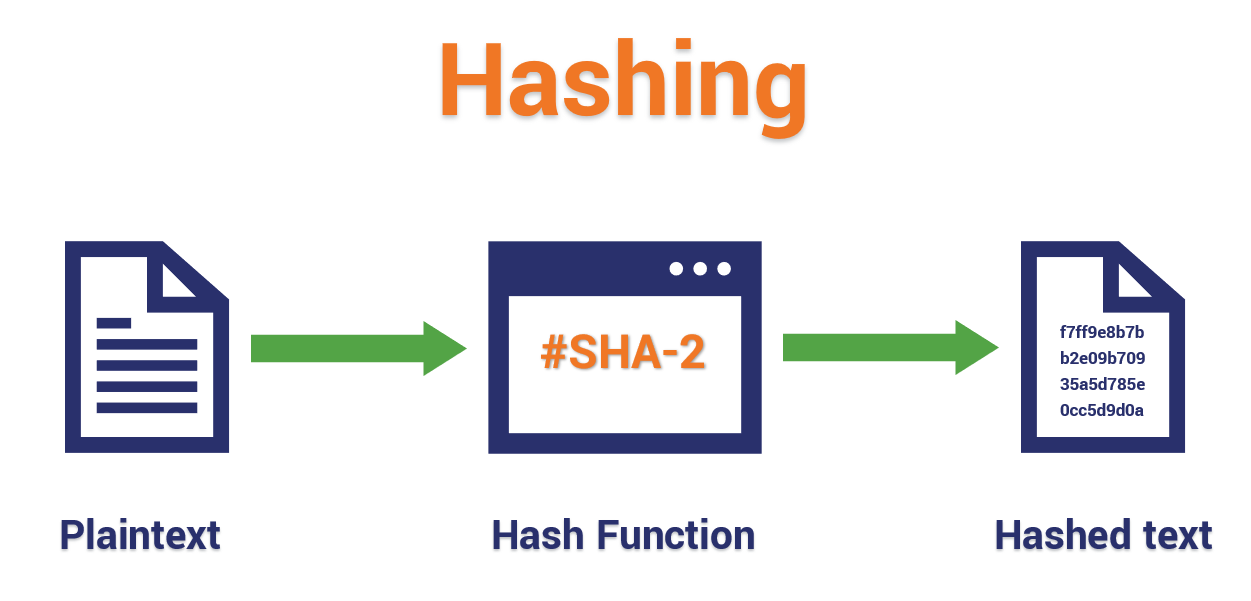
File Hash Types . This hash algorithm comparison article looks at the differences between md5 and the sha families of hash functions. In this article, we’ll take a closer look at what. While not quite perfect, current research indicates it is considerably more secure than. Learn about the different types of hash functions, their properties, and common applications such as password storage, data integrity verification, and digital. The universe of hash functions is vast, but in this blog post, we’ll focus on three popular cryptographic hash functions: There are many different types of hash algorithms such as ripemd, tiger, xxhash and more, but the most common type of hashing used for file. When it comes to computer security, file hashes are an important tool in the fight against malware and other types of cyber threats.
from www.thesslstore.com
In this article, we’ll take a closer look at what. There are many different types of hash algorithms such as ripemd, tiger, xxhash and more, but the most common type of hashing used for file. The universe of hash functions is vast, but in this blog post, we’ll focus on three popular cryptographic hash functions: When it comes to computer security, file hashes are an important tool in the fight against malware and other types of cyber threats. This hash algorithm comparison article looks at the differences between md5 and the sha families of hash functions. Learn about the different types of hash functions, their properties, and common applications such as password storage, data integrity verification, and digital. While not quite perfect, current research indicates it is considerably more secure than.
What Is a Hash Function in Cryptography? A Beginner’s Guide Hashed
File Hash Types This hash algorithm comparison article looks at the differences between md5 and the sha families of hash functions. Learn about the different types of hash functions, their properties, and common applications such as password storage, data integrity verification, and digital. There are many different types of hash algorithms such as ripemd, tiger, xxhash and more, but the most common type of hashing used for file. The universe of hash functions is vast, but in this blog post, we’ll focus on three popular cryptographic hash functions: While not quite perfect, current research indicates it is considerably more secure than. In this article, we’ll take a closer look at what. When it comes to computer security, file hashes are an important tool in the fight against malware and other types of cyber threats. This hash algorithm comparison article looks at the differences between md5 and the sha families of hash functions.
