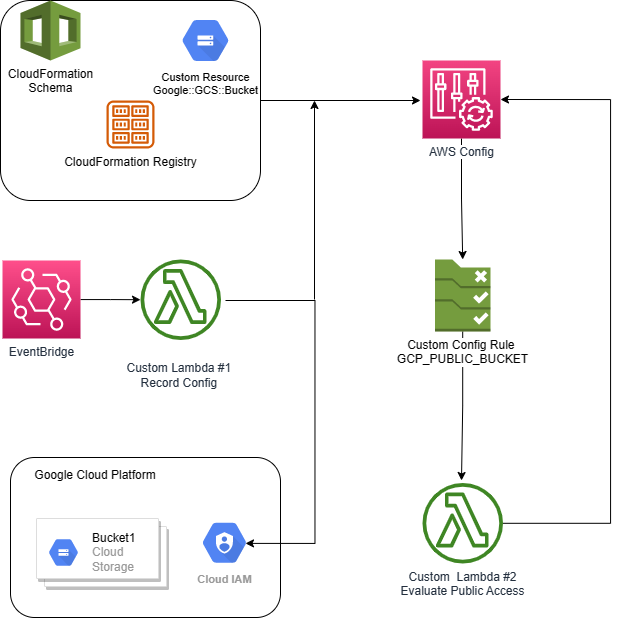
Google Storage Bucket Vulnerability . This script (optionally) accepts gcp user/service account credentials and a keyword. Learn how to set up appropriate access controls so you can locate sensitive data. Threat actors continued targeting unprotected public cloud. Taking charge of your security. A script to enumerate google storage buckets, determine what access you have to them, and determine if they can be privilege escalated. This article covers both google cloud and cloud service provider agnostic threats. A new tool is helping security researchers discover misconfigured google data storage, as more and more businesses move their. 4 steps for hardening your cloud storage buckets:
from vivek-aws.medium.com
This article covers both google cloud and cloud service provider agnostic threats. Threat actors continued targeting unprotected public cloud. A script to enumerate google storage buckets, determine what access you have to them, and determine if they can be privilege escalated. 4 steps for hardening your cloud storage buckets: This script (optionally) accepts gcp user/service account credentials and a keyword. A new tool is helping security researchers discover misconfigured google data storage, as more and more businesses move their. Taking charge of your security. Learn how to set up appropriate access controls so you can locate sensitive data.
Unveiling the Hidden Risks How to Track and Secure Any Publicly
Google Storage Bucket Vulnerability This article covers both google cloud and cloud service provider agnostic threats. Learn how to set up appropriate access controls so you can locate sensitive data. Taking charge of your security. 4 steps for hardening your cloud storage buckets: This script (optionally) accepts gcp user/service account credentials and a keyword. This article covers both google cloud and cloud service provider agnostic threats. Threat actors continued targeting unprotected public cloud. A script to enumerate google storage buckets, determine what access you have to them, and determine if they can be privilege escalated. A new tool is helping security researchers discover misconfigured google data storage, as more and more businesses move their.
From www.youtube.com
How to Set Buckets and Files Public In Google Cloud Storage YouTube Google Storage Bucket Vulnerability A script to enumerate google storage buckets, determine what access you have to them, and determine if they can be privilege escalated. Threat actors continued targeting unprotected public cloud. This script (optionally) accepts gcp user/service account credentials and a keyword. Taking charge of your security. A new tool is helping security researchers discover misconfigured google data storage, as more and. Google Storage Bucket Vulnerability.
From www.youtube.com
Backing up with Rclone to Google Storage Bucket YouTube Google Storage Bucket Vulnerability A new tool is helping security researchers discover misconfigured google data storage, as more and more businesses move their. Learn how to set up appropriate access controls so you can locate sensitive data. 4 steps for hardening your cloud storage buckets: This script (optionally) accepts gcp user/service account credentials and a keyword. Taking charge of your security. Threat actors continued. Google Storage Bucket Vulnerability.
