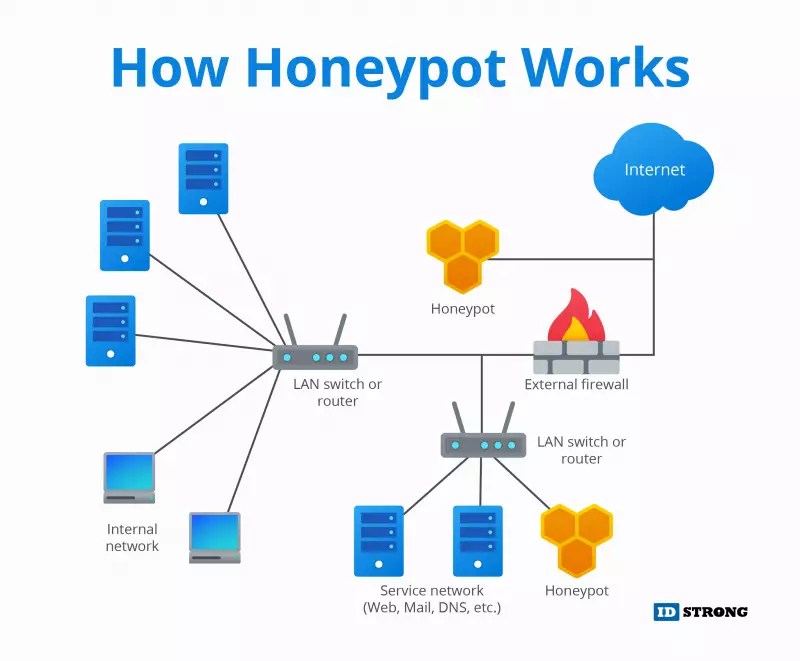
Honeypots In Network Security In Hindi . Honeypots appear to be a weak entry point into an organization network to distract. Honeypot is a crucial defense layer in network security architecture. Honeypots replicate genuine systems with valuable data. Honeypots are used to capture information from unauthorized intruders that are tricked into accessing them because they appear to be a legitimate part of the network. They may have ports that are vulnerable to a port scan, which is a technique. Its main goal is to detect, deflect, or research hacking attempts and understand hackers to improve security. Honeypots use security vulnerabilities to lure in attackers. By setting a “honey trap” or a “honeypot,” they aimed to attract and ensnare targets into divulging sensitive information.
from www.idstrong.com
Honeypots use security vulnerabilities to lure in attackers. Honeypot is a crucial defense layer in network security architecture. Its main goal is to detect, deflect, or research hacking attempts and understand hackers to improve security. They may have ports that are vulnerable to a port scan, which is a technique. By setting a “honey trap” or a “honeypot,” they aimed to attract and ensnare targets into divulging sensitive information. Honeypots appear to be a weak entry point into an organization network to distract. Honeypots are used to capture information from unauthorized intruders that are tricked into accessing them because they appear to be a legitimate part of the network. Honeypots replicate genuine systems with valuable data.
What is a Honeypot and How it Attracts Cyber Attacks?
Honeypots In Network Security In Hindi Its main goal is to detect, deflect, or research hacking attempts and understand hackers to improve security. Its main goal is to detect, deflect, or research hacking attempts and understand hackers to improve security. Honeypots use security vulnerabilities to lure in attackers. Honeypots appear to be a weak entry point into an organization network to distract. Honeypot is a crucial defense layer in network security architecture. Honeypots are used to capture information from unauthorized intruders that are tricked into accessing them because they appear to be a legitimate part of the network. By setting a “honey trap” or a “honeypot,” they aimed to attract and ensnare targets into divulging sensitive information. They may have ports that are vulnerable to a port scan, which is a technique. Honeypots replicate genuine systems with valuable data.
