Hadoop Yarn Exploit . We look into how threat actors are exploiting apache hadoop yarn, a part of the hadoop framework that is responsible for. There was an unauthorized access vulnerability in hadoop yarn resourcemanager. 1065 servers are exposed and vulnerable. A monero cryptomining campaign has been actively abusing exposed hadoop yarn servers since april 2018 and mined for a total. Rate of hadoop yarn exploits is slowing but still at a concerning 350,000 events per day. Threat actors are targeting misconfigured and vulnerable servers running apache hadoop yarn, docker, atlassian confluence, and. The spinning yarn cyberattack campaign targets cloud servers running apache hadoop, atlassian confluence, docker, and redis. This vulnerability existed in hadoop yarn, the.
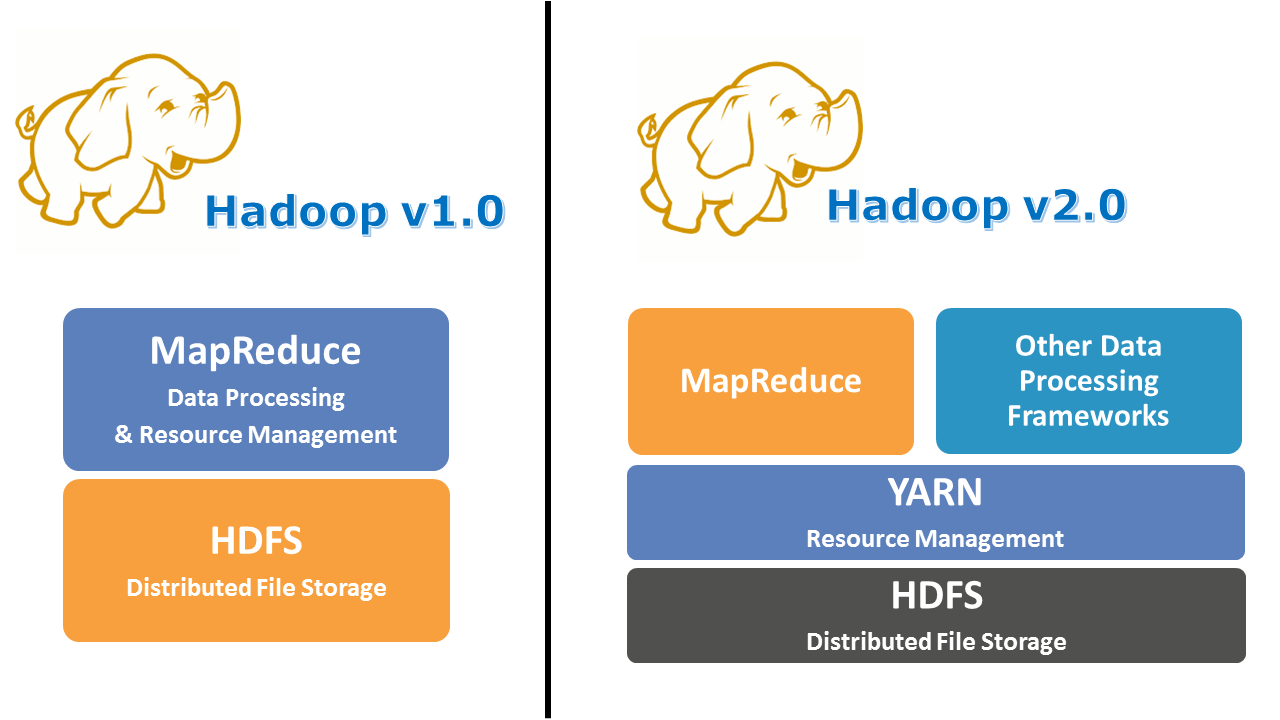
from www.edureka.co
There was an unauthorized access vulnerability in hadoop yarn resourcemanager. Threat actors are targeting misconfigured and vulnerable servers running apache hadoop yarn, docker, atlassian confluence, and. The spinning yarn cyberattack campaign targets cloud servers running apache hadoop, atlassian confluence, docker, and redis. This vulnerability existed in hadoop yarn, the. A monero cryptomining campaign has been actively abusing exposed hadoop yarn servers since april 2018 and mined for a total. We look into how threat actors are exploiting apache hadoop yarn, a part of the hadoop framework that is responsible for. 1065 servers are exposed and vulnerable. Rate of hadoop yarn exploits is slowing but still at a concerning 350,000 events per day.
