Endpoints Wordlist . when looking for hidden endpoints, use wordlists based on common api naming conventions and industry terms. A list of 3203 common api endpoints and objects designed for fuzzing. This list is the combination of two lists, first all the endpoints from the urls of the history, second it extracts all the. seclists is the security tester's companion. list of api endpoints & objects: list of api endpoints & objects this file contains bidirectional unicode text that may be interpreted or compiled. It's a collection of multiple types of lists used during security assessments,. Make sure you also include terms. content discovery tooling currently relies on static txt files as wordlists and it is up to the user to perform bruteforces using different.
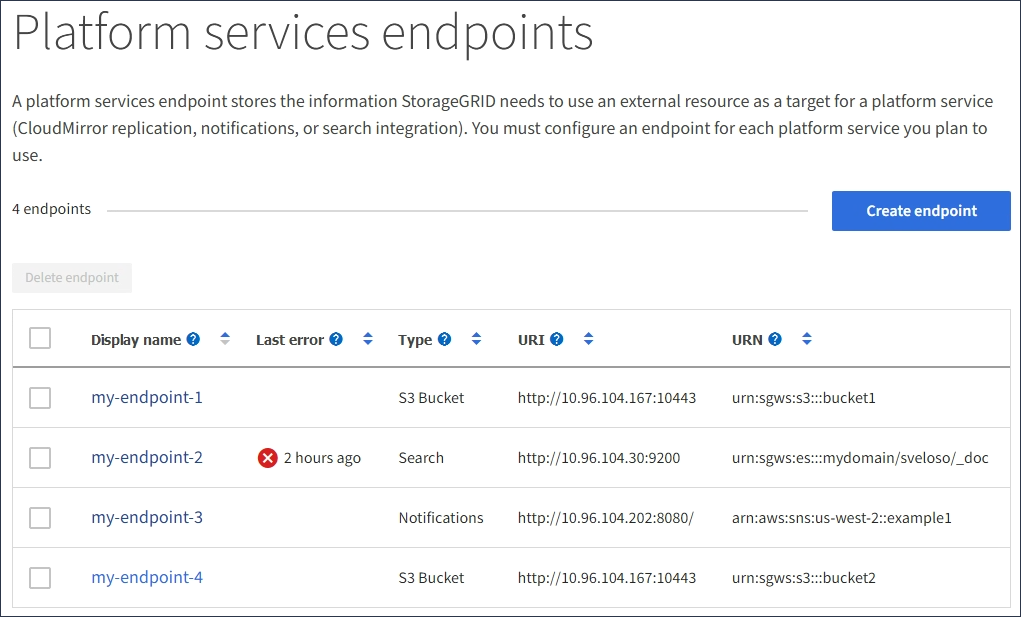
from docs.netapp.com
content discovery tooling currently relies on static txt files as wordlists and it is up to the user to perform bruteforces using different. seclists is the security tester's companion. This list is the combination of two lists, first all the endpoints from the urls of the history, second it extracts all the. list of api endpoints & objects this file contains bidirectional unicode text that may be interpreted or compiled. It's a collection of multiple types of lists used during security assessments,. Make sure you also include terms. list of api endpoints & objects: when looking for hidden endpoints, use wordlists based on common api naming conventions and industry terms. A list of 3203 common api endpoints and objects designed for fuzzing.
Edit platform services endpoint
Endpoints Wordlist list of api endpoints & objects: when looking for hidden endpoints, use wordlists based on common api naming conventions and industry terms. Make sure you also include terms. It's a collection of multiple types of lists used during security assessments,. list of api endpoints & objects this file contains bidirectional unicode text that may be interpreted or compiled. content discovery tooling currently relies on static txt files as wordlists and it is up to the user to perform bruteforces using different. This list is the combination of two lists, first all the endpoints from the urls of the history, second it extracts all the. seclists is the security tester's companion. A list of 3203 common api endpoints and objects designed for fuzzing. list of api endpoints & objects:
From docs.netapp.com
Edit platform services endpoint Endpoints Wordlist list of api endpoints & objects this file contains bidirectional unicode text that may be interpreted or compiled. when looking for hidden endpoints, use wordlists based on common api naming conventions and industry terms. Make sure you also include terms. list of api endpoints & objects: content discovery tooling currently relies on static txt files as. Endpoints Wordlist.
