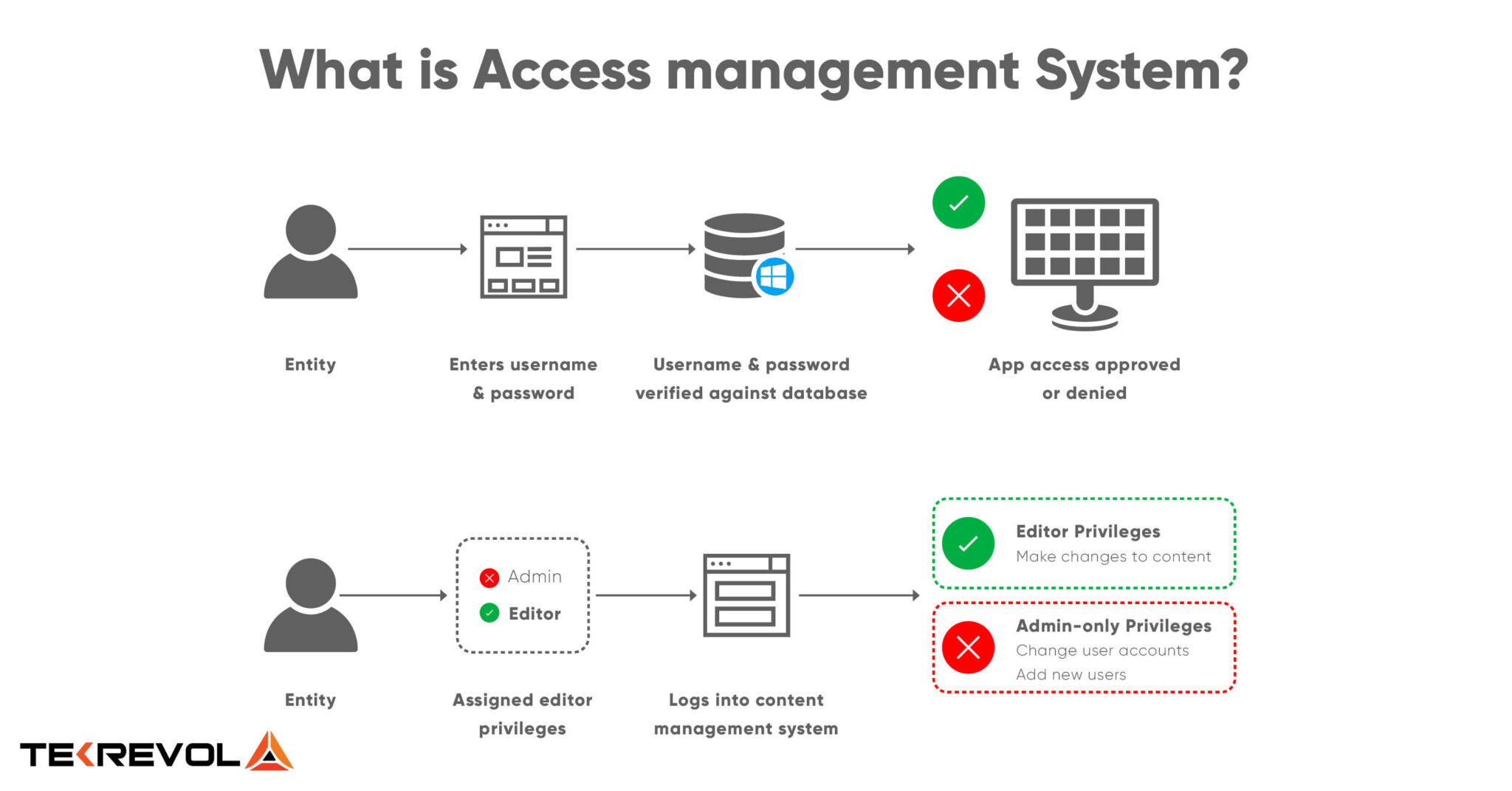
Access Management Example . An employee needs to access a cloud database. Access management is a crucial component of security infrastructure used to protect and manage access to information and resources. Compliance — access provisioning tools can provide. Increased it team productivity — automating routine access management tasks frees up it staff to focus on other priorities. Access management is a security practice that focuses on controlling and monitoring access to data, resources, and systems within an organization. Identity and access management is for making sure that only the right people can access an organization’s data and resources. Access management consists of four key elements: Identity and access management (iam or idam) is a framework containing the tools and policies a company uses to verify a user’s identity,. Identity and access management (iam) is the cybersecurity discipline that deals with how users access digital resources and what they can do with those resources. It helps make sure that only explicitly authorized individuals have appropriate permissions to access specific information or perform certain tasks.
