Store Key Encryption . You can encrypt private keys using a robust encryption algorithm such as aes (advanced encryption standard) and store the encrypted key in a secure location. The android keystore system offers a secure container that shields cryptographic keys from malicious attacks and unauthorized use. Effective encryption key management is essential for safeguarding sensitive data. The android keystore system lets you store cryptographic keys in a container to make them more difficult to extract from the. Learn how to use the android keystore to create and delete key pairs, and use the created keys to encrypt/decrypt blocks of text. If you are planning on storing keys in offline devices/databases, then encrypt the keys using key encryption keys (keks) prior to the export. This protects against offline attacks (unless they capture the key out. Type in the encryption key when you start up, store it in memory.
from www.bogotobogo.com
This protects against offline attacks (unless they capture the key out. Learn how to use the android keystore to create and delete key pairs, and use the created keys to encrypt/decrypt blocks of text. The android keystore system offers a secure container that shields cryptographic keys from malicious attacks and unauthorized use. The android keystore system lets you store cryptographic keys in a container to make them more difficult to extract from the. Type in the encryption key when you start up, store it in memory. You can encrypt private keys using a robust encryption algorithm such as aes (advanced encryption standard) and store the encrypted key in a secure location. If you are planning on storing keys in offline devices/databases, then encrypt the keys using key encryption keys (keks) prior to the export. Effective encryption key management is essential for safeguarding sensitive data.
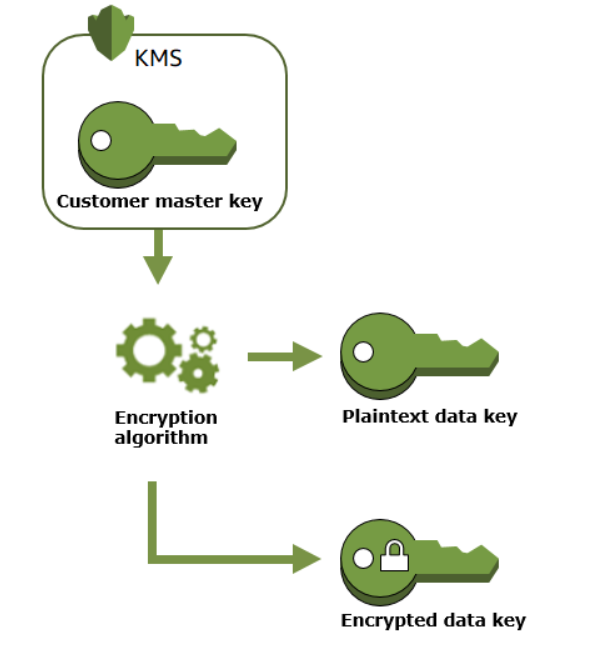
AWSQwikLabs KMS (Key Management Service) 2021
Store Key Encryption If you are planning on storing keys in offline devices/databases, then encrypt the keys using key encryption keys (keks) prior to the export. Effective encryption key management is essential for safeguarding sensitive data. You can encrypt private keys using a robust encryption algorithm such as aes (advanced encryption standard) and store the encrypted key in a secure location. The android keystore system lets you store cryptographic keys in a container to make them more difficult to extract from the. The android keystore system offers a secure container that shields cryptographic keys from malicious attacks and unauthorized use. This protects against offline attacks (unless they capture the key out. If you are planning on storing keys in offline devices/databases, then encrypt the keys using key encryption keys (keks) prior to the export. Type in the encryption key when you start up, store it in memory. Learn how to use the android keystore to create and delete key pairs, and use the created keys to encrypt/decrypt blocks of text.
From arenatoken.pages.dev
Best way to store encryption keys in java Arena Token Store Key Encryption The android keystore system offers a secure container that shields cryptographic keys from malicious attacks and unauthorized use. You can encrypt private keys using a robust encryption algorithm such as aes (advanced encryption standard) and store the encrypted key in a secure location. Learn how to use the android keystore to create and delete key pairs, and use the created. Store Key Encryption.
From www.twilio.com
What is Public Key Cryptography? Twilio Store Key Encryption Type in the encryption key when you start up, store it in memory. Effective encryption key management is essential for safeguarding sensitive data. This protects against offline attacks (unless they capture the key out. The android keystore system offers a secure container that shields cryptographic keys from malicious attacks and unauthorized use. If you are planning on storing keys in. Store Key Encryption.
