Keychain Vs Secure Enclave . It runs its own microkernel, which is not directly. The metadata key is protected by the secure enclave but is cached in the application processor to allow fast queries of the keychain. The secure enclave is a dedicated secure subsystem integrated into apple systems on chip (socs). Iphones and macs with touch id or face id use a separate processor to handle your biometric information. It's called the secure enclave, it's basically an entire computer unto itself, and it offers a variety of security features. The secure enclave boots separately from the rest of your device. Secure enclave is a specialized hardware part of apple's system on chip (soc). It ensures that stored keys and. Additionally in recent iphones (5s. If you are using the keychain to store a key which you can retrieve then the security level is not the same. The secure enclave is used for the creation and storage of unique encryption keys. The keychain stores the keys (and other small data) encrypted and restricts access to that data.
from learn.microsoft.com
The secure enclave is a dedicated secure subsystem integrated into apple systems on chip (socs). Additionally in recent iphones (5s. If you are using the keychain to store a key which you can retrieve then the security level is not the same. Iphones and macs with touch id or face id use a separate processor to handle your biometric information. The secure enclave boots separately from the rest of your device. The secure enclave is used for the creation and storage of unique encryption keys. Secure enclave is a specialized hardware part of apple's system on chip (soc). It runs its own microkernel, which is not directly. The keychain stores the keys (and other small data) encrypted and restricts access to that data. It ensures that stored keys and.
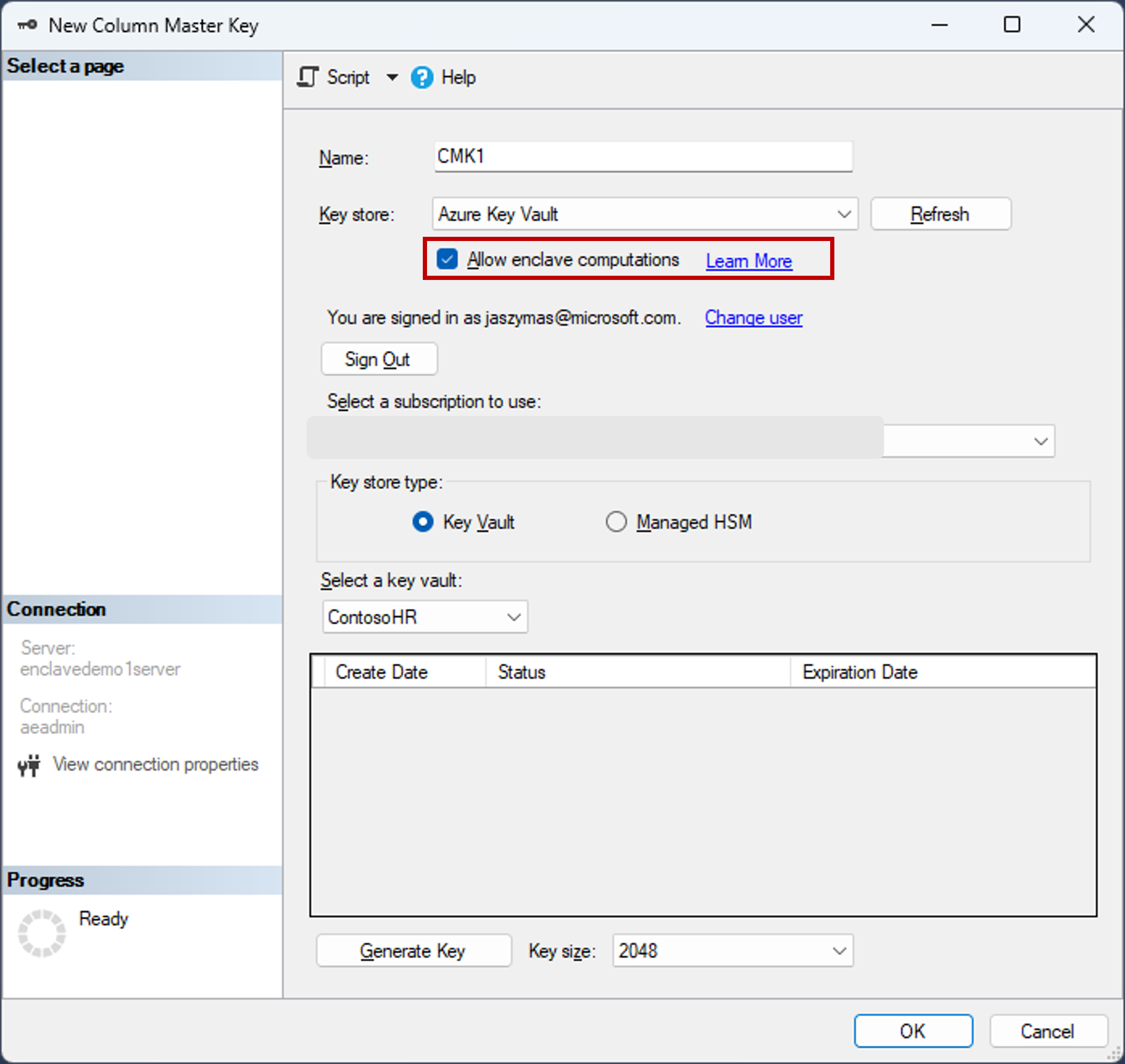
Tutorial Getting started with Always Encrypted with secure enclaves
Keychain Vs Secure Enclave If you are using the keychain to store a key which you can retrieve then the security level is not the same. Iphones and macs with touch id or face id use a separate processor to handle your biometric information. Additionally in recent iphones (5s. The secure enclave is used for the creation and storage of unique encryption keys. It ensures that stored keys and. The secure enclave is a dedicated secure subsystem integrated into apple systems on chip (socs). It runs its own microkernel, which is not directly. It's called the secure enclave, it's basically an entire computer unto itself, and it offers a variety of security features. If you are using the keychain to store a key which you can retrieve then the security level is not the same. The secure enclave boots separately from the rest of your device. Secure enclave is a specialized hardware part of apple's system on chip (soc). The keychain stores the keys (and other small data) encrypted and restricts access to that data. The metadata key is protected by the secure enclave but is cached in the application processor to allow fast queries of the keychain.
