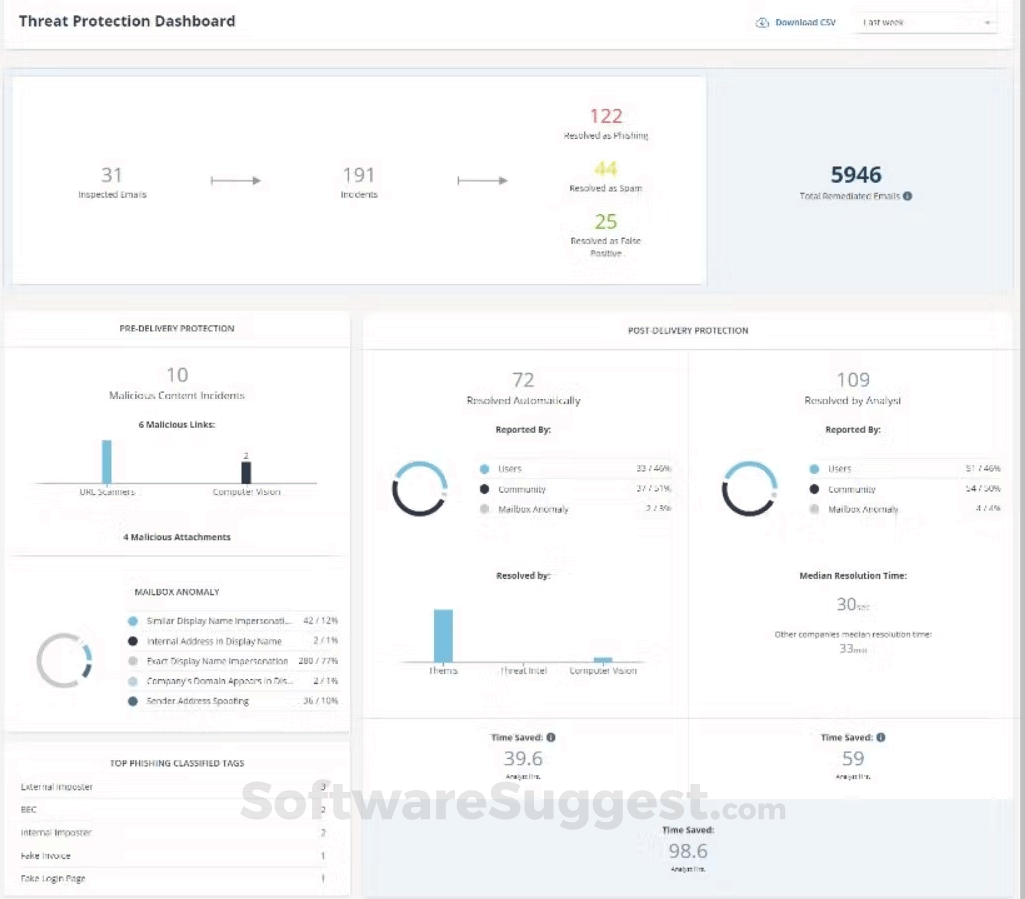
Ironscales Whitelist Domain . Say goodbye to phishing, bec, and qr code attacks. Discover the 10 most common tactics deployed to defeat email security controls. When you whitelist by following the instructions in these articles, you'll need our ip addresses, hostnames, or header information. Plans that meet your needchoose the right plan In cybersecurity, whitelists, also known as allowlists, serve as a proactive access control mechanism by explicitly allowing. Plans that meet your needchoose the right plan Our adaptive ai automatically learns and evolves to keep your employees safe from email attacks. Learn about the 13 most common email phishing techniques. Defend against bec, ato, social engineering, genai threats, and more. Hello, this is caused by ironscales quarantining the emails. Some of the campaign templates launched by ironscales direct users to custom domains that have been registered for training purposes.
from www.softwaresuggest.com
Say goodbye to phishing, bec, and qr code attacks. In cybersecurity, whitelists, also known as allowlists, serve as a proactive access control mechanism by explicitly allowing. Plans that meet your needchoose the right plan Discover the 10 most common tactics deployed to defeat email security controls. Our adaptive ai automatically learns and evolves to keep your employees safe from email attacks. Some of the campaign templates launched by ironscales direct users to custom domains that have been registered for training purposes. Plans that meet your needchoose the right plan Hello, this is caused by ironscales quarantining the emails. Defend against bec, ato, social engineering, genai threats, and more. When you whitelist by following the instructions in these articles, you'll need our ip addresses, hostnames, or header information.