from www.tekrevol.com
Identity and access management is for making sure that only the right people can access an organization’s data and resources. Increased it team productivity — automating routine access management tasks frees up it staff to focus on other priorities. An employee needs to access a cloud database. Access management is a security practice that focuses on controlling and monitoring access to data, resources, and systems within an organization. Access management consists of four key elements: Compliance — access provisioning tools can provide. It helps make sure that only explicitly authorized individuals have appropriate permissions to access specific information or perform certain tasks. Identity and access management (iam) is the cybersecurity discipline that deals with how users access digital resources and what they can do with those resources. Access management is a crucial component of security infrastructure used to protect and manage access to information and resources. Identity and access management (iam or idam) is a framework containing the tools and policies a company uses to verify a user’s identity,.
A Detailed Insight into What is Access Management system?
Access Management Example Access management consists of four key elements: Increased it team productivity — automating routine access management tasks frees up it staff to focus on other priorities. Identity and access management (iam or idam) is a framework containing the tools and policies a company uses to verify a user’s identity,. Compliance — access provisioning tools can provide. Access management is a security practice that focuses on controlling and monitoring access to data, resources, and systems within an organization. Identity and access management is for making sure that only the right people can access an organization’s data and resources. It helps make sure that only explicitly authorized individuals have appropriate permissions to access specific information or perform certain tasks. An employee needs to access a cloud database. Access management consists of four key elements: Identity and access management (iam) is the cybersecurity discipline that deals with how users access digital resources and what they can do with those resources. Access management is a crucial component of security infrastructure used to protect and manage access to information and resources.
From bok.idpro.org
Cameron Introduction to IAM Architecture (v2) IDPro Body of Knowledge Access Management Example Identity and access management is for making sure that only the right people can access an organization’s data and resources. Compliance — access provisioning tools can provide. Increased it team productivity — automating routine access management tasks frees up it staff to focus on other priorities. Identity and access management (iam) is the cybersecurity discipline that deals with how users. Access Management Example.
From www.opengatesw.net
Microsoft Access Templates Powerful MS Access templates built on UI Access Management Example Access management consists of four key elements: Compliance — access provisioning tools can provide. It helps make sure that only explicitly authorized individuals have appropriate permissions to access specific information or perform certain tasks. An employee needs to access a cloud database. Identity and access management is for making sure that only the right people can access an organization’s data. Access Management Example.
From www.geeksforgeeks.org
Architecture of Identity Access Management in Cloud Computing Access Management Example Identity and access management (iam or idam) is a framework containing the tools and policies a company uses to verify a user’s identity,. An employee needs to access a cloud database. Increased it team productivity — automating routine access management tasks frees up it staff to focus on other priorities. Access management is a crucial component of security infrastructure used. Access Management Example.
From wentzwu.com
Discretionary and NonDiscretionary Access Control Policies by Wentz Wu Access Management Example Identity and access management (iam) is the cybersecurity discipline that deals with how users access digital resources and what they can do with those resources. It helps make sure that only explicitly authorized individuals have appropriate permissions to access specific information or perform certain tasks. Identity and access management is for making sure that only the right people can access. Access Management Example.
