Top Information Security Attack Vectors . By examining threat actors and their behaviors, we’re able to identify the most common attack vectors and recommend strategies for. In this blog post, we’ll take a look at 12 common attack vectors that threat actors use in an attempt to infiltrate their target. Cyberattack vectors (also known as threat vectors) are pathways through which cybercriminals gain unauthorized access to an. An attack vector is the method or combination of methods that cybercriminals use to breach or infiltrate a victim’s network. Attack vectors (also called threat vectors) are points of vulnerability unauthorized users can exploit to enter it systems. Attack vectors empower programmers to misuse framework weaknesses, including the human component.
from expel.com
An attack vector is the method or combination of methods that cybercriminals use to breach or infiltrate a victim’s network. Cyberattack vectors (also known as threat vectors) are pathways through which cybercriminals gain unauthorized access to an. Attack vectors empower programmers to misuse framework weaknesses, including the human component. In this blog post, we’ll take a look at 12 common attack vectors that threat actors use in an attempt to infiltrate their target. By examining threat actors and their behaviors, we’re able to identify the most common attack vectors and recommend strategies for. Attack vectors (also called threat vectors) are points of vulnerability unauthorized users can exploit to enter it systems.
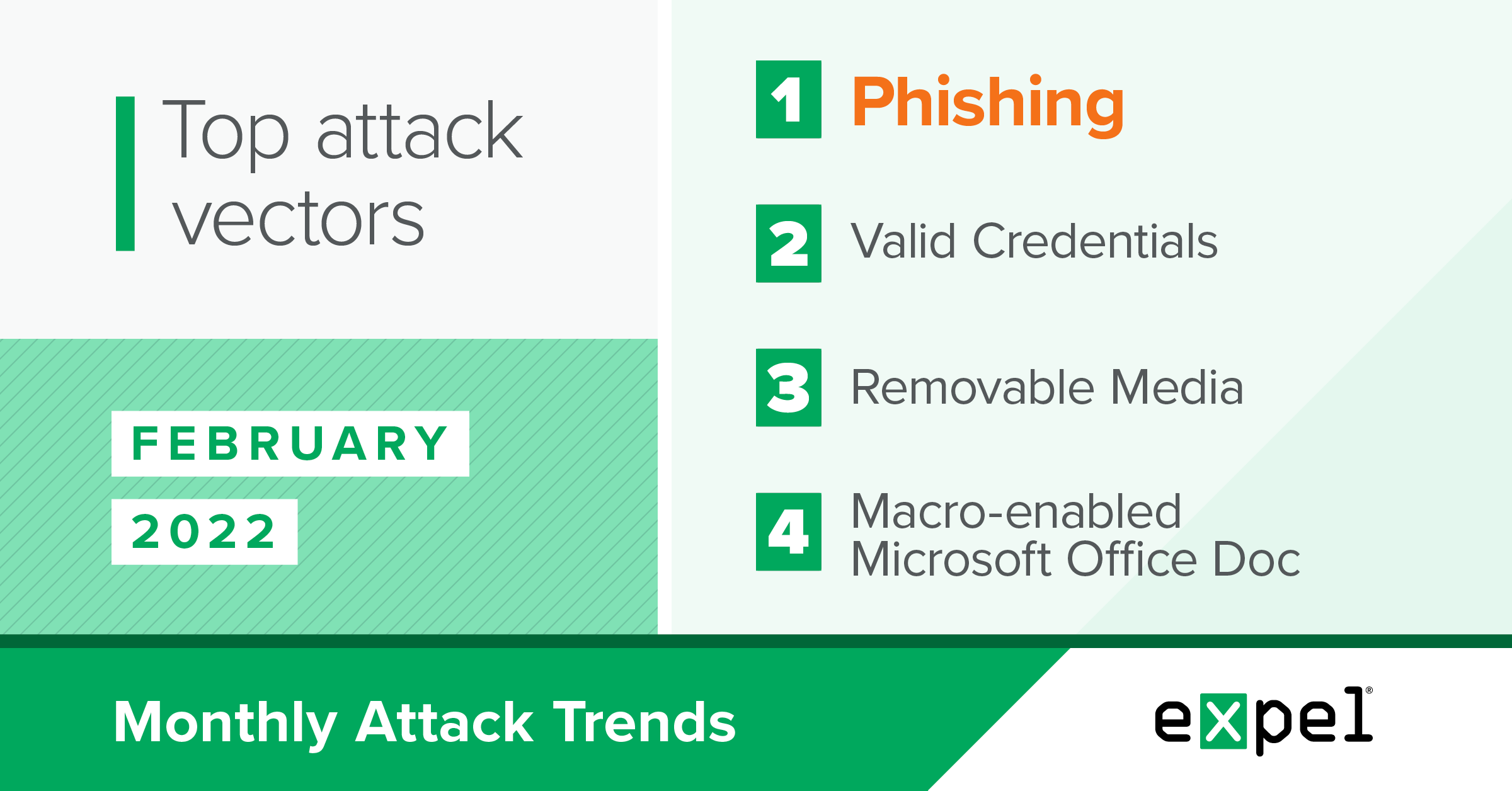
Top Attack Vectors February 2022 Expel
Top Information Security Attack Vectors Cyberattack vectors (also known as threat vectors) are pathways through which cybercriminals gain unauthorized access to an. Attack vectors empower programmers to misuse framework weaknesses, including the human component. Attack vectors (also called threat vectors) are points of vulnerability unauthorized users can exploit to enter it systems. By examining threat actors and their behaviors, we’re able to identify the most common attack vectors and recommend strategies for. An attack vector is the method or combination of methods that cybercriminals use to breach or infiltrate a victim’s network. In this blog post, we’ll take a look at 12 common attack vectors that threat actors use in an attempt to infiltrate their target. Cyberattack vectors (also known as threat vectors) are pathways through which cybercriminals gain unauthorized access to an.
From www.vecteezy.com
Cyber Security Illustration 1397516 Vector Art at Vecteezy Top Information Security Attack Vectors By examining threat actors and their behaviors, we’re able to identify the most common attack vectors and recommend strategies for. Attack vectors (also called threat vectors) are points of vulnerability unauthorized users can exploit to enter it systems. In this blog post, we’ll take a look at 12 common attack vectors that threat actors use in an attempt to infiltrate. Top Information Security Attack Vectors.
