How To Use Gtfobins . Gtfobins is a curated collection of unix binaries used for bypassing local security restrictions, while lolbas (living off the land binaries and scripts) serves a similar purpose in windows environments. 392 rows gtfobins is a curated list of unix binaries that can be used to bypass local security restrictions in misconfigured systems. In this tutorial, we will be exploring gtfo, a tool used to search these projects for abusable binaries right from the command line. Gtfobins is a curated list of unix binaries that can be used to bypass local security restrictions in misconfigured systems. Each entry in the gtfobins database provides. In this video, we will be taking a look at how to obtain initial access and perform privilege escalation with gtfobins.
from cyberkhalid.github.io
Gtfobins is a curated list of unix binaries that can be used to bypass local security restrictions in misconfigured systems. In this tutorial, we will be exploring gtfo, a tool used to search these projects for abusable binaries right from the command line. 392 rows gtfobins is a curated list of unix binaries that can be used to bypass local security restrictions in misconfigured systems. In this video, we will be taking a look at how to obtain initial access and perform privilege escalation with gtfobins. Gtfobins is a curated collection of unix binaries used for bypassing local security restrictions, while lolbas (living off the land binaries and scripts) serves a similar purpose in windows environments. Each entry in the gtfobins database provides.
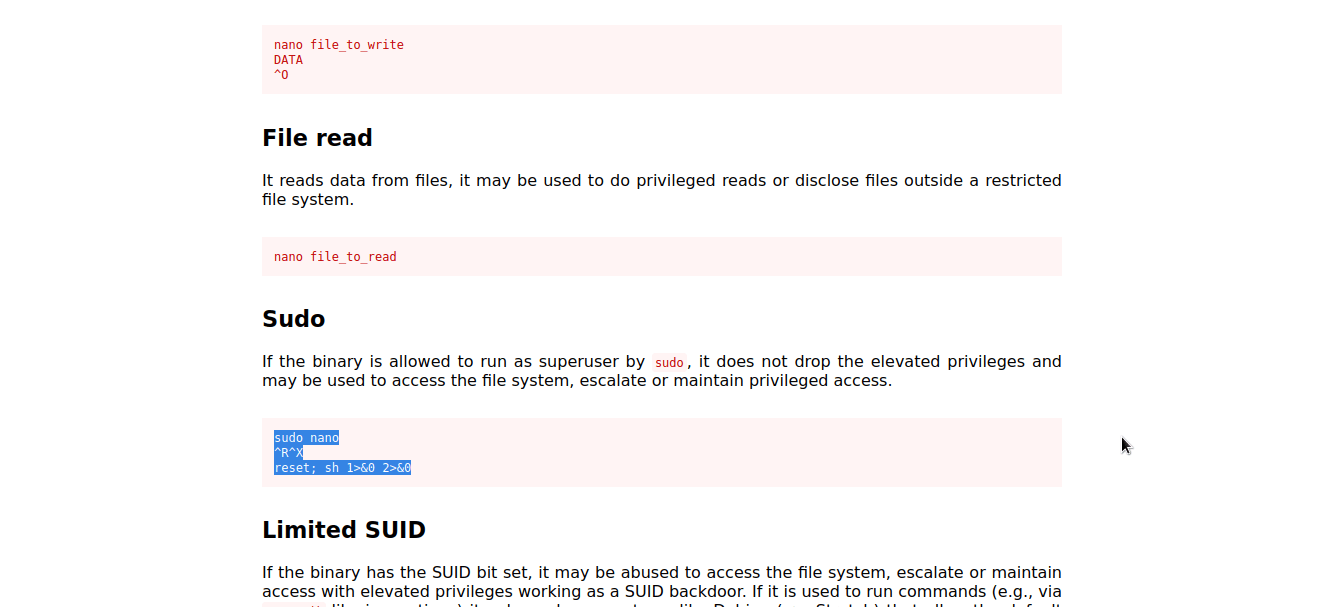
Shell Escape Sequences cyberkhalid
How To Use Gtfobins 392 rows gtfobins is a curated list of unix binaries that can be used to bypass local security restrictions in misconfigured systems. Gtfobins is a curated collection of unix binaries used for bypassing local security restrictions, while lolbas (living off the land binaries and scripts) serves a similar purpose in windows environments. 392 rows gtfobins is a curated list of unix binaries that can be used to bypass local security restrictions in misconfigured systems. In this video, we will be taking a look at how to obtain initial access and perform privilege escalation with gtfobins. Each entry in the gtfobins database provides. Gtfobins is a curated list of unix binaries that can be used to bypass local security restrictions in misconfigured systems. In this tutorial, we will be exploring gtfo, a tool used to search these projects for abusable binaries right from the command line.
