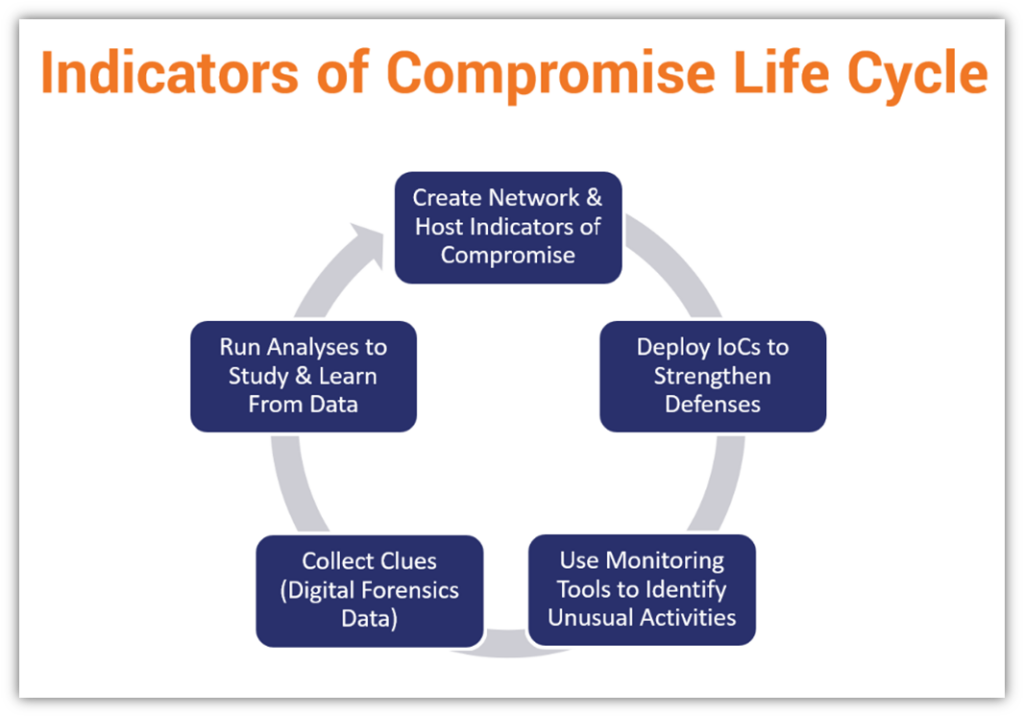
Indicator-Compromise .Com- Potentially Malicious Hostname . Indicators of compromise, or iocs, are indicators and proof of a data breach that is often discovered after a cyber attack. This guide explores the types of iocs, their. These are red flags of cyberattacks like. Indicators of compromise (iocs) are artifacts that indicate a potential intrusion. An indicator of compromise is a broad term for any detected signal of a potential cyberattack. Hi, priority 1 means some thing required your. Indicators of compromise are behaviors or data which show that a data breach, intrusion, or cyberattack has occurred. To keep it practical, indicators of compromise (iocs) are technical data that can be used to reliably identify malicious activities or.
from www.thesslstore.com
This guide explores the types of iocs, their. Hi, priority 1 means some thing required your. To keep it practical, indicators of compromise (iocs) are technical data that can be used to reliably identify malicious activities or. An indicator of compromise is a broad term for any detected signal of a potential cyberattack. Indicators of compromise, or iocs, are indicators and proof of a data breach that is often discovered after a cyber attack. Indicators of compromise (iocs) are artifacts that indicate a potential intrusion. Indicators of compromise are behaviors or data which show that a data breach, intrusion, or cyberattack has occurred. These are red flags of cyberattacks like.
Indicators of Compromise Cybersecurity’s Digital Breadcrumbs Hashed
Indicator-Compromise .Com- Potentially Malicious Hostname An indicator of compromise is a broad term for any detected signal of a potential cyberattack. Indicators of compromise are behaviors or data which show that a data breach, intrusion, or cyberattack has occurred. Hi, priority 1 means some thing required your. To keep it practical, indicators of compromise (iocs) are technical data that can be used to reliably identify malicious activities or. Indicators of compromise, or iocs, are indicators and proof of a data breach that is often discovered after a cyber attack. Indicators of compromise (iocs) are artifacts that indicate a potential intrusion. These are red flags of cyberattacks like. This guide explores the types of iocs, their. An indicator of compromise is a broad term for any detected signal of a potential cyberattack.
