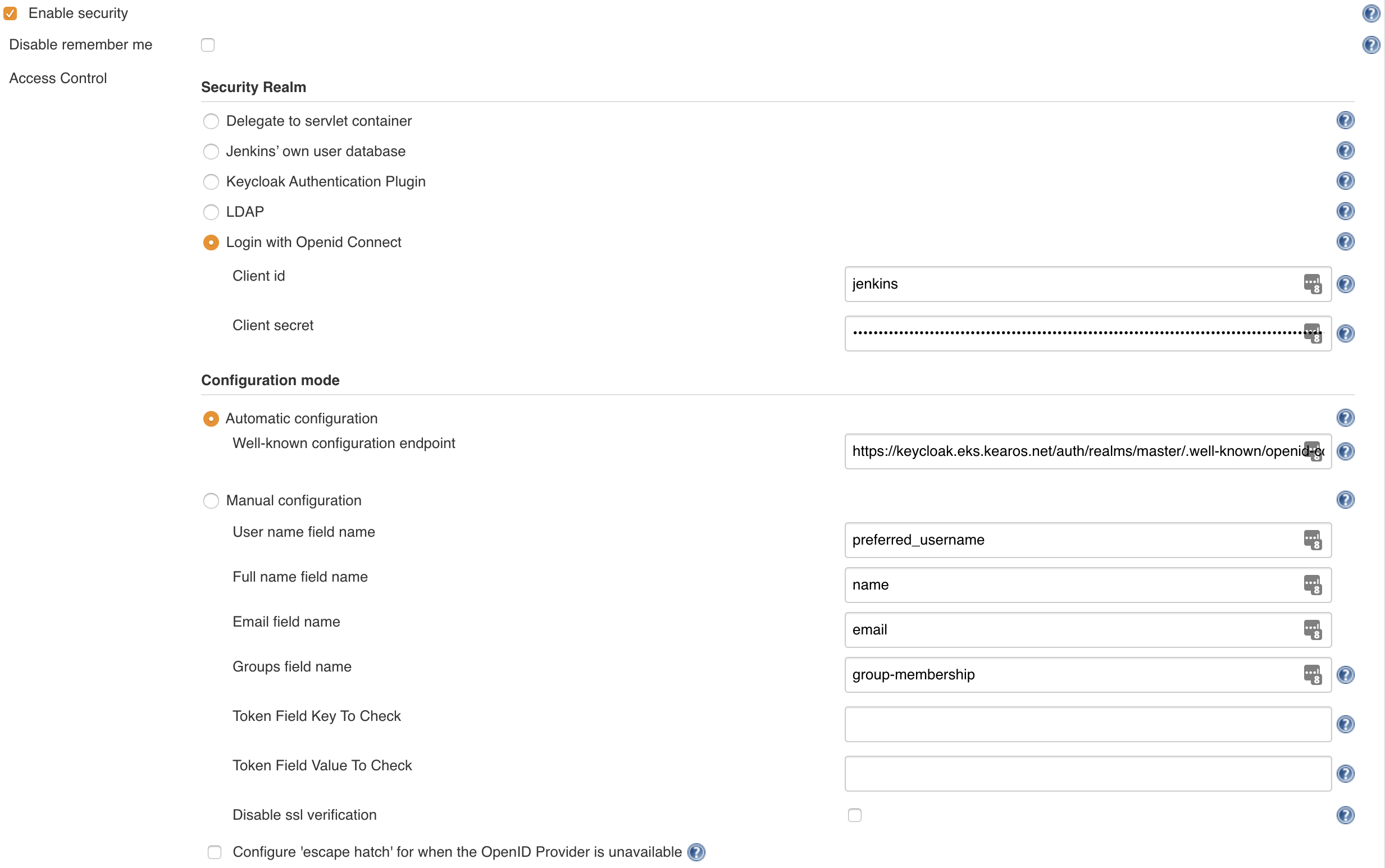
Keycloak Well Known Configuration . Basic steps to secure applications and services. It lists endpoints and other configuration. It lists endpoints and other configuration. It lists endpoints and other configuration. One running on port 8080 and the other on port 8081. Edit this section report an issue. Keycloak on 8080 will be my borker. These are the basic steps for securing an. openid providers supporting discovery must make a json document available at the path formed by concatenating the string. setup two keycloaks.
