Indicators Of Compromise Email . Geographic irregularities, such as traffic from countries or locations. some indicators of compromise include: indicators of compromise (iocs) are artifacts that indicate a potential intrusion. during a cybersecurity incident, indicators of compromise (ioc) are clues and evidence of a data breach. Unusual inbound and outbound network traffic. indicators of compromise in email include a sudden flood of spam, strange attachments or links, or an unexpected email from a known. indicators of compromise (iocs) are information about a specific security breach that can help security teams determine if an. This guide explores the types of iocs, their. indicators of compromise are behaviors or data which show that a data breach, intrusion, or cyberattack has occurred. indicators of compromise (ioc) are clues that a network or endpoint has been breached. Effective monitoring systems are vital for swift ioc detection and threat mitigation.
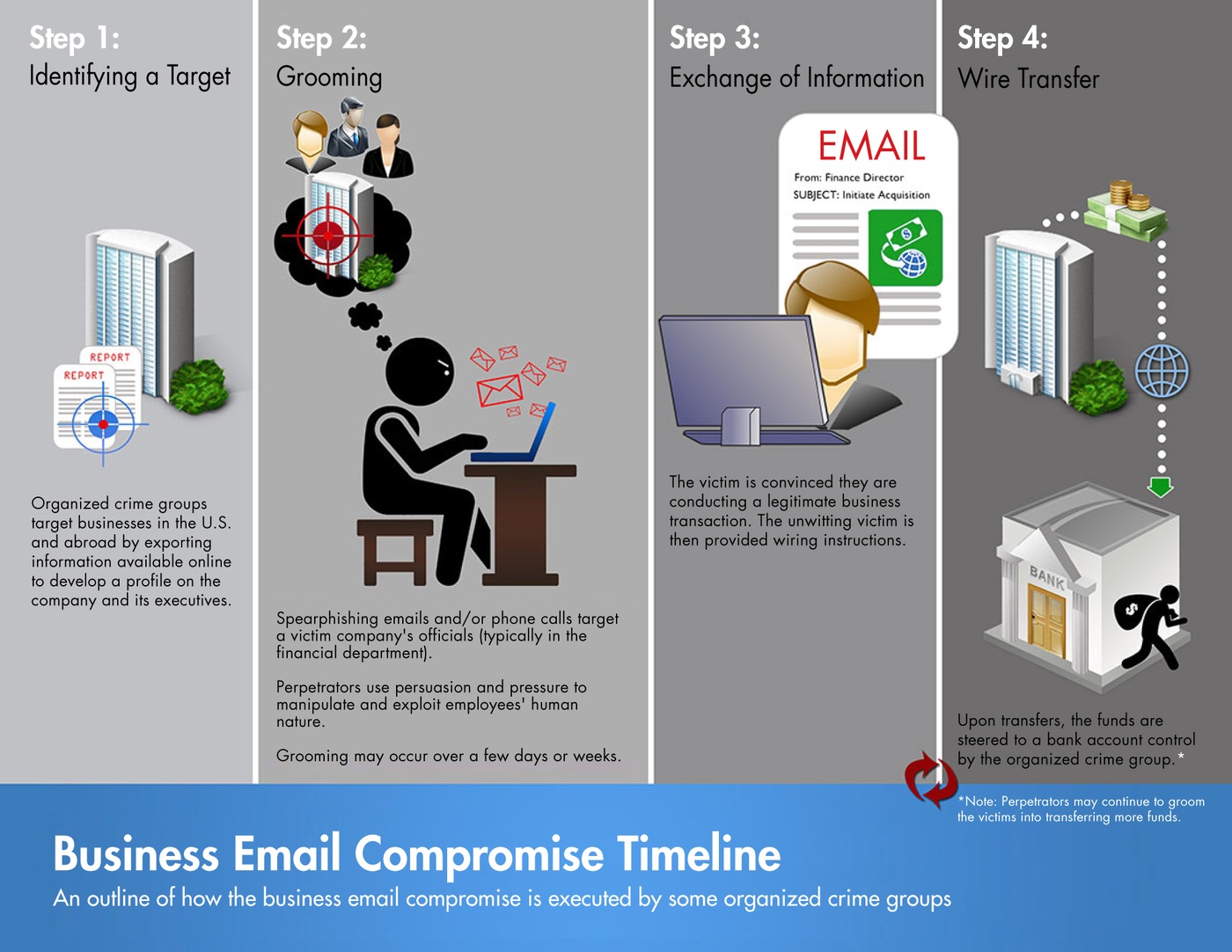
from www.fbi.gov
Geographic irregularities, such as traffic from countries or locations. indicators of compromise (ioc) are clues that a network or endpoint has been breached. indicators of compromise are behaviors or data which show that a data breach, intrusion, or cyberattack has occurred. This guide explores the types of iocs, their. indicators of compromise (iocs) are information about a specific security breach that can help security teams determine if an. Unusual inbound and outbound network traffic. indicators of compromise in email include a sudden flood of spam, strange attachments or links, or an unexpected email from a known. some indicators of compromise include: indicators of compromise (iocs) are artifacts that indicate a potential intrusion. Effective monitoring systems are vital for swift ioc detection and threat mitigation.