From www.dreamstime.com
The MBTI MyersBriggs Personality Type Indicator Use in Psychology Indicator-Compromise .Com- Potentially Malicious Hostname To keep it practical, indicators of compromise (iocs) are technical data that can be used to reliably identify malicious activities or. Indicators of compromise are behaviors or data which show that a data breach, intrusion, or cyberattack has occurred. These are red flags of cyberattacks like. An indicator of compromise is a broad term for any detected signal of a. Indicator-Compromise .Com- Potentially Malicious Hostname.
From www.muhammedaygun.com
Indicator Of Compromise (IoC ) Nedir? Muhammed AYGÜN Indicator-Compromise .Com- Potentially Malicious Hostname Indicators of compromise, or iocs, are indicators and proof of a data breach that is often discovered after a cyber attack. These are red flags of cyberattacks like. Indicators of compromise are behaviors or data which show that a data breach, intrusion, or cyberattack has occurred. This guide explores the types of iocs, their. To keep it practical, indicators of. Indicator-Compromise .Com- Potentially Malicious Hostname.
From www.lepide.com
What are Indicators of Compromise? Indicator-Compromise .Com- Potentially Malicious Hostname This guide explores the types of iocs, their. To keep it practical, indicators of compromise (iocs) are technical data that can be used to reliably identify malicious activities or. Indicators of compromise (iocs) are artifacts that indicate a potential intrusion. Indicators of compromise, or iocs, are indicators and proof of a data breach that is often discovered after a cyber. Indicator-Compromise .Com- Potentially Malicious Hostname.
From www.packetlabs.net
What are Indicators of Compromise (IoCs)? Indicator-Compromise .Com- Potentially Malicious Hostname These are red flags of cyberattacks like. Indicators of compromise are behaviors or data which show that a data breach, intrusion, or cyberattack has occurred. This guide explores the types of iocs, their. An indicator of compromise is a broad term for any detected signal of a potential cyberattack. Indicators of compromise (iocs) are artifacts that indicate a potential intrusion.. Indicator-Compromise .Com- Potentially Malicious Hostname.
From www.thesslstore.com
Indicators of Compromise Cybersecurity’s Digital Breadcrumbs Hashed Indicator-Compromise .Com- Potentially Malicious Hostname Indicators of compromise (iocs) are artifacts that indicate a potential intrusion. An indicator of compromise is a broad term for any detected signal of a potential cyberattack. Hi, priority 1 means some thing required your. These are red flags of cyberattacks like. This guide explores the types of iocs, their. Indicators of compromise, or iocs, are indicators and proof of. Indicator-Compromise .Com- Potentially Malicious Hostname.
From securityonline.info
pythoniocextract v1.16.1 releases Advanced Indicator of Compromise Indicator-Compromise .Com- Potentially Malicious Hostname This guide explores the types of iocs, their. To keep it practical, indicators of compromise (iocs) are technical data that can be used to reliably identify malicious activities or. Hi, priority 1 means some thing required your. Indicators of compromise are behaviors or data which show that a data breach, intrusion, or cyberattack has occurred. Indicators of compromise, or iocs,. Indicator-Compromise .Com- Potentially Malicious Hostname.
From www.youtube.com
What are the Indicators of compromise YouTube Indicator-Compromise .Com- Potentially Malicious Hostname Hi, priority 1 means some thing required your. To keep it practical, indicators of compromise (iocs) are technical data that can be used to reliably identify malicious activities or. Indicators of compromise, or iocs, are indicators and proof of a data breach that is often discovered after a cyber attack. These are red flags of cyberattacks like. Indicators of compromise. Indicator-Compromise .Com- Potentially Malicious Hostname.
From www.youtube.com
Threat Hunting using an Indicator of Compromise (IOC) File YouTube Indicator-Compromise .Com- Potentially Malicious Hostname Hi, priority 1 means some thing required your. Indicators of compromise (iocs) are artifacts that indicate a potential intrusion. To keep it practical, indicators of compromise (iocs) are technical data that can be used to reliably identify malicious activities or. This guide explores the types of iocs, their. These are red flags of cyberattacks like. Indicators of compromise, or iocs,. Indicator-Compromise .Com- Potentially Malicious Hostname.
From www.xcitium.com
What are Indicators of Compromise Security? IOC Meaning Indicator-Compromise .Com- Potentially Malicious Hostname Indicators of compromise, or iocs, are indicators and proof of a data breach that is often discovered after a cyber attack. Hi, priority 1 means some thing required your. To keep it practical, indicators of compromise (iocs) are technical data that can be used to reliably identify malicious activities or. These are red flags of cyberattacks like. An indicator of. Indicator-Compromise .Com- Potentially Malicious Hostname.