from joostvdg.github.io
openid providers supporting discovery must make a json document available at the path formed by concatenating the string. It lists endpoints and other configuration. One running on port 8080 and the other on port 8081. These are the basic steps for securing an. Basic steps to secure applications and services. Keycloak on 8080 will be my borker. It lists endpoints and other configuration. It lists endpoints and other configuration. setup two keycloaks. Edit this section report an issue.
SSO Jenkins With Keycloak On J's Software Development Pages
Keycloak Well Known Configuration openid providers supporting discovery must make a json document available at the path formed by concatenating the string. Edit this section report an issue. One running on port 8080 and the other on port 8081. Keycloak on 8080 will be my borker. These are the basic steps for securing an. setup two keycloaks. It lists endpoints and other configuration. Basic steps to secure applications and services. openid providers supporting discovery must make a json document available at the path formed by concatenating the string. It lists endpoints and other configuration. It lists endpoints and other configuration.
From help.hcltechsw.com
Sample KeyCloak configuration as an OIDC provider for Domino Keycloak Well Known Configuration It lists endpoints and other configuration. setup two keycloaks. Keycloak on 8080 will be my borker. openid providers supporting discovery must make a json document available at the path formed by concatenating the string. It lists endpoints and other configuration. Edit this section report an issue. These are the basic steps for securing an. One running on port. Keycloak Well Known Configuration.
From github.com
keycloak(behind nginx) .wellknown/openidconfiguration path not return Keycloak Well Known Configuration It lists endpoints and other configuration. Basic steps to secure applications and services. setup two keycloaks. Edit this section report an issue. openid providers supporting discovery must make a json document available at the path formed by concatenating the string. It lists endpoints and other configuration. Keycloak on 8080 will be my borker. One running on port 8080. Keycloak Well Known Configuration.
From guides.micronaut.io
Secure a Micronaut application with Keycloak Keycloak Well Known Configuration Basic steps to secure applications and services. Keycloak on 8080 will be my borker. It lists endpoints and other configuration. These are the basic steps for securing an. One running on port 8080 and the other on port 8081. It lists endpoints and other configuration. It lists endpoints and other configuration. openid providers supporting discovery must make a json. Keycloak Well Known Configuration.
From joostvdg.github.io
SSO Jenkins With Keycloak On J's Software Development Pages Keycloak Well Known Configuration Basic steps to secure applications and services. Keycloak on 8080 will be my borker. These are the basic steps for securing an. Edit this section report an issue. openid providers supporting discovery must make a json document available at the path formed by concatenating the string. It lists endpoints and other configuration. It lists endpoints and other configuration. It. Keycloak Well Known Configuration.
From blog.mei-home.net
SSO with Keycloak in the Homelab ln help Keycloak Well Known Configuration openid providers supporting discovery must make a json document available at the path formed by concatenating the string. Basic steps to secure applications and services. It lists endpoints and other configuration. These are the basic steps for securing an. It lists endpoints and other configuration. It lists endpoints and other configuration. Keycloak on 8080 will be my borker. One. Keycloak Well Known Configuration.
From ultimatesecurity.pro
Keycloak with Okta OpenID Connect Provider · Ultimate Security Keycloak Well Known Configuration These are the basic steps for securing an. Basic steps to secure applications and services. Edit this section report an issue. setup two keycloaks. It lists endpoints and other configuration. It lists endpoints and other configuration. One running on port 8080 and the other on port 8081. It lists endpoints and other configuration. Keycloak on 8080 will be my. Keycloak Well Known Configuration.
From zhuanlan.zhihu.com
使用Spring Gateway和KeyCloak构建一个OIDC认证系统 知乎 Keycloak Well Known Configuration One running on port 8080 and the other on port 8081. openid providers supporting discovery must make a json document available at the path formed by concatenating the string. Basic steps to secure applications and services. Edit this section report an issue. It lists endpoints and other configuration. It lists endpoints and other configuration. setup two keycloaks. Keycloak. Keycloak Well Known Configuration.
