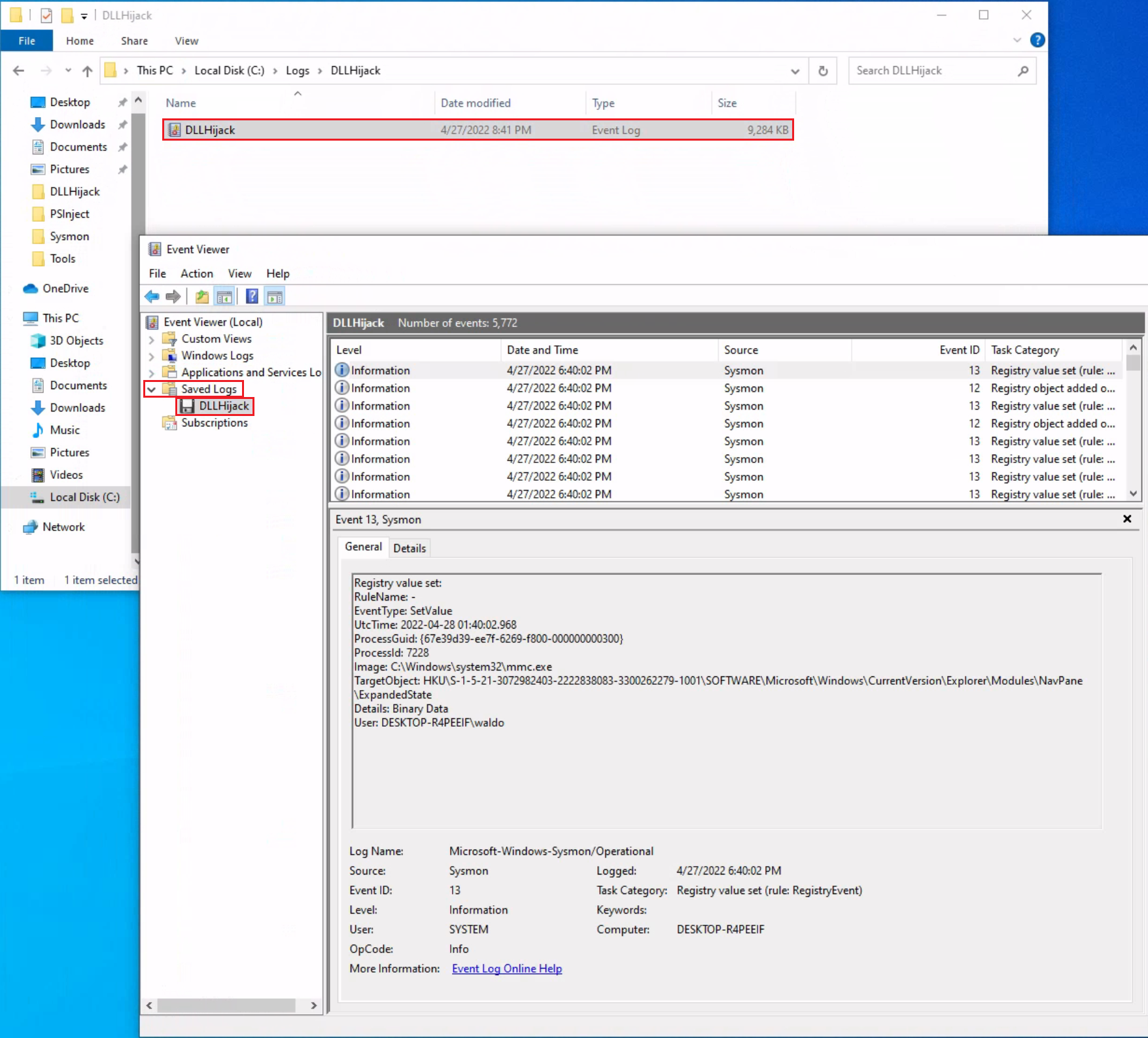
Windows Event Logs Tryhackme . Soc level 1, cyber defense. Using the left panel, expand applications and. After learning about the tool suite, sysinternals, we are now going to be learning about logs, specifically. Event log analysis — identifying and interpreting different. Endpoint security monitoring, security operations & monitoring. Open event viewer either by searching for the program or using eventvwr.msc command within the windows terminal. Learn how to use remina, wevtutil, get. A write up for a tryhackme room that involves windows event logs analysis and powershell attacks. Powershell will log operations from the engine, providers, and cmdlets to the windows event log.
from academy.hackthebox.com
Soc level 1, cyber defense. A write up for a tryhackme room that involves windows event logs analysis and powershell attacks. After learning about the tool suite, sysinternals, we are now going to be learning about logs, specifically. Using the left panel, expand applications and. Learn how to use remina, wevtutil, get. Event log analysis — identifying and interpreting different. Open event viewer either by searching for the program or using eventvwr.msc command within the windows terminal. Powershell will log operations from the engine, providers, and cmdlets to the windows event log. Endpoint security monitoring, security operations & monitoring.