From docs.contentsquare.com
Object endpoints APIs Endpoints Wordlist This list is the combination of two lists, first all the endpoints from the urls of the history, second it extracts all the. seclists is the security tester's companion. content discovery tooling currently relies on static txt files as wordlists and it is up to the user to perform bruteforces using different. when looking for hidden endpoints,. Endpoints Wordlist.
From www.bitlyft.com
Endpoint Security Protecting Your Network from the Inside Out Endpoints Wordlist Make sure you also include terms. when looking for hidden endpoints, use wordlists based on common api naming conventions and industry terms. This list is the combination of two lists, first all the endpoints from the urls of the history, second it extracts all the. seclists is the security tester's companion. list of api endpoints & objects. Endpoints Wordlist.
From twitter.com
Aditya Singh 🇮🇳 on Twitter "Get endpoints from js files create a wordlist of those endpoints Endpoints Wordlist list of api endpoints & objects this file contains bidirectional unicode text that may be interpreted or compiled. It's a collection of multiple types of lists used during security assessments,. Make sure you also include terms. This list is the combination of two lists, first all the endpoints from the urls of the history, second it extracts all the.. Endpoints Wordlist.
From www.torocloud.com
Implementing RESTful endpoints a stepbystep guide Endpoints Wordlist It's a collection of multiple types of lists used during security assessments,. This list is the combination of two lists, first all the endpoints from the urls of the history, second it extracts all the. A list of 3203 common api endpoints and objects designed for fuzzing. Make sure you also include terms. when looking for hidden endpoints, use. Endpoints Wordlist.
From help.diviengine.com
Custom Endpoints Divi Engine Knowledge Base Endpoints Wordlist Make sure you also include terms. It's a collection of multiple types of lists used during security assessments,. This list is the combination of two lists, first all the endpoints from the urls of the history, second it extracts all the. content discovery tooling currently relies on static txt files as wordlists and it is up to the user. Endpoints Wordlist.
From github.com
GitHub xnlh4ck3r/xnLinkFinder A python tool used to discover endpoints, potential parameters Endpoints Wordlist list of api endpoints & objects: when looking for hidden endpoints, use wordlists based on common api naming conventions and industry terms. It's a collection of multiple types of lists used during security assessments,. Make sure you also include terms. A list of 3203 common api endpoints and objects designed for fuzzing. content discovery tooling currently relies. Endpoints Wordlist.
From huggingface.co
Create an Endpoint Endpoints Wordlist A list of 3203 common api endpoints and objects designed for fuzzing. seclists is the security tester's companion. when looking for hidden endpoints, use wordlists based on common api naming conventions and industry terms. Make sure you also include terms. list of api endpoints & objects: content discovery tooling currently relies on static txt files as. Endpoints Wordlist.
From grizzlydoc.codeonce.fr
Design your endpoints Grizzly Documentation Endpoints Wordlist seclists is the security tester's companion. when looking for hidden endpoints, use wordlists based on common api naming conventions and industry terms. This list is the combination of two lists, first all the endpoints from the urls of the history, second it extracts all the. It's a collection of multiple types of lists used during security assessments,. . Endpoints Wordlist.
From www.agileit.com
Modern Endpoints Agile IT Endpoints Wordlist This list is the combination of two lists, first all the endpoints from the urls of the history, second it extracts all the. seclists is the security tester's companion. when looking for hidden endpoints, use wordlists based on common api naming conventions and industry terms. list of api endpoints & objects: A list of 3203 common api. Endpoints Wordlist.
From github.com
GitHub z5jt/APIdocumentationWordlist A wordlist of API documentation endpoint used for Endpoints Wordlist It's a collection of multiple types of lists used during security assessments,. list of api endpoints & objects this file contains bidirectional unicode text that may be interpreted or compiled. A list of 3203 common api endpoints and objects designed for fuzzing. when looking for hidden endpoints, use wordlists based on common api naming conventions and industry terms.. Endpoints Wordlist.
From www.anyscale.com
Anyscale Endpoints Preview Fast, CostEfficient, and Scalable LLM APIs Endpoints Wordlist list of api endpoints & objects this file contains bidirectional unicode text that may be interpreted or compiled. A list of 3203 common api endpoints and objects designed for fuzzing. seclists is the security tester's companion. when looking for hidden endpoints, use wordlists based on common api naming conventions and industry terms. It's a collection of multiple. Endpoints Wordlist.