IRONSCALES Pricing, Features, and Reviews (Sep 2024)
Ironscales Whitelist Domain Some of the campaign templates launched by ironscales direct users to custom domains that have been registered for training purposes. Plans that meet your needchoose the right plan When you whitelist by following the instructions in these articles, you'll need our ip addresses, hostnames, or header information. Hello, this is caused by ironscales quarantining the emails. Learn about the 13 most common email phishing techniques. In cybersecurity, whitelists, also known as allowlists, serve as a proactive access control mechanism by explicitly allowing. Some of the campaign templates launched by ironscales direct users to custom domains that have been registered for training purposes. Plans that meet your needchoose the right plan Say goodbye to phishing, bec, and qr code attacks. Our adaptive ai automatically learns and evolves to keep your employees safe from email attacks. Defend against bec, ato, social engineering, genai threats, and more. Discover the 10 most common tactics deployed to defeat email security controls.
From www.producthunt.com
Domain Whitelist Makers Product Hunt Ironscales Whitelist Domain Say goodbye to phishing, bec, and qr code attacks. Hello, this is caused by ironscales quarantining the emails. Our adaptive ai automatically learns and evolves to keep your employees safe from email attacks. Defend against bec, ato, social engineering, genai threats, and more. Plans that meet your needchoose the right plan Learn about the 13 most common email phishing techniques.. Ironscales Whitelist Domain.
From www.capterra.ca
IRONSCALES Pricing, Reviews & Features Capterra Canada 2024 Ironscales Whitelist Domain Discover the 10 most common tactics deployed to defeat email security controls. Defend against bec, ato, social engineering, genai threats, and more. Plans that meet your needchoose the right plan When you whitelist by following the instructions in these articles, you'll need our ip addresses, hostnames, or header information. Learn about the 13 most common email phishing techniques. In cybersecurity,. Ironscales Whitelist Domain.
From ai-techpark.com
IRONSCALES Launches Themis Copilot Beta Version AITech Park Ironscales Whitelist Domain Hello, this is caused by ironscales quarantining the emails. Defend against bec, ato, social engineering, genai threats, and more. Learn about the 13 most common email phishing techniques. Discover the 10 most common tactics deployed to defeat email security controls. Plans that meet your needchoose the right plan Plans that meet your needchoose the right plan Our adaptive ai automatically. Ironscales Whitelist Domain.
From www.youtube.com
How to Whitelist Domain in Office 365 How to Whitelist Domain and Ironscales Whitelist Domain Some of the campaign templates launched by ironscales direct users to custom domains that have been registered for training purposes. Learn about the 13 most common email phishing techniques. Discover the 10 most common tactics deployed to defeat email security controls. Hello, this is caused by ironscales quarantining the emails. Defend against bec, ato, social engineering, genai threats, and more.. Ironscales Whitelist Domain.
From expertinsights.com
IRONSCALES Security Awareness Training Reviews and Pricing Expert Ironscales Whitelist Domain Learn about the 13 most common email phishing techniques. Plans that meet your needchoose the right plan When you whitelist by following the instructions in these articles, you'll need our ip addresses, hostnames, or header information. In cybersecurity, whitelists, also known as allowlists, serve as a proactive access control mechanism by explicitly allowing. Discover the 10 most common tactics deployed. Ironscales Whitelist Domain.
From petri.com
How to Whitelist a Domain in Office 365 Petri Ironscales Whitelist Domain Defend against bec, ato, social engineering, genai threats, and more. Learn about the 13 most common email phishing techniques. In cybersecurity, whitelists, also known as allowlists, serve as a proactive access control mechanism by explicitly allowing. Plans that meet your needchoose the right plan Our adaptive ai automatically learns and evolves to keep your employees safe from email attacks. When. Ironscales Whitelist Domain.
From www.behance.net
Ironscales project on Behance Ironscales Whitelist Domain Discover the 10 most common tactics deployed to defeat email security controls. Hello, this is caused by ironscales quarantining the emails. Say goodbye to phishing, bec, and qr code attacks. In cybersecurity, whitelists, also known as allowlists, serve as a proactive access control mechanism by explicitly allowing. Plans that meet your needchoose the right plan Some of the campaign templates. Ironscales Whitelist Domain.
