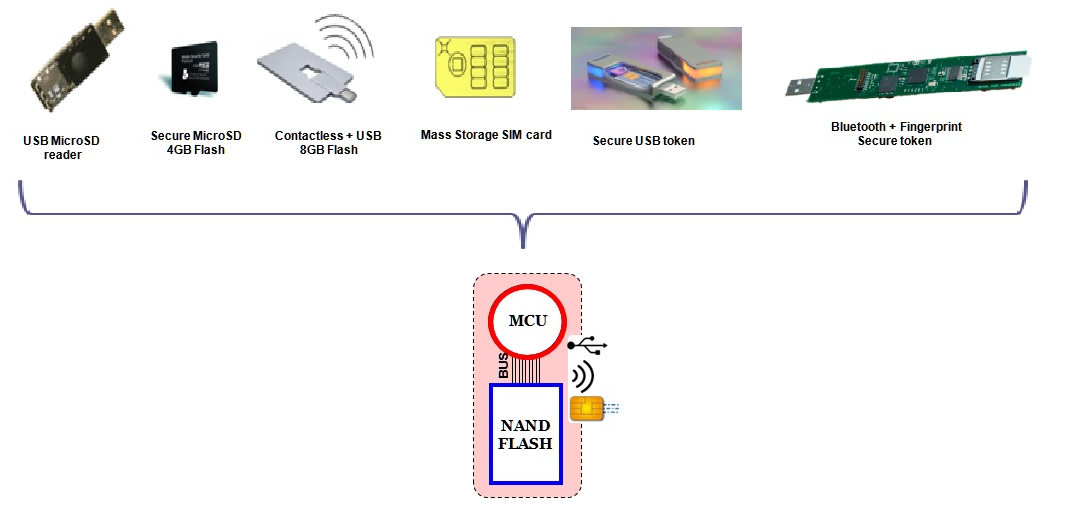
Hardware Protection Examples . Here's what we need to know. This protection can be in the form of physical. Hardware security is vulnerability protection that comes in the form of a physical device rather than software that's installed on the hardware of a. Hardware security is a domain of enterprise security that focuses on protecting all physical devices, machines, and peripherals. Hardware security has evolved into a pressing it issue as enterprises install autonomous sensors, controllers and monitors. Cyberspace does not exist in a vacuum. All cyber systems are built using the physical hardware of the. Hardware is a cybersecurity risk.
from project.inria.fr
Here's what we need to know. Hardware security is vulnerability protection that comes in the form of a physical device rather than software that's installed on the hardware of a. Cyberspace does not exist in a vacuum. Hardware is a cybersecurity risk. Hardware security has evolved into a pressing it issue as enterprises install autonomous sensors, controllers and monitors. All cyber systems are built using the physical hardware of the. This protection can be in the form of physical. Hardware security is a domain of enterprise security that focuses on protecting all physical devices, machines, and peripherals.
Hardware security PlugDB
Hardware Protection Examples Hardware security is vulnerability protection that comes in the form of a physical device rather than software that's installed on the hardware of a. Here's what we need to know. Cyberspace does not exist in a vacuum. Hardware is a cybersecurity risk. This protection can be in the form of physical. Hardware security is a domain of enterprise security that focuses on protecting all physical devices, machines, and peripherals. Hardware security is vulnerability protection that comes in the form of a physical device rather than software that's installed on the hardware of a. All cyber systems are built using the physical hardware of the. Hardware security has evolved into a pressing it issue as enterprises install autonomous sensors, controllers and monitors.
From www.thesecuritybuddy.com
What is the Hardware Security Module (HSM) and how does it work? The Hardware Protection Examples Here's what we need to know. Hardware is a cybersecurity risk. This protection can be in the form of physical. Cyberspace does not exist in a vacuum. Hardware security has evolved into a pressing it issue as enterprises install autonomous sensors, controllers and monitors. Hardware security is a domain of enterprise security that focuses on protecting all physical devices, machines,. Hardware Protection Examples.
From www.slideserve.com
PPT Chapter 2 ComputerSystem Structures PowerPoint Presentation Hardware Protection Examples Here's what we need to know. Hardware security has evolved into a pressing it issue as enterprises install autonomous sensors, controllers and monitors. Hardware security is a domain of enterprise security that focuses on protecting all physical devices, machines, and peripherals. Hardware is a cybersecurity risk. Hardware security is vulnerability protection that comes in the form of a physical device. Hardware Protection Examples.
From locker.io
What are hardware security keys, and should you use them? Hardware Protection Examples Hardware security is a domain of enterprise security that focuses on protecting all physical devices, machines, and peripherals. Hardware security is vulnerability protection that comes in the form of a physical device rather than software that's installed on the hardware of a. Cyberspace does not exist in a vacuum. Hardware security has evolved into a pressing it issue as enterprises. Hardware Protection Examples.
