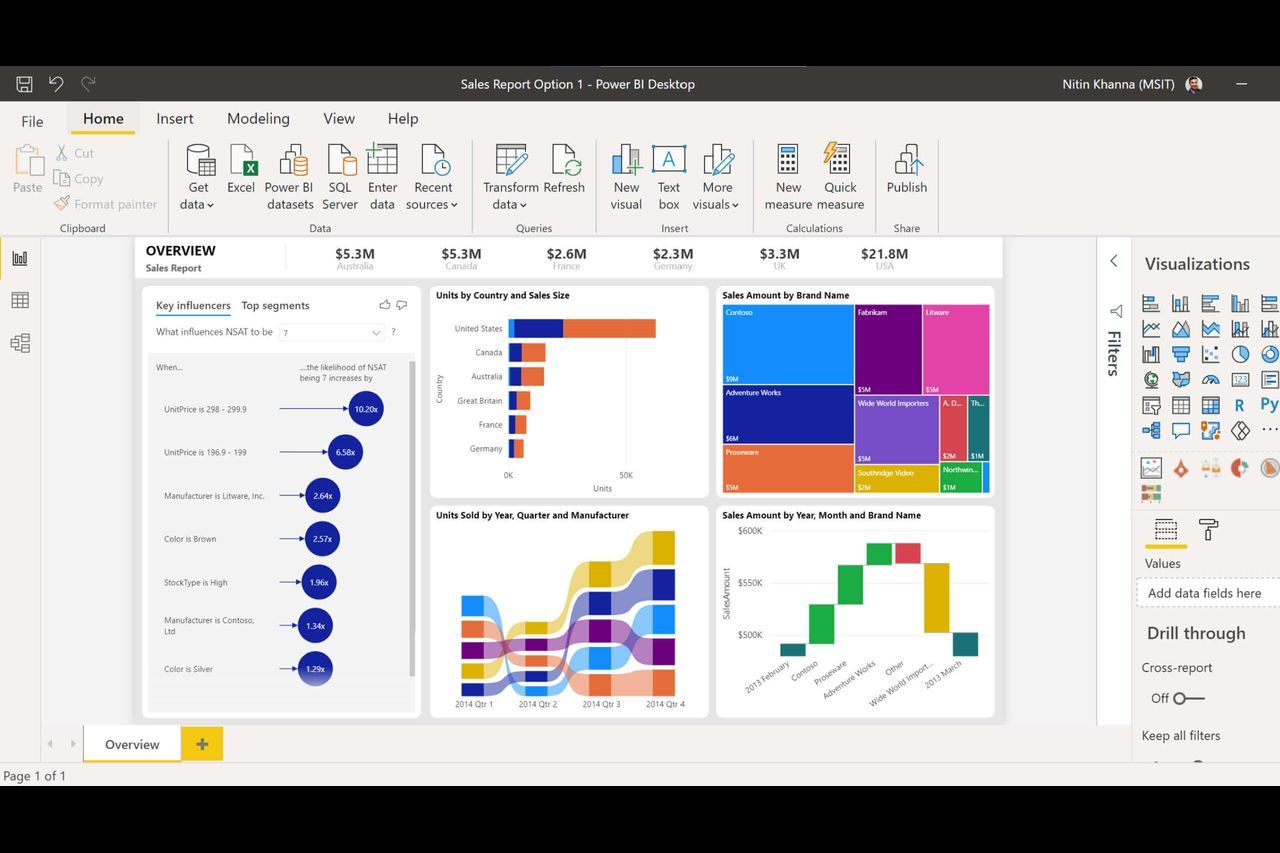
Power Bi Security White Paper . This paper introduces the security model for tabular bi semantic and power bi. Foster a culture of security. While the power bi security white paper focuses on key technical topics such as authentication, data residency, and network isolation, the primary goal of the series is to provide. The power bi security white paper focuses on key technical subjects such as authentication, data residency, and network isolation. This paper introduces the security model for tabular bi semantic and power bi. This paper introduces the security model for tabular bi semantic and power bi. As detailed in a new microsoft power bi security whitepaper, our point of view is that data security should no longer be about bi. You will learn how to create roles, implement dynamic. Work confidently from anywhere and. You will learn how to create roles, implement. Read the power bi security white paper. You will learn how to create roles, implement dynamic.