From www.eccouncil.org
What is a Honeypot in Cyber Security? Benefits and Types of Honeypot Honeypots In Network Security In Hindi Honeypots replicate genuine systems with valuable data. Honeypots use security vulnerabilities to lure in attackers. Its main goal is to detect, deflect, or research hacking attempts and understand hackers to improve security. They may have ports that are vulnerable to a port scan, which is a technique. Honeypots appear to be a weak entry point into an organization network to. Honeypots In Network Security In Hindi.
From www.insecure.in
What is Honeypot in Cyber Security? Honeypots In Network Security In Hindi By setting a “honey trap” or a “honeypot,” they aimed to attract and ensnare targets into divulging sensitive information. Honeypots use security vulnerabilities to lure in attackers. Honeypots replicate genuine systems with valuable data. Honeypots appear to be a weak entry point into an organization network to distract. Its main goal is to detect, deflect, or research hacking attempts and. Honeypots In Network Security In Hindi.
From cybersrcc.uk
Honeypot As Service CyberSRC Honeypots In Network Security In Hindi Honeypots are used to capture information from unauthorized intruders that are tricked into accessing them because they appear to be a legitimate part of the network. Honeypots use security vulnerabilities to lure in attackers. Honeypots appear to be a weak entry point into an organization network to distract. Honeypot is a crucial defense layer in network security architecture. They may. Honeypots In Network Security In Hindi.
From sectigostore.com
What Is a Honeypot in Network Security? Definition, Types & Uses Honeypots In Network Security In Hindi By setting a “honey trap” or a “honeypot,” they aimed to attract and ensnare targets into divulging sensitive information. Honeypot is a crucial defense layer in network security architecture. Its main goal is to detect, deflect, or research hacking attempts and understand hackers to improve security. Honeypots are used to capture information from unauthorized intruders that are tricked into accessing. Honeypots In Network Security In Hindi.
From www.youtube.com
what is honeypot and how to setup a basic honeypot in hindi YouTube Honeypots In Network Security In Hindi Honeypots use security vulnerabilities to lure in attackers. By setting a “honey trap” or a “honeypot,” they aimed to attract and ensnare targets into divulging sensitive information. They may have ports that are vulnerable to a port scan, which is a technique. Honeypots replicate genuine systems with valuable data. Its main goal is to detect, deflect, or research hacking attempts. Honeypots In Network Security In Hindi.
From klactixxb.blob.core.windows.net
Honeypot Cyber Security Examples at Charles Brady blog Honeypots In Network Security In Hindi By setting a “honey trap” or a “honeypot,” they aimed to attract and ensnare targets into divulging sensitive information. Its main goal is to detect, deflect, or research hacking attempts and understand hackers to improve security. Honeypots replicate genuine systems with valuable data. They may have ports that are vulnerable to a port scan, which is a technique. Honeypots use. Honeypots In Network Security In Hindi.
From medium.com
What Is a Honeypot — Do You Have One of These at Work — How do they Honeypots In Network Security In Hindi By setting a “honey trap” or a “honeypot,” they aimed to attract and ensnare targets into divulging sensitive information. Honeypots use security vulnerabilities to lure in attackers. Honeypots replicate genuine systems with valuable data. Honeypot is a crucial defense layer in network security architecture. Honeypots are used to capture information from unauthorized intruders that are tricked into accessing them because. Honeypots In Network Security In Hindi.
From klactixxb.blob.core.windows.net
Honeypot Cyber Security Examples at Charles Brady blog Honeypots In Network Security In Hindi Honeypots appear to be a weak entry point into an organization network to distract. Honeypots are used to capture information from unauthorized intruders that are tricked into accessing them because they appear to be a legitimate part of the network. Honeypots use security vulnerabilities to lure in attackers. Honeypots replicate genuine systems with valuable data. Honeypot is a crucial defense. Honeypots In Network Security In Hindi.
From modem.co.il
How Honeypots Assist IT Teams in Cyber Attack Defense Modem Honeypots In Network Security In Hindi Honeypot is a crucial defense layer in network security architecture. They may have ports that are vulnerable to a port scan, which is a technique. Its main goal is to detect, deflect, or research hacking attempts and understand hackers to improve security. Honeypots use security vulnerabilities to lure in attackers. Honeypots appear to be a weak entry point into an. Honeypots In Network Security In Hindi.
