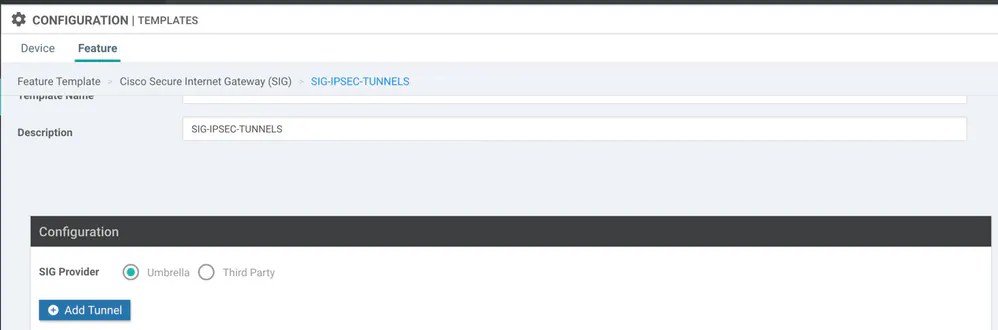
Umbrella Sig Configuration . An umbrella identity represents a network entity, user, or group. Use this checklist to deploy cisco umbrella sig security packages (sig essentials and sig advantage). This document describes how to configure cisco umbrella secure internet gateway (sig) tunnels with ipsec in both active/active and active/standby. You can add an identity to an umbrella policy and enable. This session provides and introduction to umbrella sig security solution and how its different policies increase the security of a network from the cloud. Experts will discuss how to select the most appropriate integration method for your network, as well as best practices for successful implementation.
from www.cisco.com
Use this checklist to deploy cisco umbrella sig security packages (sig essentials and sig advantage). An umbrella identity represents a network entity, user, or group. This document describes how to configure cisco umbrella secure internet gateway (sig) tunnels with ipsec in both active/active and active/standby. Experts will discuss how to select the most appropriate integration method for your network, as well as best practices for successful implementation. You can add an identity to an umbrella policy and enable. This session provides and introduction to umbrella sig security solution and how its different policies increase the security of a network from the cloud.
Configure Umbrella SIG Tunnels for Active/Backup or Active/Active
Umbrella Sig Configuration Use this checklist to deploy cisco umbrella sig security packages (sig essentials and sig advantage). An umbrella identity represents a network entity, user, or group. This session provides and introduction to umbrella sig security solution and how its different policies increase the security of a network from the cloud. Use this checklist to deploy cisco umbrella sig security packages (sig essentials and sig advantage). Experts will discuss how to select the most appropriate integration method for your network, as well as best practices for successful implementation. This document describes how to configure cisco umbrella secure internet gateway (sig) tunnels with ipsec in both active/active and active/standby. You can add an identity to an umbrella policy and enable.
From secure.cisco.com
Umbrella SIG AutoTunnel Configuration Umbrella Sig Configuration Experts will discuss how to select the most appropriate integration method for your network, as well as best practices for successful implementation. This session provides and introduction to umbrella sig security solution and how its different policies increase the security of a network from the cloud. Use this checklist to deploy cisco umbrella sig security packages (sig essentials and sig. Umbrella Sig Configuration.
From www.wwt.com
Umbrella SIG Integration With Cisco SDWAN WWT Umbrella Sig Configuration Experts will discuss how to select the most appropriate integration method for your network, as well as best practices for successful implementation. An umbrella identity represents a network entity, user, or group. This document describes how to configure cisco umbrella secure internet gateway (sig) tunnels with ipsec in both active/active and active/standby. You can add an identity to an umbrella. Umbrella Sig Configuration.
From community.cisco.com
Router Security IKEv2 IPsecTunnel to Umbrella StepbyStep Configtion Umbrella Sig Configuration Experts will discuss how to select the most appropriate integration method for your network, as well as best practices for successful implementation. Use this checklist to deploy cisco umbrella sig security packages (sig essentials and sig advantage). You can add an identity to an umbrella policy and enable. This session provides and introduction to umbrella sig security solution and how. Umbrella Sig Configuration.
From exylwbubi.blob.core.windows.net
Umbrella Configuration Guide at Lura Behrens blog Umbrella Sig Configuration Use this checklist to deploy cisco umbrella sig security packages (sig essentials and sig advantage). You can add an identity to an umbrella policy and enable. This session provides and introduction to umbrella sig security solution and how its different policies increase the security of a network from the cloud. An umbrella identity represents a network entity, user, or group.. Umbrella Sig Configuration.