Windows Event Logs & Finding Evil Course HTB Academy
Windows Event Logs Tryhackme Endpoint security monitoring, security operations & monitoring. Soc level 1, cyber defense. After learning about the tool suite, sysinternals, we are now going to be learning about logs, specifically. Open event viewer either by searching for the program or using eventvwr.msc command within the windows terminal. Using the left panel, expand applications and. Learn how to use remina, wevtutil, get. Powershell will log operations from the engine, providers, and cmdlets to the windows event log. A write up for a tryhackme room that involves windows event logs analysis and powershell attacks. Event log analysis — identifying and interpreting different. Endpoint security monitoring, security operations & monitoring.
From igorsec.blog
Windows Event Logs TryHackMe Igor_sec's Blog Windows Event Logs Tryhackme After learning about the tool suite, sysinternals, we are now going to be learning about logs, specifically. Powershell will log operations from the engine, providers, and cmdlets to the windows event log. Soc level 1, cyber defense. Learn how to use remina, wevtutil, get. Endpoint security monitoring, security operations & monitoring. Open event viewer either by searching for the program. Windows Event Logs Tryhackme.
From www.tactig.com
How to Configure and Analyze Event Logs in Windows 10? Tactig Windows Event Logs Tryhackme Powershell will log operations from the engine, providers, and cmdlets to the windows event log. Using the left panel, expand applications and. Event log analysis — identifying and interpreting different. Soc level 1, cyber defense. Learn how to use remina, wevtutil, get. Endpoint security monitoring, security operations & monitoring. Open event viewer either by searching for the program or using. Windows Event Logs Tryhackme.
From www.youtube.com
Windows Events Log TryHackMe SOC Analyst YouTube Windows Event Logs Tryhackme Learn how to use remina, wevtutil, get. Open event viewer either by searching for the program or using eventvwr.msc command within the windows terminal. Endpoint security monitoring, security operations & monitoring. After learning about the tool suite, sysinternals, we are now going to be learning about logs, specifically. A write up for a tryhackme room that involves windows event logs. Windows Event Logs Tryhackme.
From academy.hackthebox.com
Windows Event Logs & Finding Evil Course HTB Academy Windows Event Logs Tryhackme Event log analysis — identifying and interpreting different. A write up for a tryhackme room that involves windows event logs analysis and powershell attacks. Using the left panel, expand applications and. Endpoint security monitoring, security operations & monitoring. Learn how to use remina, wevtutil, get. Powershell will log operations from the engine, providers, and cmdlets to the windows event log.. Windows Event Logs Tryhackme.
From www.manageengine.com
What is Windows Event Log A complete guide from ADAudit Plus Windows Event Logs Tryhackme Powershell will log operations from the engine, providers, and cmdlets to the windows event log. A write up for a tryhackme room that involves windows event logs analysis and powershell attacks. Endpoint security monitoring, security operations & monitoring. Event log analysis — identifying and interpreting different. Learn how to use remina, wevtutil, get. After learning about the tool suite, sysinternals,. Windows Event Logs Tryhackme.
From igorsec.blog
Windows Event Logs TryHackMe Igor_sec's Blog Windows Event Logs Tryhackme Endpoint security monitoring, security operations & monitoring. A write up for a tryhackme room that involves windows event logs analysis and powershell attacks. After learning about the tool suite, sysinternals, we are now going to be learning about logs, specifically. Open event viewer either by searching for the program or using eventvwr.msc command within the windows terminal. Event log analysis. Windows Event Logs Tryhackme.
From thedutchhacker.com
Windows Event Logs on Tryhackme The Dutch Hacker Windows Event Logs Tryhackme Open event viewer either by searching for the program or using eventvwr.msc command within the windows terminal. Endpoint security monitoring, security operations & monitoring. Soc level 1, cyber defense. Learn how to use remina, wevtutil, get. Using the left panel, expand applications and. After learning about the tool suite, sysinternals, we are now going to be learning about logs, specifically.. Windows Event Logs Tryhackme.