From www.slideserve.com
PPT NERC CIP Compliance PowerPoint Presentation, free download ID Keychain Vs Secure Enclave The secure enclave boots separately from the rest of your device. Additionally in recent iphones (5s. If you are using the keychain to store a key which you can retrieve then the security level is not the same. The secure enclave is a dedicated secure subsystem integrated into apple systems on chip (socs). Secure enclave is a specialized hardware part. Keychain Vs Secure Enclave.
From thewindowsupdate.com
Always Encrypted Wizard now supports secure enclaves and inplace Keychain Vs Secure Enclave It runs its own microkernel, which is not directly. Secure enclave is a specialized hardware part of apple's system on chip (soc). The secure enclave boots separately from the rest of your device. The metadata key is protected by the secure enclave but is cached in the application processor to allow fast queries of the keychain. The keychain stores the. Keychain Vs Secure Enclave.
From www.youtube.com
Using SSH Keys With Keychain Part 1 YouTube Keychain Vs Secure Enclave It's called the secure enclave, it's basically an entire computer unto itself, and it offers a variety of security features. Additionally in recent iphones (5s. It runs its own microkernel, which is not directly. The keychain stores the keys (and other small data) encrypted and restricts access to that data. If you are using the keychain to store a key. Keychain Vs Secure Enclave.
From learn.microsoft.com
Tutorial Getting started using Always Encrypted with secure enclaves Keychain Vs Secure Enclave The secure enclave boots separately from the rest of your device. The secure enclave is used for the creation and storage of unique encryption keys. It ensures that stored keys and. Additionally in recent iphones (5s. It runs its own microkernel, which is not directly. It's called the secure enclave, it's basically an entire computer unto itself, and it offers. Keychain Vs Secure Enclave.
From docs.turnkey.com
Secure enclaves Turnkey Documentation Keychain Vs Secure Enclave It runs its own microkernel, which is not directly. The metadata key is protected by the secure enclave but is cached in the application processor to allow fast queries of the keychain. If you are using the keychain to store a key which you can retrieve then the security level is not the same. Secure enclave is a specialized hardware. Keychain Vs Secure Enclave.