From umbrella.cisco.com
Cisco Umbrella Breaks New Ground in SASE Convergence Cisco Umbrella Umbrella Sig Configuration Use this checklist to deploy cisco umbrella sig security packages (sig essentials and sig advantage). This document describes how to configure cisco umbrella secure internet gateway (sig) tunnels with ipsec in both active/active and active/standby. You can add an identity to an umbrella policy and enable. Experts will discuss how to select the most appropriate integration method for your network,. Umbrella Sig Configuration.
From exylwbubi.blob.core.windows.net
Umbrella Configuration Guide at Lura Behrens blog Umbrella Sig Configuration You can add an identity to an umbrella policy and enable. Use this checklist to deploy cisco umbrella sig security packages (sig essentials and sig advantage). Experts will discuss how to select the most appropriate integration method for your network, as well as best practices for successful implementation. An umbrella identity represents a network entity, user, or group. This session. Umbrella Sig Configuration.
From support.umbrella.com
FTD ApplicationBased PBR for Umbrella SIG Cisco Umbrella Umbrella Sig Configuration Experts will discuss how to select the most appropriate integration method for your network, as well as best practices for successful implementation. Use this checklist to deploy cisco umbrella sig security packages (sig essentials and sig advantage). An umbrella identity represents a network entity, user, or group. This document describes how to configure cisco umbrella secure internet gateway (sig) tunnels. Umbrella Sig Configuration.
From support.umbrella.com
FTD ApplicationBased PBR for Umbrella SIG Cisco Umbrella Umbrella Sig Configuration This document describes how to configure cisco umbrella secure internet gateway (sig) tunnels with ipsec in both active/active and active/standby. Use this checklist to deploy cisco umbrella sig security packages (sig essentials and sig advantage). An umbrella identity represents a network entity, user, or group. Experts will discuss how to select the most appropriate integration method for your network, as. Umbrella Sig Configuration.
From www.cisco.com
Configure Umbrella SIG Tunnels for Active/Backup or Active/Active Umbrella Sig Configuration Use this checklist to deploy cisco umbrella sig security packages (sig essentials and sig advantage). Experts will discuss how to select the most appropriate integration method for your network, as well as best practices for successful implementation. This document describes how to configure cisco umbrella secure internet gateway (sig) tunnels with ipsec in both active/active and active/standby. An umbrella identity. Umbrella Sig Configuration.
From support.umbrella.com
FTD ApplicationBased PBR for Umbrella SIG Cisco Umbrella Umbrella Sig Configuration An umbrella identity represents a network entity, user, or group. Experts will discuss how to select the most appropriate integration method for your network, as well as best practices for successful implementation. This document describes how to configure cisco umbrella secure internet gateway (sig) tunnels with ipsec in both active/active and active/standby. This session provides and introduction to umbrella sig. Umbrella Sig Configuration.
From docs.umbrella.com
Configure Tunnels with Cisco Router in AWS Umbrella Sig Configuration Experts will discuss how to select the most appropriate integration method for your network, as well as best practices for successful implementation. You can add an identity to an umbrella policy and enable. An umbrella identity represents a network entity, user, or group. This document describes how to configure cisco umbrella secure internet gateway (sig) tunnels with ipsec in both. Umbrella Sig Configuration.
From support.umbrella.com
FTD ApplicationBased PBR for Umbrella SIG Cisco Umbrella Umbrella Sig Configuration This session provides and introduction to umbrella sig security solution and how its different policies increase the security of a network from the cloud. Experts will discuss how to select the most appropriate integration method for your network, as well as best practices for successful implementation. You can add an identity to an umbrella policy and enable. This document describes. Umbrella Sig Configuration.
From secure.cisco.com
Umbrella SIG AutoTunnel Configuration Umbrella Sig Configuration An umbrella identity represents a network entity, user, or group. This session provides and introduction to umbrella sig security solution and how its different policies increase the security of a network from the cloud. You can add an identity to an umbrella policy and enable. Use this checklist to deploy cisco umbrella sig security packages (sig essentials and sig advantage).. Umbrella Sig Configuration.
From www.youtube.com
Cisco Umbrella SIG Introduction (English) YouTube Umbrella Sig Configuration Use this checklist to deploy cisco umbrella sig security packages (sig essentials and sig advantage). You can add an identity to an umbrella policy and enable. Experts will discuss how to select the most appropriate integration method for your network, as well as best practices for successful implementation. This document describes how to configure cisco umbrella secure internet gateway (sig). Umbrella Sig Configuration.
