Network Devices Vulnerabilities . These are the design flaws in the system that can be exploited by hackers. A network vulnerability is a flaw or weakness in your it processes that could allow someone to gain access, steal data, or. Once the network devices are discovered and classified, security administrators are able to receive the latest security. While some vulnerabilities are unintentionally introduced during Network security vulnerability is a broad category of flaws, potential exploits, and weaknesses in system hardware, software, administration, and. Vulnerability management for network devices. Network vulnerabilities are weaknesses in a computer network that malicious actors can exploit to gain unauthorized access, launch dos attacks, or spread malware.
from www.le-vpn.com
While some vulnerabilities are unintentionally introduced during Vulnerability management for network devices. Once the network devices are discovered and classified, security administrators are able to receive the latest security. These are the design flaws in the system that can be exploited by hackers. Network security vulnerability is a broad category of flaws, potential exploits, and weaknesses in system hardware, software, administration, and. A network vulnerability is a flaw or weakness in your it processes that could allow someone to gain access, steal data, or. Network vulnerabilities are weaknesses in a computer network that malicious actors can exploit to gain unauthorized access, launch dos attacks, or spread malware.
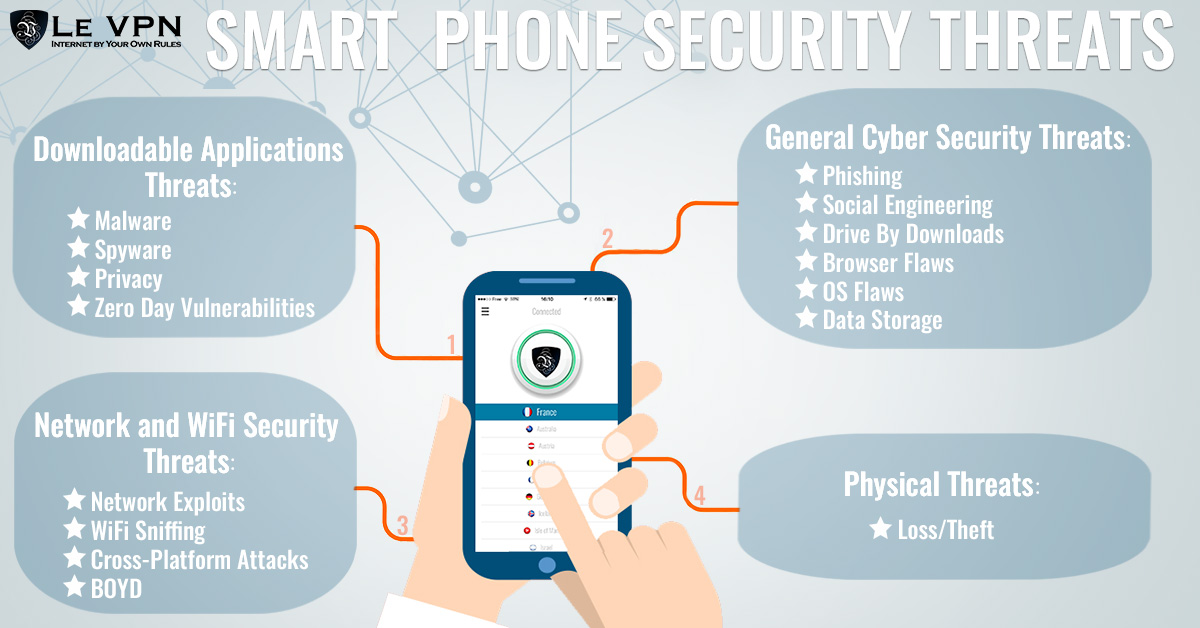
How to security challenges on mobile devices. Le VPN
Network Devices Vulnerabilities Once the network devices are discovered and classified, security administrators are able to receive the latest security. A network vulnerability is a flaw or weakness in your it processes that could allow someone to gain access, steal data, or. Vulnerability management for network devices. While some vulnerabilities are unintentionally introduced during Network vulnerabilities are weaknesses in a computer network that malicious actors can exploit to gain unauthorized access, launch dos attacks, or spread malware. Network security vulnerability is a broad category of flaws, potential exploits, and weaknesses in system hardware, software, administration, and. Once the network devices are discovered and classified, security administrators are able to receive the latest security. These are the design flaws in the system that can be exploited by hackers.