From www.youtube.com
Compressor Challenge Hack The Box CTF GTFO bins zip binary YouTube How To Use Gtfobins Each entry in the gtfobins database provides. 392 rows gtfobins is a curated list of unix binaries that can be used to bypass local security restrictions in misconfigured systems. Gtfobins is a curated list of unix binaries that can be used to bypass local security restrictions in misconfigured systems. In this tutorial, we will be exploring gtfo, a tool used. How To Use Gtfobins.
From steamah.com
GTFO Alpha How To Use The Terminals SteamAH How To Use Gtfobins In this video, we will be taking a look at how to obtain initial access and perform privilege escalation with gtfobins. Each entry in the gtfobins database provides. 392 rows gtfobins is a curated list of unix binaries that can be used to bypass local security restrictions in misconfigured systems. Gtfobins is a curated list of unix binaries that can. How To Use Gtfobins.
From github.com
GitHub abhisheksuran/GTFObins_finder This script search for the bin on the https//gtfobins How To Use Gtfobins In this video, we will be taking a look at how to obtain initial access and perform privilege escalation with gtfobins. Gtfobins is a curated collection of unix binaries used for bypassing local security restrictions, while lolbas (living off the land binaries and scripts) serves a similar purpose in windows environments. 392 rows gtfobins is a curated list of unix. How To Use Gtfobins.
From medium.com
Stable Diffusion Tutorial How to use Stable Diffusion NightCafe How To Use Gtfobins Each entry in the gtfobins database provides. In this tutorial, we will be exploring gtfo, a tool used to search these projects for abusable binaries right from the command line. Gtfobins is a curated list of unix binaries that can be used to bypass local security restrictions in misconfigured systems. In this video, we will be taking a look at. How To Use Gtfobins.
From github.com
GitHub Frissi0n/GTFONow Automatic privilege escalation for misconfigured capabilities, sudo How To Use Gtfobins 392 rows gtfobins is a curated list of unix binaries that can be used to bypass local security restrictions in misconfigured systems. In this video, we will be taking a look at how to obtain initial access and perform privilege escalation with gtfobins. In this tutorial, we will be exploring gtfo, a tool used to search these projects for abusable. How To Use Gtfobins.
From twitter.com
Jose Enrique Hernandez on Twitter "Hey, infosec brains trust! 🧠 Ever felt like you're juggling How To Use Gtfobins Each entry in the gtfobins database provides. Gtfobins is a curated collection of unix binaries used for bypassing local security restrictions, while lolbas (living off the land binaries and scripts) serves a similar purpose in windows environments. 392 rows gtfobins is a curated list of unix binaries that can be used to bypass local security restrictions in misconfigured systems. In. How To Use Gtfobins.
From electronicsreference.com
TryHackMe RootMe Notes and Walkthrough Electronics Reference How To Use Gtfobins Gtfobins is a curated list of unix binaries that can be used to bypass local security restrictions in misconfigured systems. Gtfobins is a curated collection of unix binaries used for bypassing local security restrictions, while lolbas (living off the land binaries and scripts) serves a similar purpose in windows environments. In this video, we will be taking a look at. How To Use Gtfobins.
From deepakkush.medium.com
How to use GTFOBins Deepak Kushwah Medium How To Use Gtfobins In this tutorial, we will be exploring gtfo, a tool used to search these projects for abusable binaries right from the command line. Each entry in the gtfobins database provides. 392 rows gtfobins is a curated list of unix binaries that can be used to bypass local security restrictions in misconfigured systems. In this video, we will be taking a. How To Use Gtfobins.
