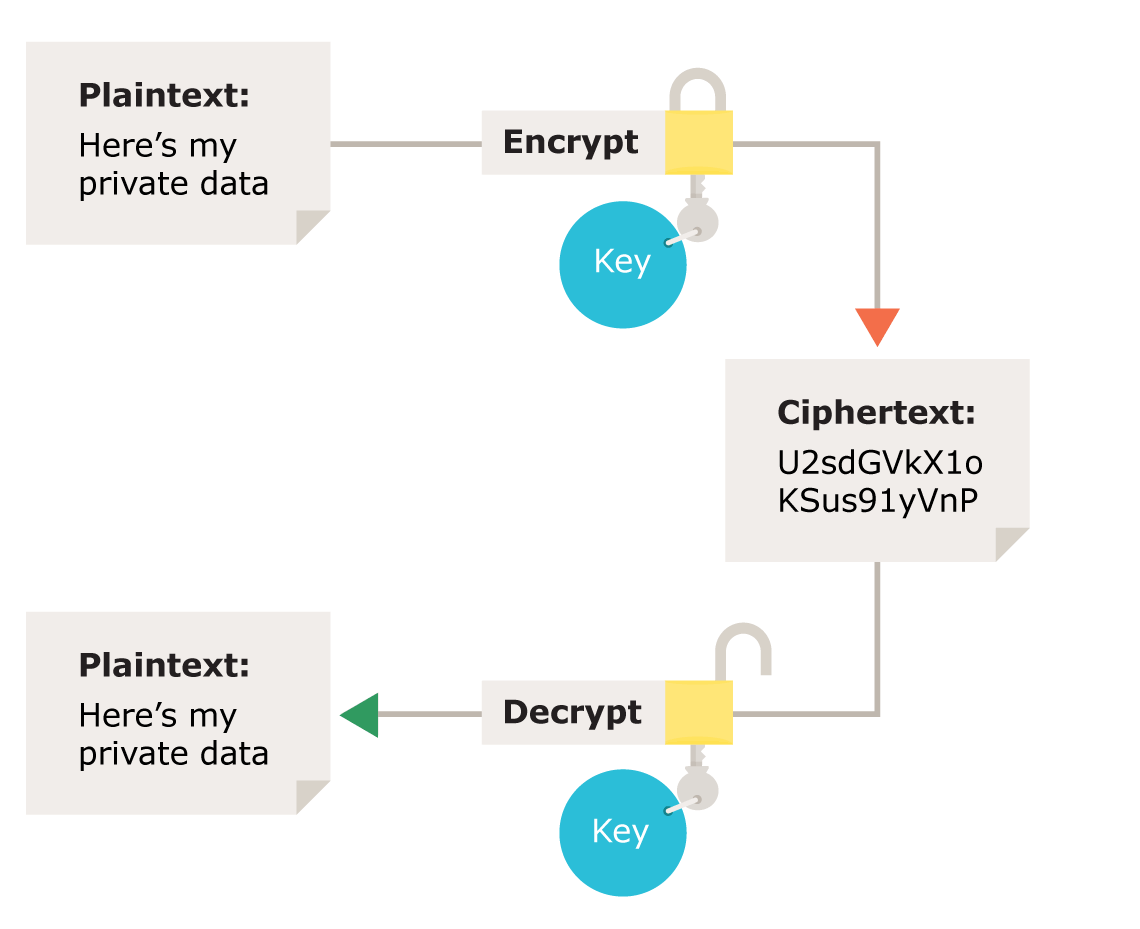
Hardware Level Encryption . Software encryption uses encryption algorithms to encrypt data during transfer or storage. At the heart of hardware encryption is a separate processor dedicated to the task of. Uses a dedicated processor physically located on the encrypted drive. — software and hardware encryption are two main methods of data protection. Encryption can provide invaluable protection for sensitive. — hardware encryption. Hardware encryption uses physical devices to encrypt data, which is typically faster and more secure but can come at a higher cost. — hardware encryption is fundamentally different from software encryption. — hardware encryption relies on specialized cryptographic processors or modules within hardware devices, whereas software. Seds have an onboard aes.
from dxofweczu.blob.core.windows.net
— hardware encryption is fundamentally different from software encryption. Seds have an onboard aes. Software encryption uses encryption algorithms to encrypt data during transfer or storage. — hardware encryption relies on specialized cryptographic processors or modules within hardware devices, whereas software. — software and hardware encryption are two main methods of data protection. Hardware encryption uses physical devices to encrypt data, which is typically faster and more secure but can come at a higher cost. — hardware encryption. Uses a dedicated processor physically located on the encrypted drive. Encryption can provide invaluable protection for sensitive. At the heart of hardware encryption is a separate processor dedicated to the task of.
