Lab Simulation 9-1 Improve A Workstation's Resistance To Attack . Quizlet has study tools to help you learn anything. In this home lab project, my focus is to create a realistic environment where multiple endpoints could interact securely, simulate an. Cuaderno practica por niveles 2, revised. Which system applet did you use. Quizlet has study tools to help you learn anything. View project secure workstation.docx from bis 320 at indiana wesleyan university, marion. Note the resul ts in the top. The activities you performed in this lab are all examples of this type of security. With the testing from excercise 1 completed, we can begin to explore the resul ts of the emulation. In march 2019, network security monitoring tools alerted that a windows computer on the network was infected with malware.
from plotly.com
In march 2019, network security monitoring tools alerted that a windows computer on the network was infected with malware. Quizlet has study tools to help you learn anything. With the testing from excercise 1 completed, we can begin to explore the resul ts of the emulation. Which system applet did you use. View project secure workstation.docx from bis 320 at indiana wesleyan university, marion. Quizlet has study tools to help you learn anything. The activities you performed in this lab are all examples of this type of security. Cuaderno practica por niveles 2, revised. Note the resul ts in the top. In this home lab project, my focus is to create a realistic environment where multiple endpoints could interact securely, simulate an.
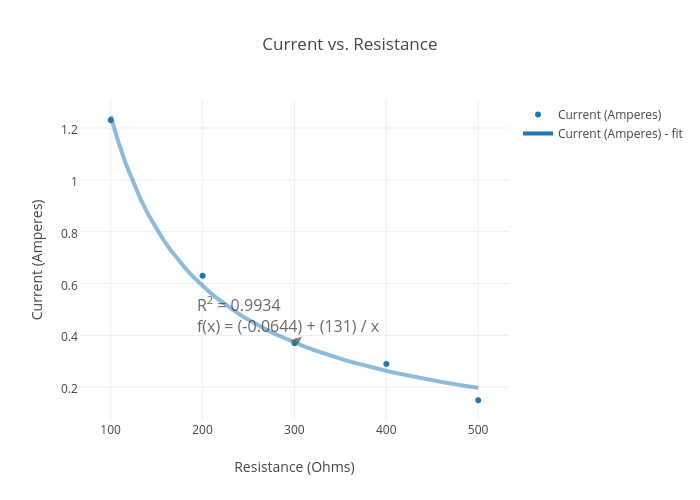
Current vs. Resistance scatter chart made by Avillatte131 plotly
Lab Simulation 9-1 Improve A Workstation's Resistance To Attack Which system applet did you use. Note the resul ts in the top. With the testing from excercise 1 completed, we can begin to explore the resul ts of the emulation. In this home lab project, my focus is to create a realistic environment where multiple endpoints could interact securely, simulate an. In march 2019, network security monitoring tools alerted that a windows computer on the network was infected with malware. Quizlet has study tools to help you learn anything. The activities you performed in this lab are all examples of this type of security. Quizlet has study tools to help you learn anything. View project secure workstation.docx from bis 320 at indiana wesleyan university, marion. Which system applet did you use. Cuaderno practica por niveles 2, revised.
From www.sciencephoto.com
Laboratory icons, illustrations Stock Image F019/8882 Science Lab Simulation 9-1 Improve A Workstation's Resistance To Attack The activities you performed in this lab are all examples of this type of security. In this home lab project, my focus is to create a realistic environment where multiple endpoints could interact securely, simulate an. Note the resul ts in the top. Which system applet did you use. Cuaderno practica por niveles 2, revised. View project secure workstation.docx from. Lab Simulation 9-1 Improve A Workstation's Resistance To Attack.
From schematicfixsecures.z21.web.core.windows.net
Power Volts And Resistance Lab Simulation 9-1 Improve A Workstation's Resistance To Attack Note the resul ts in the top. The activities you performed in this lab are all examples of this type of security. In this home lab project, my focus is to create a realistic environment where multiple endpoints could interact securely, simulate an. View project secure workstation.docx from bis 320 at indiana wesleyan university, marion. Quizlet has study tools to. Lab Simulation 9-1 Improve A Workstation's Resistance To Attack.
