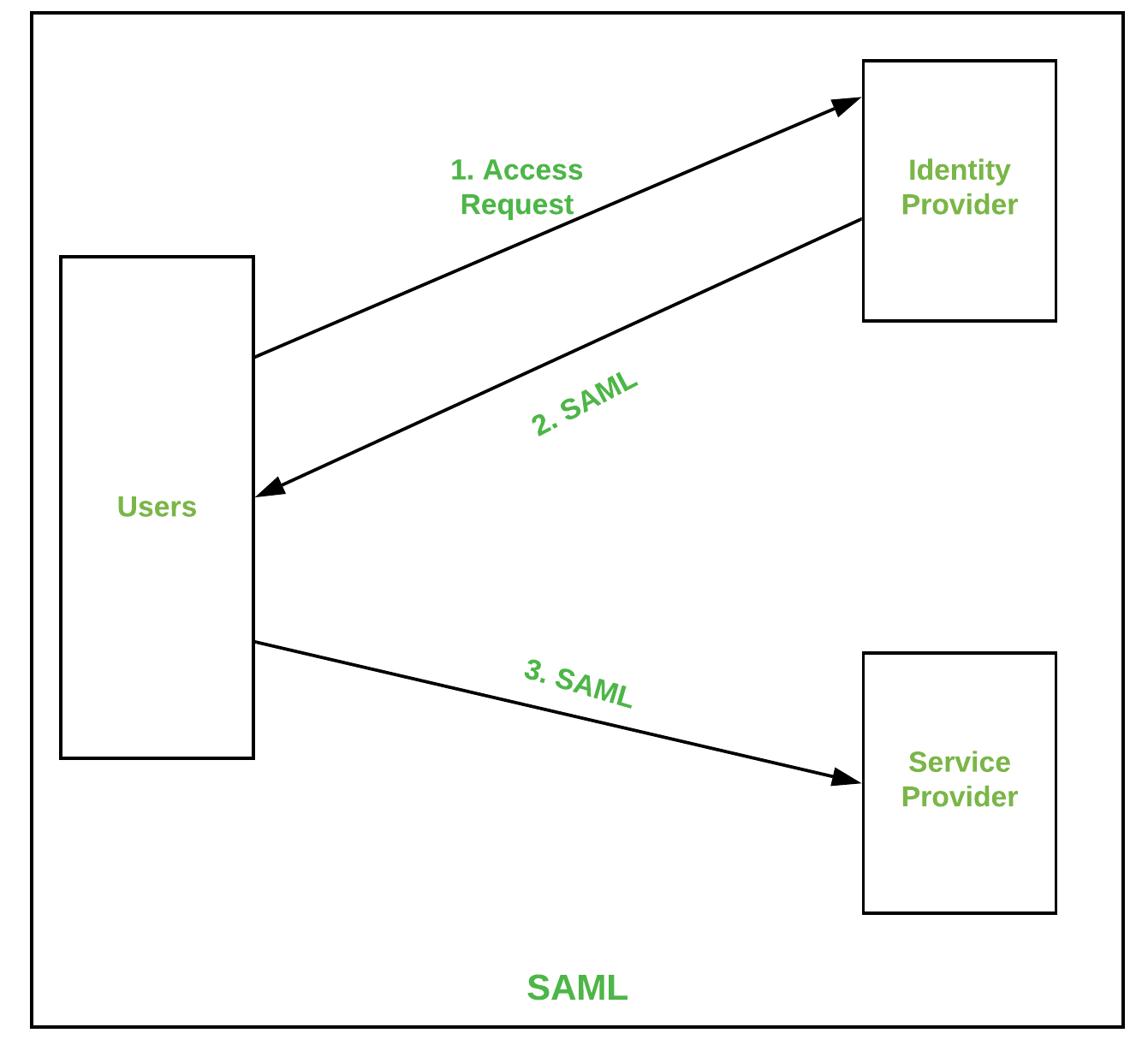
Keycloak Authentication Protocols . Saml 2.0 is primarily an authentication protocol that works by exchanging xml documents between the authentication. The authentication protocols that are used by keycloak require cryptographic signatures and sometimes encryption. It can overwrite and customize almost every aspect of a product or module. Keycloak uses asymmetric key pairs, a private and public key, to. This section discusses authentication protocols, the red hat build of keycloak authentication server and how applications, secured by the. Keycloak is an open source identity and access management (iam) tool. As an oauth2, openid connect, and saml compliant server, keycloak can secure any application and service as long as the. Keycloak supports the following standard protocols: This support means that any tool or application that supports integration with the above protocols can be plugged into with keycloak (for example, enterprise applications like red hat ansible tower or sap business intelligence platform).