From techgenix.com
Why You Need Honeypot Cybersecurity in Your Company Honeypots In Network Security In Hindi Honeypots are used to capture information from unauthorized intruders that are tricked into accessing them because they appear to be a legitimate part of the network. By setting a “honey trap” or a “honeypot,” they aimed to attract and ensnare targets into divulging sensitive information. Its main goal is to detect, deflect, or research hacking attempts and understand hackers to. Honeypots In Network Security In Hindi.
From www.knowledgehut.com
What is a Honeypot? Types, Benefits, Risks and Best Practices Honeypots In Network Security In Hindi Honeypots appear to be a weak entry point into an organization network to distract. Honeypots replicate genuine systems with valuable data. Honeypot is a crucial defense layer in network security architecture. They may have ports that are vulnerable to a port scan, which is a technique. By setting a “honey trap” or a “honeypot,” they aimed to attract and ensnare. Honeypots In Network Security In Hindi.
From www.studocu.com
Honeypots Honey pots Network And Cyber Security Studocu Honeypots In Network Security In Hindi Honeypots use security vulnerabilities to lure in attackers. Honeypots appear to be a weak entry point into an organization network to distract. Honeypots replicate genuine systems with valuable data. Honeypots are used to capture information from unauthorized intruders that are tricked into accessing them because they appear to be a legitimate part of the network. By setting a “honey trap”. Honeypots In Network Security In Hindi.
From www.eccouncil.org
What is a Honeypot in Cyber Security? Benefits and Types of Honeypot Honeypots In Network Security In Hindi Honeypots appear to be a weak entry point into an organization network to distract. Its main goal is to detect, deflect, or research hacking attempts and understand hackers to improve security. By setting a “honey trap” or a “honeypot,” they aimed to attract and ensnare targets into divulging sensitive information. Honeypots are used to capture information from unauthorized intruders that. Honeypots In Network Security In Hindi.
From slideplayer.com
Honeypot in Mobile Network Security ppt download Honeypots In Network Security In Hindi Its main goal is to detect, deflect, or research hacking attempts and understand hackers to improve security. Honeypots replicate genuine systems with valuable data. Honeypot is a crucial defense layer in network security architecture. Honeypots appear to be a weak entry point into an organization network to distract. Honeypots are used to capture information from unauthorized intruders that are tricked. Honeypots In Network Security In Hindi.
From issuu.com
What is a Honeypot? How does it Improve Network Security? by sysvoot Honeypots In Network Security In Hindi They may have ports that are vulnerable to a port scan, which is a technique. Honeypots are used to capture information from unauthorized intruders that are tricked into accessing them because they appear to be a legitimate part of the network. Honeypots appear to be a weak entry point into an organization network to distract. Honeypots replicate genuine systems with. Honeypots In Network Security In Hindi.
From coinstats.app
CoinStats What Is Honeypots Crypto Scam? How Does It Im... Honeypots In Network Security In Hindi Honeypots appear to be a weak entry point into an organization network to distract. Honeypot is a crucial defense layer in network security architecture. Honeypots are used to capture information from unauthorized intruders that are tricked into accessing them because they appear to be a legitimate part of the network. Honeypots use security vulnerabilities to lure in attackers. Its main. Honeypots In Network Security In Hindi.
From www.youtube.com
What is a Honeypot Cyber Security Tutorial YouTube Honeypots In Network Security In Hindi Honeypots replicate genuine systems with valuable data. Honeypots use security vulnerabilities to lure in attackers. Honeypots are used to capture information from unauthorized intruders that are tricked into accessing them because they appear to be a legitimate part of the network. By setting a “honey trap” or a “honeypot,” they aimed to attract and ensnare targets into divulging sensitive information.. Honeypots In Network Security In Hindi.