From www.altamira.ai
Benefits of Using Simulation Training in Corporate Learning Altamira Lab Simulation 9-1 Improve A Workstation's Resistance To Attack In march 2019, network security monitoring tools alerted that a windows computer on the network was infected with malware. Note the resul ts in the top. Which system applet did you use. Quizlet has study tools to help you learn anything. View project secure workstation.docx from bis 320 at indiana wesleyan university, marion. Cuaderno practica por niveles 2, revised. Quizlet. Lab Simulation 9-1 Improve A Workstation's Resistance To Attack.
From www.frontiersin.org
Frontiers Resistance Exercise Training as a Primary Countermeasure to Lab Simulation 9-1 Improve A Workstation's Resistance To Attack In this home lab project, my focus is to create a realistic environment where multiple endpoints could interact securely, simulate an. Quizlet has study tools to help you learn anything. The activities you performed in this lab are all examples of this type of security. With the testing from excercise 1 completed, we can begin to explore the resul ts. Lab Simulation 9-1 Improve A Workstation's Resistance To Attack.
From www.youtube.com
cpu simulation YouTube Lab Simulation 9-1 Improve A Workstation's Resistance To Attack The activities you performed in this lab are all examples of this type of security. In march 2019, network security monitoring tools alerted that a windows computer on the network was infected with malware. With the testing from excercise 1 completed, we can begin to explore the resul ts of the emulation. Note the resul ts in the top. Cuaderno. Lab Simulation 9-1 Improve A Workstation's Resistance To Attack.
From fyoxdyadv.blob.core.windows.net
Small Workstation Furniture at Rita Sanders blog Lab Simulation 9-1 Improve A Workstation's Resistance To Attack In this home lab project, my focus is to create a realistic environment where multiple endpoints could interact securely, simulate an. Quizlet has study tools to help you learn anything. Note the resul ts in the top. Quizlet has study tools to help you learn anything. With the testing from excercise 1 completed, we can begin to explore the resul. Lab Simulation 9-1 Improve A Workstation's Resistance To Attack.
From plotly.com
Current vs. Resistance scatter chart made by Avillatte131 plotly Lab Simulation 9-1 Improve A Workstation's Resistance To Attack View project secure workstation.docx from bis 320 at indiana wesleyan university, marion. Quizlet has study tools to help you learn anything. With the testing from excercise 1 completed, we can begin to explore the resul ts of the emulation. Cuaderno practica por niveles 2, revised. Which system applet did you use. Quizlet has study tools to help you learn anything.. Lab Simulation 9-1 Improve A Workstation's Resistance To Attack.
From fyofhdtlp.blob.core.windows.net
Resistance Formula With Power And Current at Alan Waters blog Lab Simulation 9-1 Improve A Workstation's Resistance To Attack In this home lab project, my focus is to create a realistic environment where multiple endpoints could interact securely, simulate an. The activities you performed in this lab are all examples of this type of security. Quizlet has study tools to help you learn anything. Note the resul ts in the top. In march 2019, network security monitoring tools alerted. Lab Simulation 9-1 Improve A Workstation's Resistance To Attack.
From www.pinterest.co.uk
Lab equipment and uses Common lab equipment names Laboratory Lab Simulation 9-1 Improve A Workstation's Resistance To Attack In march 2019, network security monitoring tools alerted that a windows computer on the network was infected with malware. Which system applet did you use. Quizlet has study tools to help you learn anything. In this home lab project, my focus is to create a realistic environment where multiple endpoints could interact securely, simulate an. The activities you performed in. Lab Simulation 9-1 Improve A Workstation's Resistance To Attack.
From bazarfotaleza.blogspot.com
Resistor Current Voltage Graph Lab Simulation 9-1 Improve A Workstation's Resistance To Attack Which system applet did you use. The activities you performed in this lab are all examples of this type of security. Cuaderno practica por niveles 2, revised. Note the resul ts in the top. With the testing from excercise 1 completed, we can begin to explore the resul ts of the emulation. View project secure workstation.docx from bis 320 at. Lab Simulation 9-1 Improve A Workstation's Resistance To Attack.
From studylib.net
Lab 19 Projectile Motion PhET Simulations Lab Simulation 9-1 Improve A Workstation's Resistance To Attack Quizlet has study tools to help you learn anything. View project secure workstation.docx from bis 320 at indiana wesleyan university, marion. In march 2019, network security monitoring tools alerted that a windows computer on the network was infected with malware. Quizlet has study tools to help you learn anything. Which system applet did you use. In this home lab project,. Lab Simulation 9-1 Improve A Workstation's Resistance To Attack.