From aws.amazon.com
Guidance for Trusted Secure Enclaves on AWS Keychain Vs Secure Enclave The keychain stores the keys (and other small data) encrypted and restricts access to that data. Secure enclave is a specialized hardware part of apple's system on chip (soc). The secure enclave is a dedicated secure subsystem integrated into apple systems on chip (socs). The secure enclave is used for the creation and storage of unique encryption keys. The secure. Keychain Vs Secure Enclave.
From www.reddit.com
Put together this Enclave Keychain to show the pride r/fo76FilthyCasuals Keychain Vs Secure Enclave The metadata key is protected by the secure enclave but is cached in the application processor to allow fast queries of the keychain. Secure enclave is a specialized hardware part of apple's system on chip (soc). Additionally in recent iphones (5s. The keychain stores the keys (and other small data) encrypted and restricts access to that data. It runs its. Keychain Vs Secure Enclave.
From aws.amazon.com
Guidance for Trusted Secure Enclaves on AWS Keychain Vs Secure Enclave The keychain stores the keys (and other small data) encrypted and restricts access to that data. The metadata key is protected by the secure enclave but is cached in the application processor to allow fast queries of the keychain. The secure enclave is a dedicated secure subsystem integrated into apple systems on chip (socs). Secure enclave is a specialized hardware. Keychain Vs Secure Enclave.
From www.redeszone.net
Publican la clave de descifrado del Secure Enclave Processor de Apple Keychain Vs Secure Enclave Secure enclave is a specialized hardware part of apple's system on chip (soc). If you are using the keychain to store a key which you can retrieve then the security level is not the same. The keychain stores the keys (and other small data) encrypted and restricts access to that data. It's called the secure enclave, it's basically an entire. Keychain Vs Secure Enclave.
From learn.microsoft.com
Tutorial Getting started with Always Encrypted with secure enclaves Keychain Vs Secure Enclave Additionally in recent iphones (5s. It ensures that stored keys and. Iphones and macs with touch id or face id use a separate processor to handle your biometric information. The secure enclave is a dedicated secure subsystem integrated into apple systems on chip (socs). The metadata key is protected by the secure enclave but is cached in the application processor. Keychain Vs Secure Enclave.
From ctovision.com
Secure Enclaves Foundation For The CloudBased Enterprise Keychain Vs Secure Enclave The secure enclave is used for the creation and storage of unique encryption keys. The secure enclave is a dedicated secure subsystem integrated into apple systems on chip (socs). It's called the secure enclave, it's basically an entire computer unto itself, and it offers a variety of security features. The metadata key is protected by the secure enclave but is. Keychain Vs Secure Enclave.
From blog.greggant.com
Apple's secret OS and the Secure Enclave Processor Keychain Vs Secure Enclave If you are using the keychain to store a key which you can retrieve then the security level is not the same. Additionally in recent iphones (5s. The keychain stores the keys (and other small data) encrypted and restricts access to that data. It runs its own microkernel, which is not directly. Iphones and macs with touch id or face. Keychain Vs Secure Enclave.
From elisa.tech
Trusted Execution Inside Secure Enclaves LFX Mentorship Report ELISA Keychain Vs Secure Enclave The secure enclave boots separately from the rest of your device. The secure enclave is a dedicated secure subsystem integrated into apple systems on chip (socs). Iphones and macs with touch id or face id use a separate processor to handle your biometric information. Secure enclave is a specialized hardware part of apple's system on chip (soc). The keychain stores. Keychain Vs Secure Enclave.
From www.profolus.com
Apple Secure Enclave Purpose, Mechanism, Pros and Cons Profolus Keychain Vs Secure Enclave The metadata key is protected by the secure enclave but is cached in the application processor to allow fast queries of the keychain. Additionally in recent iphones (5s. The secure enclave is a dedicated secure subsystem integrated into apple systems on chip (socs). It ensures that stored keys and. Secure enclave is a specialized hardware part of apple's system on. Keychain Vs Secure Enclave.
From hackaday.com
RISCV Will Stop Hackers Dead From Getting Into Your Computer Hackaday Keychain Vs Secure Enclave Iphones and macs with touch id or face id use a separate processor to handle your biometric information. Additionally in recent iphones (5s. The secure enclave is used for the creation and storage of unique encryption keys. It ensures that stored keys and. Secure enclave is a specialized hardware part of apple's system on chip (soc). The metadata key is. Keychain Vs Secure Enclave.