From www.businesswire.com
IRONSCALES Honored With Coveted Global InfoSec Award at This Year’s RSA Ironscales Whitelist Domain Some of the campaign templates launched by ironscales direct users to custom domains that have been registered for training purposes. Plans that meet your needchoose the right plan Say goodbye to phishing, bec, and qr code attacks. Defend against bec, ato, social engineering, genai threats, and more. When you whitelist by following the instructions in these articles, you'll need our. Ironscales Whitelist Domain.
From www.softwaresuggest.com
IRONSCALES Pricing, Features, and Reviews (Sep 2024) Ironscales Whitelist Domain Our adaptive ai automatically learns and evolves to keep your employees safe from email attacks. Discover the 10 most common tactics deployed to defeat email security controls. In cybersecurity, whitelists, also known as allowlists, serve as a proactive access control mechanism by explicitly allowing. Say goodbye to phishing, bec, and qr code attacks. When you whitelist by following the instructions. Ironscales Whitelist Domain.
From www.storagenewsletter.com
Proact Partnered With Ironscales StorageNewsletter Ironscales Whitelist Domain When you whitelist by following the instructions in these articles, you'll need our ip addresses, hostnames, or header information. Plans that meet your needchoose the right plan Our adaptive ai automatically learns and evolves to keep your employees safe from email attacks. In cybersecurity, whitelists, also known as allowlists, serve as a proactive access control mechanism by explicitly allowing. Defend. Ironscales Whitelist Domain.
From secure.ironscales.com
Google Workspace + IRONSCALES A Complete Email Security Solution Ironscales Whitelist Domain Some of the campaign templates launched by ironscales direct users to custom domains that have been registered for training purposes. Plans that meet your needchoose the right plan Discover the 10 most common tactics deployed to defeat email security controls. In cybersecurity, whitelists, also known as allowlists, serve as a proactive access control mechanism by explicitly allowing. Defend against bec,. Ironscales Whitelist Domain.
From www.youtube.com
How to Whitelist Email Domains? YouTube Ironscales Whitelist Domain Discover the 10 most common tactics deployed to defeat email security controls. Some of the campaign templates launched by ironscales direct users to custom domains that have been registered for training purposes. Defend against bec, ato, social engineering, genai threats, and more. Plans that meet your needchoose the right plan Plans that meet your needchoose the right plan Our adaptive. Ironscales Whitelist Domain.
From www.linkedin.com
IRONSCALES on LinkedIn The IRONSCALES State of Cybersecurity Report Ironscales Whitelist Domain Plans that meet your needchoose the right plan Hello, this is caused by ironscales quarantining the emails. Plans that meet your needchoose the right plan Learn about the 13 most common email phishing techniques. Say goodbye to phishing, bec, and qr code attacks. Some of the campaign templates launched by ironscales direct users to custom domains that have been registered. Ironscales Whitelist Domain.
From support.atera.com
Atera and Ironscales Atera Support Ironscales Whitelist Domain Plans that meet your needchoose the right plan When you whitelist by following the instructions in these articles, you'll need our ip addresses, hostnames, or header information. In cybersecurity, whitelists, also known as allowlists, serve as a proactive access control mechanism by explicitly allowing. Say goodbye to phishing, bec, and qr code attacks. Hello, this is caused by ironscales quarantining. Ironscales Whitelist Domain.
From ironscales.com
Proofpoint vs. IRONSCALES Choosing the Right Email Security Platform Ironscales Whitelist Domain Discover the 10 most common tactics deployed to defeat email security controls. Hello, this is caused by ironscales quarantining the emails. Say goodbye to phishing, bec, and qr code attacks. Plans that meet your needchoose the right plan In cybersecurity, whitelists, also known as allowlists, serve as a proactive access control mechanism by explicitly allowing. Learn about the 13 most. Ironscales Whitelist Domain.
From www.securityinfowatch.com
IRONSCALES new product release strengthens advanced phishing threat Ironscales Whitelist Domain Defend against bec, ato, social engineering, genai threats, and more. Plans that meet your needchoose the right plan When you whitelist by following the instructions in these articles, you'll need our ip addresses, hostnames, or header information. Learn about the 13 most common email phishing techniques. Say goodbye to phishing, bec, and qr code attacks. Hello, this is caused by. Ironscales Whitelist Domain.