From www.alamy.com
Six Components of Access Management Stock Photo Alamy Access Management Example It helps make sure that only explicitly authorized individuals have appropriate permissions to access specific information or perform certain tasks. Compliance — access provisioning tools can provide. Increased it team productivity — automating routine access management tasks frees up it staff to focus on other priorities. Identity and access management (iam or idam) is a framework containing the tools and. Access Management Example.
From ndiamond.github.io
Access Management Framework Manage Access Control Playbook Access Management Example Access management consists of four key elements: Increased it team productivity — automating routine access management tasks frees up it staff to focus on other priorities. Identity and access management (iam) is the cybersecurity discipline that deals with how users access digital resources and what they can do with those resources. Access management is a security practice that focuses on. Access Management Example.
From sennovate.com
The 5Minute Identity and Access Management Tutorial Sennovate Access Management Example It helps make sure that only explicitly authorized individuals have appropriate permissions to access specific information or perform certain tasks. An employee needs to access a cloud database. Compliance — access provisioning tools can provide. Identity and access management (iam) is the cybersecurity discipline that deals with how users access digital resources and what they can do with those resources.. Access Management Example.
From braxtongrant.com
Understanding Key Identity & Access Management Components Blog Access Management Example Access management is a crucial component of security infrastructure used to protect and manage access to information and resources. Identity and access management (iam) is the cybersecurity discipline that deals with how users access digital resources and what they can do with those resources. It helps make sure that only explicitly authorized individuals have appropriate permissions to access specific information. Access Management Example.
From www.ilantus.com
What is Access Management? Ilantus Blog Access Management Example Identity and access management (iam) is the cybersecurity discipline that deals with how users access digital resources and what they can do with those resources. Access management consists of four key elements: It helps make sure that only explicitly authorized individuals have appropriate permissions to access specific information or perform certain tasks. Access management is a crucial component of security. Access Management Example.
From www.slideteam.net
Authenticated Identity And User Access Management Presentation Access Management Example Access management is a crucial component of security infrastructure used to protect and manage access to information and resources. It helps make sure that only explicitly authorized individuals have appropriate permissions to access specific information or perform certain tasks. Access management consists of four key elements: Compliance — access provisioning tools can provide. Identity and access management (iam or idam). Access Management Example.
From www.formsbirds.com
Standard Access Control Policy Template Free Download Access Management Example Identity and access management (iam) is the cybersecurity discipline that deals with how users access digital resources and what they can do with those resources. It helps make sure that only explicitly authorized individuals have appropriate permissions to access specific information or perform certain tasks. Access management is a security practice that focuses on controlling and monitoring access to data,. Access Management Example.
From docs.microsoft.com
Manage app & resource access using groups Azure AD Microsoft Entra Access Management Example Compliance — access provisioning tools can provide. Identity and access management is for making sure that only the right people can access an organization’s data and resources. Identity and access management (iam) is the cybersecurity discipline that deals with how users access digital resources and what they can do with those resources. Increased it team productivity — automating routine access. Access Management Example.
From subscription.packtpub.com
Mastering Identity and Access Management with Microsoft Azure Access Management Example Increased it team productivity — automating routine access management tasks frees up it staff to focus on other priorities. Access management is a crucial component of security infrastructure used to protect and manage access to information and resources. Identity and access management (iam or idam) is a framework containing the tools and policies a company uses to verify a user’s. Access Management Example.
From www.educba.com
10 Powerful Features Of Microsoft Access edu CBA Access Management Example Identity and access management (iam or idam) is a framework containing the tools and policies a company uses to verify a user’s identity,. Identity and access management (iam) is the cybersecurity discipline that deals with how users access digital resources and what they can do with those resources. Compliance — access provisioning tools can provide. Identity and access management is. Access Management Example.
