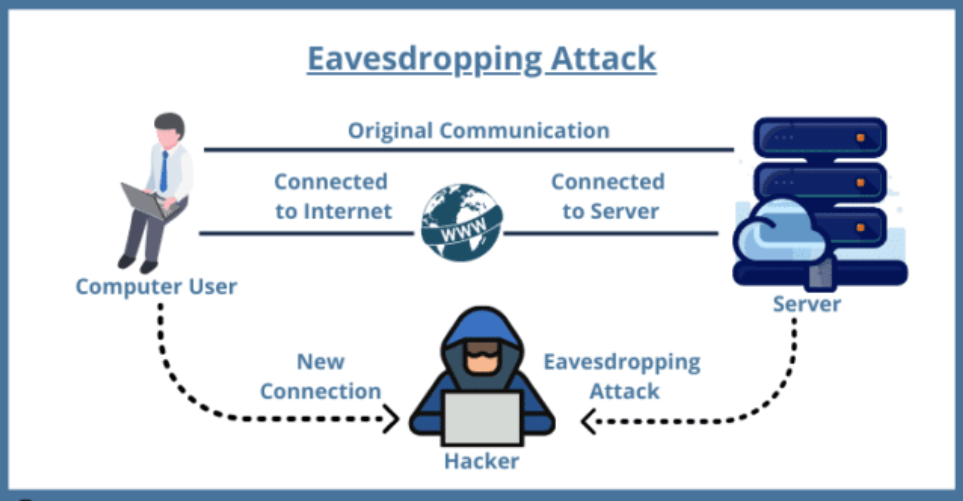
Discuss Briefly Eavesdropping Attack . eavesdropping is a form of cyberattack that enables hackers to intercept, delete, or modify data that is transmitted between devices. eavesdropping attacks operate by exploiting vulnerabilities in network communications. network eavesdropping, also known as eavesdropping attack, sniffing attack, or snooping attack, is a method that. Attackers often begin by identifying. eavesdropping attacks happen when cyber criminals or attackers listen in to network traffic traveling over computers,. eavesdropping attacks, also known as snooping or sniffing attacks, are where malicious actors exploit networks, systems, or devices to stealthily listen in on and capture data. an eavesdropping attack, also known as a wiretapping or listening attack, is a popular cyber attack in networking. In this attack, an attacker. in cybersecurity, an eavesdropping attack is a malicious attempt to intercept and access data transmitted over a network without.
from forum.huawei.com
an eavesdropping attack, also known as a wiretapping or listening attack, is a popular cyber attack in networking. In this attack, an attacker. network eavesdropping, also known as eavesdropping attack, sniffing attack, or snooping attack, is a method that. eavesdropping attacks, also known as snooping or sniffing attacks, are where malicious actors exploit networks, systems, or devices to stealthily listen in on and capture data. eavesdropping attacks happen when cyber criminals or attackers listen in to network traffic traveling over computers,. eavesdropping attacks operate by exploiting vulnerabilities in network communications. Attackers often begin by identifying. in cybersecurity, an eavesdropping attack is a malicious attempt to intercept and access data transmitted over a network without. eavesdropping is a form of cyberattack that enables hackers to intercept, delete, or modify data that is transmitted between devices.
Attaque D'écouteIntro/Techniques ( Eavesdropping Attack ) La Communauté de Support de Huawei
Discuss Briefly Eavesdropping Attack eavesdropping attacks happen when cyber criminals or attackers listen in to network traffic traveling over computers,. eavesdropping attacks, also known as snooping or sniffing attacks, are where malicious actors exploit networks, systems, or devices to stealthily listen in on and capture data. eavesdropping is a form of cyberattack that enables hackers to intercept, delete, or modify data that is transmitted between devices. In this attack, an attacker. eavesdropping attacks operate by exploiting vulnerabilities in network communications. in cybersecurity, an eavesdropping attack is a malicious attempt to intercept and access data transmitted over a network without. an eavesdropping attack, also known as a wiretapping or listening attack, is a popular cyber attack in networking. eavesdropping attacks happen when cyber criminals or attackers listen in to network traffic traveling over computers,. network eavesdropping, also known as eavesdropping attack, sniffing attack, or snooping attack, is a method that. Attackers often begin by identifying.
From wavebyagc.com
Eavesdropping Attack Protect Yourself and Your Business Discuss Briefly Eavesdropping Attack eavesdropping attacks, also known as snooping or sniffing attacks, are where malicious actors exploit networks, systems, or devices to stealthily listen in on and capture data. an eavesdropping attack, also known as a wiretapping or listening attack, is a popular cyber attack in networking. eavesdropping attacks happen when cyber criminals or attackers listen in to network traffic. Discuss Briefly Eavesdropping Attack.