From thedutchhacker.com
Windows Event Logs on Tryhackme The Dutch Hacker Windows Event Logs Tryhackme Open event viewer either by searching for the program or using eventvwr.msc command within the windows terminal. After learning about the tool suite, sysinternals, we are now going to be learning about logs, specifically. Endpoint security monitoring, security operations & monitoring. Learn how to use remina, wevtutil, get. Using the left panel, expand applications and. A write up for a. Windows Event Logs Tryhackme.
From www.eginnovations.com
What is Windows Event Log? eG Innovations Windows Event Logs Tryhackme After learning about the tool suite, sysinternals, we are now going to be learning about logs, specifically. Open event viewer either by searching for the program or using eventvwr.msc command within the windows terminal. Powershell will log operations from the engine, providers, and cmdlets to the windows event log. Learn how to use remina, wevtutil, get. Using the left panel,. Windows Event Logs Tryhackme.
From medium.com
Windows Event Logs Room — TryHackMe by Christof Medium Windows Event Logs Tryhackme Soc level 1, cyber defense. Learn how to use remina, wevtutil, get. A write up for a tryhackme room that involves windows event logs analysis and powershell attacks. Event log analysis — identifying and interpreting different. After learning about the tool suite, sysinternals, we are now going to be learning about logs, specifically. Using the left panel, expand applications and.. Windows Event Logs Tryhackme.
From thedutchhacker.com
Windows Event Logs on Tryhackme The Dutch Hacker Windows Event Logs Tryhackme Using the left panel, expand applications and. A write up for a tryhackme room that involves windows event logs analysis and powershell attacks. After learning about the tool suite, sysinternals, we are now going to be learning about logs, specifically. Learn how to use remina, wevtutil, get. Open event viewer either by searching for the program or using eventvwr.msc command. Windows Event Logs Tryhackme.
From www.rockwellautomation.com
Windows Event Logs Windows Event Logs Tryhackme Learn how to use remina, wevtutil, get. After learning about the tool suite, sysinternals, we are now going to be learning about logs, specifically. Using the left panel, expand applications and. Soc level 1, cyber defense. Endpoint security monitoring, security operations & monitoring. Event log analysis — identifying and interpreting different. Powershell will log operations from the engine, providers, and. Windows Event Logs Tryhackme.
From www.reddit.com
Analyzing Windows Event Logs Manually TryHackMe Tempest P1 r Windows Event Logs Tryhackme Event log analysis — identifying and interpreting different. After learning about the tool suite, sysinternals, we are now going to be learning about logs, specifically. Learn how to use remina, wevtutil, get. Open event viewer either by searching for the program or using eventvwr.msc command within the windows terminal. Using the left panel, expand applications and. A write up for. Windows Event Logs Tryhackme.
From igorsec.blog
Windows Event Logs TryHackMe Igor_sec's Blog Windows Event Logs Tryhackme Learn how to use remina, wevtutil, get. Using the left panel, expand applications and. Event log analysis — identifying and interpreting different. Powershell will log operations from the engine, providers, and cmdlets to the windows event log. Soc level 1, cyber defense. Endpoint security monitoring, security operations & monitoring. A write up for a tryhackme room that involves windows event. Windows Event Logs Tryhackme.
From www.manageengine.com
What is Windows Event Log A complete guide from ADAudit Plus Windows Event Logs Tryhackme Event log analysis — identifying and interpreting different. A write up for a tryhackme room that involves windows event logs analysis and powershell attacks. Using the left panel, expand applications and. Soc level 1, cyber defense. Powershell will log operations from the engine, providers, and cmdlets to the windows event log. Learn how to use remina, wevtutil, get. After learning. Windows Event Logs Tryhackme.
From jacob-taylor.gitbook.io
Windows Event Logs SOC LEVEL 1 Windows Event Logs Tryhackme Soc level 1, cyber defense. Endpoint security monitoring, security operations & monitoring. Using the left panel, expand applications and. Event log analysis — identifying and interpreting different. Learn how to use remina, wevtutil, get. A write up for a tryhackme room that involves windows event logs analysis and powershell attacks. After learning about the tool suite, sysinternals, we are now. Windows Event Logs Tryhackme.