From makrushin.com
Indicators of compromise as a way to reduce risk · Denis Makrushin Indicator-Compromise .Com- Potentially Malicious Hostname Indicators of compromise, or iocs, are indicators and proof of a data breach that is often discovered after a cyber attack. This guide explores the types of iocs, their. Hi, priority 1 means some thing required your. These are red flags of cyberattacks like. An indicator of compromise is a broad term for any detected signal of a potential cyberattack.. Indicator-Compromise .Com- Potentially Malicious Hostname.
From www.lepide.com
What are Indicators of Compromise? Indicator-Compromise .Com- Potentially Malicious Hostname Indicators of compromise, or iocs, are indicators and proof of a data breach that is often discovered after a cyber attack. Hi, priority 1 means some thing required your. Indicators of compromise (iocs) are artifacts that indicate a potential intrusion. An indicator of compromise is a broad term for any detected signal of a potential cyberattack. To keep it practical,. Indicator-Compromise .Com- Potentially Malicious Hostname.
From www.idstrong.com
Indicator of Compromise (IoC) vs. Indicator of Attack (IoA) Indicator-Compromise .Com- Potentially Malicious Hostname Indicators of compromise are behaviors or data which show that a data breach, intrusion, or cyberattack has occurred. Indicators of compromise, or iocs, are indicators and proof of a data breach that is often discovered after a cyber attack. Indicators of compromise (iocs) are artifacts that indicate a potential intrusion. These are red flags of cyberattacks like. An indicator of. Indicator-Compromise .Com- Potentially Malicious Hostname.
From www.wallarm.com
What are Indicators of Compromise (IOC)? Indicator-Compromise .Com- Potentially Malicious Hostname Indicators of compromise are behaviors or data which show that a data breach, intrusion, or cyberattack has occurred. This guide explores the types of iocs, their. Indicators of compromise (iocs) are artifacts that indicate a potential intrusion. To keep it practical, indicators of compromise (iocs) are technical data that can be used to reliably identify malicious activities or. An indicator. Indicator-Compromise .Com- Potentially Malicious Hostname.
From www.linkedin.com
Searching for unsigned DLLs as indicator of compromise Indicator-Compromise .Com- Potentially Malicious Hostname Hi, priority 1 means some thing required your. These are red flags of cyberattacks like. Indicators of compromise (iocs) are artifacts that indicate a potential intrusion. Indicators of compromise, or iocs, are indicators and proof of a data breach that is often discovered after a cyber attack. Indicators of compromise are behaviors or data which show that a data breach,. Indicator-Compromise .Com- Potentially Malicious Hostname.
From cyberhoot.com
Indicators of Compromise (IoC) CyberHoot Indicator-Compromise .Com- Potentially Malicious Hostname Indicators of compromise (iocs) are artifacts that indicate a potential intrusion. An indicator of compromise is a broad term for any detected signal of a potential cyberattack. Indicators of compromise, or iocs, are indicators and proof of a data breach that is often discovered after a cyber attack. To keep it practical, indicators of compromise (iocs) are technical data that. Indicator-Compromise .Com- Potentially Malicious Hostname.
From developers.tetrascience.com
IDBS Connector Troubleshooting Indicator-Compromise .Com- Potentially Malicious Hostname This guide explores the types of iocs, their. To keep it practical, indicators of compromise (iocs) are technical data that can be used to reliably identify malicious activities or. Indicators of compromise (iocs) are artifacts that indicate a potential intrusion. These are red flags of cyberattacks like. Indicators of compromise are behaviors or data which show that a data breach,. Indicator-Compromise .Com- Potentially Malicious Hostname.
From www.youtube.com
How to Generate an Indicator of Compromise (IOC) File YouTube Indicator-Compromise .Com- Potentially Malicious Hostname Indicators of compromise are behaviors or data which show that a data breach, intrusion, or cyberattack has occurred. To keep it practical, indicators of compromise (iocs) are technical data that can be used to reliably identify malicious activities or. Indicators of compromise, or iocs, are indicators and proof of a data breach that is often discovered after a cyber attack.. Indicator-Compromise .Com- Potentially Malicious Hostname.
From blog.threat.zone
Glossary Indicator of Compromise VS Indicator of Attack Indicator-Compromise .Com- Potentially Malicious Hostname Indicators of compromise, or iocs, are indicators and proof of a data breach that is often discovered after a cyber attack. This guide explores the types of iocs, their. An indicator of compromise is a broad term for any detected signal of a potential cyberattack. Hi, priority 1 means some thing required your. Indicators of compromise are behaviors or data. Indicator-Compromise .Com- Potentially Malicious Hostname.