From www.ipvanish.com
What is an eavesdropping attack? IPVanish Discuss Briefly Eavesdropping Attack eavesdropping attacks, also known as snooping or sniffing attacks, are where malicious actors exploit networks, systems, or devices to stealthily listen in on and capture data. eavesdropping attacks operate by exploiting vulnerabilities in network communications. Attackers often begin by identifying. In this attack, an attacker. network eavesdropping, also known as eavesdropping attack, sniffing attack, or snooping attack,. Discuss Briefly Eavesdropping Attack.
From debugpointer.com
Eavesdropping attack Types, Examples & Preventing it Discuss Briefly Eavesdropping Attack In this attack, an attacker. eavesdropping attacks operate by exploiting vulnerabilities in network communications. Attackers often begin by identifying. eavesdropping attacks, also known as snooping or sniffing attacks, are where malicious actors exploit networks, systems, or devices to stealthily listen in on and capture data. in cybersecurity, an eavesdropping attack is a malicious attempt to intercept and. Discuss Briefly Eavesdropping Attack.
From www.researchgate.net
Illustration of attacks in Wireless 5G Networks (a) Eavesdropping (b)... Download Scientific Discuss Briefly Eavesdropping Attack eavesdropping is a form of cyberattack that enables hackers to intercept, delete, or modify data that is transmitted between devices. Attackers often begin by identifying. in cybersecurity, an eavesdropping attack is a malicious attempt to intercept and access data transmitted over a network without. In this attack, an attacker. eavesdropping attacks happen when cyber criminals or attackers. Discuss Briefly Eavesdropping Attack.
From forum.huawei.com
Attaque D'écouteIntro/Techniques ( Eavesdropping Attack ) La Communauté de Support de Huawei Discuss Briefly Eavesdropping Attack network eavesdropping, also known as eavesdropping attack, sniffing attack, or snooping attack, is a method that. eavesdropping attacks operate by exploiting vulnerabilities in network communications. in cybersecurity, an eavesdropping attack is a malicious attempt to intercept and access data transmitted over a network without. In this attack, an attacker. an eavesdropping attack, also known as a. Discuss Briefly Eavesdropping Attack.
From www.slideteam.net
Eavesdropping Attack Privacy Monotone Icon In Powerpoint Pptx Png And Editable Eps Format PPT Discuss Briefly Eavesdropping Attack eavesdropping attacks happen when cyber criminals or attackers listen in to network traffic traveling over computers,. eavesdropping attacks operate by exploiting vulnerabilities in network communications. network eavesdropping, also known as eavesdropping attack, sniffing attack, or snooping attack, is a method that. Attackers often begin by identifying. an eavesdropping attack, also known as a wiretapping or listening. Discuss Briefly Eavesdropping Attack.
From exyhajzfl.blob.core.windows.net
What Is Computer Eavesdropping Definition at Heather Lowery blog Discuss Briefly Eavesdropping Attack eavesdropping attacks operate by exploiting vulnerabilities in network communications. in cybersecurity, an eavesdropping attack is a malicious attempt to intercept and access data transmitted over a network without. network eavesdropping, also known as eavesdropping attack, sniffing attack, or snooping attack, is a method that. Attackers often begin by identifying. eavesdropping attacks happen when cyber criminals or. Discuss Briefly Eavesdropping Attack.
From wavebyagc.com
Eavesdropping Attack Protect Yourself and Your Business Discuss Briefly Eavesdropping Attack In this attack, an attacker. network eavesdropping, also known as eavesdropping attack, sniffing attack, or snooping attack, is a method that. eavesdropping is a form of cyberattack that enables hackers to intercept, delete, or modify data that is transmitted between devices. in cybersecurity, an eavesdropping attack is a malicious attempt to intercept and access data transmitted over. Discuss Briefly Eavesdropping Attack.
From www.slideteam.net
Eavesdropping Attack Cybersecurity Monotone Icon In Powerpoint Pptx Png And Editable Eps Format Discuss Briefly Eavesdropping Attack Attackers often begin by identifying. an eavesdropping attack, also known as a wiretapping or listening attack, is a popular cyber attack in networking. eavesdropping attacks, also known as snooping or sniffing attacks, are where malicious actors exploit networks, systems, or devices to stealthily listen in on and capture data. eavesdropping attacks happen when cyber criminals or attackers. Discuss Briefly Eavesdropping Attack.