From www.youtube.com
Free to use GTFO Gameplay YouTube How To Use Gtfobins Gtfobins is a curated list of unix binaries that can be used to bypass local security restrictions in misconfigured systems. In this tutorial, we will be exploring gtfo, a tool used to search these projects for abusable binaries right from the command line. Each entry in the gtfobins database provides. 392 rows gtfobins is a curated list of unix binaries. How To Use Gtfobins.
From medium.com
How to run Stable Diffusion on Intel GPUs with OpenVINO by Raymond Lo, PhD OpenVINOtoolkit How To Use Gtfobins Gtfobins is a curated list of unix binaries that can be used to bypass local security restrictions in misconfigured systems. In this tutorial, we will be exploring gtfo, a tool used to search these projects for abusable binaries right from the command line. Each entry in the gtfobins database provides. Gtfobins is a curated collection of unix binaries used for. How To Use Gtfobins.
From www.youtube.com
Beginner's Guide to GTFOBins Linux privilege escalation YouTube How To Use Gtfobins In this tutorial, we will be exploring gtfo, a tool used to search these projects for abusable binaries right from the command line. Each entry in the gtfobins database provides. 392 rows gtfobins is a curated list of unix binaries that can be used to bypass local security restrictions in misconfigured systems. In this video, we will be taking a. How To Use Gtfobins.
From resource-cdn.sider.ai
How to Use Sider's Upscale Feature for Image Enhancement Sider How To Use Gtfobins 392 rows gtfobins is a curated list of unix binaries that can be used to bypass local security restrictions in misconfigured systems. Each entry in the gtfobins database provides. In this tutorial, we will be exploring gtfo, a tool used to search these projects for abusable binaries right from the command line. Gtfobins is a curated list of unix binaries. How To Use Gtfobins.
From www.youtube.com
GTFO Guide HOW TO OPEN AND USE TEXT LOGS speedrunning (scuffed) YouTube How To Use Gtfobins In this video, we will be taking a look at how to obtain initial access and perform privilege escalation with gtfobins. Gtfobins is a curated list of unix binaries that can be used to bypass local security restrictions in misconfigured systems. 392 rows gtfobins is a curated list of unix binaries that can be used to bypass local security restrictions. How To Use Gtfobins.
From dotcommagazine.com
GtfobinsTop Ten Things You Need To Know. MagazineInfluencers And Entrepreneurs Making How To Use Gtfobins Each entry in the gtfobins database provides. Gtfobins is a curated list of unix binaries that can be used to bypass local security restrictions in misconfigured systems. Gtfobins is a curated collection of unix binaries used for bypassing local security restrictions, while lolbas (living off the land binaries and scripts) serves a similar purpose in windows environments. In this video,. How To Use Gtfobins.
From digest.getnotable.ai
How To Use The New ChatGPT Desktop App Right Now How To Use Gtfobins In this video, we will be taking a look at how to obtain initial access and perform privilege escalation with gtfobins. Gtfobins is a curated collection of unix binaries used for bypassing local security restrictions, while lolbas (living off the land binaries and scripts) serves a similar purpose in windows environments. 392 rows gtfobins is a curated list of unix. How To Use Gtfobins.
From www.youtube.com
HOW TO INSTALL AND USE GTFO VR MOD (Howto 9min, Links, Tutorial) YouTube How To Use Gtfobins In this tutorial, we will be exploring gtfo, a tool used to search these projects for abusable binaries right from the command line. In this video, we will be taking a look at how to obtain initial access and perform privilege escalation with gtfobins. Each entry in the gtfobins database provides. 392 rows gtfobins is a curated list of unix. How To Use Gtfobins.
From www.youtube.com
GTFO Beginner Guide How to Use Terminals YouTube How To Use Gtfobins Gtfobins is a curated list of unix binaries that can be used to bypass local security restrictions in misconfigured systems. Each entry in the gtfobins database provides. 392 rows gtfobins is a curated list of unix binaries that can be used to bypass local security restrictions in misconfigured systems. In this tutorial, we will be exploring gtfo, a tool used. How To Use Gtfobins.