From help.sumologic.com
Automations in Cloud SIEM Sumo Logic Docs Indicator-Compromise .Com- Potentially Malicious Hostname These are red flags of cyberattacks like. Indicators of compromise (iocs) are artifacts that indicate a potential intrusion. To keep it practical, indicators of compromise (iocs) are technical data that can be used to reliably identify malicious activities or. An indicator of compromise is a broad term for any detected signal of a potential cyberattack. Indicators of compromise, or iocs,. Indicator-Compromise .Com- Potentially Malicious Hostname.
From exobbptro.blob.core.windows.net
Indicator Of Compromise Sample at Arthur Carnes blog Indicator-Compromise .Com- Potentially Malicious Hostname Indicators of compromise are behaviors or data which show that a data breach, intrusion, or cyberattack has occurred. Hi, priority 1 means some thing required your. This guide explores the types of iocs, their. Indicators of compromise, or iocs, are indicators and proof of a data breach that is often discovered after a cyber attack. These are red flags of. Indicator-Compromise .Com- Potentially Malicious Hostname.
From blog.threat.zone
Inside Zone Indicator of Compromise (IoC) Indicator-Compromise .Com- Potentially Malicious Hostname This guide explores the types of iocs, their. Hi, priority 1 means some thing required your. Indicators of compromise, or iocs, are indicators and proof of a data breach that is often discovered after a cyber attack. These are red flags of cyberattacks like. To keep it practical, indicators of compromise (iocs) are technical data that can be used to. Indicator-Compromise .Com- Potentially Malicious Hostname.
From techgenix.com
How Can an Indicator of Compromise (IOC) Help You in Cybersecurity? Indicator-Compromise .Com- Potentially Malicious Hostname Indicators of compromise (iocs) are artifacts that indicate a potential intrusion. These are red flags of cyberattacks like. Indicators of compromise are behaviors or data which show that a data breach, intrusion, or cyberattack has occurred. To keep it practical, indicators of compromise (iocs) are technical data that can be used to reliably identify malicious activities or. Hi, priority 1. Indicator-Compromise .Com- Potentially Malicious Hostname.
From www.youtube.com
What is IOC and IOA Indicator of Attack and Indicator of Compromise Indicator-Compromise .Com- Potentially Malicious Hostname These are red flags of cyberattacks like. Indicators of compromise (iocs) are artifacts that indicate a potential intrusion. This guide explores the types of iocs, their. To keep it practical, indicators of compromise (iocs) are technical data that can be used to reliably identify malicious activities or. Hi, priority 1 means some thing required your. Indicators of compromise are behaviors. Indicator-Compromise .Com- Potentially Malicious Hostname.
From www.trendmicro.com.my
Empowering the Analyst Indicators of Compromise Security News Indicator-Compromise .Com- Potentially Malicious Hostname Indicators of compromise are behaviors or data which show that a data breach, intrusion, or cyberattack has occurred. An indicator of compromise is a broad term for any detected signal of a potential cyberattack. Indicators of compromise (iocs) are artifacts that indicate a potential intrusion. These are red flags of cyberattacks like. Indicators of compromise, or iocs, are indicators and. Indicator-Compromise .Com- Potentially Malicious Hostname.
From www.youtube.com
DLL Hijacking Attack Malicious DLL in C++ Indicator of Compromise Indicator-Compromise .Com- Potentially Malicious Hostname Hi, priority 1 means some thing required your. An indicator of compromise is a broad term for any detected signal of a potential cyberattack. These are red flags of cyberattacks like. Indicators of compromise (iocs) are artifacts that indicate a potential intrusion. Indicators of compromise, or iocs, are indicators and proof of a data breach that is often discovered after. Indicator-Compromise .Com- Potentially Malicious Hostname.
From www.sekoia.io
What is an Indicator of Compromise (IoC)? SEKOIA.IO Indicator-Compromise .Com- Potentially Malicious Hostname These are red flags of cyberattacks like. Indicators of compromise are behaviors or data which show that a data breach, intrusion, or cyberattack has occurred. Indicators of compromise (iocs) are artifacts that indicate a potential intrusion. This guide explores the types of iocs, their. An indicator of compromise is a broad term for any detected signal of a potential cyberattack.. Indicator-Compromise .Com- Potentially Malicious Hostname.