From www.shiksha.com
What Is Eavesdropping How To Prevent It? Shiksha Online Discuss Briefly Eavesdropping Attack an eavesdropping attack, also known as a wiretapping or listening attack, is a popular cyber attack in networking. In this attack, an attacker. Attackers often begin by identifying. eavesdropping attacks, also known as snooping or sniffing attacks, are where malicious actors exploit networks, systems, or devices to stealthily listen in on and capture data. eavesdropping attacks happen. Discuss Briefly Eavesdropping Attack.
From captex.bank
Eavesdropping Attack » CapTex Bank Discuss Briefly Eavesdropping Attack Attackers often begin by identifying. In this attack, an attacker. in cybersecurity, an eavesdropping attack is a malicious attempt to intercept and access data transmitted over a network without. eavesdropping is a form of cyberattack that enables hackers to intercept, delete, or modify data that is transmitted between devices. eavesdropping attacks, also known as snooping or sniffing. Discuss Briefly Eavesdropping Attack.
From binfintech.com
Eavesdropping Attack and How to Prevent it in Ethical Hacking Discuss Briefly Eavesdropping Attack eavesdropping is a form of cyberattack that enables hackers to intercept, delete, or modify data that is transmitted between devices. In this attack, an attacker. eavesdropping attacks, also known as snooping or sniffing attacks, are where malicious actors exploit networks, systems, or devices to stealthily listen in on and capture data. in cybersecurity, an eavesdropping attack is. Discuss Briefly Eavesdropping Attack.
From www.slideteam.net
Eavesdropping Attack Cybersecurity Colored Icon In Powerpoint Pptx Png And Editable Eps Format Discuss Briefly Eavesdropping Attack eavesdropping attacks operate by exploiting vulnerabilities in network communications. an eavesdropping attack, also known as a wiretapping or listening attack, is a popular cyber attack in networking. eavesdropping attacks, also known as snooping or sniffing attacks, are where malicious actors exploit networks, systems, or devices to stealthily listen in on and capture data. eavesdropping attacks happen. Discuss Briefly Eavesdropping Attack.
From www.youtube.com
eavesdropping attack in network security YouTube Discuss Briefly Eavesdropping Attack eavesdropping is a form of cyberattack that enables hackers to intercept, delete, or modify data that is transmitted between devices. In this attack, an attacker. network eavesdropping, also known as eavesdropping attack, sniffing attack, or snooping attack, is a method that. eavesdropping attacks, also known as snooping or sniffing attacks, are where malicious actors exploit networks, systems,. Discuss Briefly Eavesdropping Attack.
From www.wallarm.com
What is Eavesdropping Attack and How to prevent it? Discuss Briefly Eavesdropping Attack an eavesdropping attack, also known as a wiretapping or listening attack, is a popular cyber attack in networking. in cybersecurity, an eavesdropping attack is a malicious attempt to intercept and access data transmitted over a network without. eavesdropping attacks happen when cyber criminals or attackers listen in to network traffic traveling over computers,. eavesdropping attacks operate. Discuss Briefly Eavesdropping Attack.
From www.researchgate.net
5 Eavesdropping attack. Download Scientific Diagram Discuss Briefly Eavesdropping Attack eavesdropping attacks happen when cyber criminals or attackers listen in to network traffic traveling over computers,. network eavesdropping, also known as eavesdropping attack, sniffing attack, or snooping attack, is a method that. eavesdropping attacks operate by exploiting vulnerabilities in network communications. eavesdropping attacks, also known as snooping or sniffing attacks, are where malicious actors exploit networks,. Discuss Briefly Eavesdropping Attack.
From exormwuvj.blob.core.windows.net
What Is The Objective Of A Network Eavesdropping Attack at Judith Belue blog Discuss Briefly Eavesdropping Attack an eavesdropping attack, also known as a wiretapping or listening attack, is a popular cyber attack in networking. eavesdropping attacks operate by exploiting vulnerabilities in network communications. network eavesdropping, also known as eavesdropping attack, sniffing attack, or snooping attack, is a method that. In this attack, an attacker. eavesdropping attacks happen when cyber criminals or attackers. Discuss Briefly Eavesdropping Attack.
From www.youtube.com
What Is an Eavesdropping Attack? YouTube Discuss Briefly Eavesdropping Attack an eavesdropping attack, also known as a wiretapping or listening attack, is a popular cyber attack in networking. Attackers often begin by identifying. eavesdropping attacks happen when cyber criminals or attackers listen in to network traffic traveling over computers,. In this attack, an attacker. eavesdropping is a form of cyberattack that enables hackers to intercept, delete, or. Discuss Briefly Eavesdropping Attack.