From www.youtube.com
SGX Secure Enclaves The Future of Application Security in the Cloud Keychain Vs Secure Enclave Iphones and macs with touch id or face id use a separate processor to handle your biometric information. Secure enclave is a specialized hardware part of apple's system on chip (soc). The secure enclave is a dedicated secure subsystem integrated into apple systems on chip (socs). The secure enclave is used for the creation and storage of unique encryption keys.. Keychain Vs Secure Enclave.
From support.apple.com
Secure Enclave Apple Support (UK) Keychain Vs Secure Enclave Secure enclave is a specialized hardware part of apple's system on chip (soc). The secure enclave is used for the creation and storage of unique encryption keys. The secure enclave boots separately from the rest of your device. It's called the secure enclave, it's basically an entire computer unto itself, and it offers a variety of security features. The metadata. Keychain Vs Secure Enclave.
From www.slideserve.com
PPT What’s new in SQL Server and Azure SQL Database Security Keychain Vs Secure Enclave It runs its own microkernel, which is not directly. The secure enclave is used for the creation and storage of unique encryption keys. Secure enclave is a specialized hardware part of apple's system on chip (soc). The secure enclave is a dedicated secure subsystem integrated into apple systems on chip (socs). The metadata key is protected by the secure enclave. Keychain Vs Secure Enclave.
From www.egnyte.com
Secure Enclaves for Protecting Highly Sensitive Data Egnyte Keychain Vs Secure Enclave Additionally in recent iphones (5s. It ensures that stored keys and. The secure enclave is a dedicated secure subsystem integrated into apple systems on chip (socs). Secure enclave is a specialized hardware part of apple's system on chip (soc). The metadata key is protected by the secure enclave but is cached in the application processor to allow fast queries of. Keychain Vs Secure Enclave.
From www.youtube.com
Apple Security Platform & Secure Enclave Explained FIRST CLICKS YouTube Keychain Vs Secure Enclave The secure enclave boots separately from the rest of your device. The secure enclave is a dedicated secure subsystem integrated into apple systems on chip (socs). It runs its own microkernel, which is not directly. Secure enclave is a specialized hardware part of apple's system on chip (soc). Additionally in recent iphones (5s. Iphones and macs with touch id or. Keychain Vs Secure Enclave.
From www.youtube.com
What is a Secure Enclave for CMMCL2 Compliance YouTube Keychain Vs Secure Enclave It runs its own microkernel, which is not directly. The metadata key is protected by the secure enclave but is cached in the application processor to allow fast queries of the keychain. It's called the secure enclave, it's basically an entire computer unto itself, and it offers a variety of security features. The secure enclave is a dedicated secure subsystem. Keychain Vs Secure Enclave.
From www.redeszone.net
Secure Enclave Qué es y cómo funciona esta capa de seguridad de Apple Keychain Vs Secure Enclave The metadata key is protected by the secure enclave but is cached in the application processor to allow fast queries of the keychain. It runs its own microkernel, which is not directly. The secure enclave boots separately from the rest of your device. It ensures that stored keys and. Secure enclave is a specialized hardware part of apple's system on. Keychain Vs Secure Enclave.
From nordvpn.com
Secure enclave How it makes your devices safer NordVPN Keychain Vs Secure Enclave It runs its own microkernel, which is not directly. It's called the secure enclave, it's basically an entire computer unto itself, and it offers a variety of security features. Additionally in recent iphones (5s. The secure enclave is a dedicated secure subsystem integrated into apple systems on chip (socs). The secure enclave is used for the creation and storage of. Keychain Vs Secure Enclave.
From enclave.io
Enclave — Secure access to anything, from anywhere Enclave Keychain Vs Secure Enclave Iphones and macs with touch id or face id use a separate processor to handle your biometric information. Secure enclave is a specialized hardware part of apple's system on chip (soc). If you are using the keychain to store a key which you can retrieve then the security level is not the same. The metadata key is protected by the. Keychain Vs Secure Enclave.
From aws.amazon.com
Guidance for Secure Blockchain Key Management with AWS Nitro Enclaves Keychain Vs Secure Enclave It ensures that stored keys and. The secure enclave is a dedicated secure subsystem integrated into apple systems on chip (socs). The metadata key is protected by the secure enclave but is cached in the application processor to allow fast queries of the keychain. If you are using the keychain to store a key which you can retrieve then the. Keychain Vs Secure Enclave.
