What Is Pam Key . Privileged access management (pam) consists of the cybersecurity strategies and technologies for exerting control over the elevated (“privileged”) access and permissions for. It's a crucial defence line for organisations against cyber threats. A subset of iam, focused on defining and controlling who or what has the authority to make changes to a network or device. Privileged access management (pam) is the cybersecurity discipline that governs and secures privileged accounts (such as. Privileged access management helps organizations manage and secure access to their most critical systems, applications, and data,. Privileged access management is a category of cybersecurity solutions that enables security and it teams to securely manage access for all privileged identities in an enterprise environment. Privileged access management (pam) is not just a cybersecurity buzzword;
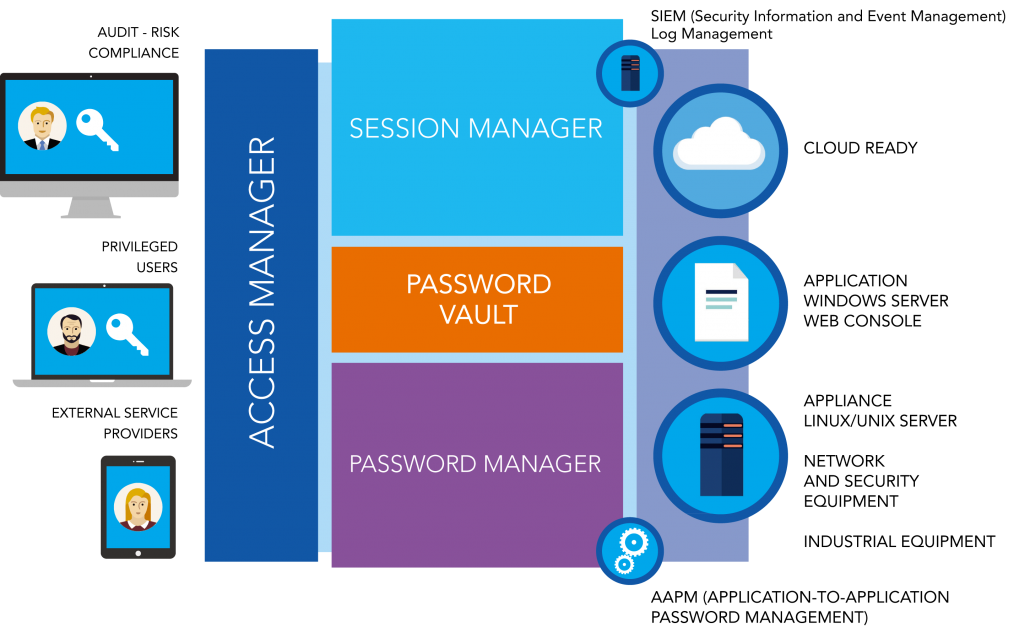
from www.wallix.com
A subset of iam, focused on defining and controlling who or what has the authority to make changes to a network or device. Privileged access management (pam) is the cybersecurity discipline that governs and secures privileged accounts (such as. Privileged access management (pam) is not just a cybersecurity buzzword; Privileged access management (pam) consists of the cybersecurity strategies and technologies for exerting control over the elevated (“privileged”) access and permissions for. Privileged access management is a category of cybersecurity solutions that enables security and it teams to securely manage access for all privileged identities in an enterprise environment. Privileged access management helps organizations manage and secure access to their most critical systems, applications, and data,. It's a crucial defence line for organisations against cyber threats.
Privileged Access Management Features WALLIX
What Is Pam Key A subset of iam, focused on defining and controlling who or what has the authority to make changes to a network or device. Privileged access management is a category of cybersecurity solutions that enables security and it teams to securely manage access for all privileged identities in an enterprise environment. A subset of iam, focused on defining and controlling who or what has the authority to make changes to a network or device. It's a crucial defence line for organisations against cyber threats. Privileged access management helps organizations manage and secure access to their most critical systems, applications, and data,. Privileged access management (pam) is not just a cybersecurity buzzword; Privileged access management (pam) consists of the cybersecurity strategies and technologies for exerting control over the elevated (“privileged”) access and permissions for. Privileged access management (pam) is the cybersecurity discipline that governs and secures privileged accounts (such as.
From docs.oracle.com
About PAM Managing Authentication in Oracle® Solaris 11.4 What Is Pam Key Privileged access management helps organizations manage and secure access to their most critical systems, applications, and data,. Privileged access management (pam) consists of the cybersecurity strategies and technologies for exerting control over the elevated (“privileged”) access and permissions for. Privileged access management (pam) is the cybersecurity discipline that governs and secures privileged accounts (such as. It's a crucial defence line. What Is Pam Key.