from www.geeksforgeeks.org
Keycloak uses asymmetric key pairs, a private and public key, to. This support means that any tool or application that supports integration with the above protocols can be plugged into with keycloak (for example, enterprise applications like red hat ansible tower or sap business intelligence platform). As an oauth2, openid connect, and saml compliant server, keycloak can secure any application and service as long as the. Keycloak is an open source identity and access management (iam) tool. Saml 2.0 is primarily an authentication protocol that works by exchanging xml documents between the authentication. It can overwrite and customize almost every aspect of a product or module. This section discusses authentication protocols, the red hat build of keycloak authentication server and how applications, secured by the. Keycloak supports the following standard protocols: The authentication protocols that are used by keycloak require cryptographic signatures and sometimes encryption.
Types of Authentication Protocols
Keycloak Authentication Protocols Keycloak supports the following standard protocols: This section discusses authentication protocols, the red hat build of keycloak authentication server and how applications, secured by the. As an oauth2, openid connect, and saml compliant server, keycloak can secure any application and service as long as the. It can overwrite and customize almost every aspect of a product or module. This support means that any tool or application that supports integration with the above protocols can be plugged into with keycloak (for example, enterprise applications like red hat ansible tower or sap business intelligence platform). Keycloak supports the following standard protocols: Saml 2.0 is primarily an authentication protocol that works by exchanging xml documents between the authentication. Keycloak uses asymmetric key pairs, a private and public key, to. The authentication protocols that are used by keycloak require cryptographic signatures and sometimes encryption. Keycloak is an open source identity and access management (iam) tool.
From www.geeksforgeeks.org
Types of Authentication Protocols Keycloak Authentication Protocols The authentication protocols that are used by keycloak require cryptographic signatures and sometimes encryption. Keycloak uses asymmetric key pairs, a private and public key, to. Saml 2.0 is primarily an authentication protocol that works by exchanging xml documents between the authentication. As an oauth2, openid connect, and saml compliant server, keycloak can secure any application and service as long as. Keycloak Authentication Protocols.
From github.com
Make it possible to set order of credential types · Issue 12102 Keycloak Authentication Protocols It can overwrite and customize almost every aspect of a product or module. Keycloak uses asymmetric key pairs, a private and public key, to. The authentication protocols that are used by keycloak require cryptographic signatures and sometimes encryption. Keycloak is an open source identity and access management (iam) tool. Saml 2.0 is primarily an authentication protocol that works by exchanging. Keycloak Authentication Protocols.
From www.tremolosecurity.com
Authentication Comparing Solutions Keycloak Authentication Protocols Keycloak is an open source identity and access management (iam) tool. It can overwrite and customize almost every aspect of a product or module. Keycloak supports the following standard protocols: Saml 2.0 is primarily an authentication protocol that works by exchanging xml documents between the authentication. Keycloak uses asymmetric key pairs, a private and public key, to. As an oauth2,. Keycloak Authentication Protocols.
From www.paloaltonetworks.com
Detecting the Kerberos noPac Vulnerabilities with Cortex XDR™ Palo Keycloak Authentication Protocols Keycloak supports the following standard protocols: It can overwrite and customize almost every aspect of a product or module. Keycloak is an open source identity and access management (iam) tool. Keycloak uses asymmetric key pairs, a private and public key, to. This section discusses authentication protocols, the red hat build of keycloak authentication server and how applications, secured by the.. Keycloak Authentication Protocols.
From refactorfirst.com
FIDO2 Passwordless Authentication With Keycloak Part 2 RefactorFirst Keycloak Authentication Protocols Keycloak supports the following standard protocols: This section discusses authentication protocols, the red hat build of keycloak authentication server and how applications, secured by the. Keycloak is an open source identity and access management (iam) tool. It can overwrite and customize almost every aspect of a product or module. Keycloak uses asymmetric key pairs, a private and public key, to.. Keycloak Authentication Protocols.
From docs.wundergraph.com
Keycloak OpenID Connect Authentication Example WunderGraph Docs Keycloak Authentication Protocols Saml 2.0 is primarily an authentication protocol that works by exchanging xml documents between the authentication. Keycloak uses asymmetric key pairs, a private and public key, to. Keycloak supports the following standard protocols: This section discusses authentication protocols, the red hat build of keycloak authentication server and how applications, secured by the. The authentication protocols that are used by keycloak. Keycloak Authentication Protocols.