Apache Hadoop YARN Introduction to YARN Architecture Edureka
Hadoop Yarn Exploit This vulnerability existed in hadoop yarn, the. Rate of hadoop yarn exploits is slowing but still at a concerning 350,000 events per day. We look into how threat actors are exploiting apache hadoop yarn, a part of the hadoop framework that is responsible for. The spinning yarn cyberattack campaign targets cloud servers running apache hadoop, atlassian confluence, docker, and redis. Threat actors are targeting misconfigured and vulnerable servers running apache hadoop yarn, docker, atlassian confluence, and. A monero cryptomining campaign has been actively abusing exposed hadoop yarn servers since april 2018 and mined for a total. There was an unauthorized access vulnerability in hadoop yarn resourcemanager. This vulnerability existed in hadoop yarn, the. 1065 servers are exposed and vulnerable.
From hackernoon.com
Hadoop YARN Assessment of the Attack Surface and Its Exploits HackerNoon Hadoop Yarn Exploit Threat actors are targeting misconfigured and vulnerable servers running apache hadoop yarn, docker, atlassian confluence, and. We look into how threat actors are exploiting apache hadoop yarn, a part of the hadoop framework that is responsible for. Rate of hadoop yarn exploits is slowing but still at a concerning 350,000 events per day. The spinning yarn cyberattack campaign targets cloud. Hadoop Yarn Exploit.
From securityboulevard.com
Hadoop YARN An Assessment of the Attack Surface and Its Exploits Hadoop Yarn Exploit A monero cryptomining campaign has been actively abusing exposed hadoop yarn servers since april 2018 and mined for a total. This vulnerability existed in hadoop yarn, the. There was an unauthorized access vulnerability in hadoop yarn resourcemanager. We look into how threat actors are exploiting apache hadoop yarn, a part of the hadoop framework that is responsible for. Rate of. Hadoop Yarn Exploit.
From blog.csdn.net
Hadoopyarn未授权访问漏洞复_hadoop未授权访问漏洞修复CSDN博客 Hadoop Yarn Exploit There was an unauthorized access vulnerability in hadoop yarn resourcemanager. 1065 servers are exposed and vulnerable. This vulnerability existed in hadoop yarn, the. A monero cryptomining campaign has been actively abusing exposed hadoop yarn servers since april 2018 and mined for a total. We look into how threat actors are exploiting apache hadoop yarn, a part of the hadoop framework. Hadoop Yarn Exploit.
From www.youtube.com
What is Hadoop Yarn? Hadoop Yarn Tutorial Hadoop Yarn Architecture Hadoop Yarn Exploit The spinning yarn cyberattack campaign targets cloud servers running apache hadoop, atlassian confluence, docker, and redis. We look into how threat actors are exploiting apache hadoop yarn, a part of the hadoop framework that is responsible for. Threat actors are targeting misconfigured and vulnerable servers running apache hadoop yarn, docker, atlassian confluence, and. A monero cryptomining campaign has been actively. Hadoop Yarn Exploit.
From www.radware.com
Hadoop YARN An Assessment of the Attack Surface and Its Exploits Hadoop Yarn Exploit Rate of hadoop yarn exploits is slowing but still at a concerning 350,000 events per day. A monero cryptomining campaign has been actively abusing exposed hadoop yarn servers since april 2018 and mined for a total. This vulnerability existed in hadoop yarn, the. 1065 servers are exposed and vulnerable. We look into how threat actors are exploiting apache hadoop yarn,. Hadoop Yarn Exploit.