From jayendrapatil.com
AWS S3 Encryption Store Key Encryption Learn how to use the android keystore to create and delete key pairs, and use the created keys to encrypt/decrypt blocks of text. This protects against offline attacks (unless they capture the key out. Type in the encryption key when you start up, store it in memory. You can encrypt private keys using a robust encryption algorithm such as aes. Store Key Encryption.
From www.thesslstore.com
14 SSH Key Management Best Practices You Need to Know Hashed Out by Store Key Encryption Learn how to use the android keystore to create and delete key pairs, and use the created keys to encrypt/decrypt blocks of text. The android keystore system lets you store cryptographic keys in a container to make them more difficult to extract from the. If you are planning on storing keys in offline devices/databases, then encrypt the keys using key. Store Key Encryption.
From o3schools.com
Ultimate Guide to Understanding What Symmetric Key Cryptography is 2023 Store Key Encryption Effective encryption key management is essential for safeguarding sensitive data. You can encrypt private keys using a robust encryption algorithm such as aes (advanced encryption standard) and store the encrypted key in a secure location. Type in the encryption key when you start up, store it in memory. If you are planning on storing keys in offline devices/databases, then encrypt. Store Key Encryption.
From cheapsslweb.com
Public Key and Private Key Pairs How do they work? Store Key Encryption Type in the encryption key when you start up, store it in memory. This protects against offline attacks (unless they capture the key out. The android keystore system offers a secure container that shields cryptographic keys from malicious attacks and unauthorized use. You can encrypt private keys using a robust encryption algorithm such as aes (advanced encryption standard) and store. Store Key Encryption.
From www.thesslstore.com
Cryptographic Keys 101 What They Are & How They Secure Data Hashed Store Key Encryption You can encrypt private keys using a robust encryption algorithm such as aes (advanced encryption standard) and store the encrypted key in a secure location. Effective encryption key management is essential for safeguarding sensitive data. Type in the encryption key when you start up, store it in memory. If you are planning on storing keys in offline devices/databases, then encrypt. Store Key Encryption.
From learn.microsoft.com
Configure CMK encryption at rest in Azure VMware Solution Azure Store Key Encryption If you are planning on storing keys in offline devices/databases, then encrypt the keys using key encryption keys (keks) prior to the export. Effective encryption key management is essential for safeguarding sensitive data. The android keystore system offers a secure container that shields cryptographic keys from malicious attacks and unauthorized use. The android keystore system lets you store cryptographic keys. Store Key Encryption.
From www.youtube.com
Customer Managed Encryption Keys in GCP Cloud Storage YouTube Store Key Encryption If you are planning on storing keys in offline devices/databases, then encrypt the keys using key encryption keys (keks) prior to the export. The android keystore system lets you store cryptographic keys in a container to make them more difficult to extract from the. Learn how to use the android keystore to create and delete key pairs, and use the. Store Key Encryption.
From research.aimultiple.com
Encryption Key Management Benefits, Tools & Best Practices in 2024 Store Key Encryption The android keystore system offers a secure container that shields cryptographic keys from malicious attacks and unauthorized use. The android keystore system lets you store cryptographic keys in a container to make them more difficult to extract from the. You can encrypt private keys using a robust encryption algorithm such as aes (advanced encryption standard) and store the encrypted key. Store Key Encryption.
From sectigostore.com
What Is Asymmetric Encryption & How Does It Work? InfoSec Insights Store Key Encryption Type in the encryption key when you start up, store it in memory. Effective encryption key management is essential for safeguarding sensitive data. The android keystore system lets you store cryptographic keys in a container to make them more difficult to extract from the. This protects against offline attacks (unless they capture the key out. You can encrypt private keys. Store Key Encryption.
From auth0.com
What's the Difference Between Encryption, Hashing, Encoding and Store Key Encryption Learn how to use the android keystore to create and delete key pairs, and use the created keys to encrypt/decrypt blocks of text. Type in the encryption key when you start up, store it in memory. The android keystore system lets you store cryptographic keys in a container to make them more difficult to extract from the. Effective encryption key. Store Key Encryption.
From android-developers.googleblog.com
Android Developers Blog New Keystore features keep your slice of Store Key Encryption This protects against offline attacks (unless they capture the key out. Effective encryption key management is essential for safeguarding sensitive data. The android keystore system lets you store cryptographic keys in a container to make them more difficult to extract from the. The android keystore system offers a secure container that shields cryptographic keys from malicious attacks and unauthorized use.. Store Key Encryption.