From xebia.com
Encryption at rest with Google storage buckets Xebia Google Storage Bucket Vulnerability Taking charge of your security. Threat actors continued targeting unprotected public cloud. A new tool is helping security researchers discover misconfigured google data storage, as more and more businesses move their. A script to enumerate google storage buckets, determine what access you have to them, and determine if they can be privilege escalated. This article covers both google cloud and. Google Storage Bucket Vulnerability.
From cloud.google.com
Quickstart Discover object storage with the Google Cloud console Google Storage Bucket Vulnerability Threat actors continued targeting unprotected public cloud. Taking charge of your security. This article covers both google cloud and cloud service provider agnostic threats. A script to enumerate google storage buckets, determine what access you have to them, and determine if they can be privilege escalated. Learn how to set up appropriate access controls so you can locate sensitive data.. Google Storage Bucket Vulnerability.
From www.comparitech.com
6 of all Google Cloud Buckets are vulnerable to unauthorized access Google Storage Bucket Vulnerability This article covers both google cloud and cloud service provider agnostic threats. Threat actors continued targeting unprotected public cloud. 4 steps for hardening your cloud storage buckets: Learn how to set up appropriate access controls so you can locate sensitive data. This script (optionally) accepts gcp user/service account credentials and a keyword. A script to enumerate google storage buckets, determine. Google Storage Bucket Vulnerability.
From ip-slip.com
IP SLIP MAKE GOOGLE STORAGE BUCKETS PRIVATE Google Storage Bucket Vulnerability Threat actors continued targeting unprotected public cloud. 4 steps for hardening your cloud storage buckets: A new tool is helping security researchers discover misconfigured google data storage, as more and more businesses move their. This article covers both google cloud and cloud service provider agnostic threats. A script to enumerate google storage buckets, determine what access you have to them,. Google Storage Bucket Vulnerability.
From github.com
Support for encryption · Issue 5 · osinfraio/terraformgooglestorage Google Storage Bucket Vulnerability This script (optionally) accepts gcp user/service account credentials and a keyword. A new tool is helping security researchers discover misconfigured google data storage, as more and more businesses move their. 4 steps for hardening your cloud storage buckets: A script to enumerate google storage buckets, determine what access you have to them, and determine if they can be privilege escalated.. Google Storage Bucket Vulnerability.
From www.bytescale.com
Google Storage Documentation Google Storage Bucket Vulnerability Taking charge of your security. 4 steps for hardening your cloud storage buckets: A new tool is helping security researchers discover misconfigured google data storage, as more and more businesses move their. A script to enumerate google storage buckets, determine what access you have to them, and determine if they can be privilege escalated. This script (optionally) accepts gcp user/service. Google Storage Bucket Vulnerability.
From securityonline.info
GCPBucketBrute enumerate Google Storage buckets Google Storage Bucket Vulnerability Learn how to set up appropriate access controls so you can locate sensitive data. 4 steps for hardening your cloud storage buckets: Taking charge of your security. This script (optionally) accepts gcp user/service account credentials and a keyword. A new tool is helping security researchers discover misconfigured google data storage, as more and more businesses move their. This article covers. Google Storage Bucket Vulnerability.
From blog.securelayer7.net
Handson Amazon S3 Bucket Vulnerabilities and learn exploiting them Google Storage Bucket Vulnerability This script (optionally) accepts gcp user/service account credentials and a keyword. A script to enumerate google storage buckets, determine what access you have to them, and determine if they can be privilege escalated. Threat actors continued targeting unprotected public cloud. 4 steps for hardening your cloud storage buckets: Taking charge of your security. This article covers both google cloud and. Google Storage Bucket Vulnerability.