From www.educba.com
What is Yarn in Hadoop Architecture and Key Features of Yarn Hadoop Yarn Exploit There was an unauthorized access vulnerability in hadoop yarn resourcemanager. We look into how threat actors are exploiting apache hadoop yarn, a part of the hadoop framework that is responsible for. 1065 servers are exposed and vulnerable. Threat actors are targeting misconfigured and vulnerable servers running apache hadoop yarn, docker, atlassian confluence, and. Rate of hadoop yarn exploits is slowing. Hadoop Yarn Exploit.
From www.radware.com
Hadoop YARN An Assessment of the Attack Surface and Its Exploits Hadoop Yarn Exploit A monero cryptomining campaign has been actively abusing exposed hadoop yarn servers since april 2018 and mined for a total. Threat actors are targeting misconfigured and vulnerable servers running apache hadoop yarn, docker, atlassian confluence, and. This vulnerability existed in hadoop yarn, the. The spinning yarn cyberattack campaign targets cloud servers running apache hadoop, atlassian confluence, docker, and redis. Rate. Hadoop Yarn Exploit.
From securityboulevard.com
Hadoop YARN An Assessment of the Attack Surface and Its Exploits Hadoop Yarn Exploit Rate of hadoop yarn exploits is slowing but still at a concerning 350,000 events per day. The spinning yarn cyberattack campaign targets cloud servers running apache hadoop, atlassian confluence, docker, and redis. A monero cryptomining campaign has been actively abusing exposed hadoop yarn servers since april 2018 and mined for a total. We look into how threat actors are exploiting. Hadoop Yarn Exploit.
From medium.com
Hadoop YARN Assessment of the Attack Surface and Its Exploits by Hadoop Yarn Exploit There was an unauthorized access vulnerability in hadoop yarn resourcemanager. A monero cryptomining campaign has been actively abusing exposed hadoop yarn servers since april 2018 and mined for a total. The spinning yarn cyberattack campaign targets cloud servers running apache hadoop, atlassian confluence, docker, and redis. Threat actors are targeting misconfigured and vulnerable servers running apache hadoop yarn, docker, atlassian. Hadoop Yarn Exploit.
From www.radware.com
Hadoop YARN An Assessment of the Attack Surface and Its Exploits Hadoop Yarn Exploit 1065 servers are exposed and vulnerable. The spinning yarn cyberattack campaign targets cloud servers running apache hadoop, atlassian confluence, docker, and redis. This vulnerability existed in hadoop yarn, the. There was an unauthorized access vulnerability in hadoop yarn resourcemanager. We look into how threat actors are exploiting apache hadoop yarn, a part of the hadoop framework that is responsible for.. Hadoop Yarn Exploit.
From stacklima.com
Architecture Hadoop YARN StackLima Hadoop Yarn Exploit We look into how threat actors are exploiting apache hadoop yarn, a part of the hadoop framework that is responsible for. 1065 servers are exposed and vulnerable. The spinning yarn cyberattack campaign targets cloud servers running apache hadoop, atlassian confluence, docker, and redis. Rate of hadoop yarn exploits is slowing but still at a concerning 350,000 events per day. A. Hadoop Yarn Exploit.
From hackernoon.com
Hadoop YARN Assessment of the Attack Surface and Its Exploits HackerNoon Hadoop Yarn Exploit A monero cryptomining campaign has been actively abusing exposed hadoop yarn servers since april 2018 and mined for a total. Rate of hadoop yarn exploits is slowing but still at a concerning 350,000 events per day. The spinning yarn cyberattack campaign targets cloud servers running apache hadoop, atlassian confluence, docker, and redis. Threat actors are targeting misconfigured and vulnerable servers. Hadoop Yarn Exploit.
From www.alibabacloud.com
ZeroDay Attack Analysis and Dissemination Method Disclosure for Hadoop Hadoop Yarn Exploit There was an unauthorized access vulnerability in hadoop yarn resourcemanager. The spinning yarn cyberattack campaign targets cloud servers running apache hadoop, atlassian confluence, docker, and redis. We look into how threat actors are exploiting apache hadoop yarn, a part of the hadoop framework that is responsible for. A monero cryptomining campaign has been actively abusing exposed hadoop yarn servers since. Hadoop Yarn Exploit.