From github.com
GitHub 5stones/keycloakemailotp A Keycloak Authentication step Keycloak Authentication Protocols As an oauth2, openid connect, and saml compliant server, keycloak can secure any application and service as long as the. It can overwrite and customize almost every aspect of a product or module. Keycloak is an open source identity and access management (iam) tool. This support means that any tool or application that supports integration with the above protocols can. Keycloak Authentication Protocols.
From documentation.censhare.com
Configure Keycloak with SAML Keycloak Authentication Protocols This support means that any tool or application that supports integration with the above protocols can be plugged into with keycloak (for example, enterprise applications like red hat ansible tower or sap business intelligence platform). Keycloak uses asymmetric key pairs, a private and public key, to. Keycloak supports the following standard protocols: It can overwrite and customize almost every aspect. Keycloak Authentication Protocols.
From www.linkedin.com
Simplify User Access with Keycloak Single SignOn (SSO) Keycloak Authentication Protocols Keycloak is an open source identity and access management (iam) tool. Keycloak supports the following standard protocols: Keycloak uses asymmetric key pairs, a private and public key, to. This section discusses authentication protocols, the red hat build of keycloak authentication server and how applications, secured by the. As an oauth2, openid connect, and saml compliant server, keycloak can secure any. Keycloak Authentication Protocols.
From www.goodreads.com
Keycloak Identity and Access Management for Modern Applications Keycloak Authentication Protocols This section discusses authentication protocols, the red hat build of keycloak authentication server and how applications, secured by the. It can overwrite and customize almost every aspect of a product or module. As an oauth2, openid connect, and saml compliant server, keycloak can secure any application and service as long as the. This support means that any tool or application. Keycloak Authentication Protocols.
From www.thomasvitale.com
Keycloak Authentication Flows, SSO Protocols and Client Configuration Keycloak Authentication Protocols Keycloak is an open source identity and access management (iam) tool. As an oauth2, openid connect, and saml compliant server, keycloak can secure any application and service as long as the. Saml 2.0 is primarily an authentication protocol that works by exchanging xml documents between the authentication. Keycloak uses asymmetric key pairs, a private and public key, to. The authentication. Keycloak Authentication Protocols.
From apisix.apache.org
Accessing APISIXDashboard from Everywhere with Keycloak Authentication Keycloak Authentication Protocols Keycloak supports the following standard protocols: Keycloak is an open source identity and access management (iam) tool. Saml 2.0 is primarily an authentication protocol that works by exchanging xml documents between the authentication. Keycloak uses asymmetric key pairs, a private and public key, to. It can overwrite and customize almost every aspect of a product or module. This section discusses. Keycloak Authentication Protocols.
From www.thomasvitale.com
Keycloak Authentication Flows, SSO Protocols and Client Configuration Keycloak Authentication Protocols It can overwrite and customize almost every aspect of a product or module. As an oauth2, openid connect, and saml compliant server, keycloak can secure any application and service as long as the. This support means that any tool or application that supports integration with the above protocols can be plugged into with keycloak (for example, enterprise applications like red. Keycloak Authentication Protocols.
From www.thomasvitale.com
Keycloak Authentication Flows, SSO Protocols and Client Configuration Keycloak Authentication Protocols It can overwrite and customize almost every aspect of a product or module. Saml 2.0 is primarily an authentication protocol that works by exchanging xml documents between the authentication. Keycloak supports the following standard protocols: Keycloak is an open source identity and access management (iam) tool. Keycloak uses asymmetric key pairs, a private and public key, to. This support means. Keycloak Authentication Protocols.
From medium.com
Keycloak for Identity and Access Management & High Availability Keycloak Authentication Protocols The authentication protocols that are used by keycloak require cryptographic signatures and sometimes encryption. Keycloak uses asymmetric key pairs, a private and public key, to. Saml 2.0 is primarily an authentication protocol that works by exchanging xml documents between the authentication. Keycloak supports the following standard protocols: As an oauth2, openid connect, and saml compliant server, keycloak can secure any. Keycloak Authentication Protocols.