From www.asdf.id
Eavesdropping Attack Arti, Cara Kerja, Cara Mendeteksi Discuss Briefly Eavesdropping Attack in cybersecurity, an eavesdropping attack is a malicious attempt to intercept and access data transmitted over a network without. Attackers often begin by identifying. eavesdropping attacks, also known as snooping or sniffing attacks, are where malicious actors exploit networks, systems, or devices to stealthily listen in on and capture data. eavesdropping attacks happen when cyber criminals or. Discuss Briefly Eavesdropping Attack.
From www.youtube.com
What is an Eavesdropping Attack Part One YouTube Discuss Briefly Eavesdropping Attack eavesdropping attacks happen when cyber criminals or attackers listen in to network traffic traveling over computers,. in cybersecurity, an eavesdropping attack is a malicious attempt to intercept and access data transmitted over a network without. eavesdropping attacks operate by exploiting vulnerabilities in network communications. eavesdropping attacks, also known as snooping or sniffing attacks, are where malicious. Discuss Briefly Eavesdropping Attack.
From www.researchgate.net
Eavesdropping, message alteration, and spoofing attacks Download Scientific Diagram Discuss Briefly Eavesdropping Attack eavesdropping attacks operate by exploiting vulnerabilities in network communications. eavesdropping attacks, also known as snooping or sniffing attacks, are where malicious actors exploit networks, systems, or devices to stealthily listen in on and capture data. eavesdropping is a form of cyberattack that enables hackers to intercept, delete, or modify data that is transmitted between devices. in. Discuss Briefly Eavesdropping Attack.
From limevpn.com
Top 10 Most Common Types of Hacking Attacks LimeVPN Discuss Briefly Eavesdropping Attack an eavesdropping attack, also known as a wiretapping or listening attack, is a popular cyber attack in networking. eavesdropping attacks operate by exploiting vulnerabilities in network communications. in cybersecurity, an eavesdropping attack is a malicious attempt to intercept and access data transmitted over a network without. eavesdropping is a form of cyberattack that enables hackers to. Discuss Briefly Eavesdropping Attack.
From www.efani.com
Eavesdropping Attack What Is It, Types, Its Impact, and Prevention Tips Discuss Briefly Eavesdropping Attack an eavesdropping attack, also known as a wiretapping or listening attack, is a popular cyber attack in networking. Attackers often begin by identifying. eavesdropping is a form of cyberattack that enables hackers to intercept, delete, or modify data that is transmitted between devices. In this attack, an attacker. network eavesdropping, also known as eavesdropping attack, sniffing attack,. Discuss Briefly Eavesdropping Attack.
From techyvow.com
Eavesdropping AttackEverything You Need to Know Discuss Briefly Eavesdropping Attack an eavesdropping attack, also known as a wiretapping or listening attack, is a popular cyber attack in networking. eavesdropping is a form of cyberattack that enables hackers to intercept, delete, or modify data that is transmitted between devices. eavesdropping attacks operate by exploiting vulnerabilities in network communications. network eavesdropping, also known as eavesdropping attack, sniffing attack,. Discuss Briefly Eavesdropping Attack.
From www.baeldung.com
What Is an Eavesdropping Attack? Baeldung on Computer Science Discuss Briefly Eavesdropping Attack eavesdropping attacks operate by exploiting vulnerabilities in network communications. In this attack, an attacker. Attackers often begin by identifying. eavesdropping attacks, also known as snooping or sniffing attacks, are where malicious actors exploit networks, systems, or devices to stealthily listen in on and capture data. in cybersecurity, an eavesdropping attack is a malicious attempt to intercept and. Discuss Briefly Eavesdropping Attack.
From www.sangfor.com
What Is Eavesdropping Attack How Does it Work Sangfor Discuss Briefly Eavesdropping Attack In this attack, an attacker. network eavesdropping, also known as eavesdropping attack, sniffing attack, or snooping attack, is a method that. eavesdropping attacks happen when cyber criminals or attackers listen in to network traffic traveling over computers,. in cybersecurity, an eavesdropping attack is a malicious attempt to intercept and access data transmitted over a network without. . Discuss Briefly Eavesdropping Attack.
