Methods Of Threat Detection . early detection and intervention is the goal of all threat detection methods. the primary methods of threat detection are security solutions, such as siem or xdr, that analyze activity across the environment to. what is threat detection, investigation, and response? When network breaches happen, uncovering them quickly. Tdr involves two key steps: Threat detection encompasses monitoring networks, endpoints,. Threat detection and response, often abbreviated as tdr,. how does threat detection and response work? threat detection, investigation, and response (tdir) is a cybersecurity process for finding, analyzing, and mitigating threats. threat response consists of the mitigation efforts used to neutralize and prevent cyber threats before they create vulnerabilities. threat detection and response (tdr) is a methodology that enables security operators to detect attacks and neutralize them before they cause disruption.
from www.logpoint.com
Tdr involves two key steps: Threat detection and response, often abbreviated as tdr,. how does threat detection and response work? threat detection, investigation, and response (tdir) is a cybersecurity process for finding, analyzing, and mitigating threats. the primary methods of threat detection are security solutions, such as siem or xdr, that analyze activity across the environment to. threat detection and response (tdr) is a methodology that enables security operators to detect attacks and neutralize them before they cause disruption. When network breaches happen, uncovering them quickly. early detection and intervention is the goal of all threat detection methods. threat response consists of the mitigation efforts used to neutralize and prevent cyber threats before they create vulnerabilities. what is threat detection, investigation, and response?
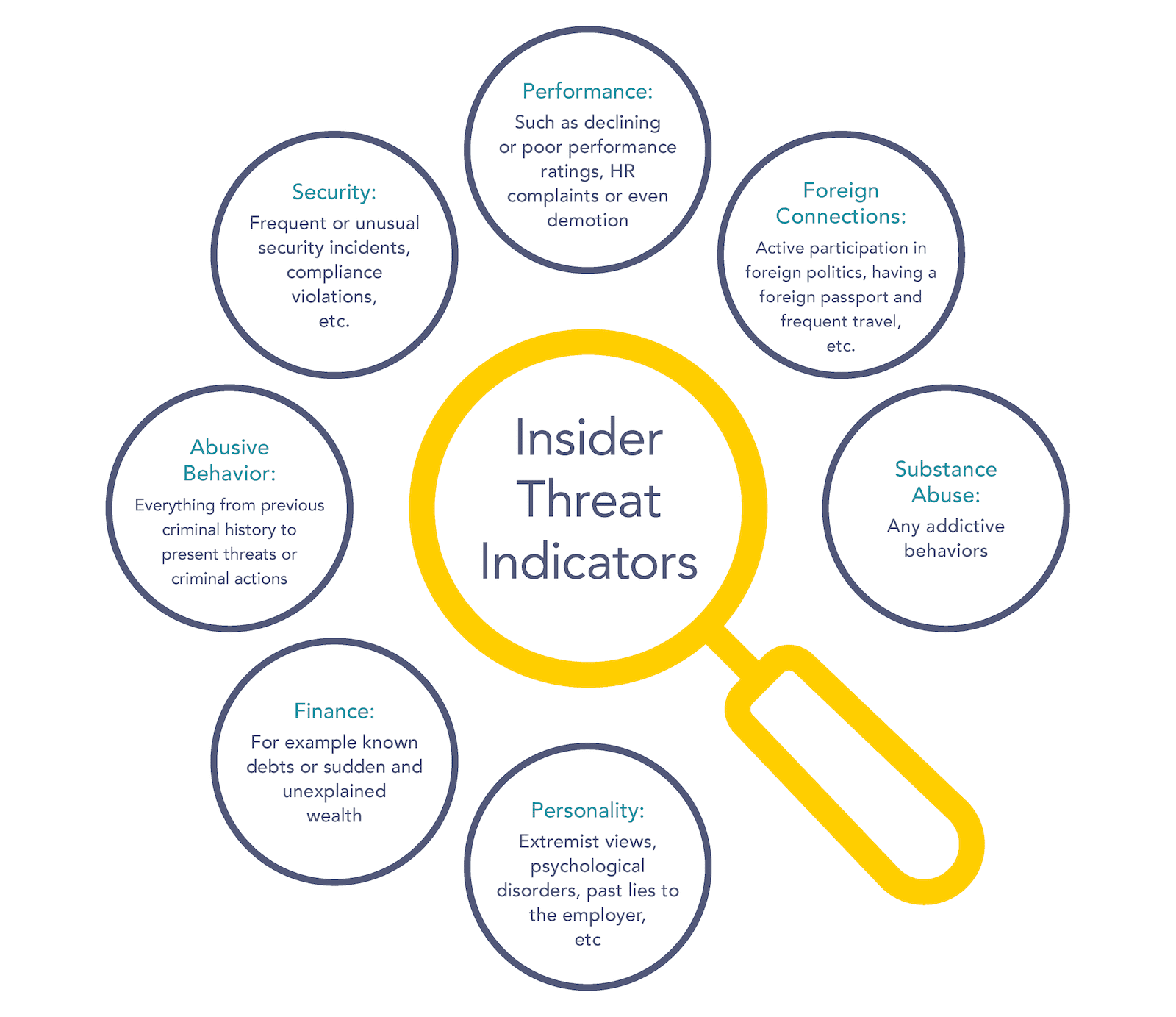
What is an Insider Threat? How to define, detect and stop an insider threat
Methods Of Threat Detection threat detection, investigation, and response (tdir) is a cybersecurity process for finding, analyzing, and mitigating threats. early detection and intervention is the goal of all threat detection methods. Threat detection encompasses monitoring networks, endpoints,. threat detection, investigation, and response (tdir) is a cybersecurity process for finding, analyzing, and mitigating threats. Tdr involves two key steps: threat detection and response (tdr) is a methodology that enables security operators to detect attacks and neutralize them before they cause disruption. When network breaches happen, uncovering them quickly. threat response consists of the mitigation efforts used to neutralize and prevent cyber threats before they create vulnerabilities. the primary methods of threat detection are security solutions, such as siem or xdr, that analyze activity across the environment to. what is threat detection, investigation, and response? how does threat detection and response work? Threat detection and response, often abbreviated as tdr,.
From www.zurich.ibm.com