From pchtechnologies.com
5 Network Vulnerabilities You Should Address Immediately PCH Technologies Network Devices Vulnerabilities Network security vulnerability is a broad category of flaws, potential exploits, and weaknesses in system hardware, software, administration, and. Network vulnerabilities are weaknesses in a computer network that malicious actors can exploit to gain unauthorized access, launch dos attacks, or spread malware. Once the network devices are discovered and classified, security administrators are able to receive the latest security. A. Network Devices Vulnerabilities.
From boltonshield.com
Uncovering Network Vulnerabilities How Cyber Security Enhances Network Devices Vulnerabilities Network security vulnerability is a broad category of flaws, potential exploits, and weaknesses in system hardware, software, administration, and. Network vulnerabilities are weaknesses in a computer network that malicious actors can exploit to gain unauthorized access, launch dos attacks, or spread malware. A network vulnerability is a flaw or weakness in your it processes that could allow someone to gain. Network Devices Vulnerabilities.
From thecyphere.com
Top 10 Network Security Vulnerabilities Network Devices Vulnerabilities A network vulnerability is a flaw or weakness in your it processes that could allow someone to gain access, steal data, or. These are the design flaws in the system that can be exploited by hackers. Network security vulnerability is a broad category of flaws, potential exploits, and weaknesses in system hardware, software, administration, and. Network vulnerabilities are weaknesses in. Network Devices Vulnerabilities.
From info.bbhsolutions.com
3 Vulnerabilities Associated With Remote Access Network Devices Vulnerabilities Network security vulnerability is a broad category of flaws, potential exploits, and weaknesses in system hardware, software, administration, and. Once the network devices are discovered and classified, security administrators are able to receive the latest security. Network vulnerabilities are weaknesses in a computer network that malicious actors can exploit to gain unauthorized access, launch dos attacks, or spread malware. Vulnerability. Network Devices Vulnerabilities.
From www.youtube.com
Vulnerabilities in IoT YouTube Network Devices Vulnerabilities A network vulnerability is a flaw or weakness in your it processes that could allow someone to gain access, steal data, or. Vulnerability management for network devices. These are the design flaws in the system that can be exploited by hackers. Network vulnerabilities are weaknesses in a computer network that malicious actors can exploit to gain unauthorized access, launch dos. Network Devices Vulnerabilities.
From www.cloudi-fi.com
What are the IoT vulnerabilities that could hamper your network security Network Devices Vulnerabilities Network security vulnerability is a broad category of flaws, potential exploits, and weaknesses in system hardware, software, administration, and. These are the design flaws in the system that can be exploited by hackers. Vulnerability management for network devices. Once the network devices are discovered and classified, security administrators are able to receive the latest security. While some vulnerabilities are unintentionally. Network Devices Vulnerabilities.
From www.mdpi.com
Electronics Free FullText CoLLIoT A Collaborative Intruder Network Devices Vulnerabilities Vulnerability management for network devices. These are the design flaws in the system that can be exploited by hackers. Once the network devices are discovered and classified, security administrators are able to receive the latest security. A network vulnerability is a flaw or weakness in your it processes that could allow someone to gain access, steal data, or. While some. Network Devices Vulnerabilities.
From www.n3t.com
Network Vulnerabilities Hardware Network Devices Vulnerabilities Network security vulnerability is a broad category of flaws, potential exploits, and weaknesses in system hardware, software, administration, and. Network vulnerabilities are weaknesses in a computer network that malicious actors can exploit to gain unauthorized access, launch dos attacks, or spread malware. These are the design flaws in the system that can be exploited by hackers. Once the network devices. Network Devices Vulnerabilities.