From www.ssla.co.uk
What is hash function? And how does it work ssla.co.uk File Hash Types Learn about the different types of hash functions, their properties, and common applications such as password storage, data integrity verification, and digital. While not quite perfect, current research indicates it is considerably more secure than. In this article, we’ll take a closer look at what. There are many different types of hash algorithms such as ripemd, tiger, xxhash and more,. File Hash Types.
From www.thesslstore.com
What Is a Hash Function in Cryptography? A Beginner’s Guide Hashed File Hash Types When it comes to computer security, file hashes are an important tool in the fight against malware and other types of cyber threats. While not quite perfect, current research indicates it is considerably more secure than. There are many different types of hash algorithms such as ripemd, tiger, xxhash and more, but the most common type of hashing used for. File Hash Types.
From www.golinuxcloud.com
How to crack hash using hashview [StepbyStep] GoLinuxCloud File Hash Types The universe of hash functions is vast, but in this blog post, we’ll focus on three popular cryptographic hash functions: There are many different types of hash algorithms such as ripemd, tiger, xxhash and more, but the most common type of hashing used for file. This hash algorithm comparison article looks at the differences between md5 and the sha families. File Hash Types.
From www.slideserve.com
PPT Hash Tables in C PowerPoint Presentation, free download ID3043234 File Hash Types This hash algorithm comparison article looks at the differences between md5 and the sha families of hash functions. There are many different types of hash algorithms such as ripemd, tiger, xxhash and more, but the most common type of hashing used for file. The universe of hash functions is vast, but in this blog post, we’ll focus on three popular. File Hash Types.
From atola.com
Calculate dual hash of an existing E01 file in Atola Insight Forensic File Hash Types This hash algorithm comparison article looks at the differences between md5 and the sha families of hash functions. The universe of hash functions is vast, but in this blog post, we’ll focus on three popular cryptographic hash functions: In this article, we’ll take a closer look at what. Learn about the different types of hash functions, their properties, and common. File Hash Types.
From www.2brightsparks.com
HashOnClick > Using HashOnClick File Hash Types The universe of hash functions is vast, but in this blog post, we’ll focus on three popular cryptographic hash functions: There are many different types of hash algorithms such as ripemd, tiger, xxhash and more, but the most common type of hashing used for file. This hash algorithm comparison article looks at the differences between md5 and the sha families. File Hash Types.
From oladino.com
Maybe Christmas Doesnt Come From A Store SVG Cricut File Oladino File Hash Types There are many different types of hash algorithms such as ripemd, tiger, xxhash and more, but the most common type of hashing used for file. This hash algorithm comparison article looks at the differences between md5 and the sha families of hash functions. When it comes to computer security, file hashes are an important tool in the fight against malware. File Hash Types.
From oladino.com
Retro Groovy Pink Christmas Merry Grinchmas SVG Graphic Design File File Hash Types Learn about the different types of hash functions, their properties, and common applications such as password storage, data integrity verification, and digital. When it comes to computer security, file hashes are an important tool in the fight against malware and other types of cyber threats. In this article, we’ll take a closer look at what. This hash algorithm comparison article. File Hash Types.
From www.thesslstore.com
What Is a Hash Function in Cryptography? A Beginner’s Guide Hashed File Hash Types Learn about the different types of hash functions, their properties, and common applications such as password storage, data integrity verification, and digital. In this article, we’ll take a closer look at what. While not quite perfect, current research indicates it is considerably more secure than. This hash algorithm comparison article looks at the differences between md5 and the sha families. File Hash Types.
From www.linkedin.com
What is Hashing? File Hash Types While not quite perfect, current research indicates it is considerably more secure than. The universe of hash functions is vast, but in this blog post, we’ll focus on three popular cryptographic hash functions: There are many different types of hash algorithms such as ripemd, tiger, xxhash and more, but the most common type of hashing used for file. When it. File Hash Types.
From securityxploded.com
hash generator File Hash Types The universe of hash functions is vast, but in this blog post, we’ll focus on three popular cryptographic hash functions: While not quite perfect, current research indicates it is considerably more secure than. Learn about the different types of hash functions, their properties, and common applications such as password storage, data integrity verification, and digital. In this article, we’ll take. File Hash Types.