From www.netsecurity.com
Indicator of Compromise (IoC) vs. Indicator of Attack (IoA Indicator-Compromise .Com- Potentially Malicious Hostname Hi, priority 1 means some thing required your. An indicator of compromise is a broad term for any detected signal of a potential cyberattack. This guide explores the types of iocs, their. Indicators of compromise, or iocs, are indicators and proof of a data breach that is often discovered after a cyber attack. These are red flags of cyberattacks like.. Indicator-Compromise .Com- Potentially Malicious Hostname.
From fineproxy.org
Indicator of Compromise (IOC) FineProxy Glossary Indicator-Compromise .Com- Potentially Malicious Hostname Indicators of compromise are behaviors or data which show that a data breach, intrusion, or cyberattack has occurred. To keep it practical, indicators of compromise (iocs) are technical data that can be used to reliably identify malicious activities or. An indicator of compromise is a broad term for any detected signal of a potential cyberattack. These are red flags of. Indicator-Compromise .Com- Potentially Malicious Hostname.
From blogs.cisco.com
Indicators of Compromise and where to find them Cisco Blogs Indicator-Compromise .Com- Potentially Malicious Hostname An indicator of compromise is a broad term for any detected signal of a potential cyberattack. Hi, priority 1 means some thing required your. Indicators of compromise (iocs) are artifacts that indicate a potential intrusion. Indicators of compromise, or iocs, are indicators and proof of a data breach that is often discovered after a cyber attack. These are red flags. Indicator-Compromise .Com- Potentially Malicious Hostname.
From securitymadesimple.org
What is an Indicator of Compromise Indicator-Compromise .Com- Potentially Malicious Hostname Indicators of compromise, or iocs, are indicators and proof of a data breach that is often discovered after a cyber attack. To keep it practical, indicators of compromise (iocs) are technical data that can be used to reliably identify malicious activities or. An indicator of compromise is a broad term for any detected signal of a potential cyberattack. Indicators of. Indicator-Compromise .Com- Potentially Malicious Hostname.
From www.e-spincorp.com
Indicator of Compromise (IOC) ESPIN Group Indicator-Compromise .Com- Potentially Malicious Hostname To keep it practical, indicators of compromise (iocs) are technical data that can be used to reliably identify malicious activities or. This guide explores the types of iocs, their. Indicators of compromise, or iocs, are indicators and proof of a data breach that is often discovered after a cyber attack. Indicators of compromise are behaviors or data which show that. Indicator-Compromise .Com- Potentially Malicious Hostname.
From www.semanticscholar.org
Indicator of compromise Semantic Scholar Indicator-Compromise .Com- Potentially Malicious Hostname These are red flags of cyberattacks like. Hi, priority 1 means some thing required your. Indicators of compromise, or iocs, are indicators and proof of a data breach that is often discovered after a cyber attack. To keep it practical, indicators of compromise (iocs) are technical data that can be used to reliably identify malicious activities or. An indicator of. Indicator-Compromise .Com- Potentially Malicious Hostname.
From flare.io
Indicators of Compromise (IOCs) and External Risk Monitoring Flare Indicator-Compromise .Com- Potentially Malicious Hostname An indicator of compromise is a broad term for any detected signal of a potential cyberattack. Indicators of compromise (iocs) are artifacts that indicate a potential intrusion. These are red flags of cyberattacks like. Indicators of compromise, or iocs, are indicators and proof of a data breach that is often discovered after a cyber attack. Indicators of compromise are behaviors. Indicator-Compromise .Com- Potentially Malicious Hostname.
From www.sentinelone.com
What are Indicators of Compromise (IoCs)? An Easy Guide Indicator-Compromise .Com- Potentially Malicious Hostname Indicators of compromise are behaviors or data which show that a data breach, intrusion, or cyberattack has occurred. Indicators of compromise (iocs) are artifacts that indicate a potential intrusion. An indicator of compromise is a broad term for any detected signal of a potential cyberattack. These are red flags of cyberattacks like. Hi, priority 1 means some thing required your.. Indicator-Compromise .Com- Potentially Malicious Hostname.
From www.scaler.com
How to Check Hostname in Linux? Scaler Topics Indicator-Compromise .Com- Potentially Malicious Hostname To keep it practical, indicators of compromise (iocs) are technical data that can be used to reliably identify malicious activities or. Indicators of compromise are behaviors or data which show that a data breach, intrusion, or cyberattack has occurred. Indicators of compromise (iocs) are artifacts that indicate a potential intrusion. Indicators of compromise, or iocs, are indicators and proof of. Indicator-Compromise .Com- Potentially Malicious Hostname.