From www.efani.com
Eavesdropping Attack Everything You Should Know Discuss Briefly Eavesdropping Attack eavesdropping attacks, also known as snooping or sniffing attacks, are where malicious actors exploit networks, systems, or devices to stealthily listen in on and capture data. network eavesdropping, also known as eavesdropping attack, sniffing attack, or snooping attack, is a method that. eavesdropping attacks operate by exploiting vulnerabilities in network communications. an eavesdropping attack, also known. Discuss Briefly Eavesdropping Attack.
From www.researchgate.net
A simple eavesdropping attack behavior, where he tries to listen to the... Download Scientific Discuss Briefly Eavesdropping Attack Attackers often begin by identifying. In this attack, an attacker. eavesdropping attacks operate by exploiting vulnerabilities in network communications. eavesdropping attacks happen when cyber criminals or attackers listen in to network traffic traveling over computers,. eavesdropping is a form of cyberattack that enables hackers to intercept, delete, or modify data that is transmitted between devices. in. Discuss Briefly Eavesdropping Attack.
From www.asdf.id
Eavesdropping Attack Arti, Cara Kerja, Cara Mendeteksi Discuss Briefly Eavesdropping Attack an eavesdropping attack, also known as a wiretapping or listening attack, is a popular cyber attack in networking. eavesdropping attacks, also known as snooping or sniffing attacks, are where malicious actors exploit networks, systems, or devices to stealthily listen in on and capture data. eavesdropping attacks happen when cyber criminals or attackers listen in to network traffic. Discuss Briefly Eavesdropping Attack.
From www.youtube.com
what is eavesdropping? explain in full detail eavesdropping network attack 2017 YouTube Discuss Briefly Eavesdropping Attack In this attack, an attacker. network eavesdropping, also known as eavesdropping attack, sniffing attack, or snooping attack, is a method that. an eavesdropping attack, also known as a wiretapping or listening attack, is a popular cyber attack in networking. eavesdropping attacks, also known as snooping or sniffing attacks, are where malicious actors exploit networks, systems, or devices. Discuss Briefly Eavesdropping Attack.
From www.baeldung.com
What Is an Eavesdropping Attack? Baeldung on Computer Science Discuss Briefly Eavesdropping Attack eavesdropping attacks, also known as snooping or sniffing attacks, are where malicious actors exploit networks, systems, or devices to stealthily listen in on and capture data. an eavesdropping attack, also known as a wiretapping or listening attack, is a popular cyber attack in networking. eavesdropping attacks happen when cyber criminals or attackers listen in to network traffic. Discuss Briefly Eavesdropping Attack.
From www.slideserve.com
PPT Eavesdropping Attack Network Projects Research Ideas PowerPoint Presentation ID10837889 Discuss Briefly Eavesdropping Attack eavesdropping is a form of cyberattack that enables hackers to intercept, delete, or modify data that is transmitted between devices. eavesdropping attacks happen when cyber criminals or attackers listen in to network traffic traveling over computers,. in cybersecurity, an eavesdropping attack is a malicious attempt to intercept and access data transmitted over a network without. eavesdropping. Discuss Briefly Eavesdropping Attack.
From www.techslang.com
What is an Eavesdropping Attack? — Definition by Techslang Discuss Briefly Eavesdropping Attack in cybersecurity, an eavesdropping attack is a malicious attempt to intercept and access data transmitted over a network without. eavesdropping attacks happen when cyber criminals or attackers listen in to network traffic traveling over computers,. network eavesdropping, also known as eavesdropping attack, sniffing attack, or snooping attack, is a method that. eavesdropping attacks, also known as. Discuss Briefly Eavesdropping Attack.
From www.vrogue.co
Eavesdropping Attack vrogue.co Discuss Briefly Eavesdropping Attack in cybersecurity, an eavesdropping attack is a malicious attempt to intercept and access data transmitted over a network without. eavesdropping attacks operate by exploiting vulnerabilities in network communications. Attackers often begin by identifying. eavesdropping is a form of cyberattack that enables hackers to intercept, delete, or modify data that is transmitted between devices. eavesdropping attacks, also. Discuss Briefly Eavesdropping Attack.
From www.researchgate.net
Eavesdropping attack. Download Scientific Diagram Discuss Briefly Eavesdropping Attack an eavesdropping attack, also known as a wiretapping or listening attack, is a popular cyber attack in networking. In this attack, an attacker. eavesdropping attacks happen when cyber criminals or attackers listen in to network traffic traveling over computers,. Attackers often begin by identifying. eavesdropping attacks, also known as snooping or sniffing attacks, are where malicious actors. Discuss Briefly Eavesdropping Attack.