From cloud2data.com
Apache Hadoop And Yarn Features and functions of Hadoop YARN Cloud2Data Hadoop Yarn Exploit The spinning yarn cyberattack campaign targets cloud servers running apache hadoop, atlassian confluence, docker, and redis. There was an unauthorized access vulnerability in hadoop yarn resourcemanager. 1065 servers are exposed and vulnerable. A monero cryptomining campaign has been actively abusing exposed hadoop yarn servers since april 2018 and mined for a total. This vulnerability existed in hadoop yarn, the. Threat. Hadoop Yarn Exploit.
From www.trendmicro.com
Threat Actors Exploit Misconfigured Apache Hadoop YARN Trend Micro (US) Hadoop Yarn Exploit A monero cryptomining campaign has been actively abusing exposed hadoop yarn servers since april 2018 and mined for a total. The spinning yarn cyberattack campaign targets cloud servers running apache hadoop, atlassian confluence, docker, and redis. 1065 servers are exposed and vulnerable. This vulnerability existed in hadoop yarn, the. We look into how threat actors are exploiting apache hadoop yarn,. Hadoop Yarn Exploit.
From securityboulevard.com
Hadoop YARN An Assessment of the Attack Surface and Its Exploits Hadoop Yarn Exploit The spinning yarn cyberattack campaign targets cloud servers running apache hadoop, atlassian confluence, docker, and redis. A monero cryptomining campaign has been actively abusing exposed hadoop yarn servers since april 2018 and mined for a total. 1065 servers are exposed and vulnerable. We look into how threat actors are exploiting apache hadoop yarn, a part of the hadoop framework that. Hadoop Yarn Exploit.
From securityboulevard.com
Hadoop YARN An Assessment of the Attack Surface and Its Exploits Hadoop Yarn Exploit The spinning yarn cyberattack campaign targets cloud servers running apache hadoop, atlassian confluence, docker, and redis. This vulnerability existed in hadoop yarn, the. We look into how threat actors are exploiting apache hadoop yarn, a part of the hadoop framework that is responsible for. 1065 servers are exposed and vulnerable. Threat actors are targeting misconfigured and vulnerable servers running apache. Hadoop Yarn Exploit.
From securityboulevard.com
Hadoop YARN An Assessment of the Attack Surface and Its Exploits Hadoop Yarn Exploit 1065 servers are exposed and vulnerable. Threat actors are targeting misconfigured and vulnerable servers running apache hadoop yarn, docker, atlassian confluence, and. The spinning yarn cyberattack campaign targets cloud servers running apache hadoop, atlassian confluence, docker, and redis. This vulnerability existed in hadoop yarn, the. We look into how threat actors are exploiting apache hadoop yarn, a part of the. Hadoop Yarn Exploit.
From www.edureka.co
Apache Hadoop YARN Introduction to YARN Architecture Edureka Hadoop Yarn Exploit This vulnerability existed in hadoop yarn, the. The spinning yarn cyberattack campaign targets cloud servers running apache hadoop, atlassian confluence, docker, and redis. Threat actors are targeting misconfigured and vulnerable servers running apache hadoop yarn, docker, atlassian confluence, and. There was an unauthorized access vulnerability in hadoop yarn resourcemanager. 1065 servers are exposed and vulnerable. We look into how threat. Hadoop Yarn Exploit.
From securityboulevard.com
Hadoop YARN An Assessment of the Attack Surface and Its Exploits Hadoop Yarn Exploit A monero cryptomining campaign has been actively abusing exposed hadoop yarn servers since april 2018 and mined for a total. This vulnerability existed in hadoop yarn, the. There was an unauthorized access vulnerability in hadoop yarn resourcemanager. 1065 servers are exposed and vulnerable. The spinning yarn cyberattack campaign targets cloud servers running apache hadoop, atlassian confluence, docker, and redis. We. Hadoop Yarn Exploit.