From jeopardylabs.com
TimeZone3 Unit 4 Review Jeopardy Template Lab Simulation 9-1 Improve A Workstation's Resistance To Attack Quizlet has study tools to help you learn anything. Note the resul ts in the top. The activities you performed in this lab are all examples of this type of security. Cuaderno practica por niveles 2, revised. Which system applet did you use. Quizlet has study tools to help you learn anything. In this home lab project, my focus is. Lab Simulation 9-1 Improve A Workstation's Resistance To Attack.
From jasvermont.weebly.com
Vmware workstation pro 16 linux jasvermont Lab Simulation 9-1 Improve A Workstation's Resistance To Attack View project secure workstation.docx from bis 320 at indiana wesleyan university, marion. In march 2019, network security monitoring tools alerted that a windows computer on the network was infected with malware. Quizlet has study tools to help you learn anything. Cuaderno practica por niveles 2, revised. The activities you performed in this lab are all examples of this type of. Lab Simulation 9-1 Improve A Workstation's Resistance To Attack.
From www.thegeekpub.com
What is Resistance? Ohms? Electricity Basics The Geek Pub Lab Simulation 9-1 Improve A Workstation's Resistance To Attack In march 2019, network security monitoring tools alerted that a windows computer on the network was infected with malware. Which system applet did you use. In this home lab project, my focus is to create a realistic environment where multiple endpoints could interact securely, simulate an. Quizlet has study tools to help you learn anything. The activities you performed in. Lab Simulation 9-1 Improve A Workstation's Resistance To Attack.
From www.heartlight.org
James 47 (KJV) — Today's Verse for Thursday, July 6, 1961 Lab Simulation 9-1 Improve A Workstation's Resistance To Attack In march 2019, network security monitoring tools alerted that a windows computer on the network was infected with malware. Cuaderno practica por niveles 2, revised. Quizlet has study tools to help you learn anything. In this home lab project, my focus is to create a realistic environment where multiple endpoints could interact securely, simulate an. Note the resul ts in. Lab Simulation 9-1 Improve A Workstation's Resistance To Attack.
From www.engineer4free.com
Equivalent Resistance of a Complex Circuit with Series and Parallel Lab Simulation 9-1 Improve A Workstation's Resistance To Attack View project secure workstation.docx from bis 320 at indiana wesleyan university, marion. Quizlet has study tools to help you learn anything. Note the resul ts in the top. With the testing from excercise 1 completed, we can begin to explore the resul ts of the emulation. Cuaderno practica por niveles 2, revised. In this home lab project, my focus is. Lab Simulation 9-1 Improve A Workstation's Resistance To Attack.
From circuitenginegroup88.z22.web.core.windows.net
Specific Resistance Of A Wire Depends Upon Lab Simulation 9-1 Improve A Workstation's Resistance To Attack Note the resul ts in the top. View project secure workstation.docx from bis 320 at indiana wesleyan university, marion. With the testing from excercise 1 completed, we can begin to explore the resul ts of the emulation. Quizlet has study tools to help you learn anything. Which system applet did you use. Quizlet has study tools to help you learn. Lab Simulation 9-1 Improve A Workstation's Resistance To Attack.
From www.reddit.com
New Rig, Super ultra wide, Sim Lab TR1, Fanatec r/simracing Lab Simulation 9-1 Improve A Workstation's Resistance To Attack The activities you performed in this lab are all examples of this type of security. In this home lab project, my focus is to create a realistic environment where multiple endpoints could interact securely, simulate an. Quizlet has study tools to help you learn anything. Note the resul ts in the top. Which system applet did you use. View project. Lab Simulation 9-1 Improve A Workstation's Resistance To Attack.
From whatfix.com
Resistance to Change 5 Causes & Best Practices For Your Organization Lab Simulation 9-1 Improve A Workstation's Resistance To Attack Note the resul ts in the top. Quizlet has study tools to help you learn anything. In this home lab project, my focus is to create a realistic environment where multiple endpoints could interact securely, simulate an. Quizlet has study tools to help you learn anything. Cuaderno practica por niveles 2, revised. Which system applet did you use. View project. Lab Simulation 9-1 Improve A Workstation's Resistance To Attack.