From blog.radware.com
Network Security in an AppDriven World Radware Blog Network Devices Vulnerabilities Once the network devices are discovered and classified, security administrators are able to receive the latest security. Network vulnerabilities are weaknesses in a computer network that malicious actors can exploit to gain unauthorized access, launch dos attacks, or spread malware. Network security vulnerability is a broad category of flaws, potential exploits, and weaknesses in system hardware, software, administration, and. Vulnerability. Network Devices Vulnerabilities.
From securityintelligence.com
Identify Vulnerabilities in Your IT Infrastructure, Policies and Network Devices Vulnerabilities Vulnerability management for network devices. Network vulnerabilities are weaknesses in a computer network that malicious actors can exploit to gain unauthorized access, launch dos attacks, or spread malware. A network vulnerability is a flaw or weakness in your it processes that could allow someone to gain access, steal data, or. While some vulnerabilities are unintentionally introduced during Once the network. Network Devices Vulnerabilities.
From www.slideserve.com
PPT Network Vulnerabilities and Attacks PowerPoint Presentation, free Network Devices Vulnerabilities A network vulnerability is a flaw or weakness in your it processes that could allow someone to gain access, steal data, or. Vulnerability management for network devices. These are the design flaws in the system that can be exploited by hackers. While some vulnerabilities are unintentionally introduced during Network security vulnerability is a broad category of flaws, potential exploits, and. Network Devices Vulnerabilities.
From flatworldknowledge.lardbucket.org
Where Are Vulnerabilities? Understanding the Weaknesses Network Devices Vulnerabilities Once the network devices are discovered and classified, security administrators are able to receive the latest security. These are the design flaws in the system that can be exploited by hackers. Network security vulnerability is a broad category of flaws, potential exploits, and weaknesses in system hardware, software, administration, and. Network vulnerabilities are weaknesses in a computer network that malicious. Network Devices Vulnerabilities.
From www.eccouncil.org
Understanding IoT Security Challenges and Risks CCSE Network Devices Vulnerabilities Network security vulnerability is a broad category of flaws, potential exploits, and weaknesses in system hardware, software, administration, and. A network vulnerability is a flaw or weakness in your it processes that could allow someone to gain access, steal data, or. Network vulnerabilities are weaknesses in a computer network that malicious actors can exploit to gain unauthorized access, launch dos. Network Devices Vulnerabilities.
From tuhocielts.dolenglish.vn
Users urged to update Google Chrome 116 Daily News dol.vn Tự học Network Devices Vulnerabilities Once the network devices are discovered and classified, security administrators are able to receive the latest security. Network security vulnerability is a broad category of flaws, potential exploits, and weaknesses in system hardware, software, administration, and. While some vulnerabilities are unintentionally introduced during Network vulnerabilities are weaknesses in a computer network that malicious actors can exploit to gain unauthorized access,. Network Devices Vulnerabilities.
From www.splunk.com
What Is IoT Monitoring? Splunk Network Devices Vulnerabilities While some vulnerabilities are unintentionally introduced during Vulnerability management for network devices. Once the network devices are discovered and classified, security administrators are able to receive the latest security. A network vulnerability is a flaw or weakness in your it processes that could allow someone to gain access, steal data, or. Network security vulnerability is a broad category of flaws,. Network Devices Vulnerabilities.
From www.slideserve.com
PPT Chapter 4 Computer Network Vulnerabilities PowerPoint Network Devices Vulnerabilities Network security vulnerability is a broad category of flaws, potential exploits, and weaknesses in system hardware, software, administration, and. Vulnerability management for network devices. These are the design flaws in the system that can be exploited by hackers. Network vulnerabilities are weaknesses in a computer network that malicious actors can exploit to gain unauthorized access, launch dos attacks, or spread. Network Devices Vulnerabilities.
From servaplex.com
Security for Network Devices Vulnerability Manager Plus Network Devices Vulnerabilities While some vulnerabilities are unintentionally introduced during A network vulnerability is a flaw or weakness in your it processes that could allow someone to gain access, steal data, or. Vulnerability management for network devices. Network security vulnerability is a broad category of flaws, potential exploits, and weaknesses in system hardware, software, administration, and. Once the network devices are discovered and. Network Devices Vulnerabilities.