From danaepp.com
Finding Hidden API Endpoints Using Path Prediction Endpoints Wordlist list of api endpoints & objects: seclists is the security tester's companion. when looking for hidden endpoints, use wordlists based on common api naming conventions and industry terms. Make sure you also include terms. This list is the combination of two lists, first all the endpoints from the urls of the history, second it extracts all the.. Endpoints Wordlist.
From github.com
GitHub xnlh4ck3r/GAPBurpExtension Burp Extension to find potential endpoints, parameters Endpoints Wordlist when looking for hidden endpoints, use wordlists based on common api naming conventions and industry terms. list of api endpoints & objects: Make sure you also include terms. It's a collection of multiple types of lists used during security assessments,. This list is the combination of two lists, first all the endpoints from the urls of the history,. Endpoints Wordlist.
From www.geeksforgeeks.org
Endpoints in Wireshark Endpoints Wordlist list of api endpoints & objects: Make sure you also include terms. seclists is the security tester's companion. when looking for hidden endpoints, use wordlists based on common api naming conventions and industry terms. It's a collection of multiple types of lists used during security assessments,. list of api endpoints & objects this file contains bidirectional. Endpoints Wordlist.
From docs.rapidapi.com
Endpoints Endpoints Wordlist list of api endpoints & objects: Make sure you also include terms. This list is the combination of two lists, first all the endpoints from the urls of the history, second it extracts all the. It's a collection of multiple types of lists used during security assessments,. when looking for hidden endpoints, use wordlists based on common api. Endpoints Wordlist.
From github.com
GitHub endpoints/endpointsexample an example api written using endpoints Endpoints Wordlist seclists is the security tester's companion. when looking for hidden endpoints, use wordlists based on common api naming conventions and industry terms. list of api endpoints & objects this file contains bidirectional unicode text that may be interpreted or compiled. This list is the combination of two lists, first all the endpoints from the urls of the. Endpoints Wordlist.
From developer.tripletex.no
New endpoints available for standardTime Tripletex For Developers Endpoints Wordlist content discovery tooling currently relies on static txt files as wordlists and it is up to the user to perform bruteforces using different. It's a collection of multiple types of lists used during security assessments,. This list is the combination of two lists, first all the endpoints from the urls of the history, second it extracts all the. A. Endpoints Wordlist.
From www.thruinc.com
Endpoint Examples OptiPaaS Guide 1 Endpoints Wordlist content discovery tooling currently relies on static txt files as wordlists and it is up to the user to perform bruteforces using different. Make sure you also include terms. seclists is the security tester's companion. list of api endpoints & objects: It's a collection of multiple types of lists used during security assessments,. list of api. Endpoints Wordlist.
From docs.merge.dev
Writing to POST endpoints with Merge Endpoints Wordlist A list of 3203 common api endpoints and objects designed for fuzzing. This list is the combination of two lists, first all the endpoints from the urls of the history, second it extracts all the. content discovery tooling currently relies on static txt files as wordlists and it is up to the user to perform bruteforces using different. Make. Endpoints Wordlist.
From cloudy-sec.com
Understand and Configure Microsoft Endpoint DLP Cloudy Security Endpoints Wordlist list of api endpoints & objects this file contains bidirectional unicode text that may be interpreted or compiled. content discovery tooling currently relies on static txt files as wordlists and it is up to the user to perform bruteforces using different. A list of 3203 common api endpoints and objects designed for fuzzing. list of api endpoints. Endpoints Wordlist.
From www.juniper.net
Endpoints Overview (Virtual) Apstra 4.1 Juniper Networks Endpoints Wordlist seclists is the security tester's companion. Make sure you also include terms. when looking for hidden endpoints, use wordlists based on common api naming conventions and industry terms. list of api endpoints & objects: It's a collection of multiple types of lists used during security assessments,. list of api endpoints & objects this file contains bidirectional. Endpoints Wordlist.
From ibkrm.github.io
VPC Endpoints AWS SA Professional Endpoints Wordlist list of api endpoints & objects: when looking for hidden endpoints, use wordlists based on common api naming conventions and industry terms. content discovery tooling currently relies on static txt files as wordlists and it is up to the user to perform bruteforces using different. It's a collection of multiple types of lists used during security assessments,.. Endpoints Wordlist.
From docs.arrigo.se
Endpoints The written words. Endpoints Wordlist This list is the combination of two lists, first all the endpoints from the urls of the history, second it extracts all the. list of api endpoints & objects: seclists is the security tester's companion. A list of 3203 common api endpoints and objects designed for fuzzing. content discovery tooling currently relies on static txt files as. Endpoints Wordlist.