from www.ilink-digital.com
You will learn how to create roles, implement dynamic. While the power bi security white paper focuses on key technical topics such as authentication, data residency, and network isolation, the primary goal of the series is to provide. This paper introduces the security model for tabular bi semantic and power bi. As detailed in a new microsoft power bi security whitepaper, our point of view is that data security should no longer be about bi. You will learn how to create roles, implement. The power bi security white paper focuses on key technical subjects such as authentication, data residency, and network isolation. Read the power bi security white paper. Work confidently from anywhere and. You will learn how to create roles, implement dynamic. This paper introduces the security model for tabular bi semantic and power bi.
Microsoft Power BI Security 6 Best Practices iLink Digital
Power Bi Security White Paper Work confidently from anywhere and. This paper introduces the security model for tabular bi semantic and power bi. This paper introduces the security model for tabular bi semantic and power bi. The power bi security white paper focuses on key technical subjects such as authentication, data residency, and network isolation. Foster a culture of security. You will learn how to create roles, implement dynamic. You will learn how to create roles, implement. You will learn how to create roles, implement dynamic. Work confidently from anywhere and. As detailed in a new microsoft power bi security whitepaper, our point of view is that data security should no longer be about bi. This paper introduces the security model for tabular bi semantic and power bi. While the power bi security white paper focuses on key technical topics such as authentication, data residency, and network isolation, the primary goal of the series is to provide. Read the power bi security white paper.
From www.liongard.com
Create ataglance security dashboards with Power BI Liongard Power Bi Security White Paper While the power bi security white paper focuses on key technical topics such as authentication, data residency, and network isolation, the primary goal of the series is to provide. You will learn how to create roles, implement dynamic. As detailed in a new microsoft power bi security whitepaper, our point of view is that data security should no longer be. Power Bi Security White Paper.
From www.youtube.com
Power BI Security Best Practices YouTube Power Bi Security White Paper You will learn how to create roles, implement. This paper introduces the security model for tabular bi semantic and power bi. You will learn how to create roles, implement dynamic. While the power bi security white paper focuses on key technical topics such as authentication, data residency, and network isolation, the primary goal of the series is to provide. Foster. Power Bi Security White Paper.
From www.loginworks.com
How to implement RLS security with Filters in Power BI? Power Bi Security White Paper The power bi security white paper focuses on key technical subjects such as authentication, data residency, and network isolation. This paper introduces the security model for tabular bi semantic and power bi. This paper introduces the security model for tabular bi semantic and power bi. Foster a culture of security. This paper introduces the security model for tabular bi semantic. Power Bi Security White Paper.
From www.scribd.com
Power BI Security Whitepaper PDF Microsoft Azure Mobile App Power Bi Security White Paper The power bi security white paper focuses on key technical subjects such as authentication, data residency, and network isolation. This paper introduces the security model for tabular bi semantic and power bi. You will learn how to create roles, implement. This paper introduces the security model for tabular bi semantic and power bi. Read the power bi security white paper.. Power Bi Security White Paper.
From k21academy.com
Data Security in Power BI How to Implement and Configure Power Bi Security White Paper This paper introduces the security model for tabular bi semantic and power bi. You will learn how to create roles, implement dynamic. The power bi security white paper focuses on key technical subjects such as authentication, data residency, and network isolation. You will learn how to create roles, implement. You will learn how to create roles, implement dynamic. While the. Power Bi Security White Paper.
From www.sqlcircuit.com
SQLCircuit Power BI Security Model Power Bi Security White Paper This paper introduces the security model for tabular bi semantic and power bi. Foster a culture of security. Read the power bi security white paper. The power bi security white paper focuses on key technical subjects such as authentication, data residency, and network isolation. This paper introduces the security model for tabular bi semantic and power bi. This paper introduces. Power Bi Security White Paper.