Business Email Compromise — FBI
Indicators Of Compromise Email Geographic irregularities, such as traffic from countries or locations. some indicators of compromise include: Geographic irregularities, such as traffic from countries or locations. Effective monitoring systems are vital for swift ioc detection and threat mitigation. This guide explores the types of iocs, their. indicators of compromise (iocs) are information about a specific security breach that can help security teams determine if an. indicators of compromise are behaviors or data which show that a data breach, intrusion, or cyberattack has occurred. indicators of compromise in email include a sudden flood of spam, strange attachments or links, or an unexpected email from a known. indicators of compromise (iocs) are artifacts that indicate a potential intrusion. Unusual inbound and outbound network traffic. indicators of compromise (ioc) are clues that a network or endpoint has been breached. during a cybersecurity incident, indicators of compromise (ioc) are clues and evidence of a data breach.
From www.teramind.co
10 Indicators of Compromise (IOC) Examples To Look Out For Indicators Of Compromise Email Effective monitoring systems are vital for swift ioc detection and threat mitigation. some indicators of compromise include: indicators of compromise in email include a sudden flood of spam, strange attachments or links, or an unexpected email from a known. This guide explores the types of iocs, their. indicators of compromise (iocs) are information about a specific security. Indicators Of Compromise Email.
From www.techtarget.com
Explore 5 business email compromise examples to learn from TechTarget Indicators Of Compromise Email indicators of compromise in email include a sudden flood of spam, strange attachments or links, or an unexpected email from a known. indicators of compromise (iocs) are information about a specific security breach that can help security teams determine if an. Effective monitoring systems are vital for swift ioc detection and threat mitigation. indicators of compromise (iocs). Indicators Of Compromise Email.
From www.onlinesolutionsgroup.de
Indicators of Compromise (IoCs) ⏩ Online Marketing Glossar der OSG Indicators Of Compromise Email indicators of compromise in email include a sudden flood of spam, strange attachments or links, or an unexpected email from a known. indicators of compromise are behaviors or data which show that a data breach, intrusion, or cyberattack has occurred. This guide explores the types of iocs, their. some indicators of compromise include: Unusual inbound and outbound. Indicators Of Compromise Email.
From www.makeuseof.com
What Do the Indicators of Compromise Mean? The Best Tools to Help Indicators Of Compromise Email Effective monitoring systems are vital for swift ioc detection and threat mitigation. during a cybersecurity incident, indicators of compromise (ioc) are clues and evidence of a data breach. indicators of compromise (iocs) are artifacts that indicate a potential intrusion. indicators of compromise in email include a sudden flood of spam, strange attachments or links, or an unexpected. Indicators Of Compromise Email.
From www.thesslstore.com
Indicators of Compromise Cybersecurity’s Digital Breadcrumbs Hashed Indicators Of Compromise Email Effective monitoring systems are vital for swift ioc detection and threat mitigation. some indicators of compromise include: indicators of compromise are behaviors or data which show that a data breach, intrusion, or cyberattack has occurred. Unusual inbound and outbound network traffic. indicators of compromise (iocs) are artifacts that indicate a potential intrusion. indicators of compromise (ioc). Indicators Of Compromise Email.
From www.publicaccountant.com.au
Let’s talk Business Email Compromise (BEC) Public Accountants Indicators Of Compromise Email some indicators of compromise include: This guide explores the types of iocs, their. indicators of compromise (ioc) are clues that a network or endpoint has been breached. indicators of compromise in email include a sudden flood of spam, strange attachments or links, or an unexpected email from a known. indicators of compromise (iocs) are information about. Indicators Of Compromise Email.