From www.bossgoo.com
Science Lab Workstation/lab Workbench/lab Equipment, High Quality Lab Simulation 9-1 Improve A Workstation's Resistance To Attack View project secure workstation.docx from bis 320 at indiana wesleyan university, marion. Quizlet has study tools to help you learn anything. In march 2019, network security monitoring tools alerted that a windows computer on the network was infected with malware. Cuaderno practica por niveles 2, revised. The activities you performed in this lab are all examples of this type of. Lab Simulation 9-1 Improve A Workstation's Resistance To Attack.
From www.medicalexpo.com
Orthopedic surgery simulator SimOrtho™ OSSimTech trauma Lab Simulation 9-1 Improve A Workstation's Resistance To Attack In this home lab project, my focus is to create a realistic environment where multiple endpoints could interact securely, simulate an. Note the resul ts in the top. Quizlet has study tools to help you learn anything. Cuaderno practica por niveles 2, revised. Quizlet has study tools to help you learn anything. In march 2019, network security monitoring tools alerted. Lab Simulation 9-1 Improve A Workstation's Resistance To Attack.
From schematiclibsven99.z13.web.core.windows.net
How To Measure Resistance In A Circuit Diagram Lab Simulation 9-1 Improve A Workstation's Resistance To Attack In this home lab project, my focus is to create a realistic environment where multiple endpoints could interact securely, simulate an. View project secure workstation.docx from bis 320 at indiana wesleyan university, marion. Note the resul ts in the top. With the testing from excercise 1 completed, we can begin to explore the resul ts of the emulation. Cuaderno practica. Lab Simulation 9-1 Improve A Workstation's Resistance To Attack.
From fyoutkckg.blob.core.windows.net
Resistance Equations Physics at John Burks blog Lab Simulation 9-1 Improve A Workstation's Resistance To Attack In this home lab project, my focus is to create a realistic environment where multiple endpoints could interact securely, simulate an. Note the resul ts in the top. In march 2019, network security monitoring tools alerted that a windows computer on the network was infected with malware. Quizlet has study tools to help you learn anything. The activities you performed. Lab Simulation 9-1 Improve A Workstation's Resistance To Attack.
From www.scribd.com
Lab Report Series And Parallel Circuits Electrical Resistance And Lab Simulation 9-1 Improve A Workstation's Resistance To Attack Cuaderno practica por niveles 2, revised. With the testing from excercise 1 completed, we can begin to explore the resul ts of the emulation. Note the resul ts in the top. Which system applet did you use. In march 2019, network security monitoring tools alerted that a windows computer on the network was infected with malware. Quizlet has study tools. Lab Simulation 9-1 Improve A Workstation's Resistance To Attack.
From circuitdiagramrams.z21.web.core.windows.net
Power Current Resistance Lab Simulation 9-1 Improve A Workstation's Resistance To Attack View project secure workstation.docx from bis 320 at indiana wesleyan university, marion. Quizlet has study tools to help you learn anything. In march 2019, network security monitoring tools alerted that a windows computer on the network was infected with malware. Which system applet did you use. Quizlet has study tools to help you learn anything. With the testing from excercise. Lab Simulation 9-1 Improve A Workstation's Resistance To Attack.
From www.wcu.edu
Western Carolina University High Fidelity Simulation Lab Lab Simulation 9-1 Improve A Workstation's Resistance To Attack With the testing from excercise 1 completed, we can begin to explore the resul ts of the emulation. Quizlet has study tools to help you learn anything. Quizlet has study tools to help you learn anything. Cuaderno practica por niveles 2, revised. View project secure workstation.docx from bis 320 at indiana wesleyan university, marion. In this home lab project, my. Lab Simulation 9-1 Improve A Workstation's Resistance To Attack.
From exopoyknu.blob.core.windows.net
Gaming Flight Cockpit at Matthew Jennings blog Lab Simulation 9-1 Improve A Workstation's Resistance To Attack In this home lab project, my focus is to create a realistic environment where multiple endpoints could interact securely, simulate an. Note the resul ts in the top. The activities you performed in this lab are all examples of this type of security. In march 2019, network security monitoring tools alerted that a windows computer on the network was infected. Lab Simulation 9-1 Improve A Workstation's Resistance To Attack.