From www.spiceworks.com
Top 10 Firewall Hardware Devices for 2022 Toolbox Spiceworks Hardware Protection Examples Here's what we need to know. All cyber systems are built using the physical hardware of the. Hardware security is vulnerability protection that comes in the form of a physical device rather than software that's installed on the hardware of a. Hardware is a cybersecurity risk. Hardware security is a domain of enterprise security that focuses on protecting all physical. Hardware Protection Examples.
From www.slideserve.com
PPT CHAPTER 2 COMPUTERSYSTEM STRUCTURES PowerPoint Presentation Hardware Protection Examples Hardware security is vulnerability protection that comes in the form of a physical device rather than software that's installed on the hardware of a. Hardware is a cybersecurity risk. Cyberspace does not exist in a vacuum. Hardware security is a domain of enterprise security that focuses on protecting all physical devices, machines, and peripherals. This protection can be in the. Hardware Protection Examples.
From www.youtube.com
What are hardware security modules (HSM), why we need them and how they Hardware Protection Examples This protection can be in the form of physical. Hardware security is a domain of enterprise security that focuses on protecting all physical devices, machines, and peripherals. Cyberspace does not exist in a vacuum. Hardware is a cybersecurity risk. Hardware security has evolved into a pressing it issue as enterprises install autonomous sensors, controllers and monitors. All cyber systems are. Hardware Protection Examples.
From www.techdesignforums.com
Using hardware secure modules to protect SoCs Tech Design Forum Hardware Protection Examples Hardware security is vulnerability protection that comes in the form of a physical device rather than software that's installed on the hardware of a. This protection can be in the form of physical. Cyberspace does not exist in a vacuum. Hardware is a cybersecurity risk. Here's what we need to know. Hardware security has evolved into a pressing it issue. Hardware Protection Examples.
From www.quality-assurance-solutions.com
Computer Protection Security Guidelines Hardware Protection Examples Cyberspace does not exist in a vacuum. Hardware security is a domain of enterprise security that focuses on protecting all physical devices, machines, and peripherals. This protection can be in the form of physical. Hardware security has evolved into a pressing it issue as enterprises install autonomous sensors, controllers and monitors. Here's what we need to know. Hardware is a. Hardware Protection Examples.
From www.slideserve.com
PPT Memory Addressing in Linux (Chap. 2 in Understanding the Linux Hardware Protection Examples Here's what we need to know. Hardware security has evolved into a pressing it issue as enterprises install autonomous sensors, controllers and monitors. All cyber systems are built using the physical hardware of the. Hardware security is a domain of enterprise security that focuses on protecting all physical devices, machines, and peripherals. This protection can be in the form of. Hardware Protection Examples.
From www.youtube.com
Hardware Protection Levels YouTube Hardware Protection Examples Hardware security has evolved into a pressing it issue as enterprises install autonomous sensors, controllers and monitors. This protection can be in the form of physical. Cyberspace does not exist in a vacuum. All cyber systems are built using the physical hardware of the. Hardware is a cybersecurity risk. Here's what we need to know. Hardware security is a domain. Hardware Protection Examples.
From cheapsslweb.com
Extensive Overview of Hardware Security Modules (HSMs) Hardware Protection Examples Hardware security has evolved into a pressing it issue as enterprises install autonomous sensors, controllers and monitors. This protection can be in the form of physical. Hardware is a cybersecurity risk. Here's what we need to know. Hardware security is vulnerability protection that comes in the form of a physical device rather than software that's installed on the hardware of. Hardware Protection Examples.
From www.thesslstore.com
What Is a Hardware Security Module? HSMs Explained Hashed Out by The Hardware Protection Examples This protection can be in the form of physical. Hardware security has evolved into a pressing it issue as enterprises install autonomous sensors, controllers and monitors. Here's what we need to know. Cyberspace does not exist in a vacuum. Hardware security is a domain of enterprise security that focuses on protecting all physical devices, machines, and peripherals. Hardware is a. Hardware Protection Examples.
From certera.com
Hardware Security Modules (HSMs) Comprehensive Guide Hardware Protection Examples Hardware security is a domain of enterprise security that focuses on protecting all physical devices, machines, and peripherals. Here's what we need to know. This protection can be in the form of physical. Hardware security has evolved into a pressing it issue as enterprises install autonomous sensors, controllers and monitors. Hardware security is vulnerability protection that comes in the form. Hardware Protection Examples.