From www.youtube.com
Creating Employee Management Database in MS Access FULL LESSON Leave Access Management Example Access management is a crucial component of security infrastructure used to protect and manage access to information and resources. It helps make sure that only explicitly authorized individuals have appropriate permissions to access specific information or perform certain tasks. Identity and access management (iam) is the cybersecurity discipline that deals with how users access digital resources and what they can. Access Management Example.
From frontegg.com
What is RoleBased Access Control RBAC vs ABAC Access Management Example Access management is a crucial component of security infrastructure used to protect and manage access to information and resources. Identity and access management is for making sure that only the right people can access an organization’s data and resources. Access management consists of four key elements: Identity and access management (iam or idam) is a framework containing the tools and. Access Management Example.
From drata.com
How to Perform User Access Reviews Drata Drata Access Management Example An employee needs to access a cloud database. Access management is a security practice that focuses on controlling and monitoring access to data, resources, and systems within an organization. Access management is a crucial component of security infrastructure used to protect and manage access to information and resources. It helps make sure that only explicitly authorized individuals have appropriate permissions. Access Management Example.
From www.xorlogics.com
3 Basic A’s of Identity and Access Management Authentication Access Management Example Compliance — access provisioning tools can provide. Access management consists of four key elements: Identity and access management (iam or idam) is a framework containing the tools and policies a company uses to verify a user’s identity,. Access management is a crucial component of security infrastructure used to protect and manage access to information and resources. Access management is a. Access Management Example.
From www.slideshare.net
Access Manager Overview Access Management Example Access management is a crucial component of security infrastructure used to protect and manage access to information and resources. Access management consists of four key elements: Access management is a security practice that focuses on controlling and monitoring access to data, resources, and systems within an organization. It helps make sure that only explicitly authorized individuals have appropriate permissions to. Access Management Example.
From www.tekrevol.com
A Detailed Insight into What is Access Management system? Access Management Example Access management consists of four key elements: Identity and access management (iam or idam) is a framework containing the tools and policies a company uses to verify a user’s identity,. Increased it team productivity — automating routine access management tasks frees up it staff to focus on other priorities. Compliance — access provisioning tools can provide. Access management is a. Access Management Example.
From www.wallarm.com
What is IAM (Identity and Access Management) Access Management Example Identity and access management is for making sure that only the right people can access an organization’s data and resources. Compliance — access provisioning tools can provide. Increased it team productivity — automating routine access management tasks frees up it staff to focus on other priorities. Access management consists of four key elements: It helps make sure that only explicitly. Access Management Example.
From www.it-procedure-template.com
User Access Management Procedure IT Procedure Template Access Management Example Compliance — access provisioning tools can provide. Identity and access management is for making sure that only the right people can access an organization’s data and resources. It helps make sure that only explicitly authorized individuals have appropriate permissions to access specific information or perform certain tasks. An employee needs to access a cloud database. Identity and access management (iam). Access Management Example.
From medium.com
Getting Started with Open Source Identity Access Management (Keycloak Access Management Example It helps make sure that only explicitly authorized individuals have appropriate permissions to access specific information or perform certain tasks. Identity and access management (iam or idam) is a framework containing the tools and policies a company uses to verify a user’s identity,. Access management is a security practice that focuses on controlling and monitoring access to data, resources, and. Access Management Example.
From www.spiceworks.com
What Is Privileged Access Management (PAM)? Definition, Components, and Access Management Example Access management is a security practice that focuses on controlling and monitoring access to data, resources, and systems within an organization. Access management is a crucial component of security infrastructure used to protect and manage access to information and resources. Identity and access management (iam) is the cybersecurity discipline that deals with how users access digital resources and what they. Access Management Example.
From mydiagram.online
[DIAGRAM] Microsoft Access Database Diagram Access Management Example Access management is a security practice that focuses on controlling and monitoring access to data, resources, and systems within an organization. An employee needs to access a cloud database. Compliance — access provisioning tools can provide. Identity and access management is for making sure that only the right people can access an organization’s data and resources. Access management consists of. Access Management Example.