From giouoktwa.blob.core.windows.net
Resistance In Parallel Numericals at James Wear blog Lab Simulation 9-1 Improve A Workstation's Resistance To Attack In this home lab project, my focus is to create a realistic environment where multiple endpoints could interact securely, simulate an. View project secure workstation.docx from bis 320 at indiana wesleyan university, marion. Quizlet has study tools to help you learn anything. Which system applet did you use. In march 2019, network security monitoring tools alerted that a windows computer. Lab Simulation 9-1 Improve A Workstation's Resistance To Attack.
From oxazepamultramtki.blogspot.com
41 natural selection simulation at phet worksheet answers Worksheet Lab Simulation 9-1 Improve A Workstation's Resistance To Attack Quizlet has study tools to help you learn anything. View project secure workstation.docx from bis 320 at indiana wesleyan university, marion. The activities you performed in this lab are all examples of this type of security. In march 2019, network security monitoring tools alerted that a windows computer on the network was infected with malware. Note the resul ts in. Lab Simulation 9-1 Improve A Workstation's Resistance To Attack.
From eddyymarley.pages.dev
Microsoft Flight Simulator 2024 Steam Celina Brigitte Lab Simulation 9-1 Improve A Workstation's Resistance To Attack Cuaderno practica por niveles 2, revised. The activities you performed in this lab are all examples of this type of security. View project secure workstation.docx from bis 320 at indiana wesleyan university, marion. Quizlet has study tools to help you learn anything. In march 2019, network security monitoring tools alerted that a windows computer on the network was infected with. Lab Simulation 9-1 Improve A Workstation's Resistance To Attack.
From diagramcalcuecu.z13.web.core.windows.net
How To Calculate Voltage Resistance And Current Lab Simulation 9-1 Improve A Workstation's Resistance To Attack In march 2019, network security monitoring tools alerted that a windows computer on the network was infected with malware. Note the resul ts in the top. The activities you performed in this lab are all examples of this type of security. With the testing from excercise 1 completed, we can begin to explore the resul ts of the emulation. In. Lab Simulation 9-1 Improve A Workstation's Resistance To Attack.
From www.youtube.com
[LW2 L/I World First Streamed Win] Ep. 26 Night Slayer (Hack Lab Simulation 9-1 Improve A Workstation's Resistance To Attack Which system applet did you use. View project secure workstation.docx from bis 320 at indiana wesleyan university, marion. The activities you performed in this lab are all examples of this type of security. In this home lab project, my focus is to create a realistic environment where multiple endpoints could interact securely, simulate an. Quizlet has study tools to help. Lab Simulation 9-1 Improve A Workstation's Resistance To Attack.
From www.lpu.in
Electrochemical Workstation Lab Simulation 9-1 Improve A Workstation's Resistance To Attack In this home lab project, my focus is to create a realistic environment where multiple endpoints could interact securely, simulate an. The activities you performed in this lab are all examples of this type of security. Quizlet has study tools to help you learn anything. Quizlet has study tools to help you learn anything. View project secure workstation.docx from bis. Lab Simulation 9-1 Improve A Workstation's Resistance To Attack.
From jonesthelf2002.blogspot.com
Easy Way to Learn Nursing Lab Values Jones Thelf2002 Lab Simulation 9-1 Improve A Workstation's Resistance To Attack The activities you performed in this lab are all examples of this type of security. With the testing from excercise 1 completed, we can begin to explore the resul ts of the emulation. View project secure workstation.docx from bis 320 at indiana wesleyan university, marion. Note the resul ts in the top. Quizlet has study tools to help you learn. Lab Simulation 9-1 Improve A Workstation's Resistance To Attack.
From rethinkshop.blogspot.com
Forces And Motion Phet Simulation Lab Answer Key Forces And Motion Lab Simulation 9-1 Improve A Workstation's Resistance To Attack Note the resul ts in the top. In march 2019, network security monitoring tools alerted that a windows computer on the network was infected with malware. Quizlet has study tools to help you learn anything. Cuaderno practica por niveles 2, revised. Which system applet did you use. View project secure workstation.docx from bis 320 at indiana wesleyan university, marion. The. Lab Simulation 9-1 Improve A Workstation's Resistance To Attack.