From virtualarmour.com
What Are Endpoints (& How Does Endpoint Security Work)? Endpoints Wordlist A list of 3203 common api endpoints and objects designed for fuzzing. list of api endpoints & objects this file contains bidirectional unicode text that may be interpreted or compiled. seclists is the security tester's companion. This list is the combination of two lists, first all the endpoints from the urls of the history, second it extracts all. Endpoints Wordlist.
From www.amathsdictionaryforkids.com
endpoint A Maths Dictionary for Kids Quick Reference by Jenny Eather Endpoints Wordlist Make sure you also include terms. A list of 3203 common api endpoints and objects designed for fuzzing. This list is the combination of two lists, first all the endpoints from the urls of the history, second it extracts all the. It's a collection of multiple types of lists used during security assessments,. list of api endpoints & objects:. Endpoints Wordlist.
From www.weareendpoint.com
We help add ‘Wayfinding’ to the Oxford English Dictionary Endpoint Endpoints Wordlist Make sure you also include terms. This list is the combination of two lists, first all the endpoints from the urls of the history, second it extracts all the. when looking for hidden endpoints, use wordlists based on common api naming conventions and industry terms. A list of 3203 common api endpoints and objects designed for fuzzing. list. Endpoints Wordlist.
From memart.vn
Tìm hiểu api endpoint là gì và cách sử dụng trong lập trình web của bạn Endpoints Wordlist A list of 3203 common api endpoints and objects designed for fuzzing. when looking for hidden endpoints, use wordlists based on common api naming conventions and industry terms. list of api endpoints & objects: seclists is the security tester's companion. This list is the combination of two lists, first all the endpoints from the urls of the. Endpoints Wordlist.
From www.opswat.com
What is Endpoint Management? OPSWAT Endpoints Wordlist A list of 3203 common api endpoints and objects designed for fuzzing. content discovery tooling currently relies on static txt files as wordlists and it is up to the user to perform bruteforces using different. This list is the combination of two lists, first all the endpoints from the urls of the history, second it extracts all the. . Endpoints Wordlist.
From thecitrusreport.com
What is an 'endpoint' in The Citrus Report Endpoints Wordlist Make sure you also include terms. This list is the combination of two lists, first all the endpoints from the urls of the history, second it extracts all the. list of api endpoints & objects this file contains bidirectional unicode text that may be interpreted or compiled. when looking for hidden endpoints, use wordlists based on common api. Endpoints Wordlist.
From api-blog.oxforddictionaries.com
Abracadabra! Fun things to do with the Wordlist endpoint Oxford Dictionaries API blog Endpoints Wordlist content discovery tooling currently relies on static txt files as wordlists and it is up to the user to perform bruteforces using different. list of api endpoints & objects this file contains bidirectional unicode text that may be interpreted or compiled. when looking for hidden endpoints, use wordlists based on common api naming conventions and industry terms.. Endpoints Wordlist.
From docs.nodescript.dev
Endpoints NodeScript Documentation Endpoints Wordlist seclists is the security tester's companion. This list is the combination of two lists, first all the endpoints from the urls of the history, second it extracts all the. A list of 3203 common api endpoints and objects designed for fuzzing. when looking for hidden endpoints, use wordlists based on common api naming conventions and industry terms. . Endpoints Wordlist.
From www.revealdata.com
How to Create & Manage Wordlists Endpoints Wordlist A list of 3203 common api endpoints and objects designed for fuzzing. This list is the combination of two lists, first all the endpoints from the urls of the history, second it extracts all the. It's a collection of multiple types of lists used during security assessments,. Make sure you also include terms. when looking for hidden endpoints, use. Endpoints Wordlist.
From studylib.net
Gregmat Wordlist For GRE Endpoints Wordlist Make sure you also include terms. seclists is the security tester's companion. content discovery tooling currently relies on static txt files as wordlists and it is up to the user to perform bruteforces using different. This list is the combination of two lists, first all the endpoints from the urls of the history, second it extracts all the.. Endpoints Wordlist.
From www.golinuxcloud.com
100 proven ways to find hidden endpoints [Tutorial] GoLinuxCloud Endpoints Wordlist A list of 3203 common api endpoints and objects designed for fuzzing. list of api endpoints & objects this file contains bidirectional unicode text that may be interpreted or compiled. This list is the combination of two lists, first all the endpoints from the urls of the history, second it extracts all the. when looking for hidden endpoints,. Endpoints Wordlist.