From www.journeyteam.com
9 Power BI Security Best Practices Power Bi Security White Paper While the power bi security white paper focuses on key technical topics such as authentication, data residency, and network isolation, the primary goal of the series is to provide. You will learn how to create roles, implement dynamic. Read the power bi security white paper. As detailed in a new microsoft power bi security whitepaper, our point of view is. Power Bi Security White Paper.
From www.ilink-digital.com
Microsoft Power BI Security 6 Best Practices iLink Digital Power Bi Security White Paper This paper introduces the security model for tabular bi semantic and power bi. The power bi security white paper focuses on key technical subjects such as authentication, data residency, and network isolation. You will learn how to create roles, implement. Read the power bi security white paper. Foster a culture of security. You will learn how to create roles, implement. Power Bi Security White Paper.
From www.pk-anexcelexpert.com
Static and Dynamic Row Level Security in Power BI PK An Excel Expert Power Bi Security White Paper This paper introduces the security model for tabular bi semantic and power bi. As detailed in a new microsoft power bi security whitepaper, our point of view is that data security should no longer be about bi. You will learn how to create roles, implement dynamic. While the power bi security white paper focuses on key technical topics such as. Power Bi Security White Paper.
From www.linkedin.com
The Solution Consulting FZCO on LinkedIn Power BI security white paper Power BI Power Bi Security White Paper This paper introduces the security model for tabular bi semantic and power bi. Read the power bi security white paper. Foster a culture of security. Work confidently from anywhere and. You will learn how to create roles, implement. As detailed in a new microsoft power bi security whitepaper, our point of view is that data security should no longer be. Power Bi Security White Paper.
From learn.microsoft.com
Power BI security white paper Power BI Microsoft Learn Power Bi Security White Paper Work confidently from anywhere and. You will learn how to create roles, implement. You will learn how to create roles, implement dynamic. This paper introduces the security model for tabular bi semantic and power bi. The power bi security white paper focuses on key technical subjects such as authentication, data residency, and network isolation. While the power bi security white. Power Bi Security White Paper.
From docs.microsoft.com
Power BI security whitepaper Power BI Microsoft Docs Power Bi Security White Paper Read the power bi security white paper. Foster a culture of security. This paper introduces the security model for tabular bi semantic and power bi. You will learn how to create roles, implement. Work confidently from anywhere and. This paper introduces the security model for tabular bi semantic and power bi. You will learn how to create roles, implement dynamic.. Power Bi Security White Paper.
From docs.microsoft.com
Power BI security whitepaper Power BI Microsoft Docs Power Bi Security White Paper This paper introduces the security model for tabular bi semantic and power bi. Read the power bi security white paper. Foster a culture of security. While the power bi security white paper focuses on key technical topics such as authentication, data residency, and network isolation, the primary goal of the series is to provide. You will learn how to create. Power Bi Security White Paper.
From learn.microsoft.com
Power BI security white paper Power BI Microsoft Learn Power Bi Security White Paper This paper introduces the security model for tabular bi semantic and power bi. As detailed in a new microsoft power bi security whitepaper, our point of view is that data security should no longer be about bi. Foster a culture of security. The power bi security white paper focuses on key technical subjects such as authentication, data residency, and network. Power Bi Security White Paper.
From learn.microsoft.com
Power BI security white paper Power BI Microsoft Learn Power Bi Security White Paper This paper introduces the security model for tabular bi semantic and power bi. You will learn how to create roles, implement dynamic. While the power bi security white paper focuses on key technical topics such as authentication, data residency, and network isolation, the primary goal of the series is to provide. This paper introduces the security model for tabular bi. Power Bi Security White Paper.
From skypoint.ai
How Do We Improve Power BI Security? Skypoint Power Bi Security White Paper Foster a culture of security. This paper introduces the security model for tabular bi semantic and power bi. You will learn how to create roles, implement dynamic. While the power bi security white paper focuses on key technical topics such as authentication, data residency, and network isolation, the primary goal of the series is to provide. This paper introduces the. Power Bi Security White Paper.