From maheshcg.me
A Closer Look at Identity and Access Management (IAM) and Privileged What Is Pam Key Privileged access management (pam) is the cybersecurity discipline that governs and secures privileged accounts (such as. Privileged access management helps organizations manage and secure access to their most critical systems, applications, and data,. It's a crucial defence line for organisations against cyber threats. Privileged access management is a category of cybersecurity solutions that enables security and it teams to securely. What Is Pam Key.
From schematicbuiliskt.z14.web.core.windows.net
What Is Pam Access What Is Pam Key Privileged access management (pam) consists of the cybersecurity strategies and technologies for exerting control over the elevated (“privileged”) access and permissions for. Privileged access management (pam) is the cybersecurity discipline that governs and secures privileged accounts (such as. A subset of iam, focused on defining and controlling who or what has the authority to make changes to a network or. What Is Pam Key.
From security-architect.com
Privileged Account Management (PAM) is Necessary, but Deploying it What Is Pam Key Privileged access management helps organizations manage and secure access to their most critical systems, applications, and data,. Privileged access management (pam) is the cybersecurity discipline that governs and secures privileged accounts (such as. It's a crucial defence line for organisations against cyber threats. A subset of iam, focused on defining and controlling who or what has the authority to make. What Is Pam Key.
From www.kuppingercole.com
Enterprise Guide Privileged Access Management What Is Pam Key Privileged access management (pam) is the cybersecurity discipline that governs and secures privileged accounts (such as. Privileged access management is a category of cybersecurity solutions that enables security and it teams to securely manage access for all privileged identities in an enterprise environment. A subset of iam, focused on defining and controlling who or what has the authority to make. What Is Pam Key.
From www.idtdna.com
What is the PAM sequence for CRISPR and where is it? IDT What Is Pam Key Privileged access management is a category of cybersecurity solutions that enables security and it teams to securely manage access for all privileged identities in an enterprise environment. Privileged access management helps organizations manage and secure access to their most critical systems, applications, and data,. It's a crucial defence line for organisations against cyber threats. Privileged access management (pam) is the. What Is Pam Key.
From www.researchgate.net
6. Artist Pamela Key's reconstruction of the Marana Platform Mound and What Is Pam Key Privileged access management (pam) is not just a cybersecurity buzzword; Privileged access management helps organizations manage and secure access to their most critical systems, applications, and data,. Privileged access management (pam) consists of the cybersecurity strategies and technologies for exerting control over the elevated (“privileged”) access and permissions for. Privileged access management is a category of cybersecurity solutions that enables. What Is Pam Key.
From wislibrary.org
Pam Collins Key Interventions & Documentation Strategies During a What Is Pam Key Privileged access management is a category of cybersecurity solutions that enables security and it teams to securely manage access for all privileged identities in an enterprise environment. Privileged access management (pam) is not just a cybersecurity buzzword; It's a crucial defence line for organisations against cyber threats. Privileged access management (pam) consists of the cybersecurity strategies and technologies for exerting. What Is Pam Key.
From www.youtube.com
What Is PIM or PAM? YouTube What Is Pam Key Privileged access management (pam) consists of the cybersecurity strategies and technologies for exerting control over the elevated (“privileged”) access and permissions for. Privileged access management (pam) is not just a cybersecurity buzzword; It's a crucial defence line for organisations against cyber threats. Privileged access management helps organizations manage and secure access to their most critical systems, applications, and data,. A. What Is Pam Key.
From www.cxoinsightme.com
Why PAM is Key for Partner Organisations CXO Insight Middle East What Is Pam Key Privileged access management (pam) is the cybersecurity discipline that governs and secures privileged accounts (such as. Privileged access management helps organizations manage and secure access to their most critical systems, applications, and data,. Privileged access management (pam) is not just a cybersecurity buzzword; It's a crucial defence line for organisations against cyber threats. A subset of iam, focused on defining. What Is Pam Key.
From www.keepersecurity.com
What Is PAM in Cybersecurity? How PAM Helps Protect Organizations What Is Pam Key Privileged access management (pam) consists of the cybersecurity strategies and technologies for exerting control over the elevated (“privileged”) access and permissions for. Privileged access management (pam) is the cybersecurity discipline that governs and secures privileged accounts (such as. Privileged access management is a category of cybersecurity solutions that enables security and it teams to securely manage access for all privileged. What Is Pam Key.
From www.key-programmer.com
Original MasterKey III MK3 Key Programmer is available What Is Pam Key Privileged access management (pam) is the cybersecurity discipline that governs and secures privileged accounts (such as. Privileged access management helps organizations manage and secure access to their most critical systems, applications, and data,. Privileged access management is a category of cybersecurity solutions that enables security and it teams to securely manage access for all privileged identities in an enterprise environment.. What Is Pam Key.