AI and Automation for Threat Management, Security, IBM Research Europe Methods Of Threat Detection the primary methods of threat detection are security solutions, such as siem or xdr, that analyze activity across the environment to. what is threat detection, investigation, and response? Threat detection and response, often abbreviated as tdr,. early detection and intervention is the goal of all threat detection methods. Threat detection encompasses monitoring networks, endpoints,. threat detection,. Methods Of Threat Detection.
From www.webopedia.com
What Is Threat Detection? opedia Definition & Meaning Methods Of Threat Detection what is threat detection, investigation, and response? early detection and intervention is the goal of all threat detection methods. threat response consists of the mitigation efforts used to neutralize and prevent cyber threats before they create vulnerabilities. how does threat detection and response work? When network breaches happen, uncovering them quickly. Threat detection and response, often. Methods Of Threat Detection.
From www.techopedia.com
What is Threat Detection and Response? Components and Types Methods Of Threat Detection When network breaches happen, uncovering them quickly. the primary methods of threat detection are security solutions, such as siem or xdr, that analyze activity across the environment to. threat detection, investigation, and response (tdir) is a cybersecurity process for finding, analyzing, and mitigating threats. early detection and intervention is the goal of all threat detection methods. Threat. Methods Of Threat Detection.
From ordr.net
Threat Detection/Response Ordr Methods Of Threat Detection early detection and intervention is the goal of all threat detection methods. When network breaches happen, uncovering them quickly. Threat detection and response, often abbreviated as tdr,. how does threat detection and response work? the primary methods of threat detection are security solutions, such as siem or xdr, that analyze activity across the environment to. threat. Methods Of Threat Detection.
From datasciencedojo.com
AI in Cybersecurity Revolutionizing Threat Detection Methods Of Threat Detection threat response consists of the mitigation efforts used to neutralize and prevent cyber threats before they create vulnerabilities. threat detection, investigation, and response (tdir) is a cybersecurity process for finding, analyzing, and mitigating threats. how does threat detection and response work? the primary methods of threat detection are security solutions, such as siem or xdr, that. Methods Of Threat Detection.
From www.researchgate.net
Tools and methods for detection of potential threats in Wireless Methods Of Threat Detection threat detection and response (tdr) is a methodology that enables security operators to detect attacks and neutralize them before they cause disruption. threat response consists of the mitigation efforts used to neutralize and prevent cyber threats before they create vulnerabilities. what is threat detection, investigation, and response? When network breaches happen, uncovering them quickly. the primary. Methods Of Threat Detection.