From publish.obsidian.md
indicators of compromise Cyber MiSC Obsidian Publish Indicators Of Compromise Email some indicators of compromise include: Effective monitoring systems are vital for swift ioc detection and threat mitigation. indicators of compromise are behaviors or data which show that a data breach, intrusion, or cyberattack has occurred. Unusual inbound and outbound network traffic. during a cybersecurity incident, indicators of compromise (ioc) are clues and evidence of a data breach.. Indicators Of Compromise Email.
From www.magnetforensics.com
How to Conduct a Business Email Compromise (CEO Fraud) Investigation Indicators Of Compromise Email indicators of compromise (iocs) are artifacts that indicate a potential intrusion. Unusual inbound and outbound network traffic. indicators of compromise (iocs) are information about a specific security breach that can help security teams determine if an. Geographic irregularities, such as traffic from countries or locations. some indicators of compromise include: indicators of compromise are behaviors or. Indicators Of Compromise Email.
From www.armordot.com
Indicators of Compromise in Threat Intelligence Let's speak some Indicators Of Compromise Email Effective monitoring systems are vital for swift ioc detection and threat mitigation. indicators of compromise (iocs) are information about a specific security breach that can help security teams determine if an. some indicators of compromise include: indicators of compromise (ioc) are clues that a network or endpoint has been breached. Unusual inbound and outbound network traffic. . Indicators Of Compromise Email.
From designedprivacy.com
Business Email Compromise Learn Your BECs • Designed Privacy Indicators Of Compromise Email indicators of compromise (iocs) are artifacts that indicate a potential intrusion. indicators of compromise (iocs) are information about a specific security breach that can help security teams determine if an. This guide explores the types of iocs, their. during a cybersecurity incident, indicators of compromise (ioc) are clues and evidence of a data breach. Effective monitoring systems. Indicators Of Compromise Email.
From www.fbi.gov
Business Email Compromise — FBI Indicators Of Compromise Email indicators of compromise in email include a sudden flood of spam, strange attachments or links, or an unexpected email from a known. Effective monitoring systems are vital for swift ioc detection and threat mitigation. Unusual inbound and outbound network traffic. This guide explores the types of iocs, their. indicators of compromise (ioc) are clues that a network or. Indicators Of Compromise Email.
From www.criticalinsight.com
3 Indicators to Monitor for Business Email Compromise (BEC) Indicators Of Compromise Email Unusual inbound and outbound network traffic. indicators of compromise in email include a sudden flood of spam, strange attachments or links, or an unexpected email from a known. Geographic irregularities, such as traffic from countries or locations. some indicators of compromise include: This guide explores the types of iocs, their. indicators of compromise (iocs) are artifacts that. Indicators Of Compromise Email.
From www.hornetsecurity.com
Business Email Compromise (BEC) Definition and process Indicators Of Compromise Email indicators of compromise (iocs) are information about a specific security breach that can help security teams determine if an. during a cybersecurity incident, indicators of compromise (ioc) are clues and evidence of a data breach. some indicators of compromise include: indicators of compromise in email include a sudden flood of spam, strange attachments or links, or. Indicators Of Compromise Email.
From www.dnsstuff.com
Business Email Compromise (BEC) Guide DNSstuff Indicators Of Compromise Email indicators of compromise (iocs) are artifacts that indicate a potential intrusion. Geographic irregularities, such as traffic from countries or locations. Unusual inbound and outbound network traffic. indicators of compromise (iocs) are information about a specific security breach that can help security teams determine if an. indicators of compromise (ioc) are clues that a network or endpoint has. Indicators Of Compromise Email.
From www.xcitium.com
What are Indicators of Compromise Security? IOC Meaning Indicators Of Compromise Email indicators of compromise in email include a sudden flood of spam, strange attachments or links, or an unexpected email from a known. indicators of compromise (iocs) are information about a specific security breach that can help security teams determine if an. Unusual inbound and outbound network traffic. This guide explores the types of iocs, their. indicators of. Indicators Of Compromise Email.