From securityboulevard.com
Hadoop YARN An Assessment of the Attack Surface and Its Exploits Hadoop Yarn Exploit Rate of hadoop yarn exploits is slowing but still at a concerning 350,000 events per day. 1065 servers are exposed and vulnerable. The spinning yarn cyberattack campaign targets cloud servers running apache hadoop, atlassian confluence, docker, and redis. This vulnerability existed in hadoop yarn, the. A monero cryptomining campaign has been actively abusing exposed hadoop yarn servers since april 2018. Hadoop Yarn Exploit.
From securityboulevard.com
Hadoop YARN An Assessment of the Attack Surface and Its Exploits Hadoop Yarn Exploit This vulnerability existed in hadoop yarn, the. Threat actors are targeting misconfigured and vulnerable servers running apache hadoop yarn, docker, atlassian confluence, and. 1065 servers are exposed and vulnerable. A monero cryptomining campaign has been actively abusing exposed hadoop yarn servers since april 2018 and mined for a total. Rate of hadoop yarn exploits is slowing but still at a. Hadoop Yarn Exploit.
From securityboulevard.com
Hadoop YARN An Assessment of the Attack Surface and Its Exploits Hadoop Yarn Exploit Rate of hadoop yarn exploits is slowing but still at a concerning 350,000 events per day. There was an unauthorized access vulnerability in hadoop yarn resourcemanager. The spinning yarn cyberattack campaign targets cloud servers running apache hadoop, atlassian confluence, docker, and redis. Threat actors are targeting misconfigured and vulnerable servers running apache hadoop yarn, docker, atlassian confluence, and. We look. Hadoop Yarn Exploit.
From www.radware.com
Hadoop YARN An Assessment of the Attack Surface and Its Exploits Hadoop Yarn Exploit We look into how threat actors are exploiting apache hadoop yarn, a part of the hadoop framework that is responsible for. The spinning yarn cyberattack campaign targets cloud servers running apache hadoop, atlassian confluence, docker, and redis. A monero cryptomining campaign has been actively abusing exposed hadoop yarn servers since april 2018 and mined for a total. Rate of hadoop. Hadoop Yarn Exploit.
From securityboulevard.com
Hadoop YARN An Assessment of the Attack Surface and Its Exploits Hadoop Yarn Exploit This vulnerability existed in hadoop yarn, the. 1065 servers are exposed and vulnerable. We look into how threat actors are exploiting apache hadoop yarn, a part of the hadoop framework that is responsible for. The spinning yarn cyberattack campaign targets cloud servers running apache hadoop, atlassian confluence, docker, and redis. Threat actors are targeting misconfigured and vulnerable servers running apache. Hadoop Yarn Exploit.
From velog.io
Hadoop Yarn 아키텍쳐 Hadoop Yarn Exploit Rate of hadoop yarn exploits is slowing but still at a concerning 350,000 events per day. 1065 servers are exposed and vulnerable. The spinning yarn cyberattack campaign targets cloud servers running apache hadoop, atlassian confluence, docker, and redis. We look into how threat actors are exploiting apache hadoop yarn, a part of the hadoop framework that is responsible for. Threat. Hadoop Yarn Exploit.
From medium.com
Hadoop YARN Assessment of the Attack Surface and Its Exploits by Hadoop Yarn Exploit The spinning yarn cyberattack campaign targets cloud servers running apache hadoop, atlassian confluence, docker, and redis. A monero cryptomining campaign has been actively abusing exposed hadoop yarn servers since april 2018 and mined for a total. Threat actors are targeting misconfigured and vulnerable servers running apache hadoop yarn, docker, atlassian confluence, and. 1065 servers are exposed and vulnerable. This vulnerability. Hadoop Yarn Exploit.