From www.hotzxgirl.com
Well Known Openid Configuration Keycloak Tutorial Pics Hot Sex Picture Keycloak Well Known Configuration One running on port 8080 and the other on port 8081. It lists endpoints and other configuration. These are the basic steps for securing an. It lists endpoints and other configuration. openid providers supporting discovery must make a json document available at the path formed by concatenating the string. setup two keycloaks. It lists endpoints and other configuration.. Keycloak Well Known Configuration.
From www.olivercoding.com
at home Part 6 Keycloak authentication and Azure Active Keycloak Well Known Configuration Keycloak on 8080 will be my borker. It lists endpoints and other configuration. It lists endpoints and other configuration. One running on port 8080 and the other on port 8081. Edit this section report an issue. Basic steps to secure applications and services. These are the basic steps for securing an. setup two keycloaks. It lists endpoints and other. Keycloak Well Known Configuration.
From blog.mei-home.net
SSO with Keycloak in the Homelab ln help Keycloak Well Known Configuration openid providers supporting discovery must make a json document available at the path formed by concatenating the string. Edit this section report an issue. Keycloak on 8080 will be my borker. One running on port 8080 and the other on port 8081. setup two keycloaks. It lists endpoints and other configuration. Basic steps to secure applications and services.. Keycloak Well Known Configuration.
From zhuanlan.zhihu.com
keycloak实践(postgresql/harbor/gitlab) 知乎 Keycloak Well Known Configuration It lists endpoints and other configuration. Edit this section report an issue. Basic steps to secure applications and services. It lists endpoints and other configuration. These are the basic steps for securing an. setup two keycloaks. One running on port 8080 and the other on port 8081. openid providers supporting discovery must make a json document available at. Keycloak Well Known Configuration.
From docs.getunleash.io
How to set up Keycloak and Unleash to sync user groups Unleash Keycloak Well Known Configuration It lists endpoints and other configuration. Edit this section report an issue. Basic steps to secure applications and services. It lists endpoints and other configuration. openid providers supporting discovery must make a json document available at the path formed by concatenating the string. Keycloak on 8080 will be my borker. One running on port 8080 and the other on. Keycloak Well Known Configuration.
From blog.csdn.net
keycloak 认证服务_uma_protection_woxinqidai的博客CSDN博客 Keycloak Well Known Configuration It lists endpoints and other configuration. setup two keycloaks. It lists endpoints and other configuration. These are the basic steps for securing an. One running on port 8080 and the other on port 8081. openid providers supporting discovery must make a json document available at the path formed by concatenating the string. Edit this section report an issue.. Keycloak Well Known Configuration.
From ultimatesecurity.pro
Keycloak with Okta OpenID Connect Provider · Ultimate Security Keycloak Well Known Configuration setup two keycloaks. Keycloak on 8080 will be my borker. It lists endpoints and other configuration. It lists endpoints and other configuration. These are the basic steps for securing an. It lists endpoints and other configuration. openid providers supporting discovery must make a json document available at the path formed by concatenating the string. One running on port. Keycloak Well Known Configuration.
From www.packtpub.com
Keycloak Identity and Access Management for Modern Applications Packt Keycloak Well Known Configuration openid providers supporting discovery must make a json document available at the path formed by concatenating the string. These are the basic steps for securing an. Keycloak on 8080 will be my borker. Basic steps to secure applications and services. It lists endpoints and other configuration. It lists endpoints and other configuration. Edit this section report an issue. . Keycloak Well Known Configuration.
From zhuanlan.zhihu.com
keycloak实践(postgresql/harbor/gitlab) 知乎 Keycloak Well Known Configuration Edit this section report an issue. setup two keycloaks. openid providers supporting discovery must make a json document available at the path formed by concatenating the string. It lists endpoints and other configuration. It lists endpoints and other configuration. These are the basic steps for securing an. Keycloak on 8080 will be my borker. One running on port. Keycloak Well Known Configuration.