From kali-linux.net
hashidentifier « Kali Linux Documentación en español File Hash Types This hash algorithm comparison article looks at the differences between md5 and the sha families of hash functions. The universe of hash functions is vast, but in this blog post, we’ll focus on three popular cryptographic hash functions: Learn about the different types of hash functions, their properties, and common applications such as password storage, data integrity verification, and digital.. File Hash Types.
From oladino.com
Auntie Christmas Family Claus SVG Cutting Digital File Oladino File Hash Types Learn about the different types of hash functions, their properties, and common applications such as password storage, data integrity verification, and digital. When it comes to computer security, file hashes are an important tool in the fight against malware and other types of cyber threats. While not quite perfect, current research indicates it is considerably more secure than. The universe. File Hash Types.
From www.smeegesec.com
HashTag Password Hash Identification SmeegeSec File Hash Types When it comes to computer security, file hashes are an important tool in the fight against malware and other types of cyber threats. This hash algorithm comparison article looks at the differences between md5 and the sha families of hash functions. There are many different types of hash algorithms such as ripemd, tiger, xxhash and more, but the most common. File Hash Types.
From thecleverest.com
Understanding MD5 Hashes and Security The Cleverest File Hash Types In this article, we’ll take a closer look at what. The universe of hash functions is vast, but in this blog post, we’ll focus on three popular cryptographic hash functions: This hash algorithm comparison article looks at the differences between md5 and the sha families of hash functions. When it comes to computer security, file hashes are an important tool. File Hash Types.
From hashsuite.openwall.net
Hash Suite A program to audit security of password hashes File Hash Types There are many different types of hash algorithms such as ripemd, tiger, xxhash and more, but the most common type of hashing used for file. The universe of hash functions is vast, but in this blog post, we’ll focus on three popular cryptographic hash functions: Learn about the different types of hash functions, their properties, and common applications such as. File Hash Types.
From oladino.com
Funny Bluey Christmas Tree SVG Graphic Design File Oladino File Hash Types There are many different types of hash algorithms such as ripemd, tiger, xxhash and more, but the most common type of hashing used for file. When it comes to computer security, file hashes are an important tool in the fight against malware and other types of cyber threats. In this article, we’ll take a closer look at what. This hash. File Hash Types.
From oladino.com
Pregnancy Thanksgiving Theres A Little Turkey SVG File Oladino File Hash Types While not quite perfect, current research indicates it is considerably more secure than. The universe of hash functions is vast, but in this blog post, we’ll focus on three popular cryptographic hash functions: In this article, we’ll take a closer look at what. Learn about the different types of hash functions, their properties, and common applications such as password storage,. File Hash Types.
From www.bank2home.com
How To Identify Hash Types Ethical Hacking And Testing File Hash Types There are many different types of hash algorithms such as ripemd, tiger, xxhash and more, but the most common type of hashing used for file. In this article, we’ll take a closer look at what. The universe of hash functions is vast, but in this blog post, we’ll focus on three popular cryptographic hash functions: Learn about the different types. File Hash Types.
From oladino.com
Butterfly In My Godmother Era SVG Graphic Design File Oladino File Hash Types In this article, we’ll take a closer look at what. While not quite perfect, current research indicates it is considerably more secure than. Learn about the different types of hash functions, their properties, and common applications such as password storage, data integrity verification, and digital. There are many different types of hash algorithms such as ripemd, tiger, xxhash and more,. File Hash Types.
From www.okta.com
Hashing vs. Encryption Definitions & Differences Okta UK File Hash Types Learn about the different types of hash functions, their properties, and common applications such as password storage, data integrity verification, and digital. While not quite perfect, current research indicates it is considerably more secure than. In this article, we’ll take a closer look at what. When it comes to computer security, file hashes are an important tool in the fight. File Hash Types.
From www.onlinewebtoolkit.com
Online Hash Generator Password Hash Generator File Hash Types While not quite perfect, current research indicates it is considerably more secure than. This hash algorithm comparison article looks at the differences between md5 and the sha families of hash functions. The universe of hash functions is vast, but in this blog post, we’ll focus on three popular cryptographic hash functions: In this article, we’ll take a closer look at. File Hash Types.
From oladino.com
Have Yourself A Merry Little Solstice SVG Digital File Oladino File Hash Types In this article, we’ll take a closer look at what. Learn about the different types of hash functions, their properties, and common applications such as password storage, data integrity verification, and digital. This hash algorithm comparison article looks at the differences between md5 and the sha families of hash functions. When it comes to computer security, file hashes are an. File Hash Types.