From www.securew2.com
IAM vs PAM What Is Pam Key A subset of iam, focused on defining and controlling who or what has the authority to make changes to a network or device. Privileged access management (pam) is the cybersecurity discipline that governs and secures privileged accounts (such as. Privileged access management (pam) consists of the cybersecurity strategies and technologies for exerting control over the elevated (“privileged”) access and permissions. What Is Pam Key.
From foller.me
Pam Key Facebook, Instagram, Twitter [Profiles] What Is Pam Key Privileged access management (pam) consists of the cybersecurity strategies and technologies for exerting control over the elevated (“privileged”) access and permissions for. Privileged access management is a category of cybersecurity solutions that enables security and it teams to securely manage access for all privileged identities in an enterprise environment. Privileged access management (pam) is the cybersecurity discipline that governs and. What Is Pam Key.
From delinea.com
What is Privileged Access Management (PAM)? Delinea What Is Pam Key Privileged access management (pam) is the cybersecurity discipline that governs and secures privileged accounts (such as. Privileged access management helps organizations manage and secure access to their most critical systems, applications, and data,. A subset of iam, focused on defining and controlling who or what has the authority to make changes to a network or device. Privileged access management (pam). What Is Pam Key.
From expertinsights.com
The Top 10 Privileged Access Management (PAM) Solutions Expert Insights What Is Pam Key Privileged access management helps organizations manage and secure access to their most critical systems, applications, and data,. A subset of iam, focused on defining and controlling who or what has the authority to make changes to a network or device. Privileged access management (pam) consists of the cybersecurity strategies and technologies for exerting control over the elevated (“privileged”) access and. What Is Pam Key.
From www.wallix.com
What is PAM? Privileged Access Management WALLIX What Is Pam Key Privileged access management is a category of cybersecurity solutions that enables security and it teams to securely manage access for all privileged identities in an enterprise environment. Privileged access management (pam) consists of the cybersecurity strategies and technologies for exerting control over the elevated (“privileged”) access and permissions for. Privileged access management helps organizations manage and secure access to their. What Is Pam Key.
From www.varonis.com
What is Privileged Access Management (PAM) and Why It’s Important to What Is Pam Key Privileged access management (pam) is not just a cybersecurity buzzword; Privileged access management (pam) consists of the cybersecurity strategies and technologies for exerting control over the elevated (“privileged”) access and permissions for. Privileged access management is a category of cybersecurity solutions that enables security and it teams to securely manage access for all privileged identities in an enterprise environment. A. What Is Pam Key.
From www.beyondtrust.com
What is Privileged Access Management (PAM)? BeyondTrust What Is Pam Key Privileged access management (pam) is not just a cybersecurity buzzword; Privileged access management helps organizations manage and secure access to their most critical systems, applications, and data,. Privileged access management is a category of cybersecurity solutions that enables security and it teams to securely manage access for all privileged identities in an enterprise environment. Privileged access management (pam) is the. What Is Pam Key.
From www.techtarget.com
What is partner account manager (PAM)? Definition from TechTarget What Is Pam Key Privileged access management (pam) is the cybersecurity discipline that governs and secures privileged accounts (such as. Privileged access management (pam) is not just a cybersecurity buzzword; Privileged access management is a category of cybersecurity solutions that enables security and it teams to securely manage access for all privileged identities in an enterprise environment. It's a crucial defence line for organisations. What Is Pam Key.
From blog.addgene.org
The PAM Requirement and Expanding CRISPR Beyond SpCas9 What Is Pam Key Privileged access management (pam) is the cybersecurity discipline that governs and secures privileged accounts (such as. Privileged access management (pam) is not just a cybersecurity buzzword; A subset of iam, focused on defining and controlling who or what has the authority to make changes to a network or device. Privileged access management (pam) consists of the cybersecurity strategies and technologies. What Is Pam Key.
From www.strongdm.com
What is PAM Security? Privileged Access Management Explained StrongDM What Is Pam Key A subset of iam, focused on defining and controlling who or what has the authority to make changes to a network or device. Privileged access management helps organizations manage and secure access to their most critical systems, applications, and data,. Privileged access management (pam) is not just a cybersecurity buzzword; Privileged access management is a category of cybersecurity solutions that. What Is Pam Key.
From www.spiceworks.com
Top 10 Privileged Access Management Solutions in 2021 Spiceworks What Is Pam Key Privileged access management (pam) is not just a cybersecurity buzzword; Privileged access management (pam) consists of the cybersecurity strategies and technologies for exerting control over the elevated (“privileged”) access and permissions for. Privileged access management is a category of cybersecurity solutions that enables security and it teams to securely manage access for all privileged identities in an enterprise environment. A. What Is Pam Key.
From www.zluri.com
Privileged Identity Management A Definite Guide Zluri What Is Pam Key Privileged access management (pam) is the cybersecurity discipline that governs and secures privileged accounts (such as. It's a crucial defence line for organisations against cyber threats. Privileged access management is a category of cybersecurity solutions that enables security and it teams to securely manage access for all privileged identities in an enterprise environment. A subset of iam, focused on defining. What Is Pam Key.