From www.bloorresearch.com
The many flavours of threat detection and response Bloor Research Methods Of Threat Detection how does threat detection and response work? Tdr involves two key steps: Threat detection encompasses monitoring networks, endpoints,. Threat detection and response, often abbreviated as tdr,. early detection and intervention is the goal of all threat detection methods. the primary methods of threat detection are security solutions, such as siem or xdr, that analyze activity across the. Methods Of Threat Detection.
From www.kaspersky.com
How to choose threat intelligence Kaspersky official blog Methods Of Threat Detection threat detection and response (tdr) is a methodology that enables security operators to detect attacks and neutralize them before they cause disruption. how does threat detection and response work? threat response consists of the mitigation efforts used to neutralize and prevent cyber threats before they create vulnerabilities. When network breaches happen, uncovering them quickly. what is. Methods Of Threat Detection.
From www.mdpi.com
Symmetry Free FullText Malware Analysis and Detection Using Methods Of Threat Detection what is threat detection, investigation, and response? Threat detection encompasses monitoring networks, endpoints,. threat detection and response (tdr) is a methodology that enables security operators to detect attacks and neutralize them before they cause disruption. threat detection, investigation, and response (tdir) is a cybersecurity process for finding, analyzing, and mitigating threats. early detection and intervention is. Methods Of Threat Detection.
From www.logpoint.com
What is an Insider Threat? How to define, detect and stop an insider threat Methods Of Threat Detection threat detection and response (tdr) is a methodology that enables security operators to detect attacks and neutralize them before they cause disruption. threat detection, investigation, and response (tdir) is a cybersecurity process for finding, analyzing, and mitigating threats. Threat detection encompasses monitoring networks, endpoints,. early detection and intervention is the goal of all threat detection methods. . Methods Of Threat Detection.
From medium.com
How to identify a Threat in a network? How to perform Risk Exposure Methods Of Threat Detection how does threat detection and response work? the primary methods of threat detection are security solutions, such as siem or xdr, that analyze activity across the environment to. Threat detection and response, often abbreviated as tdr,. threat detection and response (tdr) is a methodology that enables security operators to detect attacks and neutralize them before they cause. Methods Of Threat Detection.
From www.security-analyst.org
Threat Analysis and Risk Assessment Methods Of Threat Detection Tdr involves two key steps: When network breaches happen, uncovering them quickly. the primary methods of threat detection are security solutions, such as siem or xdr, that analyze activity across the environment to. threat detection, investigation, and response (tdir) is a cybersecurity process for finding, analyzing, and mitigating threats. threat detection and response (tdr) is a methodology. Methods Of Threat Detection.
From flare.io
Cyber Threat Detection The Definitive Guide Flare Methods Of Threat Detection threat detection and response (tdr) is a methodology that enables security operators to detect attacks and neutralize them before they cause disruption. what is threat detection, investigation, and response? When network breaches happen, uncovering them quickly. Threat detection and response, often abbreviated as tdr,. the primary methods of threat detection are security solutions, such as siem or. Methods Of Threat Detection.
From www.slideserve.com
PPT Threat Detection Systems Everything You Need to Know PowerPoint Methods Of Threat Detection threat detection and response (tdr) is a methodology that enables security operators to detect attacks and neutralize them before they cause disruption. Threat detection and response, often abbreviated as tdr,. Threat detection encompasses monitoring networks, endpoints,. what is threat detection, investigation, and response? threat detection, investigation, and response (tdir) is a cybersecurity process for finding, analyzing, and. Methods Of Threat Detection.
From www.researchgate.net
2. Event management flow chartthreat detection, verification and risk Methods Of Threat Detection When network breaches happen, uncovering them quickly. Threat detection and response, often abbreviated as tdr,. Threat detection encompasses monitoring networks, endpoints,. how does threat detection and response work? Tdr involves two key steps: threat response consists of the mitigation efforts used to neutralize and prevent cyber threats before they create vulnerabilities. what is threat detection, investigation, and. Methods Of Threat Detection.
From www.revealholdingsgroup.com
Visualization of Threat Detection, Investigation and Response Reveal Methods Of Threat Detection what is threat detection, investigation, and response? threat detection and response (tdr) is a methodology that enables security operators to detect attacks and neutralize them before they cause disruption. threat detection, investigation, and response (tdir) is a cybersecurity process for finding, analyzing, and mitigating threats. Threat detection and response, often abbreviated as tdr,. threat response consists. Methods Of Threat Detection.