From www.youtube.com
Privilege Escalation Using GTFOBins SUID set on find YouTube How To Use Gtfobins In this tutorial, we will be exploring gtfo, a tool used to search these projects for abusable binaries right from the command line. Gtfobins is a curated list of unix binaries that can be used to bypass local security restrictions in misconfigured systems. In this video, we will be taking a look at how to obtain initial access and perform. How To Use Gtfobins.
From twinfinite.net
GTFO How to Use Terminal Twinfinite How To Use Gtfobins In this tutorial, we will be exploring gtfo, a tool used to search these projects for abusable binaries right from the command line. Each entry in the gtfobins database provides. In this video, we will be taking a look at how to obtain initial access and perform privilege escalation with gtfobins. Gtfobins is a curated list of unix binaries that. How To Use Gtfobins.
From dotcommagazine.com
Gtfobins Top Ten Most Important Things You Need To Know MagazineInfluencers And How To Use Gtfobins In this tutorial, we will be exploring gtfo, a tool used to search these projects for abusable binaries right from the command line. 392 rows gtfobins is a curated list of unix binaries that can be used to bypass local security restrictions in misconfigured systems. In this video, we will be taking a look at how to obtain initial access. How To Use Gtfobins.
From www.youtube.com
HackTheBox Knife Linux Privilege Escalation With GTFOBins YouTube How To Use Gtfobins Gtfobins is a curated collection of unix binaries used for bypassing local security restrictions, while lolbas (living off the land binaries and scripts) serves a similar purpose in windows environments. 392 rows gtfobins is a curated list of unix binaries that can be used to bypass local security restrictions in misconfigured systems. In this video, we will be taking a. How To Use Gtfobins.
From electronicsreference.com
TryHackMe Vulnversity Complete Walkthrough and Notes Electronics Reference How To Use Gtfobins Gtfobins is a curated collection of unix binaries used for bypassing local security restrictions, while lolbas (living off the land binaries and scripts) serves a similar purpose in windows environments. 392 rows gtfobins is a curated list of unix binaries that can be used to bypass local security restrictions in misconfigured systems. In this tutorial, we will be exploring gtfo,. How To Use Gtfobins.
From cyberkhalid.github.io
Shell Escape Sequences cyberkhalid How To Use Gtfobins Gtfobins is a curated list of unix binaries that can be used to bypass local security restrictions in misconfigured systems. Each entry in the gtfobins database provides. Gtfobins is a curated collection of unix binaries used for bypassing local security restrictions, while lolbas (living off the land binaries and scripts) serves a similar purpose in windows environments. In this tutorial,. How To Use Gtfobins.
From www.youtube.com
𝐆𝐓𝐅𝐎 How To Use The Terminal To Find Objectives And Items (Basics Guide) Alpha 1 YouTube How To Use Gtfobins 392 rows gtfobins is a curated list of unix binaries that can be used to bypass local security restrictions in misconfigured systems. Each entry in the gtfobins database provides. In this tutorial, we will be exploring gtfo, a tool used to search these projects for abusable binaries right from the command line. In this video, we will be taking a. How To Use Gtfobins.
From github.com
GitHub Stahlz/gtfobinsapi Api to get gtfobins infos How To Use Gtfobins In this tutorial, we will be exploring gtfo, a tool used to search these projects for abusable binaries right from the command line. In this video, we will be taking a look at how to obtain initial access and perform privilege escalation with gtfobins. Gtfobins is a curated collection of unix binaries used for bypassing local security restrictions, while lolbas. How To Use Gtfobins.
From www.youtube.com
GTFOBins for Linux privilege escalation YouTube How To Use Gtfobins In this video, we will be taking a look at how to obtain initial access and perform privilege escalation with gtfobins. 392 rows gtfobins is a curated list of unix binaries that can be used to bypass local security restrictions in misconfigured systems. Each entry in the gtfobins database provides. Gtfobins is a curated list of unix binaries that can. How To Use Gtfobins.