From www.kuppingercole.com
Enterprise Guide Privileged Access Management What Is Pam Key Privileged access management helps organizations manage and secure access to their most critical systems, applications, and data,. A subset of iam, focused on defining and controlling who or what has the authority to make changes to a network or device. Privileged access management (pam) consists of the cybersecurity strategies and technologies for exerting control over the elevated (“privileged”) access and. What Is Pam Key.
From www.strongdm.com
IAM vs. PAM Key Differences and How They Relate StrongDM What Is Pam Key Privileged access management is a category of cybersecurity solutions that enables security and it teams to securely manage access for all privileged identities in an enterprise environment. It's a crucial defence line for organisations against cyber threats. Privileged access management helps organizations manage and secure access to their most critical systems, applications, and data,. Privileged access management (pam) consists of. What Is Pam Key.
From www.laughingplace.com
Hulu Releases New Trailer and Key Art for Original Series “Pam & Tommy What Is Pam Key It's a crucial defence line for organisations against cyber threats. Privileged access management (pam) consists of the cybersecurity strategies and technologies for exerting control over the elevated (“privileged”) access and permissions for. Privileged access management is a category of cybersecurity solutions that enables security and it teams to securely manage access for all privileged identities in an enterprise environment. A. What Is Pam Key.
From www.youtube.com
Does Your PAM have these capabilities? YouTube What Is Pam Key Privileged access management (pam) is not just a cybersecurity buzzword; Privileged access management is a category of cybersecurity solutions that enables security and it teams to securely manage access for all privileged identities in an enterprise environment. It's a crucial defence line for organisations against cyber threats. Privileged access management (pam) is the cybersecurity discipline that governs and secures privileged. What Is Pam Key.
From www.ssh.com
Privileged Access Management (PAM) in the Cloud What Is Pam Key It's a crucial defence line for organisations against cyber threats. Privileged access management helps organizations manage and secure access to their most critical systems, applications, and data,. A subset of iam, focused on defining and controlling who or what has the authority to make changes to a network or device. Privileged access management is a category of cybersecurity solutions that. What Is Pam Key.
From www.majorkeytech.com
7 Features to Consider with Modern PAM Vendors MajorKey What Is Pam Key Privileged access management helps organizations manage and secure access to their most critical systems, applications, and data,. Privileged access management (pam) is not just a cybersecurity buzzword; Privileged access management (pam) consists of the cybersecurity strategies and technologies for exerting control over the elevated (“privileged”) access and permissions for. It's a crucial defence line for organisations against cyber threats. Privileged. What Is Pam Key.
From www.youtube.com
PAM (Pluggable Authentication Modules) in Linux YouTube What Is Pam Key Privileged access management (pam) is not just a cybersecurity buzzword; A subset of iam, focused on defining and controlling who or what has the authority to make changes to a network or device. Privileged access management is a category of cybersecurity solutions that enables security and it teams to securely manage access for all privileged identities in an enterprise environment.. What Is Pam Key.
From www.openpr.com
Industry Future of Privileged Access Management (PAM) Software What Is Pam Key Privileged access management (pam) is the cybersecurity discipline that governs and secures privileged accounts (such as. Privileged access management helps organizations manage and secure access to their most critical systems, applications, and data,. Privileged access management (pam) is not just a cybersecurity buzzword; Privileged access management is a category of cybersecurity solutions that enables security and it teams to securely. What Is Pam Key.
From theknowwomen.com
Key Instincts Pamela The Know Women What Is Pam Key Privileged access management helps organizations manage and secure access to their most critical systems, applications, and data,. Privileged access management is a category of cybersecurity solutions that enables security and it teams to securely manage access for all privileged identities in an enterprise environment. A subset of iam, focused on defining and controlling who or what has the authority to. What Is Pam Key.
From www.wallix.com
Privileged Access Management Features WALLIX What Is Pam Key It's a crucial defence line for organisations against cyber threats. Privileged access management (pam) is the cybersecurity discipline that governs and secures privileged accounts (such as. Privileged access management helps organizations manage and secure access to their most critical systems, applications, and data,. Privileged access management is a category of cybersecurity solutions that enables security and it teams to securely. What Is Pam Key.
From www.techrepublic.com
IAM vs. PAM Solutions What are the Key Differences? What Is Pam Key Privileged access management (pam) is not just a cybersecurity buzzword; Privileged access management (pam) consists of the cybersecurity strategies and technologies for exerting control over the elevated (“privileged”) access and permissions for. Privileged access management (pam) is the cybersecurity discipline that governs and secures privileged accounts (such as. It's a crucial defence line for organisations against cyber threats. A subset. What Is Pam Key.