From www.youtube.com
List of Top Information Security Certifications in 2023 Top Top Information Security Attack Vectors Attack vectors (also called threat vectors) are points of vulnerability unauthorized users can exploit to enter it systems. In this blog post, we’ll take a look at 12 common attack vectors that threat actors use in an attempt to infiltrate their target. Attack vectors empower programmers to misuse framework weaknesses, including the human component. By examining threat actors and their. Top Information Security Attack Vectors.
From assignmenthelp4me.com
A comprehensive study of Cyber Security and its types Top Information Security Attack Vectors In this blog post, we’ll take a look at 12 common attack vectors that threat actors use in an attempt to infiltrate their target. An attack vector is the method or combination of methods that cybercriminals use to breach or infiltrate a victim’s network. Attack vectors (also called threat vectors) are points of vulnerability unauthorized users can exploit to enter. Top Information Security Attack Vectors.
From www.gov.uk
[Withdrawn] Common Cyber Attacks Summary GOV.UK Top Information Security Attack Vectors Attack vectors (also called threat vectors) are points of vulnerability unauthorized users can exploit to enter it systems. By examining threat actors and their behaviors, we’re able to identify the most common attack vectors and recommend strategies for. Cyberattack vectors (also known as threat vectors) are pathways through which cybercriminals gain unauthorized access to an. Attack vectors empower programmers to. Top Information Security Attack Vectors.
From www.balbix.com
8 Common Types of Cyber Attack Vectors and How to Avoid Them Balbix Top Information Security Attack Vectors By examining threat actors and their behaviors, we’re able to identify the most common attack vectors and recommend strategies for. Cyberattack vectors (also known as threat vectors) are pathways through which cybercriminals gain unauthorized access to an. In this blog post, we’ll take a look at 12 common attack vectors that threat actors use in an attempt to infiltrate their. Top Information Security Attack Vectors.
From www.dnsstuff.com
Top 6 Common Types of Cyberattacks DNSstuff Top Information Security Attack Vectors Attack vectors (also called threat vectors) are points of vulnerability unauthorized users can exploit to enter it systems. Attack vectors empower programmers to misuse framework weaknesses, including the human component. By examining threat actors and their behaviors, we’re able to identify the most common attack vectors and recommend strategies for. Cyberattack vectors (also known as threat vectors) are pathways through. Top Information Security Attack Vectors.