From slideplayer.com
Enterprise BI Deployments and Governance with Power BI ppt download Power Bi Security White Paper This paper introduces the security model for tabular bi semantic and power bi. As detailed in a new microsoft power bi security whitepaper, our point of view is that data security should no longer be about bi. The power bi security white paper focuses on key technical subjects such as authentication, data residency, and network isolation. Read the power bi. Power Bi Security White Paper.
From www.vrogue.co
Data Security In Power Bi How To Implement And Configure Vrogue Power Bi Security White Paper The power bi security white paper focuses on key technical subjects such as authentication, data residency, and network isolation. You will learn how to create roles, implement. This paper introduces the security model for tabular bi semantic and power bi. While the power bi security white paper focuses on key technical topics such as authentication, data residency, and network isolation,. Power Bi Security White Paper.
From skypointcloud.com
How Do We Improve Power BI Security? SkyPoint Cloud Power Bi Security White Paper While the power bi security white paper focuses on key technical topics such as authentication, data residency, and network isolation, the primary goal of the series is to provide. Work confidently from anywhere and. This paper introduces the security model for tabular bi semantic and power bi. The power bi security white paper focuses on key technical subjects such as. Power Bi Security White Paper.
From www.vrogue.co
Dynamic Row Level Security With Power Bi Made Simple vrogue.co Power Bi Security White Paper Foster a culture of security. Work confidently from anywhere and. This paper introduces the security model for tabular bi semantic and power bi. As detailed in a new microsoft power bi security whitepaper, our point of view is that data security should no longer be about bi. You will learn how to create roles, implement dynamic. This paper introduces the. Power Bi Security White Paper.
From slideplayer.com
Power BI Part 2 Internals ppt download Power Bi Security White Paper This paper introduces the security model for tabular bi semantic and power bi. You will learn how to create roles, implement dynamic. This paper introduces the security model for tabular bi semantic and power bi. You will learn how to create roles, implement. Foster a culture of security. Work confidently from anywhere and. As detailed in a new microsoft power. Power Bi Security White Paper.
From www.liongard.com
Create ataglance security dashboards with Power BI Liongard Power Bi Security White Paper While the power bi security white paper focuses on key technical topics such as authentication, data residency, and network isolation, the primary goal of the series is to provide. The power bi security white paper focuses on key technical subjects such as authentication, data residency, and network isolation. This paper introduces the security model for tabular bi semantic and power. Power Bi Security White Paper.
From www.scribd.com
Power BI Security Whitepaper December 2017 PDF Microsoft Azure Encryption Power Bi Security White Paper While the power bi security white paper focuses on key technical topics such as authentication, data residency, and network isolation, the primary goal of the series is to provide. This paper introduces the security model for tabular bi semantic and power bi. As detailed in a new microsoft power bi security whitepaper, our point of view is that data security. Power Bi Security White Paper.
From learn.microsoft.com
Power BI security white paper Power BI Microsoft Learn Power Bi Security White Paper You will learn how to create roles, implement dynamic. The power bi security white paper focuses on key technical subjects such as authentication, data residency, and network isolation. This paper introduces the security model for tabular bi semantic and power bi. Foster a culture of security. You will learn how to create roles, implement. This paper introduces the security model. Power Bi Security White Paper.
From www.youtube.com
Security in Power BI Quick Overview YouTube Power Bi Security White Paper Read the power bi security white paper. You will learn how to create roles, implement dynamic. You will learn how to create roles, implement dynamic. You will learn how to create roles, implement. This paper introduces the security model for tabular bi semantic and power bi. As detailed in a new microsoft power bi security whitepaper, our point of view. Power Bi Security White Paper.