From twitter.com
IRONSCALES on Twitter "🎣 Phishing attacks are on the rise, but so is Ironscales Whitelist Domain In cybersecurity, whitelists, also known as allowlists, serve as a proactive access control mechanism by explicitly allowing. Defend against bec, ato, social engineering, genai threats, and more. Plans that meet your needchoose the right plan Our adaptive ai automatically learns and evolves to keep your employees safe from email attacks. Plans that meet your needchoose the right plan Hello, this. Ironscales Whitelist Domain.
From expertinsights.com
IRONSCALES Email Security Platform Reviews and Pricing Expert Insights Ironscales Whitelist Domain Learn about the 13 most common email phishing techniques. Plans that meet your needchoose the right plan Defend against bec, ato, social engineering, genai threats, and more. Some of the campaign templates launched by ironscales direct users to custom domains that have been registered for training purposes. Hello, this is caused by ironscales quarantining the emails. When you whitelist by. Ironscales Whitelist Domain.
From www.linkedin.com
IRONSCALES on LinkedIn Request A Live Demo IRONSCALES Ironscales Whitelist Domain Hello, this is caused by ironscales quarantining the emails. Plans that meet your needchoose the right plan Say goodbye to phishing, bec, and qr code attacks. Our adaptive ai automatically learns and evolves to keep your employees safe from email attacks. Discover the 10 most common tactics deployed to defeat email security controls. When you whitelist by following the instructions. Ironscales Whitelist Domain.
From aws.amazon.com
AWS Marketplace IRONSCALES Integrated Cloud Email Security Platform Ironscales Whitelist Domain Say goodbye to phishing, bec, and qr code attacks. In cybersecurity, whitelists, also known as allowlists, serve as a proactive access control mechanism by explicitly allowing. Defend against bec, ato, social engineering, genai threats, and more. Hello, this is caused by ironscales quarantining the emails. Plans that meet your needchoose the right plan Learn about the 13 most common email. Ironscales Whitelist Domain.
From lazyadmin.nl
How to Whitelist a Domain in Office 365 — LazyAdmin Ironscales Whitelist Domain Our adaptive ai automatically learns and evolves to keep your employees safe from email attacks. Hello, this is caused by ironscales quarantining the emails. When you whitelist by following the instructions in these articles, you'll need our ip addresses, hostnames, or header information. Learn about the 13 most common email phishing techniques. Plans that meet your needchoose the right plan. Ironscales Whitelist Domain.
From activedirectorypro.com
Steps to Whitelist a Domain in Office 365 Active Directory Pro Ironscales Whitelist Domain Plans that meet your needchoose the right plan Defend against bec, ato, social engineering, genai threats, and more. Say goodbye to phishing, bec, and qr code attacks. Our adaptive ai automatically learns and evolves to keep your employees safe from email attacks. When you whitelist by following the instructions in these articles, you'll need our ip addresses, hostnames, or header. Ironscales Whitelist Domain.
From expertinsights.com
IRONSCALES Email Security Platform Reviews and Pricing Expert Insights Ironscales Whitelist Domain Plans that meet your needchoose the right plan Learn about the 13 most common email phishing techniques. Plans that meet your needchoose the right plan Hello, this is caused by ironscales quarantining the emails. In cybersecurity, whitelists, also known as allowlists, serve as a proactive access control mechanism by explicitly allowing. When you whitelist by following the instructions in these. Ironscales Whitelist Domain.
From mightyguides.com
IRONSCALES How to Stay Ahead of the Growing Email Security Threat Ironscales Whitelist Domain Say goodbye to phishing, bec, and qr code attacks. Our adaptive ai automatically learns and evolves to keep your employees safe from email attacks. Plans that meet your needchoose the right plan Learn about the 13 most common email phishing techniques. Hello, this is caused by ironscales quarantining the emails. Defend against bec, ato, social engineering, genai threats, and more.. Ironscales Whitelist Domain.
From www.linkedin.com
IRONSCALES on LinkedIn Download Your InfoTech Ransomware Incident Ironscales Whitelist Domain In cybersecurity, whitelists, also known as allowlists, serve as a proactive access control mechanism by explicitly allowing. Plans that meet your needchoose the right plan Hello, this is caused by ironscales quarantining the emails. Learn about the 13 most common email phishing techniques. Discover the 10 most common tactics deployed to defeat email security controls. Some of the campaign templates. Ironscales Whitelist Domain.
From support.atera.com
Atera and Ironscales Atera Support Ironscales Whitelist Domain Plans that meet your needchoose the right plan In cybersecurity, whitelists, also known as allowlists, serve as a proactive access control mechanism by explicitly allowing. Say goodbye to phishing, bec, and qr code attacks. Some of the campaign templates launched by ironscales direct users to custom domains that have been registered for training purposes. Plans that meet your needchoose the. Ironscales Whitelist Domain.