From www.infosectrain.com
Common Security Attacks in the OSI Layer Model Top Information Security Attack Vectors An attack vector is the method or combination of methods that cybercriminals use to breach or infiltrate a victim’s network. By examining threat actors and their behaviors, we’re able to identify the most common attack vectors and recommend strategies for. Attack vectors empower programmers to misuse framework weaknesses, including the human component. In this blog post, we’ll take a look. Top Information Security Attack Vectors.
From tech-skills-world.blogspot.com
Technically Technical Information Security Threats and Attack Vectors Top Information Security Attack Vectors Attack vectors (also called threat vectors) are points of vulnerability unauthorized users can exploit to enter it systems. Attack vectors empower programmers to misuse framework weaknesses, including the human component. In this blog post, we’ll take a look at 12 common attack vectors that threat actors use in an attempt to infiltrate their target. An attack vector is the method. Top Information Security Attack Vectors.
From www.akamai.com
What Is Cybersecurity or Cyber Security? Akamai Top Information Security Attack Vectors An attack vector is the method or combination of methods that cybercriminals use to breach or infiltrate a victim’s network. Attack vectors empower programmers to misuse framework weaknesses, including the human component. Cyberattack vectors (also known as threat vectors) are pathways through which cybercriminals gain unauthorized access to an. In this blog post, we’ll take a look at 12 common. Top Information Security Attack Vectors.
From www.computertechreviews.com
What is the Attack Vector? Definition, Risks, and More Top Information Security Attack Vectors An attack vector is the method or combination of methods that cybercriminals use to breach or infiltrate a victim’s network. By examining threat actors and their behaviors, we’re able to identify the most common attack vectors and recommend strategies for. Attack vectors (also called threat vectors) are points of vulnerability unauthorized users can exploit to enter it systems. Cyberattack vectors. Top Information Security Attack Vectors.
From blog.quest.com
Attack vector What is it and how to defend against it Top Information Security Attack Vectors Cyberattack vectors (also known as threat vectors) are pathways through which cybercriminals gain unauthorized access to an. By examining threat actors and their behaviors, we’re able to identify the most common attack vectors and recommend strategies for. An attack vector is the method or combination of methods that cybercriminals use to breach or infiltrate a victim’s network. Attack vectors (also. Top Information Security Attack Vectors.
From support.aiesec.org
Cyber Security Threats and Attacks AIESEC Help Center Top Information Security Attack Vectors Cyberattack vectors (also known as threat vectors) are pathways through which cybercriminals gain unauthorized access to an. In this blog post, we’ll take a look at 12 common attack vectors that threat actors use in an attempt to infiltrate their target. Attack vectors empower programmers to misuse framework weaknesses, including the human component. Attack vectors (also called threat vectors) are. Top Information Security Attack Vectors.
From www.insightsonindia.com
Meaning and Types of Cybersecurity Threats INSIGHTS IAS Simplifying Top Information Security Attack Vectors By examining threat actors and their behaviors, we’re able to identify the most common attack vectors and recommend strategies for. In this blog post, we’ll take a look at 12 common attack vectors that threat actors use in an attempt to infiltrate their target. Attack vectors (also called threat vectors) are points of vulnerability unauthorized users can exploit to enter. Top Information Security Attack Vectors.
From www.slideshare.net
New Threat Vectors Source Immuniweb, Top Information Security Attack Vectors An attack vector is the method or combination of methods that cybercriminals use to breach or infiltrate a victim’s network. Attack vectors empower programmers to misuse framework weaknesses, including the human component. Attack vectors (also called threat vectors) are points of vulnerability unauthorized users can exploit to enter it systems. In this blog post, we’ll take a look at 12. Top Information Security Attack Vectors.
From www.linkedin.com
Security Attack Vectors (SAV) Top Information Security Attack Vectors An attack vector is the method or combination of methods that cybercriminals use to breach or infiltrate a victim’s network. By examining threat actors and their behaviors, we’re able to identify the most common attack vectors and recommend strategies for. Attack vectors (also called threat vectors) are points of vulnerability unauthorized users can exploit to enter it systems. Cyberattack vectors. Top Information Security Attack Vectors.
From expel.com
Top Attack Vectors February 2022 Expel Top Information Security Attack Vectors By examining threat actors and their behaviors, we’re able to identify the most common attack vectors and recommend strategies for. Attack vectors (also called threat vectors) are points of vulnerability unauthorized users can exploit to enter it systems. In this blog post, we’ll take a look at 12 common attack vectors that threat actors use in an attempt to infiltrate. Top Information Security Attack Vectors.