From admin.dominodatalab.com
keycloak upstream idp trust Keycloak Authentication Protocols Keycloak is an open source identity and access management (iam) tool. Keycloak uses asymmetric key pairs, a private and public key, to. The authentication protocols that are used by keycloak require cryptographic signatures and sometimes encryption. This support means that any tool or application that supports integration with the above protocols can be plugged into with keycloak (for example, enterprise. Keycloak Authentication Protocols.
From www.vrogue.co
Docker Keycloak In Azure App Service Failed To Start vrogue.co Keycloak Authentication Protocols This section discusses authentication protocols, the red hat build of keycloak authentication server and how applications, secured by the. This support means that any tool or application that supports integration with the above protocols can be plugged into with keycloak (for example, enterprise applications like red hat ansible tower or sap business intelligence platform). Keycloak supports the following standard protocols:. Keycloak Authentication Protocols.
From baptistout.net
Passwordless authentication with Authn, Keycloak and Istio Keycloak Authentication Protocols It can overwrite and customize almost every aspect of a product or module. The authentication protocols that are used by keycloak require cryptographic signatures and sometimes encryption. This support means that any tool or application that supports integration with the above protocols can be plugged into with keycloak (for example, enterprise applications like red hat ansible tower or sap business. Keycloak Authentication Protocols.
From cybr.com
Authentication Protocols (802.1X, EAP/PEAP, EAPFAST/TLS/TTLS, and Keycloak Authentication Protocols Saml 2.0 is primarily an authentication protocol that works by exchanging xml documents between the authentication. It can overwrite and customize almost every aspect of a product or module. Keycloak supports the following standard protocols: The authentication protocols that are used by keycloak require cryptographic signatures and sometimes encryption. Keycloak uses asymmetric key pairs, a private and public key, to.. Keycloak Authentication Protocols.
From andrevianna-1662831931436.hashnode.dev
Understanding the Powerful Keycloak Tool Keycloak Authentication Protocols This section discusses authentication protocols, the red hat build of keycloak authentication server and how applications, secured by the. Keycloak is an open source identity and access management (iam) tool. The authentication protocols that are used by keycloak require cryptographic signatures and sometimes encryption. Saml 2.0 is primarily an authentication protocol that works by exchanging xml documents between the authentication.. Keycloak Authentication Protocols.
From help.hcltechsw.com
Sample KeyCloak configuration as an OIDC provider for Domino Keycloak Authentication Protocols It can overwrite and customize almost every aspect of a product or module. Keycloak supports the following standard protocols: Keycloak is an open source identity and access management (iam) tool. Keycloak uses asymmetric key pairs, a private and public key, to. The authentication protocols that are used by keycloak require cryptographic signatures and sometimes encryption. This support means that any. Keycloak Authentication Protocols.
From www.thomasvitale.com
Keycloak Authentication Flows, SSO Protocols and Client Configuration Keycloak Authentication Protocols The authentication protocols that are used by keycloak require cryptographic signatures and sometimes encryption. Keycloak is an open source identity and access management (iam) tool. This support means that any tool or application that supports integration with the above protocols can be plugged into with keycloak (for example, enterprise applications like red hat ansible tower or sap business intelligence platform).. Keycloak Authentication Protocols.
From walkingtree.tech
Keycloak and MultiFactor Authentication (MFA) Strengthening Security Keycloak Authentication Protocols Keycloak supports the following standard protocols: Keycloak uses asymmetric key pairs, a private and public key, to. Keycloak is an open source identity and access management (iam) tool. It can overwrite and customize almost every aspect of a product or module. This section discusses authentication protocols, the red hat build of keycloak authentication server and how applications, secured by the.. Keycloak Authentication Protocols.
From community.ibm.com
Extending Keycloak's authentication capabilities by integrating with Keycloak Authentication Protocols Keycloak uses asymmetric key pairs, a private and public key, to. It can overwrite and customize almost every aspect of a product or module. Saml 2.0 is primarily an authentication protocol that works by exchanging xml documents between the authentication. This support means that any tool or application that supports integration with the above protocols can be plugged into with. Keycloak Authentication Protocols.
From swimlane.com
Common REST API Authentication Methods Keycloak Authentication Protocols The authentication protocols that are used by keycloak require cryptographic signatures and sometimes encryption. Keycloak supports the following standard protocols: This support means that any tool or application that supports integration with the above protocols can be plugged into with keycloak (for example, enterprise applications like red hat ansible tower or sap business intelligence platform). As an oauth2, openid connect,. Keycloak Authentication Protocols.