From www.vrogue.co
How To Open And Use Windows 10 Event Viewer vrogue.co Windows Event Logs Tryhackme A write up for a tryhackme room that involves windows event logs analysis and powershell attacks. Powershell will log operations from the engine, providers, and cmdlets to the windows event log. After learning about the tool suite, sysinternals, we are now going to be learning about logs, specifically. Event log analysis — identifying and interpreting different. Learn how to use. Windows Event Logs Tryhackme.
From github.com
GitHub r1skkam/TryHackMeWindowsEventLogs Introduction to Windows Windows Event Logs Tryhackme Powershell will log operations from the engine, providers, and cmdlets to the windows event log. Using the left panel, expand applications and. Endpoint security monitoring, security operations & monitoring. After learning about the tool suite, sysinternals, we are now going to be learning about logs, specifically. Open event viewer either by searching for the program or using eventvwr.msc command within. Windows Event Logs Tryhackme.
From igorsec.blog
Windows Event Logs TryHackMe Igor_sec's Blog Windows Event Logs Tryhackme Event log analysis — identifying and interpreting different. Endpoint security monitoring, security operations & monitoring. Soc level 1, cyber defense. Using the left panel, expand applications and. Open event viewer either by searching for the program or using eventvwr.msc command within the windows terminal. After learning about the tool suite, sysinternals, we are now going to be learning about logs,. Windows Event Logs Tryhackme.
From medium.com
(THM) room ‘Windows Event Logs’ by Majewski Arek Medium Windows Event Logs Tryhackme A write up for a tryhackme room that involves windows event logs analysis and powershell attacks. Endpoint security monitoring, security operations & monitoring. Using the left panel, expand applications and. Learn how to use remina, wevtutil, get. After learning about the tool suite, sysinternals, we are now going to be learning about logs, specifically. Event log analysis — identifying and. Windows Event Logs Tryhackme.
From www.kumaratuljaiswal.in
TryHackMe windows sysmon utilize to monitor and log your endpoint and Windows Event Logs Tryhackme Event log analysis — identifying and interpreting different. Using the left panel, expand applications and. After learning about the tool suite, sysinternals, we are now going to be learning about logs, specifically. Learn how to use remina, wevtutil, get. Powershell will log operations from the engine, providers, and cmdlets to the windows event log. A write up for a tryhackme. Windows Event Logs Tryhackme.
From winaero.com
How to Clear All Event Logs in Windows 10 Windows Event Logs Tryhackme Soc level 1, cyber defense. A write up for a tryhackme room that involves windows event logs analysis and powershell attacks. Event log analysis — identifying and interpreting different. Learn how to use remina, wevtutil, get. Using the left panel, expand applications and. After learning about the tool suite, sysinternals, we are now going to be learning about logs, specifically.. Windows Event Logs Tryhackme.
From medium.com
Windows Event Logs Room — TryHackMe by Christof Medium Windows Event Logs Tryhackme Open event viewer either by searching for the program or using eventvwr.msc command within the windows terminal. A write up for a tryhackme room that involves windows event logs analysis and powershell attacks. Powershell will log operations from the engine, providers, and cmdlets to the windows event log. Soc level 1, cyber defense. Event log analysis — identifying and interpreting. Windows Event Logs Tryhackme.
From documentation.trendminer.com
How to get Windows event logs? Windows Event Logs Tryhackme Powershell will log operations from the engine, providers, and cmdlets to the windows event log. After learning about the tool suite, sysinternals, we are now going to be learning about logs, specifically. A write up for a tryhackme room that involves windows event logs analysis and powershell attacks. Using the left panel, expand applications and. Soc level 1, cyber defense.. Windows Event Logs Tryhackme.
From www.youtube.com
Try Hack Me Windows Event Logs YouTube Windows Event Logs Tryhackme Event log analysis — identifying and interpreting different. Endpoint security monitoring, security operations & monitoring. Learn how to use remina, wevtutil, get. Powershell will log operations from the engine, providers, and cmdlets to the windows event log. After learning about the tool suite, sysinternals, we are now going to be learning about logs, specifically. Using the left panel, expand applications. Windows Event Logs Tryhackme.
From shin569.hatenablog.com
【TryHackMe】Windows Event Logs あんたいとる Windows Event Logs Tryhackme Soc level 1, cyber defense. Learn how to use remina, wevtutil, get. After learning about the tool suite, sysinternals, we are now going to be learning about logs, specifically. Powershell will log operations from the engine, providers, and cmdlets to the windows event log. Endpoint security monitoring, security operations & monitoring. Using the left panel, expand applications and. A write. Windows Event Logs Tryhackme.