From www.dtonomy.com
Create Power BI Reporting for CrowdStrike AIDriven Security Operations Power Bi Security White Paper You will learn how to create roles, implement dynamic. Work confidently from anywhere and. This paper introduces the security model for tabular bi semantic and power bi. This paper introduces the security model for tabular bi semantic and power bi. You will learn how to create roles, implement dynamic. As detailed in a new microsoft power bi security whitepaper, our. Power Bi Security White Paper.
From hotzxgirl.com
Power Bi Security Whitepaper Power Bi Microsoft Docs 14612 Hot Sex Picture Power Bi Security White Paper You will learn how to create roles, implement. Foster a culture of security. While the power bi security white paper focuses on key technical topics such as authentication, data residency, and network isolation, the primary goal of the series is to provide. The power bi security white paper focuses on key technical subjects such as authentication, data residency, and network. Power Bi Security White Paper.
From hxexgisex.blob.core.windows.net
Power Bi Security Groups at Connie Roberts blog Power Bi Security White Paper You will learn how to create roles, implement dynamic. Read the power bi security white paper. As detailed in a new microsoft power bi security whitepaper, our point of view is that data security should no longer be about bi. The power bi security white paper focuses on key technical subjects such as authentication, data residency, and network isolation. This. Power Bi Security White Paper.
From k21academy.com
Data Security in Power BI How to Implement and Configure Power Bi Security White Paper The power bi security white paper focuses on key technical subjects such as authentication, data residency, and network isolation. Foster a culture of security. You will learn how to create roles, implement. As detailed in a new microsoft power bi security whitepaper, our point of view is that data security should no longer be about bi. This paper introduces the. Power Bi Security White Paper.
From bridgeall.com
Power BI whitepaper Archives Bridgeall Power Bi Security White Paper You will learn how to create roles, implement dynamic. This paper introduces the security model for tabular bi semantic and power bi. This paper introduces the security model for tabular bi semantic and power bi. Work confidently from anywhere and. You will learn how to create roles, implement dynamic. You will learn how to create roles, implement. Foster a culture. Power Bi Security White Paper.
From hxexgisex.blob.core.windows.net
Power Bi Security Groups at Connie Roberts blog Power Bi Security White Paper As detailed in a new microsoft power bi security whitepaper, our point of view is that data security should no longer be about bi. Read the power bi security white paper. You will learn how to create roles, implement. The power bi security white paper focuses on key technical subjects such as authentication, data residency, and network isolation. While the. Power Bi Security White Paper.
From data-flair.training
Power BI Security What is Dynamic RowLevel Security DataFlair Power Bi Security White Paper You will learn how to create roles, implement dynamic. This paper introduces the security model for tabular bi semantic and power bi. You will learn how to create roles, implement dynamic. You will learn how to create roles, implement. This paper introduces the security model for tabular bi semantic and power bi. The power bi security white paper focuses on. Power Bi Security White Paper.
From www.excelmojo.com
Power BI Security How to Create RowLevel Security? Power Bi Security White Paper This paper introduces the security model for tabular bi semantic and power bi. This paper introduces the security model for tabular bi semantic and power bi. As detailed in a new microsoft power bi security whitepaper, our point of view is that data security should no longer be about bi. This paper introduces the security model for tabular bi semantic. Power Bi Security White Paper.
From skypoint.ai
How Do We Improve Power BI Security? Skypoint Power Bi Security White Paper This paper introduces the security model for tabular bi semantic and power bi. As detailed in a new microsoft power bi security whitepaper, our point of view is that data security should no longer be about bi. Read the power bi security white paper. Work confidently from anywhere and. You will learn how to create roles, implement dynamic. Foster a. Power Bi Security White Paper.
From www.hotzxgirl.com
Power Bi Security Whitepaper Power Bi Microsoft Docs Hot Sex Picture Power Bi Security White Paper While the power bi security white paper focuses on key technical topics such as authentication, data residency, and network isolation, the primary goal of the series is to provide. You will learn how to create roles, implement dynamic. This paper introduces the security model for tabular bi semantic and power bi. This paper introduces the security model for tabular bi. Power Bi Security White Paper.