From adaptive.live
Authentication Protocols Types and Uses Adaptive Keycloak Authentication Protocols The authentication protocols that are used by keycloak require cryptographic signatures and sometimes encryption. This support means that any tool or application that supports integration with the above protocols can be plugged into with keycloak (for example, enterprise applications like red hat ansible tower or sap business intelligence platform). Keycloak supports the following standard protocols: It can overwrite and customize. Keycloak Authentication Protocols.
From github.com
Quarkus Keycloak client authentication using x509 · keycloak keycloak Keycloak Authentication Protocols Keycloak uses asymmetric key pairs, a private and public key, to. It can overwrite and customize almost every aspect of a product or module. The authentication protocols that are used by keycloak require cryptographic signatures and sometimes encryption. As an oauth2, openid connect, and saml compliant server, keycloak can secure any application and service as long as the. This support. Keycloak Authentication Protocols.
From www.springcloud.io
Unified authentication authorization platform keycloak Introduction Keycloak Authentication Protocols This support means that any tool or application that supports integration with the above protocols can be plugged into with keycloak (for example, enterprise applications like red hat ansible tower or sap business intelligence platform). Saml 2.0 is primarily an authentication protocol that works by exchanging xml documents between the authentication. Keycloak supports the following standard protocols: It can overwrite. Keycloak Authentication Protocols.
From www.vrogue.co
Step By Step Guide Using Keycloak vrogue.co Keycloak Authentication Protocols The authentication protocols that are used by keycloak require cryptographic signatures and sometimes encryption. It can overwrite and customize almost every aspect of a product or module. As an oauth2, openid connect, and saml compliant server, keycloak can secure any application and service as long as the. This section discusses authentication protocols, the red hat build of keycloak authentication server. Keycloak Authentication Protocols.
From documentation.censhare.com
Configure Keycloak with LDAP_syadmin censhare Documentation MASTER Keycloak Authentication Protocols Keycloak uses asymmetric key pairs, a private and public key, to. Saml 2.0 is primarily an authentication protocol that works by exchanging xml documents between the authentication. It can overwrite and customize almost every aspect of a product or module. The authentication protocols that are used by keycloak require cryptographic signatures and sometimes encryption. Keycloak is an open source identity. Keycloak Authentication Protocols.
From walkingtree.tech
Introduction to Keycloak and the Need for Containerization Keycloak Authentication Protocols The authentication protocols that are used by keycloak require cryptographic signatures and sometimes encryption. Saml 2.0 is primarily an authentication protocol that works by exchanging xml documents between the authentication. Keycloak supports the following standard protocols: This section discusses authentication protocols, the red hat build of keycloak authentication server and how applications, secured by the. Keycloak is an open source. Keycloak Authentication Protocols.
From stackoverflow.com
rest Keycloak Oauth2 Authentication Flow Stack Overflow Keycloak Authentication Protocols This support means that any tool or application that supports integration with the above protocols can be plugged into with keycloak (for example, enterprise applications like red hat ansible tower or sap business intelligence platform). This section discusses authentication protocols, the red hat build of keycloak authentication server and how applications, secured by the. Saml 2.0 is primarily an authentication. Keycloak Authentication Protocols.
From adaptive.live
Adaptive Authentication Protocols Types and Uses Keycloak Authentication Protocols Keycloak supports the following standard protocols: Saml 2.0 is primarily an authentication protocol that works by exchanging xml documents between the authentication. This section discusses authentication protocols, the red hat build of keycloak authentication server and how applications, secured by the. Keycloak is an open source identity and access management (iam) tool. Keycloak uses asymmetric key pairs, a private and. Keycloak Authentication Protocols.
From www.redpill-linpro.com
Get started with OpenID Connect and Keycloak /techblog Keycloak Authentication Protocols The authentication protocols that are used by keycloak require cryptographic signatures and sometimes encryption. This section discusses authentication protocols, the red hat build of keycloak authentication server and how applications, secured by the. Keycloak supports the following standard protocols: Keycloak is an open source identity and access management (iam) tool. This support means that any tool or application that supports. Keycloak Authentication Protocols.
From medium.com
authn based authentication in Keycloak by Rishabh Singh Medium Keycloak Authentication Protocols Keycloak uses asymmetric key pairs, a private and public key, to. This support means that any tool or application that supports integration with the above protocols can be plugged into with keycloak (for example, enterprise applications like red hat ansible tower or sap business intelligence platform). As an oauth2, openid connect, and saml compliant server, keycloak can secure any application. Keycloak Authentication Protocols.