From github.com
Mixed http & https URLs in .wellknown/openidconfiguration response Keycloak Well Known Configuration It lists endpoints and other configuration. Edit this section report an issue. It lists endpoints and other configuration. setup two keycloaks. Keycloak on 8080 will be my borker. One running on port 8080 and the other on port 8081. It lists endpoints and other configuration. Basic steps to secure applications and services. openid providers supporting discovery must make. Keycloak Well Known Configuration.
From sis-cc.gitlab.io
Keycloak configuration .Stat Suite documentation Keycloak Well Known Configuration These are the basic steps for securing an. Edit this section report an issue. It lists endpoints and other configuration. setup two keycloaks. It lists endpoints and other configuration. One running on port 8080 and the other on port 8081. Basic steps to secure applications and services. It lists endpoints and other configuration. openid providers supporting discovery must. Keycloak Well Known Configuration.
From www.puppeteers.net
Keycloak authorization services terminology Puppeteers Oy Keycloak Well Known Configuration Basic steps to secure applications and services. It lists endpoints and other configuration. It lists endpoints and other configuration. Keycloak on 8080 will be my borker. It lists endpoints and other configuration. setup two keycloaks. One running on port 8080 and the other on port 8081. Edit this section report an issue. These are the basic steps for securing. Keycloak Well Known Configuration.
From wiki.resolution.de
Keycloak configuration User & Group Sync Keycloak Well Known Configuration These are the basic steps for securing an. Basic steps to secure applications and services. It lists endpoints and other configuration. It lists endpoints and other configuration. It lists endpoints and other configuration. openid providers supporting discovery must make a json document available at the path formed by concatenating the string. setup two keycloaks. One running on port. Keycloak Well Known Configuration.
From keycloak.discourse.group
Configuring LDAPS for Active Directory Securing applications Keycloak Keycloak Well Known Configuration Keycloak on 8080 will be my borker. It lists endpoints and other configuration. setup two keycloaks. openid providers supporting discovery must make a json document available at the path formed by concatenating the string. Basic steps to secure applications and services. One running on port 8080 and the other on port 8081. Edit this section report an issue.. Keycloak Well Known Configuration.
From www.purewl.com
SSO & IAM Service KeyCloak, All You Need To Know About PureWL Keycloak Well Known Configuration It lists endpoints and other configuration. These are the basic steps for securing an. setup two keycloaks. Keycloak on 8080 will be my borker. Edit this section report an issue. Basic steps to secure applications and services. It lists endpoints and other configuration. One running on port 8080 and the other on port 8081. It lists endpoints and other. Keycloak Well Known Configuration.
From zhuanlan.zhihu.com
使用 Keycloak 接管 SpringBoot 应用的用户认证功能 知乎 Keycloak Well Known Configuration setup two keycloaks. It lists endpoints and other configuration. It lists endpoints and other configuration. These are the basic steps for securing an. Basic steps to secure applications and services. openid providers supporting discovery must make a json document available at the path formed by concatenating the string. One running on port 8080 and the other on port. Keycloak Well Known Configuration.
From blog.joostvdg.net
Azure Entra SSO for TAP GUI via Keycloak Joostvdg Blog Keycloak Well Known Configuration Keycloak on 8080 will be my borker. One running on port 8080 and the other on port 8081. It lists endpoints and other configuration. openid providers supporting discovery must make a json document available at the path formed by concatenating the string. Basic steps to secure applications and services. These are the basic steps for securing an. It lists. Keycloak Well Known Configuration.
From docs.sysreptor.com
Keycloak OIDC Configuration SysReptor Keycloak Well Known Configuration One running on port 8080 and the other on port 8081. These are the basic steps for securing an. setup two keycloaks. openid providers supporting discovery must make a json document available at the path formed by concatenating the string. It lists endpoints and other configuration. It lists endpoints and other configuration. Keycloak on 8080 will be my. Keycloak Well Known Configuration.