From academy.hackthebox.com
Windows Event Logs & Finding Evil Course HTB Academy Windows Event Logs Tryhackme Learn how to use remina, wevtutil, get. A write up for a tryhackme room that involves windows event logs analysis and powershell attacks. Endpoint security monitoring, security operations & monitoring. After learning about the tool suite, sysinternals, we are now going to be learning about logs, specifically. Event log analysis — identifying and interpreting different. Using the left panel, expand. Windows Event Logs Tryhackme.
From www.reddit.com
Windows Event Logs Attack Box asking for login keyring password r Windows Event Logs Tryhackme Event log analysis — identifying and interpreting different. Powershell will log operations from the engine, providers, and cmdlets to the windows event log. Open event viewer either by searching for the program or using eventvwr.msc command within the windows terminal. Endpoint security monitoring, security operations & monitoring. Using the left panel, expand applications and. A write up for a tryhackme. Windows Event Logs Tryhackme.
From motasem-notes.net
Clearing Tracks in Windows TryHackMe Evading Logging & Monitoring Windows Event Logs Tryhackme After learning about the tool suite, sysinternals, we are now going to be learning about logs, specifically. Using the left panel, expand applications and. Learn how to use remina, wevtutil, get. A write up for a tryhackme room that involves windows event logs analysis and powershell attacks. Endpoint security monitoring, security operations & monitoring. Powershell will log operations from the. Windows Event Logs Tryhackme.
From www.youtube.com
Event Log Management in Windows TryHackMe Windows Event Logs YouTube Windows Event Logs Tryhackme After learning about the tool suite, sysinternals, we are now going to be learning about logs, specifically. Learn how to use remina, wevtutil, get. Endpoint security monitoring, security operations & monitoring. Soc level 1, cyber defense. Open event viewer either by searching for the program or using eventvwr.msc command within the windows terminal. Event log analysis — identifying and interpreting. Windows Event Logs Tryhackme.
From thedutchhacker.com
Windows Event Logs on Tryhackme The Dutch Hacker Windows Event Logs Tryhackme Open event viewer either by searching for the program or using eventvwr.msc command within the windows terminal. Learn how to use remina, wevtutil, get. Powershell will log operations from the engine, providers, and cmdlets to the windows event log. Soc level 1, cyber defense. A write up for a tryhackme room that involves windows event logs analysis and powershell attacks.. Windows Event Logs Tryhackme.
From medium.com
Windows Event Logs Room — TryHackMe by Christof Medium Windows Event Logs Tryhackme Endpoint security monitoring, security operations & monitoring. Powershell will log operations from the engine, providers, and cmdlets to the windows event log. A write up for a tryhackme room that involves windows event logs analysis and powershell attacks. Open event viewer either by searching for the program or using eventvwr.msc command within the windows terminal. After learning about the tool. Windows Event Logs Tryhackme.
From www.wikihow.com
How to Check an IIS Event Log on Windows 7 Steps (with Pictures) Windows Event Logs Tryhackme Open event viewer either by searching for the program or using eventvwr.msc command within the windows terminal. After learning about the tool suite, sysinternals, we are now going to be learning about logs, specifically. Endpoint security monitoring, security operations & monitoring. Soc level 1, cyber defense. A write up for a tryhackme room that involves windows event logs analysis and. Windows Event Logs Tryhackme.
From thedutchhacker.com
Windows Event Logs on Tryhackme The Dutch Hacker Windows Event Logs Tryhackme Open event viewer either by searching for the program or using eventvwr.msc command within the windows terminal. Soc level 1, cyber defense. Using the left panel, expand applications and. Learn how to use remina, wevtutil, get. A write up for a tryhackme room that involves windows event logs analysis and powershell attacks. After learning about the tool suite, sysinternals, we. Windows Event Logs Tryhackme.
From medium.com
Windows Event Logs TryHackMe. What are event logs? by Avataris12 Medium Windows Event Logs Tryhackme Soc level 1, cyber defense. Using the left panel, expand applications and. A write up for a tryhackme room that involves windows event logs analysis and powershell attacks. After learning about the tool suite, sysinternals, we are now going to be learning about logs, specifically. Endpoint security monitoring, security operations & monitoring. Learn how to use remina, wevtutil, get. Open. Windows Event Logs Tryhackme.