From www.executech.com
5 Biggest Types of Network Vulnerabilities Executech Network Devices Vulnerabilities Network vulnerabilities are weaknesses in a computer network that malicious actors can exploit to gain unauthorized access, launch dos attacks, or spread malware. Once the network devices are discovered and classified, security administrators are able to receive the latest security. A network vulnerability is a flaw or weakness in your it processes that could allow someone to gain access, steal. Network Devices Vulnerabilities.
From www.mdpi.com
Electronics Free FullText Analysis of Consumer IoT Device Network Devices Vulnerabilities While some vulnerabilities are unintentionally introduced during Network security vulnerability is a broad category of flaws, potential exploits, and weaknesses in system hardware, software, administration, and. Once the network devices are discovered and classified, security administrators are able to receive the latest security. These are the design flaws in the system that can be exploited by hackers. Vulnerability management for. Network Devices Vulnerabilities.
From www.researchgate.net
A typical IoT model that illustrates common hardware vulnerabilities Network Devices Vulnerabilities Network vulnerabilities are weaknesses in a computer network that malicious actors can exploit to gain unauthorized access, launch dos attacks, or spread malware. These are the design flaws in the system that can be exploited by hackers. Once the network devices are discovered and classified, security administrators are able to receive the latest security. A network vulnerability is a flaw. Network Devices Vulnerabilities.
From www.networkworld.com
Top 10 IoT vulnerabilities Network World Network Devices Vulnerabilities Network security vulnerability is a broad category of flaws, potential exploits, and weaknesses in system hardware, software, administration, and. Vulnerability management for network devices. Network vulnerabilities are weaknesses in a computer network that malicious actors can exploit to gain unauthorized access, launch dos attacks, or spread malware. These are the design flaws in the system that can be exploited by. Network Devices Vulnerabilities.
From www.trendmicro.com
Gateways to Infection Exploiting Software Vulnerabilities Threat Network Devices Vulnerabilities Vulnerability management for network devices. Network vulnerabilities are weaknesses in a computer network that malicious actors can exploit to gain unauthorized access, launch dos attacks, or spread malware. A network vulnerability is a flaw or weakness in your it processes that could allow someone to gain access, steal data, or. Once the network devices are discovered and classified, security administrators. Network Devices Vulnerabilities.
From www.keyfactor.com
Top 10 IoT Vulnerabilities in Your Devices Network Devices Vulnerabilities A network vulnerability is a flaw or weakness in your it processes that could allow someone to gain access, steal data, or. Once the network devices are discovered and classified, security administrators are able to receive the latest security. Network vulnerabilities are weaknesses in a computer network that malicious actors can exploit to gain unauthorized access, launch dos attacks, or. Network Devices Vulnerabilities.
From www.le-vpn.com
How to security challenges on mobile devices. Le VPN Network Devices Vulnerabilities Network vulnerabilities are weaknesses in a computer network that malicious actors can exploit to gain unauthorized access, launch dos attacks, or spread malware. Network security vulnerability is a broad category of flaws, potential exploits, and weaknesses in system hardware, software, administration, and. A network vulnerability is a flaw or weakness in your it processes that could allow someone to gain. Network Devices Vulnerabilities.
From attaxion.com
4 Common Network Vulnerabilities Attaxion Network Devices Vulnerabilities Network security vulnerability is a broad category of flaws, potential exploits, and weaknesses in system hardware, software, administration, and. While some vulnerabilities are unintentionally introduced during A network vulnerability is a flaw or weakness in your it processes that could allow someone to gain access, steal data, or. These are the design flaws in the system that can be exploited. Network Devices Vulnerabilities.
From www.linkedin.com
Common Types Of Network Security Vulnerabilities Network Devices Vulnerabilities While some vulnerabilities are unintentionally introduced during Network security vulnerability is a broad category of flaws, potential exploits, and weaknesses in system hardware, software, administration, and. Vulnerability management for network devices. Once the network devices are discovered and classified, security administrators are able to receive the latest security. Network vulnerabilities are weaknesses in a computer network that malicious actors can. Network Devices Vulnerabilities.