From aws.amazon.com
Migrating Google Cloud Storage to Amazon S3 using AWS DataSync AWS Google Storage Bucket Vulnerability Taking charge of your security. Threat actors continued targeting unprotected public cloud. 4 steps for hardening your cloud storage buckets: A script to enumerate google storage buckets, determine what access you have to them, and determine if they can be privilege escalated. This article covers both google cloud and cloud service provider agnostic threats. This script (optionally) accepts gcp user/service. Google Storage Bucket Vulnerability.
From medium.com
Create a Google Cloud Storage Bucket(GCSBucket) by Prayag Sangode Google Storage Bucket Vulnerability This script (optionally) accepts gcp user/service account credentials and a keyword. Taking charge of your security. This article covers both google cloud and cloud service provider agnostic threats. Learn how to set up appropriate access controls so you can locate sensitive data. A script to enumerate google storage buckets, determine what access you have to them, and determine if they. Google Storage Bucket Vulnerability.
From ip-slip.com
IP SLIP MAKE GOOGLE STORAGE BUCKETS PRIVATE Google Storage Bucket Vulnerability 4 steps for hardening your cloud storage buckets: Threat actors continued targeting unprotected public cloud. This script (optionally) accepts gcp user/service account credentials and a keyword. A script to enumerate google storage buckets, determine what access you have to them, and determine if they can be privilege escalated. Learn how to set up appropriate access controls so you can locate. Google Storage Bucket Vulnerability.
From cerpsbcu.blob.core.windows.net
Google Storage Bucket Python at Richard Garner blog Google Storage Bucket Vulnerability This article covers both google cloud and cloud service provider agnostic threats. Threat actors continued targeting unprotected public cloud. Taking charge of your security. A new tool is helping security researchers discover misconfigured google data storage, as more and more businesses move their. A script to enumerate google storage buckets, determine what access you have to them, and determine if. Google Storage Bucket Vulnerability.
From www.youtube.com
Cloud Storage in Google Cloud Platform How to create bucket and Google Storage Bucket Vulnerability A script to enumerate google storage buckets, determine what access you have to them, and determine if they can be privilege escalated. A new tool is helping security researchers discover misconfigured google data storage, as more and more businesses move their. 4 steps for hardening your cloud storage buckets: Taking charge of your security. This script (optionally) accepts gcp user/service. Google Storage Bucket Vulnerability.
From www.geeksforgeeks.org
Working with Google Cloud Storage Buckets Permissions and Access Google Storage Bucket Vulnerability A new tool is helping security researchers discover misconfigured google data storage, as more and more businesses move their. Learn how to set up appropriate access controls so you can locate sensitive data. Threat actors continued targeting unprotected public cloud. 4 steps for hardening your cloud storage buckets: Taking charge of your security. A script to enumerate google storage buckets,. Google Storage Bucket Vulnerability.
From www.youtube.com
Google Cloud Storage Bucket Lock Qwiklab YouTube Google Storage Bucket Vulnerability Threat actors continued targeting unprotected public cloud. Taking charge of your security. A script to enumerate google storage buckets, determine what access you have to them, and determine if they can be privilege escalated. 4 steps for hardening your cloud storage buckets: This article covers both google cloud and cloud service provider agnostic threats. This script (optionally) accepts gcp user/service. Google Storage Bucket Vulnerability.
From ip-slip.com
IP SLIP MAKE GOOGLE STORAGE BUCKETS PRIVATE Google Storage Bucket Vulnerability A script to enumerate google storage buckets, determine what access you have to them, and determine if they can be privilege escalated. Threat actors continued targeting unprotected public cloud. Learn how to set up appropriate access controls so you can locate sensitive data. This article covers both google cloud and cloud service provider agnostic threats. 4 steps for hardening your. Google Storage Bucket Vulnerability.
From k21academy.com
Google Cloud Storage Introduction & StepByStep Guide Google Storage Bucket Vulnerability Threat actors continued targeting unprotected public cloud. 4 steps for hardening your cloud storage buckets: A script to enumerate google storage buckets, determine what access you have to them, and determine if they can be privilege escalated. This article covers both google cloud and cloud service provider agnostic threats. A new tool is helping security researchers discover misconfigured google data. Google Storage Bucket Vulnerability.