From secure.cisco.com
Umbrella SIG AutoTunnel Configuration Umbrella Sig Configuration Use this checklist to deploy cisco umbrella sig security packages (sig essentials and sig advantage). This session provides and introduction to umbrella sig security solution and how its different policies increase the security of a network from the cloud. Experts will discuss how to select the most appropriate integration method for your network, as well as best practices for successful. Umbrella Sig Configuration.
From exylwbubi.blob.core.windows.net
Umbrella Configuration Guide at Lura Behrens blog Umbrella Sig Configuration An umbrella identity represents a network entity, user, or group. Use this checklist to deploy cisco umbrella sig security packages (sig essentials and sig advantage). Experts will discuss how to select the most appropriate integration method for your network, as well as best practices for successful implementation. This document describes how to configure cisco umbrella secure internet gateway (sig) tunnels. Umbrella Sig Configuration.
From community.cisco.com
Cisco Umbrella SIG essentials license has AnyConnect license included Umbrella Sig Configuration You can add an identity to an umbrella policy and enable. Experts will discuss how to select the most appropriate integration method for your network, as well as best practices for successful implementation. An umbrella identity represents a network entity, user, or group. This session provides and introduction to umbrella sig security solution and how its different policies increase the. Umbrella Sig Configuration.
From www.thenetworkdna.com
Securing Your Network Cisco Umbrella IPSec Tunnels with Palo Alto Umbrella Sig Configuration Experts will discuss how to select the most appropriate integration method for your network, as well as best practices for successful implementation. You can add an identity to an umbrella policy and enable. This document describes how to configure cisco umbrella secure internet gateway (sig) tunnels with ipsec in both active/active and active/standby. This session provides and introduction to umbrella. Umbrella Sig Configuration.
From secure.cisco.com
Umbrella SIG AutoTunnel Configuration Umbrella Sig Configuration You can add an identity to an umbrella policy and enable. Use this checklist to deploy cisco umbrella sig security packages (sig essentials and sig advantage). This session provides and introduction to umbrella sig security solution and how its different policies increase the security of a network from the cloud. This document describes how to configure cisco umbrella secure internet. Umbrella Sig Configuration.
From secure.cisco.com
Umbrella SIG AutoTunnel Configuration Umbrella Sig Configuration This session provides and introduction to umbrella sig security solution and how its different policies increase the security of a network from the cloud. Use this checklist to deploy cisco umbrella sig security packages (sig essentials and sig advantage). This document describes how to configure cisco umbrella secure internet gateway (sig) tunnels with ipsec in both active/active and active/standby. Experts. Umbrella Sig Configuration.
From secure.cisco.com
Umbrella SIG AutoTunnel Configuration Umbrella Sig Configuration An umbrella identity represents a network entity, user, or group. This session provides and introduction to umbrella sig security solution and how its different policies increase the security of a network from the cloud. Experts will discuss how to select the most appropriate integration method for your network, as well as best practices for successful implementation. Use this checklist to. Umbrella Sig Configuration.
From secure.cisco.com
Umbrella SIG AutoTunnel Configuration Umbrella Sig Configuration This document describes how to configure cisco umbrella secure internet gateway (sig) tunnels with ipsec in both active/active and active/standby. Use this checklist to deploy cisco umbrella sig security packages (sig essentials and sig advantage). You can add an identity to an umbrella policy and enable. An umbrella identity represents a network entity, user, or group. This session provides and. Umbrella Sig Configuration.
From exylwbubi.blob.core.windows.net
Umbrella Configuration Guide at Lura Behrens blog Umbrella Sig Configuration Use this checklist to deploy cisco umbrella sig security packages (sig essentials and sig advantage). An umbrella identity represents a network entity, user, or group. You can add an identity to an umbrella policy and enable. This session provides and introduction to umbrella sig security solution and how its different policies increase the security of a network from the cloud.. Umbrella Sig Configuration.
From www.cisco.com
Configure Umbrella SIG Tunnels for Active/Backup or Active/Active Umbrella Sig Configuration This document describes how to configure cisco umbrella secure internet gateway (sig) tunnels with ipsec in both active/active and active/standby. An umbrella identity represents a network entity, user, or group. This session provides and introduction to umbrella sig security solution and how its different policies increase the security of a network from the cloud. You can add an identity to. Umbrella Sig Configuration.
From community.cisco.com
Umbrella SIG SAML Proxy Configuration Cisco Community Umbrella Sig Configuration Experts will discuss how to select the most appropriate integration method for your network, as well as best practices for successful implementation. You can add an identity to an umbrella policy and enable. This document describes how to configure cisco umbrella secure internet gateway (sig) tunnels with ipsec in both active/active and active/standby. Use this checklist to deploy cisco umbrella. Umbrella Sig Configuration.