From documentation.eccenca.com
Configure Corporate Memory with an external Keycloak documentation Keycloak Well Known Configuration It lists endpoints and other configuration. Basic steps to secure applications and services. Keycloak on 8080 will be my borker. These are the basic steps for securing an. setup two keycloaks. openid providers supporting discovery must make a json document available at the path formed by concatenating the string. One running on port 8080 and the other on. Keycloak Well Known Configuration.
From wiki.resolution.de
Keycloak configuration User & Group Sync Keycloak Well Known Configuration setup two keycloaks. It lists endpoints and other configuration. openid providers supporting discovery must make a json document available at the path formed by concatenating the string. One running on port 8080 and the other on port 8081. It lists endpoints and other configuration. These are the basic steps for securing an. Basic steps to secure applications and. Keycloak Well Known Configuration.
From blog.csdn.net
认证和授权系列主题:keycloak界面配置及认证流程详解_keycloak认证流程CSDN博客 Keycloak Well Known Configuration Basic steps to secure applications and services. It lists endpoints and other configuration. Edit this section report an issue. One running on port 8080 and the other on port 8081. It lists endpoints and other configuration. These are the basic steps for securing an. It lists endpoints and other configuration. Keycloak on 8080 will be my borker. openid providers. Keycloak Well Known Configuration.
From stackoverflow.com
How can I know the Keycloak version? Stack Overflow Keycloak Well Known Configuration setup two keycloaks. It lists endpoints and other configuration. These are the basic steps for securing an. It lists endpoints and other configuration. openid providers supporting discovery must make a json document available at the path formed by concatenating the string. Keycloak on 8080 will be my borker. One running on port 8080 and the other on port. Keycloak Well Known Configuration.
From docs.budibase.com
SSO with Keycloak Keycloak Well Known Configuration openid providers supporting discovery must make a json document available at the path formed by concatenating the string. It lists endpoints and other configuration. One running on port 8080 and the other on port 8081. Keycloak on 8080 will be my borker. These are the basic steps for securing an. setup two keycloaks. It lists endpoints and other. Keycloak Well Known Configuration.
From siweheee.medium.com
Keycloak A real Scenario from Development to Production by Wei He Keycloak Well Known Configuration openid providers supporting discovery must make a json document available at the path formed by concatenating the string. These are the basic steps for securing an. Edit this section report an issue. It lists endpoints and other configuration. One running on port 8080 and the other on port 8081. It lists endpoints and other configuration. setup two keycloaks.. Keycloak Well Known Configuration.
From github.com
keycloakweb/security.ftl at main · keycloak/keycloakweb · GitHub Keycloak Well Known Configuration It lists endpoints and other configuration. These are the basic steps for securing an. It lists endpoints and other configuration. It lists endpoints and other configuration. Basic steps to secure applications and services. One running on port 8080 and the other on port 8081. Keycloak on 8080 will be my borker. openid providers supporting discovery must make a json. Keycloak Well Known Configuration.
From www.pkimber.net
Keycloak — Keycloak Well Known Configuration It lists endpoints and other configuration. Edit this section report an issue. These are the basic steps for securing an. openid providers supporting discovery must make a json document available at the path formed by concatenating the string. Keycloak on 8080 will be my borker. Basic steps to secure applications and services. One running on port 8080 and the. Keycloak Well Known Configuration.
From zhuanlan.zhihu.com
使用Spring Gateway和KeyCloak构建一个OIDC认证系统 知乎 Keycloak Well Known Configuration openid providers supporting discovery must make a json document available at the path formed by concatenating the string. Keycloak on 8080 will be my borker. It lists endpoints and other configuration. Edit this section report an issue. It lists endpoints and other configuration. Basic steps to secure applications and services. One running on port 8080 and the other on. Keycloak Well Known Configuration.
From sis-cc.gitlab.io
Keycloak configuration .Stat Suite documentation Keycloak Well Known Configuration setup two keycloaks. It lists endpoints and other configuration. openid providers supporting discovery must make a json document available at the path formed by concatenating the string. Keycloak on 8080 will be my borker. Basic steps to secure applications and services. It lists endpoints and other configuration. Edit this section report an issue. One running on port 8080. Keycloak Well Known Configuration.