From wiki.en.it-processmaps.com
Access Management IT Process Wiki Access Management Example Identity and access management is for making sure that only the right people can access an organization’s data and resources. It helps make sure that only explicitly authorized individuals have appropriate permissions to access specific information or perform certain tasks. An employee needs to access a cloud database. Increased it team productivity — automating routine access management tasks frees up. Access Management Example.
From www.scribd.com
IT Operations_User Access Management Policies Email Login Free 30 Access Management Example Access management is a crucial component of security infrastructure used to protect and manage access to information and resources. Access management is a security practice that focuses on controlling and monitoring access to data, resources, and systems within an organization. Compliance — access provisioning tools can provide. An employee needs to access a cloud database. Identity and access management (iam. Access Management Example.
From tutore.org
Access Document Management Template Master of Documents Access Management Example Access management is a security practice that focuses on controlling and monitoring access to data, resources, and systems within an organization. An employee needs to access a cloud database. Increased it team productivity — automating routine access management tasks frees up it staff to focus on other priorities. It helps make sure that only explicitly authorized individuals have appropriate permissions. Access Management Example.
From www.nedapsecurity.com
The Ultimate Guide to Physical Access Control Systems in 2023 Access Management Example Compliance — access provisioning tools can provide. An employee needs to access a cloud database. Identity and access management is for making sure that only the right people can access an organization’s data and resources. It helps make sure that only explicitly authorized individuals have appropriate permissions to access specific information or perform certain tasks. Identity and access management (iam). Access Management Example.
From pathlock.com
SAP Access Management Identity Lifecycle Management Data Security Access Management Example Access management is a crucial component of security infrastructure used to protect and manage access to information and resources. Access management consists of four key elements: Identity and access management (iam or idam) is a framework containing the tools and policies a company uses to verify a user’s identity,. Identity and access management (iam) is the cybersecurity discipline that deals. Access Management Example.
From www.gartner.com
Definition of Identity and Access Management (IAM) Gartner Access Management Example Access management is a crucial component of security infrastructure used to protect and manage access to information and resources. Access management is a security practice that focuses on controlling and monitoring access to data, resources, and systems within an organization. It helps make sure that only explicitly authorized individuals have appropriate permissions to access specific information or perform certain tasks.. Access Management Example.
From www.itsmprocesses.com
ITSM Wiki ITIL® Access Management Access Management Example Compliance — access provisioning tools can provide. An employee needs to access a cloud database. Identity and access management is for making sure that only the right people can access an organization’s data and resources. Access management consists of four key elements: Access management is a security practice that focuses on controlling and monitoring access to data, resources, and systems. Access Management Example.
From www.tekrevol.com
A Detailed Insight into What is Access Management system? Access Management Example Identity and access management (iam) is the cybersecurity discipline that deals with how users access digital resources and what they can do with those resources. An employee needs to access a cloud database. Access management is a security practice that focuses on controlling and monitoring access to data, resources, and systems within an organization. Access management consists of four key. Access Management Example.
From www.template.net
Access Plans Templates Format, Free, Download Access Management Example An employee needs to access a cloud database. Identity and access management (iam) is the cybersecurity discipline that deals with how users access digital resources and what they can do with those resources. Access management is a crucial component of security infrastructure used to protect and manage access to information and resources. Identity and access management is for making sure. Access Management Example.
From docs.aws.amazon.com
Access management for AWS resources AWS Identity and Access Management Access Management Example It helps make sure that only explicitly authorized individuals have appropriate permissions to access specific information or perform certain tasks. Compliance — access provisioning tools can provide. Access management consists of four key elements: Access management is a crucial component of security infrastructure used to protect and manage access to information and resources. Increased it team productivity — automating routine. Access Management Example.