From learn.g2.com
How Public Key Encryption Ensures Data Integrity Store Key Encryption This protects against offline attacks (unless they capture the key out. If you are planning on storing keys in offline devices/databases, then encrypt the keys using key encryption keys (keks) prior to the export. Type in the encryption key when you start up, store it in memory. You can encrypt private keys using a robust encryption algorithm such as aes. Store Key Encryption.
From sectigo.com
Public Key vs Private Key Public Key Cryptography Explained Sectigo Store Key Encryption The android keystore system lets you store cryptographic keys in a container to make them more difficult to extract from the. This protects against offline attacks (unless they capture the key out. The android keystore system offers a secure container that shields cryptographic keys from malicious attacks and unauthorized use. Effective encryption key management is essential for safeguarding sensitive data.. Store Key Encryption.
From jayendrapatil.com
AWS S3 Encryption Store Key Encryption Effective encryption key management is essential for safeguarding sensitive data. Type in the encryption key when you start up, store it in memory. The android keystore system offers a secure container that shields cryptographic keys from malicious attacks and unauthorized use. This protects against offline attacks (unless they capture the key out. You can encrypt private keys using a robust. Store Key Encryption.
From www.poweradmin.com
A Quick Guide to Encrypted Messaging Network Wrangler Tech Blog Store Key Encryption If you are planning on storing keys in offline devices/databases, then encrypt the keys using key encryption keys (keks) prior to the export. This protects against offline attacks (unless they capture the key out. The android keystore system lets you store cryptographic keys in a container to make them more difficult to extract from the. Effective encryption key management is. Store Key Encryption.
From www.sandfield.co.nz
Cryptography 101 Sandfield Store Key Encryption You can encrypt private keys using a robust encryption algorithm such as aes (advanced encryption standard) and store the encrypted key in a secure location. Effective encryption key management is essential for safeguarding sensitive data. Type in the encryption key when you start up, store it in memory. This protects against offline attacks (unless they capture the key out. The. Store Key Encryption.
From www.bogotobogo.com
AWSQwikLabs KMS (Key Management Service) 2021 Store Key Encryption You can encrypt private keys using a robust encryption algorithm such as aes (advanced encryption standard) and store the encrypted key in a secure location. If you are planning on storing keys in offline devices/databases, then encrypt the keys using key encryption keys (keks) prior to the export. This protects against offline attacks (unless they capture the key out. Type. Store Key Encryption.
From kig.re
Dead Simple Encryption with Sym Store Key Encryption The android keystore system offers a secure container that shields cryptographic keys from malicious attacks and unauthorized use. Type in the encryption key when you start up, store it in memory. The android keystore system lets you store cryptographic keys in a container to make them more difficult to extract from the. You can encrypt private keys using a robust. Store Key Encryption.
From www.thesslstore.com
Your Guide to How PKI Works & Secures Your Organization Hashed Out by Store Key Encryption If you are planning on storing keys in offline devices/databases, then encrypt the keys using key encryption keys (keks) prior to the export. Type in the encryption key when you start up, store it in memory. The android keystore system offers a secure container that shields cryptographic keys from malicious attacks and unauthorized use. Effective encryption key management is essential. Store Key Encryption.
From firebasetutorials.com
Firebase Encryption 5 Ways to Protect Your App Data Firebase Tutorials Store Key Encryption The android keystore system offers a secure container that shields cryptographic keys from malicious attacks and unauthorized use. Type in the encryption key when you start up, store it in memory. You can encrypt private keys using a robust encryption algorithm such as aes (advanced encryption standard) and store the encrypted key in a secure location. This protects against offline. Store Key Encryption.
From www.thesslstore.com
12 Enterprise Encryption Key Management Best Practices Hashed Out by Store Key Encryption You can encrypt private keys using a robust encryption algorithm such as aes (advanced encryption standard) and store the encrypted key in a secure location. The android keystore system lets you store cryptographic keys in a container to make them more difficult to extract from the. Effective encryption key management is essential for safeguarding sensitive data. The android keystore system. Store Key Encryption.