From www.radware.com
Hadoop YARN An Assessment of the Attack Surface and Its Exploits Hadoop Yarn Exploit 1065 servers are exposed and vulnerable. A monero cryptomining campaign has been actively abusing exposed hadoop yarn servers since april 2018 and mined for a total. Rate of hadoop yarn exploits is slowing but still at a concerning 350,000 events per day. The spinning yarn cyberattack campaign targets cloud servers running apache hadoop, atlassian confluence, docker, and redis. Threat actors. Hadoop Yarn Exploit.
From securityboulevard.com
Hadoop YARN An Assessment of the Attack Surface and Its Exploits Hadoop Yarn Exploit A monero cryptomining campaign has been actively abusing exposed hadoop yarn servers since april 2018 and mined for a total. Threat actors are targeting misconfigured and vulnerable servers running apache hadoop yarn, docker, atlassian confluence, and. We look into how threat actors are exploiting apache hadoop yarn, a part of the hadoop framework that is responsible for. This vulnerability existed. Hadoop Yarn Exploit.
From securityboulevard.com
Hadoop YARN An Assessment of the Attack Surface and Its Exploits Hadoop Yarn Exploit There was an unauthorized access vulnerability in hadoop yarn resourcemanager. This vulnerability existed in hadoop yarn, the. We look into how threat actors are exploiting apache hadoop yarn, a part of the hadoop framework that is responsible for. A monero cryptomining campaign has been actively abusing exposed hadoop yarn servers since april 2018 and mined for a total. 1065 servers. Hadoop Yarn Exploit.
From securityboulevard.com
Hadoop YARN An Assessment of the Attack Surface and Its Exploits Hadoop Yarn Exploit Rate of hadoop yarn exploits is slowing but still at a concerning 350,000 events per day. 1065 servers are exposed and vulnerable. Threat actors are targeting misconfigured and vulnerable servers running apache hadoop yarn, docker, atlassian confluence, and. This vulnerability existed in hadoop yarn, the. A monero cryptomining campaign has been actively abusing exposed hadoop yarn servers since april 2018. Hadoop Yarn Exploit.
From securityboulevard.com
Hadoop YARN An Assessment of the Attack Surface and Its Exploits Hadoop Yarn Exploit This vulnerability existed in hadoop yarn, the. 1065 servers are exposed and vulnerable. We look into how threat actors are exploiting apache hadoop yarn, a part of the hadoop framework that is responsible for. Rate of hadoop yarn exploits is slowing but still at a concerning 350,000 events per day. A monero cryptomining campaign has been actively abusing exposed hadoop. Hadoop Yarn Exploit.
From securityboulevard.com
Hadoop YARN An Assessment of the Attack Surface and Its Exploits Hadoop Yarn Exploit A monero cryptomining campaign has been actively abusing exposed hadoop yarn servers since april 2018 and mined for a total. Rate of hadoop yarn exploits is slowing but still at a concerning 350,000 events per day. Threat actors are targeting misconfigured and vulnerable servers running apache hadoop yarn, docker, atlassian confluence, and. We look into how threat actors are exploiting. Hadoop Yarn Exploit.
From www.radware.com
Hadoop YARN An Assessment of the Attack Surface and Its Exploits Hadoop Yarn Exploit 1065 servers are exposed and vulnerable. Rate of hadoop yarn exploits is slowing but still at a concerning 350,000 events per day. Threat actors are targeting misconfigured and vulnerable servers running apache hadoop yarn, docker, atlassian confluence, and. The spinning yarn cyberattack campaign targets cloud servers running apache hadoop, atlassian confluence, docker, and redis. A monero cryptomining campaign has been. Hadoop Yarn Exploit.
From data-flair.training
Hadoop Yarn Tutorial for Beginners DataFlair Hadoop Yarn Exploit There was an unauthorized access vulnerability in hadoop yarn resourcemanager. 1065 servers are exposed and vulnerable. Rate of hadoop yarn exploits is slowing but still at a concerning 350,000 events per day. We look into how threat actors are exploiting apache hadoop yarn, a part of the hadoop framework that is responsible for. Threat actors are targeting misconfigured and vulnerable. Hadoop Yarn Exploit.