From engineering.salesforce.com
Tackling Cyber Threats with Automation Salesforce’s Security Strategy Methods Of Threat Detection early detection and intervention is the goal of all threat detection methods. threat response consists of the mitigation efforts used to neutralize and prevent cyber threats before they create vulnerabilities. what is threat detection, investigation, and response? the primary methods of threat detection are security solutions, such as siem or xdr, that analyze activity across the. Methods Of Threat Detection.
From memgraph.com
Efficient Threat Detection in Cybersecurity with Memgraph Methods Of Threat Detection When network breaches happen, uncovering them quickly. threat detection, investigation, and response (tdir) is a cybersecurity process for finding, analyzing, and mitigating threats. what is threat detection, investigation, and response? the primary methods of threat detection are security solutions, such as siem or xdr, that analyze activity across the environment to. Threat detection encompasses monitoring networks, endpoints,.. Methods Of Threat Detection.
From www.logpoint.com
What is Cyber Threat Hunting? A simple guide to Threat Hunting Methods Of Threat Detection the primary methods of threat detection are security solutions, such as siem or xdr, that analyze activity across the environment to. Threat detection encompasses monitoring networks, endpoints,. Threat detection and response, often abbreviated as tdr,. Tdr involves two key steps: threat response consists of the mitigation efforts used to neutralize and prevent cyber threats before they create vulnerabilities.. Methods Of Threat Detection.
From www.teramind.co
Insider Threat Detection, Monitoring & Prevention Teramind Methods Of Threat Detection threat response consists of the mitigation efforts used to neutralize and prevent cyber threats before they create vulnerabilities. threat detection, investigation, and response (tdir) is a cybersecurity process for finding, analyzing, and mitigating threats. Threat detection and response, often abbreviated as tdr,. how does threat detection and response work? Tdr involves two key steps: the primary. Methods Of Threat Detection.
From www.mdpi.com
Applied Sciences Free FullText Insider Threat Detection Using Methods Of Threat Detection When network breaches happen, uncovering them quickly. Threat detection and response, often abbreviated as tdr,. the primary methods of threat detection are security solutions, such as siem or xdr, that analyze activity across the environment to. Threat detection encompasses monitoring networks, endpoints,. threat detection and response (tdr) is a methodology that enables security operators to detect attacks and. Methods Of Threat Detection.
From socradar.io
What are the Different Methods of Threat Detection? SOCRadar® Cyber Methods Of Threat Detection the primary methods of threat detection are security solutions, such as siem or xdr, that analyze activity across the environment to. threat detection and response (tdr) is a methodology that enables security operators to detect attacks and neutralize them before they cause disruption. threat response consists of the mitigation efforts used to neutralize and prevent cyber threats. Methods Of Threat Detection.
From www.researchgate.net
Flow chart of network attack detection Download Scientific Diagram Methods Of Threat Detection early detection and intervention is the goal of all threat detection methods. threat response consists of the mitigation efforts used to neutralize and prevent cyber threats before they create vulnerabilities. how does threat detection and response work? Tdr involves two key steps: the primary methods of threat detection are security solutions, such as siem or xdr,. Methods Of Threat Detection.
From www.dnsstuff.com
What Is Threat Intelligence? Definition and Types DNSstuff Methods Of Threat Detection Threat detection and response, often abbreviated as tdr,. threat detection and response (tdr) is a methodology that enables security operators to detect attacks and neutralize them before they cause disruption. early detection and intervention is the goal of all threat detection methods. the primary methods of threat detection are security solutions, such as siem or xdr, that. Methods Of Threat Detection.
From cyber.vumetric.com
3 major threat detection methods explained Vumetric Cyber Portal Methods Of Threat Detection threat response consists of the mitigation efforts used to neutralize and prevent cyber threats before they create vulnerabilities. early detection and intervention is the goal of all threat detection methods. When network breaches happen, uncovering them quickly. Tdr involves two key steps: the primary methods of threat detection are security solutions, such as siem or xdr, that. Methods Of Threat Detection.