From prodefense.io
The Top IoT Attack Vectors How Hackers Exploit Vulnerabilities Network Devices Vulnerabilities Network security vulnerability is a broad category of flaws, potential exploits, and weaknesses in system hardware, software, administration, and. These are the design flaws in the system that can be exploited by hackers. A network vulnerability is a flaw or weakness in your it processes that could allow someone to gain access, steal data, or. Network vulnerabilities are weaknesses in. Network Devices Vulnerabilities.
From www.lightedge.com
Network Security Vulnerabilities Infographic LightEdge Solutions Network Devices Vulnerabilities These are the design flaws in the system that can be exploited by hackers. Vulnerability management for network devices. Network vulnerabilities are weaknesses in a computer network that malicious actors can exploit to gain unauthorized access, launch dos attacks, or spread malware. While some vulnerabilities are unintentionally introduced during A network vulnerability is a flaw or weakness in your it. Network Devices Vulnerabilities.
From ar.inspiredpencil.com
Network Layer Model Network Devices Vulnerabilities These are the design flaws in the system that can be exploited by hackers. A network vulnerability is a flaw or weakness in your it processes that could allow someone to gain access, steal data, or. While some vulnerabilities are unintentionally introduced during Network vulnerabilities are weaknesses in a computer network that malicious actors can exploit to gain unauthorized access,. Network Devices Vulnerabilities.
From www.studocu.com
Day 2 Network security Vulnerabilities information system Studocu Network Devices Vulnerabilities While some vulnerabilities are unintentionally introduced during A network vulnerability is a flaw or weakness in your it processes that could allow someone to gain access, steal data, or. Once the network devices are discovered and classified, security administrators are able to receive the latest security. Network vulnerabilities are weaknesses in a computer network that malicious actors can exploit to. Network Devices Vulnerabilities.
From courses.lumenlearning.com
Where Are Vulnerabilities? Understanding the Weaknesses Information Network Devices Vulnerabilities Vulnerability management for network devices. Once the network devices are discovered and classified, security administrators are able to receive the latest security. A network vulnerability is a flaw or weakness in your it processes that could allow someone to gain access, steal data, or. Network vulnerabilities are weaknesses in a computer network that malicious actors can exploit to gain unauthorized. Network Devices Vulnerabilities.
From www.trendmicro.com
Smart Yet Flawed IoT Device Vulnerabilities Explained Trend Micro (TH) Network Devices Vulnerabilities Vulnerability management for network devices. While some vulnerabilities are unintentionally introduced during Network vulnerabilities are weaknesses in a computer network that malicious actors can exploit to gain unauthorized access, launch dos attacks, or spread malware. These are the design flaws in the system that can be exploited by hackers. A network vulnerability is a flaw or weakness in your it. Network Devices Vulnerabilities.
From www.appsealing.com
IoT Security Optimization Tips & Benefits for Modern Businesses Network Devices Vulnerabilities Network security vulnerability is a broad category of flaws, potential exploits, and weaknesses in system hardware, software, administration, and. These are the design flaws in the system that can be exploited by hackers. Vulnerability management for network devices. Once the network devices are discovered and classified, security administrators are able to receive the latest security. While some vulnerabilities are unintentionally. Network Devices Vulnerabilities.
From redentry.co
3 Common Types of Network Security Vulnerabilities Redentry Network Devices Vulnerabilities A network vulnerability is a flaw or weakness in your it processes that could allow someone to gain access, steal data, or. Once the network devices are discovered and classified, security administrators are able to receive the latest security. Network security vulnerability is a broad category of flaws, potential exploits, and weaknesses in system hardware, software, administration, and. Network vulnerabilities. Network Devices Vulnerabilities.
From socradar.io
Network Devices Under Threat Mustang Panda Targets TPLink Routers Network Devices Vulnerabilities These are the design flaws in the system that can be exploited by hackers. Once the network devices are discovered and classified, security administrators are able to receive the latest security. Vulnerability management for network devices. Network vulnerabilities are weaknesses in a computer network that malicious actors can exploit to gain unauthorized access, launch dos attacks, or spread malware. Network. Network Devices Vulnerabilities.