From www.youtube.com
How to rename the google storage bucket in GCP YouTube Google Storage Bucket Vulnerability A script to enumerate google storage buckets, determine what access you have to them, and determine if they can be privilege escalated. This script (optionally) accepts gcp user/service account credentials and a keyword. Taking charge of your security. Threat actors continued targeting unprotected public cloud. This article covers both google cloud and cloud service provider agnostic threats. Learn how to. Google Storage Bucket Vulnerability.
From ip-slip.com
IP SLIP MAKE GOOGLE STORAGE BUCKETS PRIVATE Google Storage Bucket Vulnerability Threat actors continued targeting unprotected public cloud. 4 steps for hardening your cloud storage buckets: Taking charge of your security. A script to enumerate google storage buckets, determine what access you have to them, and determine if they can be privilege escalated. Learn how to set up appropriate access controls so you can locate sensitive data. A new tool is. Google Storage Bucket Vulnerability.
From www.youtube.com
Google Cloud Storage Bucket (Create, Delete, Upload, Download) YouTube Google Storage Bucket Vulnerability A new tool is helping security researchers discover misconfigured google data storage, as more and more businesses move their. This article covers both google cloud and cloud service provider agnostic threats. Threat actors continued targeting unprotected public cloud. 4 steps for hardening your cloud storage buckets: This script (optionally) accepts gcp user/service account credentials and a keyword. A script to. Google Storage Bucket Vulnerability.
From vivek-aws.medium.com
Unveiling the Hidden Risks How to Track and Secure Any Publicly Google Storage Bucket Vulnerability A script to enumerate google storage buckets, determine what access you have to them, and determine if they can be privilege escalated. This script (optionally) accepts gcp user/service account credentials and a keyword. Learn how to set up appropriate access controls so you can locate sensitive data. Taking charge of your security. Threat actors continued targeting unprotected public cloud. This. Google Storage Bucket Vulnerability.
From serverhealers.com
Create Cloud Storage Bucket in Google Cloud Platform • ServerHealers Google Storage Bucket Vulnerability A script to enumerate google storage buckets, determine what access you have to them, and determine if they can be privilege escalated. This script (optionally) accepts gcp user/service account credentials and a keyword. Learn how to set up appropriate access controls so you can locate sensitive data. Threat actors continued targeting unprotected public cloud. This article covers both google cloud. Google Storage Bucket Vulnerability.
From www.youtube.com
HOW TO FIND AWS S3 BUCKET MISCONFIGURATION VULNERABILITIES CLOUD Google Storage Bucket Vulnerability 4 steps for hardening your cloud storage buckets: Threat actors continued targeting unprotected public cloud. Learn how to set up appropriate access controls so you can locate sensitive data. This article covers both google cloud and cloud service provider agnostic threats. This script (optionally) accepts gcp user/service account credentials and a keyword. Taking charge of your security. A script to. Google Storage Bucket Vulnerability.
From www.geeksforgeeks.org
Working with Google Cloud Storage Buckets Permissions and Access Google Storage Bucket Vulnerability This script (optionally) accepts gcp user/service account credentials and a keyword. Taking charge of your security. A script to enumerate google storage buckets, determine what access you have to them, and determine if they can be privilege escalated. Learn how to set up appropriate access controls so you can locate sensitive data. A new tool is helping security researchers discover. Google Storage Bucket Vulnerability.
From datascientest.com
Les Buckets sur Google Cloud Platform Qu'estce que c'est ? À quoi ça Google Storage Bucket Vulnerability Learn how to set up appropriate access controls so you can locate sensitive data. This article covers both google cloud and cloud service provider agnostic threats. 4 steps for hardening your cloud storage buckets: A script to enumerate google storage buckets, determine what access you have to them, and determine if they can be privilege escalated. Taking charge of your. Google Storage Bucket Vulnerability.