From expertinsights.com
IRONSCALES A Comprehensive Deep Dive Expert Insights Ironscales Whitelist Domain Defend against bec, ato, social engineering, genai threats, and more. Learn about the 13 most common email phishing techniques. Hello, this is caused by ironscales quarantining the emails. Discover the 10 most common tactics deployed to defeat email security controls. Some of the campaign templates launched by ironscales direct users to custom domains that have been registered for training purposes.. Ironscales Whitelist Domain.
From expertinsights.com
IRONSCALES Email Security Platform Reviews and Pricing Expert Insights Ironscales Whitelist Domain Plans that meet your needchoose the right plan Our adaptive ai automatically learns and evolves to keep your employees safe from email attacks. When you whitelist by following the instructions in these articles, you'll need our ip addresses, hostnames, or header information. Defend against bec, ato, social engineering, genai threats, and more. Say goodbye to phishing, bec, and qr code. Ironscales Whitelist Domain.
From expertinsights.com
IRONSCALES A Comprehensive Deep Dive Expert Insights Ironscales Whitelist Domain Plans that meet your needchoose the right plan Discover the 10 most common tactics deployed to defeat email security controls. Some of the campaign templates launched by ironscales direct users to custom domains that have been registered for training purposes. Plans that meet your needchoose the right plan Defend against bec, ato, social engineering, genai threats, and more. When you. Ironscales Whitelist Domain.
From office365concepts.com
How to whitelist a domain in Office 365 Ironscales Whitelist Domain Some of the campaign templates launched by ironscales direct users to custom domains that have been registered for training purposes. Hello, this is caused by ironscales quarantining the emails. Plans that meet your needchoose the right plan Learn about the 13 most common email phishing techniques. When you whitelist by following the instructions in these articles, you'll need our ip. Ironscales Whitelist Domain.
From expertinsights.com
IRONSCALES A Comprehensive Deep Dive Expert Insights Ironscales Whitelist Domain Hello, this is caused by ironscales quarantining the emails. Our adaptive ai automatically learns and evolves to keep your employees safe from email attacks. Defend against bec, ato, social engineering, genai threats, and more. Some of the campaign templates launched by ironscales direct users to custom domains that have been registered for training purposes. Discover the 10 most common tactics. Ironscales Whitelist Domain.
From www.g2.com
IRONSCALES Reviews 2024 Details, Pricing, & Features G2 Ironscales Whitelist Domain Plans that meet your needchoose the right plan Hello, this is caused by ironscales quarantining the emails. When you whitelist by following the instructions in these articles, you'll need our ip addresses, hostnames, or header information. Some of the campaign templates launched by ironscales direct users to custom domains that have been registered for training purposes. Defend against bec, ato,. Ironscales Whitelist Domain.
From www.capterra.ca
IRONSCALES Pricing, Reviews & Features Capterra Canada 2024 Ironscales Whitelist Domain In cybersecurity, whitelists, also known as allowlists, serve as a proactive access control mechanism by explicitly allowing. Our adaptive ai automatically learns and evolves to keep your employees safe from email attacks. Defend against bec, ato, social engineering, genai threats, and more. Learn about the 13 most common email phishing techniques. Hello, this is caused by ironscales quarantining the emails.. Ironscales Whitelist Domain.
From www.youtube.com
IRONSCALES™ Starter™ for Phishing Simulation Testing Tutorial YouTube Ironscales Whitelist Domain Discover the 10 most common tactics deployed to defeat email security controls. Defend against bec, ato, social engineering, genai threats, and more. Say goodbye to phishing, bec, and qr code attacks. Hello, this is caused by ironscales quarantining the emails. In cybersecurity, whitelists, also known as allowlists, serve as a proactive access control mechanism by explicitly allowing. Plans that meet. Ironscales Whitelist Domain.
From support.atera.com
Atera and Ironscales Atera Support Ironscales Whitelist Domain When you whitelist by following the instructions in these articles, you'll need our ip addresses, hostnames, or header information. Plans that meet your needchoose the right plan Learn about the 13 most common email phishing techniques. Defend against bec, ato, social engineering, genai threats, and more. Discover the 10 most common tactics deployed to defeat email security controls. Our adaptive. Ironscales Whitelist Domain.