From blog.invgate.com
14 Most Common Types of Cyber Attacks (and How to Prevent Them) Top Information Security Attack Vectors Attack vectors empower programmers to misuse framework weaknesses, including the human component. In this blog post, we’ll take a look at 12 common attack vectors that threat actors use in an attempt to infiltrate their target. Attack vectors (also called threat vectors) are points of vulnerability unauthorized users can exploit to enter it systems. Cyberattack vectors (also known as threat. Top Information Security Attack Vectors.
From eclypsium.com
The Top 5 Firmware Attack Vectors Eclypsium Supply Chain Security Top Information Security Attack Vectors By examining threat actors and their behaviors, we’re able to identify the most common attack vectors and recommend strategies for. In this blog post, we’ll take a look at 12 common attack vectors that threat actors use in an attempt to infiltrate their target. Cyberattack vectors (also known as threat vectors) are pathways through which cybercriminals gain unauthorized access to. Top Information Security Attack Vectors.
From securityboulevard.com
The InfoSec Guide to Attack Vectors Security Boulevard Top Information Security Attack Vectors Attack vectors (also called threat vectors) are points of vulnerability unauthorized users can exploit to enter it systems. Attack vectors empower programmers to misuse framework weaknesses, including the human component. An attack vector is the method or combination of methods that cybercriminals use to breach or infiltrate a victim’s network. By examining threat actors and their behaviors, we’re able to. Top Information Security Attack Vectors.
From www.linkedin.com
Most Common Types of Cyber Attacks on Small Businesses Top Information Security Attack Vectors An attack vector is the method or combination of methods that cybercriminals use to breach or infiltrate a victim’s network. Cyberattack vectors (also known as threat vectors) are pathways through which cybercriminals gain unauthorized access to an. By examining threat actors and their behaviors, we’re able to identify the most common attack vectors and recommend strategies for. Attack vectors empower. Top Information Security Attack Vectors.
From phishgrid.com
Attack Vector vs Attack Surface 2024 PhishGrid Top Information Security Attack Vectors Attack vectors (also called threat vectors) are points of vulnerability unauthorized users can exploit to enter it systems. In this blog post, we’ll take a look at 12 common attack vectors that threat actors use in an attempt to infiltrate their target. An attack vector is the method or combination of methods that cybercriminals use to breach or infiltrate a. Top Information Security Attack Vectors.
From cyvatar.ai
What is a cyberattack vector? Avoid these 10 common attack vectors Top Information Security Attack Vectors In this blog post, we’ll take a look at 12 common attack vectors that threat actors use in an attempt to infiltrate their target. Attack vectors empower programmers to misuse framework weaknesses, including the human component. By examining threat actors and their behaviors, we’re able to identify the most common attack vectors and recommend strategies for. Cyberattack vectors (also known. Top Information Security Attack Vectors.
From www.shutterstock.com
Cyber Security Infographic Stock Vector (Royalty Free) 783784327 Top Information Security Attack Vectors An attack vector is the method or combination of methods that cybercriminals use to breach or infiltrate a victim’s network. Attack vectors (also called threat vectors) are points of vulnerability unauthorized users can exploit to enter it systems. By examining threat actors and their behaviors, we’re able to identify the most common attack vectors and recommend strategies for. Attack vectors. Top Information Security Attack Vectors.
From medium.com
Top Information Security Attack Vectors by Tirth Shah Medium Top Information Security Attack Vectors An attack vector is the method or combination of methods that cybercriminals use to breach or infiltrate a victim’s network. By examining threat actors and their behaviors, we’re able to identify the most common attack vectors and recommend strategies for. In this blog post, we’ll take a look at 12 common attack vectors that threat actors use in an attempt. Top Information Security Attack Vectors.
From www.paubox.com
What is a threat vector and why is it important to define Top Information Security Attack Vectors Attack vectors empower programmers to misuse framework weaknesses, including the human component. In this blog post, we’ll take a look at 12 common attack vectors that threat actors use in an attempt to infiltrate their target. By examining threat actors and their behaviors, we’re able to identify the most common attack vectors and recommend strategies for. An attack vector is. Top Information Security Attack Vectors.