From orca.security
The Risk of Malware in Cloud Storage Buckets Orca Security Google Storage Bucket Vulnerability A script to enumerate google storage buckets, determine what access you have to them, and determine if they can be privilege escalated. Threat actors continued targeting unprotected public cloud. Taking charge of your security. This article covers both google cloud and cloud service provider agnostic threats. This script (optionally) accepts gcp user/service account credentials and a keyword. 4 steps for. Google Storage Bucket Vulnerability.
From www.youtube.com
How to configure a Google Cloud storage bucket for CubeBackup. YouTube Google Storage Bucket Vulnerability Taking charge of your security. A new tool is helping security researchers discover misconfigured google data storage, as more and more businesses move their. 4 steps for hardening your cloud storage buckets: A script to enumerate google storage buckets, determine what access you have to them, and determine if they can be privilege escalated. Learn how to set up appropriate. Google Storage Bucket Vulnerability.
From bluegoatcyber.com
Exploring S3 Bucket Vulnerabilities Risks and Solutions Blue Goat Cyber Google Storage Bucket Vulnerability Taking charge of your security. Threat actors continued targeting unprotected public cloud. This article covers both google cloud and cloud service provider agnostic threats. 4 steps for hardening your cloud storage buckets: This script (optionally) accepts gcp user/service account credentials and a keyword. A script to enumerate google storage buckets, determine what access you have to them, and determine if. Google Storage Bucket Vulnerability.
From securityboulevard.com
Hidden Risk in the Default Roles of GoogleManaged Service Accounts Google Storage Bucket Vulnerability A script to enumerate google storage buckets, determine what access you have to them, and determine if they can be privilege escalated. Threat actors continued targeting unprotected public cloud. Learn how to set up appropriate access controls so you can locate sensitive data. This article covers both google cloud and cloud service provider agnostic threats. Taking charge of your security.. Google Storage Bucket Vulnerability.
From www.youtube.com
How to Create Bucket in Cloud Google Cloud Bucket Storage Create Google Storage Bucket Vulnerability A script to enumerate google storage buckets, determine what access you have to them, and determine if they can be privilege escalated. 4 steps for hardening your cloud storage buckets: Taking charge of your security. Learn how to set up appropriate access controls so you can locate sensitive data. A new tool is helping security researchers discover misconfigured google data. Google Storage Bucket Vulnerability.
From cloud.google.com
Optimize your Cloud Storage spend Google Cloud Blog Google Storage Bucket Vulnerability Taking charge of your security. A script to enumerate google storage buckets, determine what access you have to them, and determine if they can be privilege escalated. Learn how to set up appropriate access controls so you can locate sensitive data. This article covers both google cloud and cloud service provider agnostic threats. Threat actors continued targeting unprotected public cloud.. Google Storage Bucket Vulnerability.
From bluegoatcyber.com
Exploring S3 Bucket Vulnerabilities Risks and Solutions Blue Goat Cyber Google Storage Bucket Vulnerability This script (optionally) accepts gcp user/service account credentials and a keyword. A new tool is helping security researchers discover misconfigured google data storage, as more and more businesses move their. This article covers both google cloud and cloud service provider agnostic threats. Learn how to set up appropriate access controls so you can locate sensitive data. A script to enumerate. Google Storage Bucket Vulnerability.
From lifesciences-resources.awscloud.com
Migrating Google Cloud Storage to Amazon S3 using AWS DataSync Google Storage Bucket Vulnerability A script to enumerate google storage buckets, determine what access you have to them, and determine if they can be privilege escalated. 4 steps for hardening your cloud storage buckets: Learn how to set up appropriate access controls so you can locate sensitive data. Taking charge of your security. Threat actors continued targeting unprotected public cloud. This article covers both. Google Storage Bucket Vulnerability.