From www.sketchbubble.com
Hardware Security Vs Software Security PowerPoint Template and Google Hardware Protection Examples Here's what we need to know. Hardware security is vulnerability protection that comes in the form of a physical device rather than software that's installed on the hardware of a. Cyberspace does not exist in a vacuum. Hardware security has evolved into a pressing it issue as enterprises install autonomous sensors, controllers and monitors. All cyber systems are built using. Hardware Protection Examples.
From www.helpnetsecurity.com
Hardware security Emerging attacks and protection mechanisms Help Hardware Protection Examples Hardware security is a domain of enterprise security that focuses on protecting all physical devices, machines, and peripherals. Hardware security is vulnerability protection that comes in the form of a physical device rather than software that's installed on the hardware of a. This protection can be in the form of physical. Hardware security has evolved into a pressing it issue. Hardware Protection Examples.
From www.atatus.com
Application Security Definition, Types, Tools, Approaches Hardware Protection Examples Here's what we need to know. Cyberspace does not exist in a vacuum. Hardware is a cybersecurity risk. Hardware security has evolved into a pressing it issue as enterprises install autonomous sensors, controllers and monitors. Hardware security is vulnerability protection that comes in the form of a physical device rather than software that's installed on the hardware of a. This. Hardware Protection Examples.
From project.inria.fr
Hardware security PlugDB Hardware Protection Examples This protection can be in the form of physical. All cyber systems are built using the physical hardware of the. Here's what we need to know. Hardware security has evolved into a pressing it issue as enterprises install autonomous sensors, controllers and monitors. Hardware security is a domain of enterprise security that focuses on protecting all physical devices, machines, and. Hardware Protection Examples.
From www.youtube.com
Hardware Protection Operating system protection YouTube Hardware Protection Examples Hardware security is a domain of enterprise security that focuses on protecting all physical devices, machines, and peripherals. Hardware security is vulnerability protection that comes in the form of a physical device rather than software that's installed on the hardware of a. This protection can be in the form of physical. All cyber systems are built using the physical hardware. Hardware Protection Examples.
From www.youtube.com
Class 19c Intro to OS (Hardware Protection) YouTube Hardware Protection Examples This protection can be in the form of physical. Hardware is a cybersecurity risk. Cyberspace does not exist in a vacuum. Hardware security is vulnerability protection that comes in the form of a physical device rather than software that's installed on the hardware of a. All cyber systems are built using the physical hardware of the. Hardware security is a. Hardware Protection Examples.
From www.slideserve.com
PPT CHAPTER 2 COMPUTERSYSTEM STRUCTURES PowerPoint Presentation Hardware Protection Examples Hardware is a cybersecurity risk. Hardware security has evolved into a pressing it issue as enterprises install autonomous sensors, controllers and monitors. Hardware security is vulnerability protection that comes in the form of a physical device rather than software that's installed on the hardware of a. Here's what we need to know. Cyberspace does not exist in a vacuum. This. Hardware Protection Examples.
From www.youtube.com
How to use a Hardware Security Module Securely YouTube Hardware Protection Examples Hardware security has evolved into a pressing it issue as enterprises install autonomous sensors, controllers and monitors. Cyberspace does not exist in a vacuum. Here's what we need to know. Hardware security is a domain of enterprise security that focuses on protecting all physical devices, machines, and peripherals. All cyber systems are built using the physical hardware of the. Hardware. Hardware Protection Examples.
From www.spiceworks.com
What Is Hardware Security? Definition, Threats, and Best Practices Hardware Protection Examples Hardware is a cybersecurity risk. Hardware security is vulnerability protection that comes in the form of a physical device rather than software that's installed on the hardware of a. Hardware security is a domain of enterprise security that focuses on protecting all physical devices, machines, and peripherals. All cyber systems are built using the physical hardware of the. Cyberspace does. Hardware Protection Examples.
From m2pfintech.com
Cryptographic Keys and Hardware Security Modules An IntroductionM2P Hardware Protection Examples Hardware is a cybersecurity risk. Hardware security is vulnerability protection that comes in the form of a physical device rather than software that's installed on the hardware of a. Here's what we need to know. Hardware security has evolved into a pressing it issue as enterprises install autonomous sensors, controllers and monitors. Cyberspace does not exist in a vacuum. This. Hardware Protection Examples.
From www.spiceworks.com
What Is Hardware Security? Definition, Threats, and Best Practices Hardware Protection Examples Hardware security is a domain of enterprise security that focuses on protecting all physical devices, machines, and peripherals. Here's what we need to know. Hardware security has evolved into a pressing it issue as enterprises install autonomous sensors, controllers and monitors. Hardware is a cybersecurity risk. Hardware security is vulnerability protection that comes in the form of a physical device. Hardware Protection Examples.