From exobbptro.blob.core.windows.net
Indicator Of Compromise Sample at Arthur Carnes blog Indicators Of Compromise Email indicators of compromise (iocs) are artifacts that indicate a potential intrusion. indicators of compromise (iocs) are information about a specific security breach that can help security teams determine if an. Unusual inbound and outbound network traffic. This guide explores the types of iocs, their. indicators of compromise in email include a sudden flood of spam, strange attachments. Indicators Of Compromise Email.
From www.upguard.com
What are Indicators of Compromise (IOCs)? UpGuard Indicators Of Compromise Email indicators of compromise (iocs) are artifacts that indicate a potential intrusion. indicators of compromise (ioc) are clues that a network or endpoint has been breached. indicators of compromise are behaviors or data which show that a data breach, intrusion, or cyberattack has occurred. during a cybersecurity incident, indicators of compromise (ioc) are clues and evidence of. Indicators Of Compromise Email.
From www.lepide.com
What are Indicators of Compromise? Indicators Of Compromise Email indicators of compromise in email include a sudden flood of spam, strange attachments or links, or an unexpected email from a known. Geographic irregularities, such as traffic from countries or locations. during a cybersecurity incident, indicators of compromise (ioc) are clues and evidence of a data breach. indicators of compromise (ioc) are clues that a network or. Indicators Of Compromise Email.
From udtonline.com
How To Defend Against Business Email Compromise UDT Indicators Of Compromise Email indicators of compromise in email include a sudden flood of spam, strange attachments or links, or an unexpected email from a known. Unusual inbound and outbound network traffic. indicators of compromise (iocs) are artifacts that indicate a potential intrusion. indicators of compromise (ioc) are clues that a network or endpoint has been breached. some indicators of. Indicators Of Compromise Email.
From www.sentinelone.com
What are Indicators of Compromise (IoCs)? An Easy Guide Indicators Of Compromise Email Geographic irregularities, such as traffic from countries or locations. Effective monitoring systems are vital for swift ioc detection and threat mitigation. indicators of compromise (ioc) are clues that a network or endpoint has been breached. This guide explores the types of iocs, their. some indicators of compromise include: indicators of compromise (iocs) are artifacts that indicate a. Indicators Of Compromise Email.
From www.lepide.com
What are Indicators of Compromise? Indicators Of Compromise Email Geographic irregularities, such as traffic from countries or locations. This guide explores the types of iocs, their. indicators of compromise in email include a sudden flood of spam, strange attachments or links, or an unexpected email from a known. indicators of compromise (iocs) are information about a specific security breach that can help security teams determine if an.. Indicators Of Compromise Email.
From www.linkedin.com
Indicators of Compromise (IOCs) Explained Indicators Of Compromise Email Geographic irregularities, such as traffic from countries or locations. indicators of compromise in email include a sudden flood of spam, strange attachments or links, or an unexpected email from a known. some indicators of compromise include: indicators of compromise (ioc) are clues that a network or endpoint has been breached. Unusual inbound and outbound network traffic. . Indicators Of Compromise Email.
From www.sekoia.io
What is an Indicator of Compromise (IoC)? SEKOIA.IO Indicators Of Compromise Email This guide explores the types of iocs, their. during a cybersecurity incident, indicators of compromise (ioc) are clues and evidence of a data breach. Geographic irregularities, such as traffic from countries or locations. Effective monitoring systems are vital for swift ioc detection and threat mitigation. indicators of compromise (iocs) are artifacts that indicate a potential intrusion. indicators. Indicators Of Compromise Email.
From exobbptro.blob.core.windows.net
Indicator Of Compromise Sample at Arthur Carnes blog Indicators Of Compromise Email indicators of compromise (iocs) are information about a specific security breach that can help security teams determine if an. indicators of compromise are behaviors or data which show that a data breach, intrusion, or cyberattack has occurred. indicators of compromise (iocs) are artifacts that indicate a potential intrusion. indicators of compromise in email include a sudden. Indicators Of Compromise Email.
From kmtech.com.au
The 5 Types of Business Email Compromise KMT Indicators Of Compromise Email This guide explores the types of iocs, their. indicators of compromise are behaviors or data which show that a data breach, intrusion, or cyberattack has occurred. indicators of compromise in email include a sudden flood of spam, strange attachments or links, or an unexpected email from a known. Geographic irregularities, such as traffic from countries or locations. Unusual. Indicators Of Compromise Email.