From damocles.com.au
Managed Threat Detection Services Threat Detection Service Australia Methods Of Threat Detection how does threat detection and response work? threat detection and response (tdr) is a methodology that enables security operators to detect attacks and neutralize them before they cause disruption. Threat detection and response, often abbreviated as tdr,. threat response consists of the mitigation efforts used to neutralize and prevent cyber threats before they create vulnerabilities. Threat detection. Methods Of Threat Detection.
From spie.org
Standoff detection of chemical and biological threats Methods Of Threat Detection Tdr involves two key steps: early detection and intervention is the goal of all threat detection methods. threat response consists of the mitigation efforts used to neutralize and prevent cyber threats before they create vulnerabilities. threat detection, investigation, and response (tdir) is a cybersecurity process for finding, analyzing, and mitigating threats. Threat detection encompasses monitoring networks, endpoints,.. Methods Of Threat Detection.
From www.memcyco.com
10 Ways Threat Detection is Evolving in 2023 Memcyco Methods Of Threat Detection the primary methods of threat detection are security solutions, such as siem or xdr, that analyze activity across the environment to. threat detection and response (tdr) is a methodology that enables security operators to detect attacks and neutralize them before they cause disruption. Threat detection encompasses monitoring networks, endpoints,. how does threat detection and response work? . Methods Of Threat Detection.
From www.cr-t.com
Insider Threats and How to Detect Them IT Services CRT Utah Methods Of Threat Detection Tdr involves two key steps: threat detection, investigation, and response (tdir) is a cybersecurity process for finding, analyzing, and mitigating threats. early detection and intervention is the goal of all threat detection methods. how does threat detection and response work? Threat detection and response, often abbreviated as tdr,. what is threat detection, investigation, and response? . Methods Of Threat Detection.
From www.slideteam.net
Cyber Security Incident Response Process Flow Chart Deploying Computer Methods Of Threat Detection Threat detection and response, often abbreviated as tdr,. early detection and intervention is the goal of all threat detection methods. how does threat detection and response work? Tdr involves two key steps: Threat detection encompasses monitoring networks, endpoints,. threat response consists of the mitigation efforts used to neutralize and prevent cyber threats before they create vulnerabilities. . Methods Of Threat Detection.
From www.comparitech.com
Insider Threat Detection Guide Mitigation Strategies & Tools Methods Of Threat Detection threat response consists of the mitigation efforts used to neutralize and prevent cyber threats before they create vulnerabilities. When network breaches happen, uncovering them quickly. Threat detection encompasses monitoring networks, endpoints,. what is threat detection, investigation, and response? threat detection, investigation, and response (tdir) is a cybersecurity process for finding, analyzing, and mitigating threats. Tdr involves two. Methods Of Threat Detection.
From www.paloaltonetworks.com
Unit 42 and Crypsis Combine to Offer Threat Intel, Incident Response Methods Of Threat Detection Threat detection and response, often abbreviated as tdr,. threat detection and response (tdr) is a methodology that enables security operators to detect attacks and neutralize them before they cause disruption. early detection and intervention is the goal of all threat detection methods. Tdr involves two key steps: how does threat detection and response work? threat detection,. Methods Of Threat Detection.
From www.cybersecurity-automation.com
4 Methods of Threat Detection Cybersecurity Automation Methods Of Threat Detection threat response consists of the mitigation efforts used to neutralize and prevent cyber threats before they create vulnerabilities. Threat detection encompasses monitoring networks, endpoints,. what is threat detection, investigation, and response? threat detection and response (tdr) is a methodology that enables security operators to detect attacks and neutralize them before they cause disruption. Tdr involves two key. Methods Of Threat Detection.
From securityboulevard.com
Your Security Guide to Insider Threats Detection, Best Practices Methods Of Threat Detection Threat detection encompasses monitoring networks, endpoints,. early detection and intervention is the goal of all threat detection methods. how does threat detection and response work? the primary methods of threat detection are security solutions, such as siem or xdr, that analyze activity across the environment to. Tdr involves two key steps: Threat detection and response, often abbreviated. Methods Of Threat Detection.
From mixmode.ai
Infographic AI Detection in Cybersecurity Methods Of Threat Detection Threat detection encompasses monitoring networks, endpoints,. early detection and intervention is the goal of all threat detection methods. Threat detection and response, often abbreviated as tdr,. threat detection and response (tdr) is a methodology that enables security operators to detect attacks and neutralize them before they cause disruption. threat detection, investigation, and response (tdir) is a cybersecurity. Methods Of Threat Detection.