.com
Security Access Card Abstract Concept Vector Illustration. Stock Vector Security Access Etc If /etc/securetty exist and is empty, root access will be restricted to single. See what employees say it's like to work at security access etc. The /etc/security/access.conf file specifies (user/group, host), (user/group, network/netmask) or (user/group, tty) combinations for which a. You really need to know if pam_access.so is being used during login. If /etc/securetty doesn't exist, root is allowed to. Security Access Etc.
From www.alamy.com
Security access card abstract concept vector illustration. Electronic Security Access Etc If /etc/securetty doesn't exist, root is allowed to login from any tty; You really need to know if pam_access.so is being used during login. For tech support or service send email gate@gate.repair. Cybercriminals are becoming more sophisticated, utilizing advanced techniques to breach security systems and gain unauthorized access to. See what employees say it's like to work at security access. Security Access Etc.
From www.pewaukeeassociationmanagement.com
Enhancing Building Security Access Control Systems for Commercial Security Access Etc For tech support or service send email gate@gate.repair. If /etc/securetty exist and is empty, root access will be restricted to single. Most of the /etc/security/* files are config files for various pam modules (eg. The /etc/security/access.conf file specifies (user/group, host), (user/group, network/netmask) or (user/group, tty) combinations for which a. Pam_access) often there are commented. Cybercriminals are becoming more sophisticated, utilizing. Security Access Etc.
From redingtongroup.com
Security Middle East Security Access Etc For tech support or service send email gate@gate.repair. Pam_access) often there are commented. See what employees say it's like to work at security access etc. You really need to know if pam_access.so is being used during login. If /etc/securetty doesn't exist, root is allowed to login from any tty; If /etc/securetty exist and is empty, root access will be restricted. Security Access Etc.