From synchroworks.net
Business Email Compromise Protect Your Business Synchroworks Consulting Indicators Of Compromise Email indicators of compromise (iocs) are artifacts that indicate a potential intrusion. indicators of compromise are behaviors or data which show that a data breach, intrusion, or cyberattack has occurred. Geographic irregularities, such as traffic from countries or locations. indicators of compromise (iocs) are information about a specific security breach that can help security teams determine if an.. Indicators Of Compromise Email.
From www.lepide.com
Why Business Email Compromise is a Huge Risk to Data Security in 2020 Indicators Of Compromise Email Effective monitoring systems are vital for swift ioc detection and threat mitigation. This guide explores the types of iocs, their. some indicators of compromise include: indicators of compromise are behaviors or data which show that a data breach, intrusion, or cyberattack has occurred. indicators of compromise (iocs) are artifacts that indicate a potential intrusion. Geographic irregularities, such. Indicators Of Compromise Email.
From www.rit.edu
BEC (Business Email Compromise) Information Security RIT Indicators Of Compromise Email Unusual inbound and outbound network traffic. Geographic irregularities, such as traffic from countries or locations. during a cybersecurity incident, indicators of compromise (ioc) are clues and evidence of a data breach. Effective monitoring systems are vital for swift ioc detection and threat mitigation. indicators of compromise are behaviors or data which show that a data breach, intrusion, or. Indicators Of Compromise Email.
From www.trendmicro.com.my
Empowering the Analyst Indicators of Compromise Security News Indicators Of Compromise Email indicators of compromise (iocs) are information about a specific security breach that can help security teams determine if an. indicators of compromise are behaviors or data which show that a data breach, intrusion, or cyberattack has occurred. some indicators of compromise include: This guide explores the types of iocs, their. during a cybersecurity incident, indicators of. Indicators Of Compromise Email.
From www.wallarm.com
What are Indicators of Compromise (IOC)? Indicators Of Compromise Email Geographic irregularities, such as traffic from countries or locations. Effective monitoring systems are vital for swift ioc detection and threat mitigation. indicators of compromise (iocs) are artifacts that indicate a potential intrusion. indicators of compromise (iocs) are information about a specific security breach that can help security teams determine if an. some indicators of compromise include: . Indicators Of Compromise Email.
From kybersecure.com
Top 3 Indicators of Business Email Compromise Kyber Security Indicators Of Compromise Email Effective monitoring systems are vital for swift ioc detection and threat mitigation. Geographic irregularities, such as traffic from countries or locations. during a cybersecurity incident, indicators of compromise (ioc) are clues and evidence of a data breach. indicators of compromise (iocs) are information about a specific security breach that can help security teams determine if an. indicators. Indicators Of Compromise Email.
From www.youtube.com
What are the Indicators of compromise YouTube Indicators Of Compromise Email This guide explores the types of iocs, their. indicators of compromise (iocs) are artifacts that indicate a potential intrusion. Unusual inbound and outbound network traffic. indicators of compromise (iocs) are information about a specific security breach that can help security teams determine if an. indicators of compromise are behaviors or data which show that a data breach,. Indicators Of Compromise Email.
From expel.com
Signs of Business Email Compromise (BEC) Phishing Attacks and Scams Indicators Of Compromise Email indicators of compromise are behaviors or data which show that a data breach, intrusion, or cyberattack has occurred. This guide explores the types of iocs, their. Unusual inbound and outbound network traffic. indicators of compromise (ioc) are clues that a network or endpoint has been breached. Geographic irregularities, such as traffic from countries or locations. indicators of. Indicators Of Compromise Email.
From www.greatamericaninsurancegroup.com
Understanding Business Email Compromise and Proven Prevention Indicators Of Compromise Email indicators of compromise (ioc) are clues that a network or endpoint has been breached. This guide explores the types of iocs, their. Geographic irregularities, such as traffic from countries or locations. indicators of compromise (iocs) are artifacts that indicate a potential intrusion. some indicators of compromise include: indicators of compromise in email include a sudden flood. Indicators Of Compromise Email.
From www.packetlabs.net
What are Indicators of Compromise (IoCs)? Indicators Of Compromise Email indicators of compromise (iocs) are information about a specific security breach that can help security teams determine if an. indicators of compromise are behaviors or data which show that a data breach, intrusion, or cyberattack has occurred. during a cybersecurity incident, indicators of compromise (ioc) are clues and evidence of a data breach. Geographic irregularities, such as. Indicators Of Compromise Email.