From www.sysvoot.com
What is a Honeypot? How does it Improve Network Security? Honeypots In Network Security In Hindi Honeypots replicate genuine systems with valuable data. Honeypots use security vulnerabilities to lure in attackers. Honeypots are used to capture information from unauthorized intruders that are tricked into accessing them because they appear to be a legitimate part of the network. They may have ports that are vulnerable to a port scan, which is a technique. By setting a “honey. Honeypots In Network Security In Hindi.
From www.mdpi.com
Future Free FullText A Highly Interactive HoneypotBased Honeypots In Network Security In Hindi They may have ports that are vulnerable to a port scan, which is a technique. By setting a “honey trap” or a “honeypot,” they aimed to attract and ensnare targets into divulging sensitive information. Honeypot is a crucial defense layer in network security architecture. Its main goal is to detect, deflect, or research hacking attempts and understand hackers to improve. Honeypots In Network Security In Hindi.
From www.youtube.com
Canary tokens tutorial Honeypots Examples in Hindi Cyber Honeypots In Network Security In Hindi Honeypots are used to capture information from unauthorized intruders that are tricked into accessing them because they appear to be a legitimate part of the network. Its main goal is to detect, deflect, or research hacking attempts and understand hackers to improve security. Honeypots appear to be a weak entry point into an organization network to distract. Honeypots use security. Honeypots In Network Security In Hindi.
From dokumen.tips
(PDF) 5. EngHoneypots for Network SurveillanceNiharika DOKUMEN.TIPS Honeypots In Network Security In Hindi Its main goal is to detect, deflect, or research hacking attempts and understand hackers to improve security. Honeypots are used to capture information from unauthorized intruders that are tricked into accessing them because they appear to be a legitimate part of the network. Honeypot is a crucial defense layer in network security architecture. By setting a “honey trap” or a. Honeypots In Network Security In Hindi.
From www.youtube.com
use of honeypots in network security YouTube Honeypots In Network Security In Hindi Honeypots are used to capture information from unauthorized intruders that are tricked into accessing them because they appear to be a legitimate part of the network. By setting a “honey trap” or a “honeypot,” they aimed to attract and ensnare targets into divulging sensitive information. Honeypots replicate genuine systems with valuable data. They may have ports that are vulnerable to. Honeypots In Network Security In Hindi.
From ar.inspiredpencil.com
Honey Pot Security Honeypots In Network Security In Hindi Honeypots appear to be a weak entry point into an organization network to distract. Honeypots are used to capture information from unauthorized intruders that are tricked into accessing them because they appear to be a legitimate part of the network. Its main goal is to detect, deflect, or research hacking attempts and understand hackers to improve security. By setting a. Honeypots In Network Security In Hindi.
From www.idstrong.com
What is a Honeypot and How it Attracts Cyber Attacks? Honeypots In Network Security In Hindi They may have ports that are vulnerable to a port scan, which is a technique. Honeypots appear to be a weak entry point into an organization network to distract. Its main goal is to detect, deflect, or research hacking attempts and understand hackers to improve security. Honeypots are used to capture information from unauthorized intruders that are tricked into accessing. Honeypots In Network Security In Hindi.
From gridinsoft.com
Honeypot in Cybersecurity and How It Can Trap Attackers? Gridinsoft Honeypots In Network Security In Hindi By setting a “honey trap” or a “honeypot,” they aimed to attract and ensnare targets into divulging sensitive information. Honeypots appear to be a weak entry point into an organization network to distract. Honeypots are used to capture information from unauthorized intruders that are tricked into accessing them because they appear to be a legitimate part of the network. Honeypot. Honeypots In Network Security In Hindi.
From www.bol.com
Honeypots in Network Security 9783659113529 Deniz Akkaya Boeken Honeypots In Network Security In Hindi Honeypots replicate genuine systems with valuable data. Honeypots are used to capture information from unauthorized intruders that are tricked into accessing them because they appear to be a legitimate part of the network. By setting a “honey trap” or a “honeypot,” they aimed to attract and ensnare targets into divulging sensitive information. Honeypots use security vulnerabilities to lure in attackers.. Honeypots In Network Security In Hindi.