From dotcommagazine.com
GtfobinsTop Five Important Things You Need To Know. MagazineInfluencers And How To Use Gtfobins In this tutorial, we will be exploring gtfo, a tool used to search these projects for abusable binaries right from the command line. Each entry in the gtfobins database provides. In this video, we will be taking a look at how to obtain initial access and perform privilege escalation with gtfobins. 392 rows gtfobins is a curated list of unix. How To Use Gtfobins.
From www.youtube.com
How to Use Flashlight in GTFO Turn On Torch YouTube How To Use Gtfobins In this video, we will be taking a look at how to obtain initial access and perform privilege escalation with gtfobins. In this tutorial, we will be exploring gtfo, a tool used to search these projects for abusable binaries right from the command line. Each entry in the gtfobins database provides. Gtfobins is a curated collection of unix binaries used. How To Use Gtfobins.
From www.reddit.com
"illustrated stepbystep guide on how to use the toilette" r/dalle2 How To Use Gtfobins In this tutorial, we will be exploring gtfo, a tool used to search these projects for abusable binaries right from the command line. Each entry in the gtfobins database provides. 392 rows gtfobins is a curated list of unix binaries that can be used to bypass local security restrictions in misconfigured systems. Gtfobins is a curated collection of unix binaries. How To Use Gtfobins.
From www.youtube.com
Privilege escalation explained in Linux SUID, SGID, Sudo and GTFO Bins YouTube How To Use Gtfobins Each entry in the gtfobins database provides. 392 rows gtfobins is a curated list of unix binaries that can be used to bypass local security restrictions in misconfigured systems. Gtfobins is a curated collection of unix binaries used for bypassing local security restrictions, while lolbas (living off the land binaries and scripts) serves a similar purpose in windows environments. In. How To Use Gtfobins.
From twinfinite.net
GTFO How to Use Terminal Twinfinite How To Use Gtfobins In this video, we will be taking a look at how to obtain initial access and perform privilege escalation with gtfobins. Gtfobins is a curated list of unix binaries that can be used to bypass local security restrictions in misconfigured systems. Gtfobins is a curated collection of unix binaries used for bypassing local security restrictions, while lolbas (living off the. How To Use Gtfobins.
From electronicsreference.com
TryHackMe Smag Grotto Walkthrough and Notes Electronics Reference How To Use Gtfobins Gtfobins is a curated collection of unix binaries used for bypassing local security restrictions, while lolbas (living off the land binaries and scripts) serves a similar purpose in windows environments. In this video, we will be taking a look at how to obtain initial access and perform privilege escalation with gtfobins. 392 rows gtfobins is a curated list of unix. How To Use Gtfobins.
From www.youtube.com
Basics to Privilege Escalation GTFOBins CronJobs Sudo Exploits By Sanchay Sir (HINDI How To Use Gtfobins 392 rows gtfobins is a curated list of unix binaries that can be used to bypass local security restrictions in misconfigured systems. Each entry in the gtfobins database provides. Gtfobins is a curated collection of unix binaries used for bypassing local security restrictions, while lolbas (living off the land binaries and scripts) serves a similar purpose in windows environments. Gtfobins. How To Use Gtfobins.
From www.youtube.com
Privilege Escalation Tutorial using GTFOBins openssl to read YouTube How To Use Gtfobins Each entry in the gtfobins database provides. Gtfobins is a curated list of unix binaries that can be used to bypass local security restrictions in misconfigured systems. In this video, we will be taking a look at how to obtain initial access and perform privilege escalation with gtfobins. In this tutorial, we will be exploring gtfo, a tool used to. How To Use Gtfobins.
From www.youtube.com
Install TOBIT in SPSS 28 IBM Statistics, How to using R YouTube How To Use Gtfobins In this tutorial, we will be exploring gtfo, a tool used to search these projects for abusable binaries right from the command line. Gtfobins is a curated list of unix binaries that can be used to bypass local security restrictions in misconfigured systems. 392 rows gtfobins is a curated list of unix binaries that can be used to bypass local. How To Use Gtfobins.