From secure.cisco.com
Umbrella SIG AutoTunnel Configuration Umbrella Sig Configuration An umbrella identity represents a network entity, user, or group. Use this checklist to deploy cisco umbrella sig security packages (sig essentials and sig advantage). This document describes how to configure cisco umbrella secure internet gateway (sig) tunnels with ipsec in both active/active and active/standby. You can add an identity to an umbrella policy and enable. This session provides and. Umbrella Sig Configuration.
From exylwbubi.blob.core.windows.net
Umbrella Configuration Guide at Lura Behrens blog Umbrella Sig Configuration This session provides and introduction to umbrella sig security solution and how its different policies increase the security of a network from the cloud. You can add an identity to an umbrella policy and enable. This document describes how to configure cisco umbrella secure internet gateway (sig) tunnels with ipsec in both active/active and active/standby. An umbrella identity represents a. Umbrella Sig Configuration.
From community.cisco.com
Umbrella SIG CSR1000V もしくは cEdge からのトンネル接続設定例と トラブルシューティング Cisco Umbrella Sig Configuration This session provides and introduction to umbrella sig security solution and how its different policies increase the security of a network from the cloud. This document describes how to configure cisco umbrella secure internet gateway (sig) tunnels with ipsec in both active/active and active/standby. Use this checklist to deploy cisco umbrella sig security packages (sig essentials and sig advantage). You. Umbrella Sig Configuration.
From secure.cisco.com
Umbrella SIG AutoTunnel Configuration Umbrella Sig Configuration This document describes how to configure cisco umbrella secure internet gateway (sig) tunnels with ipsec in both active/active and active/standby. Use this checklist to deploy cisco umbrella sig security packages (sig essentials and sig advantage). You can add an identity to an umbrella policy and enable. Experts will discuss how to select the most appropriate integration method for your network,. Umbrella Sig Configuration.
From ciscolearning.github.io
SCAZT Integrating Cisco Catalyst SDWAN Branch Site with Cisco Umbrella Umbrella Sig Configuration Experts will discuss how to select the most appropriate integration method for your network, as well as best practices for successful implementation. An umbrella identity represents a network entity, user, or group. This session provides and introduction to umbrella sig security solution and how its different policies increase the security of a network from the cloud. You can add an. Umbrella Sig Configuration.
From secure.cisco.com
Umbrella SIG AutoTunnel Configuration Umbrella Sig Configuration You can add an identity to an umbrella policy and enable. An umbrella identity represents a network entity, user, or group. Experts will discuss how to select the most appropriate integration method for your network, as well as best practices for successful implementation. Use this checklist to deploy cisco umbrella sig security packages (sig essentials and sig advantage). This session. Umbrella Sig Configuration.
From umbrella.cisco.com
Request an Umbrella SIG Proof of Concept Cisco Umbrella Umbrella Sig Configuration Experts will discuss how to select the most appropriate integration method for your network, as well as best practices for successful implementation. Use this checklist to deploy cisco umbrella sig security packages (sig essentials and sig advantage). This document describes how to configure cisco umbrella secure internet gateway (sig) tunnels with ipsec in both active/active and active/standby. This session provides. Umbrella Sig Configuration.
From crossconnect.com
Umbrella SIG Your Field Guide to Protecting the Remote User Umbrella Sig Configuration Experts will discuss how to select the most appropriate integration method for your network, as well as best practices for successful implementation. An umbrella identity represents a network entity, user, or group. Use this checklist to deploy cisco umbrella sig security packages (sig essentials and sig advantage). You can add an identity to an umbrella policy and enable. This document. Umbrella Sig Configuration.
From qtech.com.mx
Cisco Umbrella SIG Essentials Package Umbrella Sig Configuration Use this checklist to deploy cisco umbrella sig security packages (sig essentials and sig advantage). Experts will discuss how to select the most appropriate integration method for your network, as well as best practices for successful implementation. An umbrella identity represents a network entity, user, or group. You can add an identity to an umbrella policy and enable. This session. Umbrella Sig Configuration.
From www.lammle.com
Umbrella Secure Gateway (SIG) Handson Class Todd Lammle, LLC Umbrella Sig Configuration You can add an identity to an umbrella policy and enable. This document describes how to configure cisco umbrella secure internet gateway (sig) tunnels with ipsec in both active/active and active/standby. Experts will discuss how to select the most appropriate integration method for your network, as well as best practices for successful implementation. An umbrella identity represents a network entity,. Umbrella Sig Configuration.