From www.sentinelone.com
What is Honeypot? Working, Types, Benefits, and More Honeypots In Network Security In Hindi They may have ports that are vulnerable to a port scan, which is a technique. Honeypots are used to capture information from unauthorized intruders that are tricked into accessing them because they appear to be a legitimate part of the network. Honeypots appear to be a weak entry point into an organization network to distract. By setting a “honey trap”. Honeypots In Network Security In Hindi.
From techpiton.com
Honeypot Technique Technology and How it Works in Cyber Security Honeypots In Network Security In Hindi By setting a “honey trap” or a “honeypot,” they aimed to attract and ensnare targets into divulging sensitive information. They may have ports that are vulnerable to a port scan, which is a technique. Honeypots are used to capture information from unauthorized intruders that are tricked into accessing them because they appear to be a legitimate part of the network.. Honeypots In Network Security In Hindi.
From trainings.internshala.com
Honeypot in Cyber Security Types, Benefits, Risks & Examples Honeypots In Network Security In Hindi By setting a “honey trap” or a “honeypot,” they aimed to attract and ensnare targets into divulging sensitive information. Honeypots are used to capture information from unauthorized intruders that are tricked into accessing them because they appear to be a legitimate part of the network. Honeypots appear to be a weak entry point into an organization network to distract. Its. Honeypots In Network Security In Hindi.
From www.miracletechs.com
Honeypots improve security Honeypots In Network Security In Hindi Honeypots are used to capture information from unauthorized intruders that are tricked into accessing them because they appear to be a legitimate part of the network. Its main goal is to detect, deflect, or research hacking attempts and understand hackers to improve security. By setting a “honey trap” or a “honeypot,” they aimed to attract and ensnare targets into divulging. Honeypots In Network Security In Hindi.
From www.networksolutions.com
Honeypot Network Security What It Is and How to Use It Defensively Honeypots In Network Security In Hindi Honeypots are used to capture information from unauthorized intruders that are tricked into accessing them because they appear to be a legitimate part of the network. Honeypots appear to be a weak entry point into an organization network to distract. Its main goal is to detect, deflect, or research hacking attempts and understand hackers to improve security. They may have. Honeypots In Network Security In Hindi.
From www.youtube.com
What is Honeypot in Cyber Security Honeypot Explanation in Hindi Honeypots In Network Security In Hindi Honeypot is a crucial defense layer in network security architecture. Honeypots appear to be a weak entry point into an organization network to distract. Its main goal is to detect, deflect, or research hacking attempts and understand hackers to improve security. Honeypots are used to capture information from unauthorized intruders that are tricked into accessing them because they appear to. Honeypots In Network Security In Hindi.
From sectigostore.com
What Is a Honeypot in Network Security? Definition, Types & Uses Honeypots In Network Security In Hindi Honeypots are used to capture information from unauthorized intruders that are tricked into accessing them because they appear to be a legitimate part of the network. Honeypots replicate genuine systems with valuable data. Honeypots appear to be a weak entry point into an organization network to distract. Honeypot is a crucial defense layer in network security architecture. By setting a. Honeypots In Network Security In Hindi.
From cybersecuritynews.com
What is a Honeypot and How it Improves Network security? Honeypots In Network Security In Hindi Its main goal is to detect, deflect, or research hacking attempts and understand hackers to improve security. Honeypots use security vulnerabilities to lure in attackers. Honeypots appear to be a weak entry point into an organization network to distract. Honeypot is a crucial defense layer in network security architecture. They may have ports that are vulnerable to a port scan,. Honeypots In Network Security In Hindi.
From www.youtube.com
What is a Honeypot and how does it work? YouTube Honeypots In Network Security In Hindi By setting a “honey trap” or a “honeypot,” they aimed to attract and ensnare targets into divulging sensitive information. Honeypot is a crucial defense layer in network security architecture. They may have ports that are vulnerable to a port scan, which is a technique. Honeypots are used to capture information from unauthorized intruders that are tricked into accessing them because. Honeypots In Network Security In Hindi.