From www.slideserve.com
PPT Hardware Security Mechanisms PowerPoint Presentation, free Hardware Protection Examples Cyberspace does not exist in a vacuum. Hardware security is vulnerability protection that comes in the form of a physical device rather than software that's installed on the hardware of a. Hardware security has evolved into a pressing it issue as enterprises install autonomous sensors, controllers and monitors. Hardware security is a domain of enterprise security that focuses on protecting. Hardware Protection Examples.
From allabouttesting.org
Hardware Security Assessment Brief Overview All About Testing Hardware Protection Examples Hardware security is a domain of enterprise security that focuses on protecting all physical devices, machines, and peripherals. Hardware security has evolved into a pressing it issue as enterprises install autonomous sensors, controllers and monitors. Hardware security is vulnerability protection that comes in the form of a physical device rather than software that's installed on the hardware of a. Cyberspace. Hardware Protection Examples.
From www.slideserve.com
PPT Operating System Concepts Implementation and Differences Hardware Protection Examples Hardware is a cybersecurity risk. Hardware security is vulnerability protection that comes in the form of a physical device rather than software that's installed on the hardware of a. This protection can be in the form of physical. Hardware security is a domain of enterprise security that focuses on protecting all physical devices, machines, and peripherals. Cyberspace does not exist. Hardware Protection Examples.
From www.studocu.com
What is hardware security What is hardware security? Hardware Hardware Protection Examples This protection can be in the form of physical. Here's what we need to know. Cyberspace does not exist in a vacuum. Hardware is a cybersecurity risk. Hardware security has evolved into a pressing it issue as enterprises install autonomous sensors, controllers and monitors. Hardware security is vulnerability protection that comes in the form of a physical device rather than. Hardware Protection Examples.
From www.n-coe.in
Top 4 'Hardware Security' companies revolutionising the way security Hardware Protection Examples This protection can be in the form of physical. Hardware security has evolved into a pressing it issue as enterprises install autonomous sensors, controllers and monitors. Hardware security is vulnerability protection that comes in the form of a physical device rather than software that's installed on the hardware of a. Cyberspace does not exist in a vacuum. Hardware is a. Hardware Protection Examples.
From www.slideserve.com
PPT Memory Management PowerPoint Presentation, free download ID382469 Hardware Protection Examples Hardware security is a domain of enterprise security that focuses on protecting all physical devices, machines, and peripherals. Hardware security has evolved into a pressing it issue as enterprises install autonomous sensors, controllers and monitors. Hardware security is vulnerability protection that comes in the form of a physical device rather than software that's installed on the hardware of a. All. Hardware Protection Examples.
From gkaccess.com
Hardware Security Examples in Cyber Security GateKeeper 2FA Hardware Protection Examples All cyber systems are built using the physical hardware of the. Hardware security has evolved into a pressing it issue as enterprises install autonomous sensors, controllers and monitors. Hardware security is vulnerability protection that comes in the form of a physical device rather than software that's installed on the hardware of a. This protection can be in the form of. Hardware Protection Examples.
From www.spiceworks.com
What Is Hardware Security? Definition, Threats, and Best Practices Hardware Protection Examples Hardware security is a domain of enterprise security that focuses on protecting all physical devices, machines, and peripherals. Hardware security has evolved into a pressing it issue as enterprises install autonomous sensors, controllers and monitors. Cyberspace does not exist in a vacuum. This protection can be in the form of physical. All cyber systems are built using the physical hardware. Hardware Protection Examples.
From www.slideserve.com
PPT Outline PowerPoint Presentation, free download ID360368 Hardware Protection Examples Hardware security is a domain of enterprise security that focuses on protecting all physical devices, machines, and peripherals. Hardware security has evolved into a pressing it issue as enterprises install autonomous sensors, controllers and monitors. This protection can be in the form of physical. Hardware security is vulnerability protection that comes in the form of a physical device rather than. Hardware Protection Examples.
From www.conceptdraw.com
Network Security Network Security Devices Fire and Emergency Plans Hardware Protection Examples Cyberspace does not exist in a vacuum. Hardware security is a domain of enterprise security that focuses on protecting all physical devices, machines, and peripherals. This protection can be in the form of physical. All cyber systems are built using the physical hardware of the. Hardware security has evolved into a pressing it issue as enterprises install autonomous sensors, controllers. Hardware Protection Examples.
From www.slideteam.net
Security Controls To Protect All Hardware Devices Presentation Hardware Protection Examples Cyberspace does not exist in a vacuum. Here's what we need to know. All cyber systems are built using the physical hardware of the. Hardware security has evolved into a pressing it issue as enterprises install autonomous sensors, controllers and monitors. Hardware security is a domain of enterprise security that focuses on protecting all physical devices, machines, and peripherals. Hardware. Hardware Protection Examples.