From safelishare.com
Using secure enclave to combat model adversarial attacks SafeLiShare Keychain Vs Secure Enclave The keychain stores the keys (and other small data) encrypted and restricts access to that data. Secure enclave is a specialized hardware part of apple's system on chip (soc). It runs its own microkernel, which is not directly. The metadata key is protected by the secure enclave but is cached in the application processor to allow fast queries of the. Keychain Vs Secure Enclave.
From rebeloper.com
Keychain Swift and Secure Enclave iOS — Rebeloper Keychain Vs Secure Enclave The keychain stores the keys (and other small data) encrypted and restricts access to that data. If you are using the keychain to store a key which you can retrieve then the security level is not the same. It runs its own microkernel, which is not directly. Secure enclave is a specialized hardware part of apple's system on chip (soc).. Keychain Vs Secure Enclave.
From support.apple.com
Secure Enclave Apple Support (IN) Keychain Vs Secure Enclave Iphones and macs with touch id or face id use a separate processor to handle your biometric information. The secure enclave boots separately from the rest of your device. The metadata key is protected by the secure enclave but is cached in the application processor to allow fast queries of the keychain. If you are using the keychain to store. Keychain Vs Secure Enclave.
From www.summit7.us
What Is a CUI Enclave and When Should You Have One? Keychain Vs Secure Enclave The secure enclave boots separately from the rest of your device. Iphones and macs with touch id or face id use a separate processor to handle your biometric information. It ensures that stored keys and. If you are using the keychain to store a key which you can retrieve then the security level is not the same. Additionally in recent. Keychain Vs Secure Enclave.
From aws.amazon.com
Guidance for Trusted Secure Enclaves on AWS Keychain Vs Secure Enclave If you are using the keychain to store a key which you can retrieve then the security level is not the same. The secure enclave is a dedicated secure subsystem integrated into apple systems on chip (socs). It ensures that stored keys and. Secure enclave is a specialized hardware part of apple's system on chip (soc). Additionally in recent iphones. Keychain Vs Secure Enclave.
From www.idownloadblog.com
Apple removes iCloud Keychain from iOS 7 GM, here's why Keychain Vs Secure Enclave The secure enclave boots separately from the rest of your device. The keychain stores the keys (and other small data) encrypted and restricts access to that data. The secure enclave is a dedicated secure subsystem integrated into apple systems on chip (socs). The secure enclave is used for the creation and storage of unique encryption keys. If you are using. Keychain Vs Secure Enclave.
From blog.acolyer.org
EnclaveDB a secure database using SGX the morning paper Keychain Vs Secure Enclave It runs its own microkernel, which is not directly. It's called the secure enclave, it's basically an entire computer unto itself, and it offers a variety of security features. The metadata key is protected by the secure enclave but is cached in the application processor to allow fast queries of the keychain. If you are using the keychain to store. Keychain Vs Secure Enclave.
From www.loginradius.com
Secure Enclave in iOS App Keychain Vs Secure Enclave The secure enclave is a dedicated secure subsystem integrated into apple systems on chip (socs). The secure enclave boots separately from the rest of your device. The secure enclave is used for the creation and storage of unique encryption keys. It's called the secure enclave, it's basically an entire computer unto itself, and it offers a variety of security features.. Keychain Vs Secure Enclave.
From blog.eidinger.info
Get the biometric authentication prompt for protected keychain items in Keychain Vs Secure Enclave The metadata key is protected by the secure enclave but is cached in the application processor to allow fast queries of the keychain. The secure enclave boots separately from the rest of your device. The secure enclave is used for the creation and storage of unique encryption keys. Additionally in recent iphones (5s. Secure enclave is a specialized hardware part. Keychain Vs Secure Enclave.
From www.anjuna.io
SDX Central Anjuna Partners With AWS, Microsoft on Secure Enclaves Keychain Vs Secure Enclave Iphones and macs with touch id or face id use a separate processor to handle your biometric information. The secure enclave is a dedicated secure subsystem integrated into apple systems on chip (socs). Additionally in recent iphones (5s. It's called the secure enclave, it's basically an entire computer unto itself, and it offers a variety of security features. If you. Keychain Vs Secure Enclave.