From khalilstemmler.com
Hash Tables What, Why & How to Use Them Khalil Stemmler File Hash Types While not quite perfect, current research indicates it is considerably more secure than. The universe of hash functions is vast, but in this blog post, we’ll focus on three popular cryptographic hash functions: Learn about the different types of hash functions, their properties, and common applications such as password storage, data integrity verification, and digital. When it comes to computer. File Hash Types.
From sleuthkit.org
Autopsy User Documentation Hash Database Lookup Module File Hash Types When it comes to computer security, file hashes are an important tool in the fight against malware and other types of cyber threats. In this article, we’ll take a closer look at what. The universe of hash functions is vast, but in this blog post, we’ll focus on three popular cryptographic hash functions: While not quite perfect, current research indicates. File Hash Types.
From oladino.com
Retro Christmas Black Cat Santa Hat SVG Graphic Design File Oladino File Hash Types When it comes to computer security, file hashes are an important tool in the fight against malware and other types of cyber threats. There are many different types of hash algorithms such as ripemd, tiger, xxhash and more, but the most common type of hashing used for file. The universe of hash functions is vast, but in this blog post,. File Hash Types.
From oladino.com
Could I Be Any More Festive SVG Graphic Design File Oladino File Hash Types The universe of hash functions is vast, but in this blog post, we’ll focus on three popular cryptographic hash functions: There are many different types of hash algorithms such as ripemd, tiger, xxhash and more, but the most common type of hashing used for file. In this article, we’ll take a closer look at what. While not quite perfect, current. File Hash Types.
From oladino.com
Retro Christmas Sugar Cookie SVG Graphic Design File Oladino File Hash Types Learn about the different types of hash functions, their properties, and common applications such as password storage, data integrity verification, and digital. There are many different types of hash algorithms such as ripemd, tiger, xxhash and more, but the most common type of hashing used for file. In this article, we’ll take a closer look at what. While not quite. File Hash Types.
From snorrigiorgetti.com
What is Hashing and How Does it Work? (2023) File Hash Types In this article, we’ll take a closer look at what. There are many different types of hash algorithms such as ripemd, tiger, xxhash and more, but the most common type of hashing used for file. The universe of hash functions is vast, but in this blog post, we’ll focus on three popular cryptographic hash functions: This hash algorithm comparison article. File Hash Types.
From www.duplicatedetective.com
File Hash Checksum Calculator File Hash Types The universe of hash functions is vast, but in this blog post, we’ll focus on three popular cryptographic hash functions: Learn about the different types of hash functions, their properties, and common applications such as password storage, data integrity verification, and digital. When it comes to computer security, file hashes are an important tool in the fight against malware and. File Hash Types.
From www.ionos.com
Hash functions definition, usage, and examples IONOS File Hash Types The universe of hash functions is vast, but in this blog post, we’ll focus on three popular cryptographic hash functions: When it comes to computer security, file hashes are an important tool in the fight against malware and other types of cyber threats. Learn about the different types of hash functions, their properties, and common applications such as password storage,. File Hash Types.
From www.youtube.com
Hash function YouTube File Hash Types There are many different types of hash algorithms such as ripemd, tiger, xxhash and more, but the most common type of hashing used for file. When it comes to computer security, file hashes are an important tool in the fight against malware and other types of cyber threats. While not quite perfect, current research indicates it is considerably more secure. File Hash Types.
From www.youtube.com
Cryptographic hash function YouTube File Hash Types There are many different types of hash algorithms such as ripemd, tiger, xxhash and more, but the most common type of hashing used for file. Learn about the different types of hash functions, their properties, and common applications such as password storage, data integrity verification, and digital. When it comes to computer security, file hashes are an important tool in. File Hash Types.
From winaero.com
Get File Hash With PowerShell in Windows 10 File Hash Types There are many different types of hash algorithms such as ripemd, tiger, xxhash and more, but the most common type of hashing used for file. In this article, we’ll take a closer look at what. While not quite perfect, current research indicates it is considerably more secure than. This hash algorithm comparison article looks at the differences between md5 and. File Hash Types.
From oladino.com
Free Twelve Carat Toothache Album Post Malone Svg Cutting File Oladino File Hash Types The universe of hash functions is vast, but in this blog post, we’ll focus on three popular cryptographic hash functions: In this article, we’ll take a closer look at what. When it comes to computer security, file hashes are an important tool in the fight against malware and other types of cyber threats. While not quite perfect, current research indicates. File Hash Types.