From www.primefactors.com
Encryption Key Management System Prime Factors Store Key Encryption Type in the encryption key when you start up, store it in memory. The android keystore system offers a secure container that shields cryptographic keys from malicious attacks and unauthorized use. Learn how to use the android keystore to create and delete key pairs, and use the created keys to encrypt/decrypt blocks of text. This protects against offline attacks (unless. Store Key Encryption.
From www.thesslstore.com
How Public Private Key Pairs Work in Cryptography 5 Common Examples Store Key Encryption The android keystore system lets you store cryptographic keys in a container to make them more difficult to extract from the. The android keystore system offers a secure container that shields cryptographic keys from malicious attacks and unauthorized use. Learn how to use the android keystore to create and delete key pairs, and use the created keys to encrypt/decrypt blocks. Store Key Encryption.
From securityboulevard.com
12 Enterprise Encryption Key Management Best Practices Security Boulevard Store Key Encryption If you are planning on storing keys in offline devices/databases, then encrypt the keys using key encryption keys (keks) prior to the export. The android keystore system lets you store cryptographic keys in a container to make them more difficult to extract from the. Learn how to use the android keystore to create and delete key pairs, and use the. Store Key Encryption.
From akropolis.pages.dev
How to store encryption keys in android Akropolis Store Key Encryption Type in the encryption key when you start up, store it in memory. Learn how to use the android keystore to create and delete key pairs, and use the created keys to encrypt/decrypt blocks of text. The android keystore system offers a secure container that shields cryptographic keys from malicious attacks and unauthorized use. Effective encryption key management is essential. Store Key Encryption.
From www.researchgate.net
The procedure of key policy attributebased encryption (KPABE Store Key Encryption Effective encryption key management is essential for safeguarding sensitive data. Learn how to use the android keystore to create and delete key pairs, and use the created keys to encrypt/decrypt blocks of text. The android keystore system lets you store cryptographic keys in a container to make them more difficult to extract from the. This protects against offline attacks (unless. Store Key Encryption.
From securityboulevard.com
12 Enterprise Encryption Key Management Best Practices Security Boulevard Store Key Encryption If you are planning on storing keys in offline devices/databases, then encrypt the keys using key encryption keys (keks) prior to the export. The android keystore system lets you store cryptographic keys in a container to make them more difficult to extract from the. Effective encryption key management is essential for safeguarding sensitive data. You can encrypt private keys using. Store Key Encryption.
From shibainu.pages.dev
How to store encryption keys securely Shiba Inu Store Key Encryption The android keystore system offers a secure container that shields cryptographic keys from malicious attacks and unauthorized use. You can encrypt private keys using a robust encryption algorithm such as aes (advanced encryption standard) and store the encrypted key in a secure location. If you are planning on storing keys in offline devices/databases, then encrypt the keys using key encryption. Store Key Encryption.
From wyzguyscybersecurity.com
Public Key Encryption Explained WyzGuys Cybersecurity Store Key Encryption This protects against offline attacks (unless they capture the key out. The android keystore system lets you store cryptographic keys in a container to make them more difficult to extract from the. If you are planning on storing keys in offline devices/databases, then encrypt the keys using key encryption keys (keks) prior to the export. Type in the encryption key. Store Key Encryption.
From freelearningtech.in
What is CRYPTOGRAPHY and Types or Encryption? Free Learning Tech Store Key Encryption If you are planning on storing keys in offline devices/databases, then encrypt the keys using key encryption keys (keks) prior to the export. The android keystore system offers a secure container that shields cryptographic keys from malicious attacks and unauthorized use. Learn how to use the android keystore to create and delete key pairs, and use the created keys to. Store Key Encryption.
From help.mypurecloud.com
Recording encryption key overview Genesys Cloud Resource Center Store Key Encryption This protects against offline attacks (unless they capture the key out. If you are planning on storing keys in offline devices/databases, then encrypt the keys using key encryption keys (keks) prior to the export. The android keystore system lets you store cryptographic keys in a container to make them more difficult to extract from the. Type in the encryption key. Store Key Encryption.
From docs.aws.amazon.com
External key stores AWS Key Management Service Store Key Encryption Learn how to use the android keystore to create and delete key pairs, and use the created keys to encrypt/decrypt blocks of text. The android keystore system offers a secure container that shields cryptographic keys from malicious attacks and unauthorized use. This protects against offline attacks (unless they capture the key out. You can encrypt private keys using a robust. Store Key Encryption.