From expel.com
Top Attack Vectors January 2022 Expel Top Information Security Attack Vectors In this blog post, we’ll take a look at 12 common attack vectors that threat actors use in an attempt to infiltrate their target. Attack vectors empower programmers to misuse framework weaknesses, including the human component. Attack vectors (also called threat vectors) are points of vulnerability unauthorized users can exploit to enter it systems. An attack vector is the method. Top Information Security Attack Vectors.
From www.freepik.com
Premium Vector Protect against cyber attacks infographic Top Information Security Attack Vectors Cyberattack vectors (also known as threat vectors) are pathways through which cybercriminals gain unauthorized access to an. Attack vectors (also called threat vectors) are points of vulnerability unauthorized users can exploit to enter it systems. By examining threat actors and their behaviors, we’re able to identify the most common attack vectors and recommend strategies for. In this blog post, we’ll. Top Information Security Attack Vectors.
From detectify.com
Attack Vector Ultimate Guide Detectify Top Information Security Attack Vectors Attack vectors (also called threat vectors) are points of vulnerability unauthorized users can exploit to enter it systems. In this blog post, we’ll take a look at 12 common attack vectors that threat actors use in an attempt to infiltrate their target. Cyberattack vectors (also known as threat vectors) are pathways through which cybercriminals gain unauthorized access to an. Attack. Top Information Security Attack Vectors.
From expel.com
Top Attack Vectors February 2022 Expel Top Information Security Attack Vectors Attack vectors empower programmers to misuse framework weaknesses, including the human component. By examining threat actors and their behaviors, we’re able to identify the most common attack vectors and recommend strategies for. In this blog post, we’ll take a look at 12 common attack vectors that threat actors use in an attempt to infiltrate their target. Cyberattack vectors (also known. Top Information Security Attack Vectors.
From uxdx.com
How Dashlane protects itself against the 5 common security attack Top Information Security Attack Vectors By examining threat actors and their behaviors, we’re able to identify the most common attack vectors and recommend strategies for. In this blog post, we’ll take a look at 12 common attack vectors that threat actors use in an attempt to infiltrate their target. Attack vectors (also called threat vectors) are points of vulnerability unauthorized users can exploit to enter. Top Information Security Attack Vectors.
From www.healthcareitnews.com
Infographic Top 10 cybersecurity threats of the future Healthcare IT Top Information Security Attack Vectors Cyberattack vectors (also known as threat vectors) are pathways through which cybercriminals gain unauthorized access to an. In this blog post, we’ll take a look at 12 common attack vectors that threat actors use in an attempt to infiltrate their target. Attack vectors empower programmers to misuse framework weaknesses, including the human component. By examining threat actors and their behaviors,. Top Information Security Attack Vectors.
From www.trendmicro.com
7 Cyber Attack Vectors & How to Protect Them Trend Micro (US) Top Information Security Attack Vectors In this blog post, we’ll take a look at 12 common attack vectors that threat actors use in an attempt to infiltrate their target. Attack vectors empower programmers to misuse framework weaknesses, including the human component. By examining threat actors and their behaviors, we’re able to identify the most common attack vectors and recommend strategies for. An attack vector is. Top Information Security Attack Vectors.
From www.youtube.com
15Get To Know Attack Vectors And Types YouTube Top Information Security Attack Vectors An attack vector is the method or combination of methods that cybercriminals use to breach or infiltrate a victim’s network. Attack vectors (also called threat vectors) are points of vulnerability unauthorized users can exploit to enter it systems. By examining threat actors and their behaviors, we’re able to identify the most common attack vectors and recommend strategies for. Cyberattack vectors. Top Information Security Attack Vectors.
From nerv0.blogspot.com
tester diary. Top information security attack vectors Top Information Security Attack Vectors Cyberattack vectors (also known as threat vectors) are pathways through which cybercriminals gain unauthorized access to an. An attack vector is the method or combination of methods that cybercriminals use to breach or infiltrate a victim’s network. By examining threat actors and their behaviors, we’re able to identify the most common attack vectors and recommend strategies for. Attack vectors empower. Top Information Security Attack Vectors.
From www.wallarm.com
What is an Attack Vector? Examples, Definition, Meaning ⚠️ Top Information Security Attack Vectors An attack vector is the method or combination of methods that cybercriminals use to breach or infiltrate a victim’s network. Cyberattack vectors (also known as threat vectors) are pathways through which cybercriminals gain unauthorized access to an. In this blog post, we’ll take a look at 12 common attack vectors that threat actors use in an attempt to infiltrate their. Top Information Security Attack Vectors.