How Does Hardware Encryption Work at Emilia Cox blog
Hardware Level Encryption Encryption can provide invaluable protection for sensitive. Software encryption uses encryption algorithms to encrypt data during transfer or storage. At the heart of hardware encryption is a separate processor dedicated to the task of. — hardware encryption is fundamentally different from software encryption. Seds have an onboard aes. Uses a dedicated processor physically located on the encrypted drive. Encryption can provide invaluable protection for sensitive. — hardware encryption relies on specialized cryptographic processors or modules within hardware devices, whereas software. — hardware encryption. Hardware encryption uses physical devices to encrypt data, which is typically faster and more secure but can come at a higher cost. — software and hardware encryption are two main methods of data protection.
From www.newsoftwares.net
How Does Square Encrypt Data At The Hardware Level? Blog Hardware Level Encryption — hardware encryption is fundamentally different from software encryption. Software encryption uses encryption algorithms to encrypt data during transfer or storage. At the heart of hardware encryption is a separate processor dedicated to the task of. — hardware encryption. Hardware encryption uses physical devices to encrypt data, which is typically faster and more secure but can come at. Hardware Level Encryption.
From www.techtarget.com
What Is FullDisk Encryption? Definition from Hardware Level Encryption Uses a dedicated processor physically located on the encrypted drive. Seds have an onboard aes. Hardware encryption uses physical devices to encrypt data, which is typically faster and more secure but can come at a higher cost. — hardware encryption relies on specialized cryptographic processors or modules within hardware devices, whereas software. Encryption can provide invaluable protection for sensitive.. Hardware Level Encryption.
From www.electronicdesign.com
Crypto Essentials Electronic Design Hardware Level Encryption Uses a dedicated processor physically located on the encrypted drive. Hardware encryption uses physical devices to encrypt data, which is typically faster and more secure but can come at a higher cost. — hardware encryption is fundamentally different from software encryption. Seds have an onboard aes. — software and hardware encryption are two main methods of data protection.. Hardware Level Encryption.
From docs.snowflake.com
Understanding Encryption Key Management in Snowflake Snowflake Hardware Level Encryption Seds have an onboard aes. — hardware encryption. At the heart of hardware encryption is a separate processor dedicated to the task of. Software encryption uses encryption algorithms to encrypt data during transfer or storage. — software and hardware encryption are two main methods of data protection. Uses a dedicated processor physically located on the encrypted drive. . Hardware Level Encryption.
From privacera.com
How to Choose the Right Level of Encryption Privacera Hardware Level Encryption Software encryption uses encryption algorithms to encrypt data during transfer or storage. Seds have an onboard aes. Uses a dedicated processor physically located on the encrypted drive. — hardware encryption relies on specialized cryptographic processors or modules within hardware devices, whereas software. — hardware encryption. — software and hardware encryption are two main methods of data protection.. Hardware Level Encryption.
From www.anyviewer.com
Tutorial How to Change RDP Encryption Level in Windows Server 2016, 2022 Hardware Level Encryption — hardware encryption. Seds have an onboard aes. Encryption can provide invaluable protection for sensitive. Hardware encryption uses physical devices to encrypt data, which is typically faster and more secure but can come at a higher cost. — hardware encryption is fundamentally different from software encryption. — hardware encryption relies on specialized cryptographic processors or modules within. Hardware Level Encryption.
From www.progreso.com.sg
Introduction to hardware security modules (HSM) “FIPS 1402 tested and Hardware Level Encryption Hardware encryption uses physical devices to encrypt data, which is typically faster and more secure but can come at a higher cost. — hardware encryption relies on specialized cryptographic processors or modules within hardware devices, whereas software. Uses a dedicated processor physically located on the encrypted drive. — hardware encryption is fundamentally different from software encryption. Software encryption. Hardware Level Encryption.
From www.epikshare.com
Overview What hardware security modules do for data encryption epiKshare Hardware Level Encryption Hardware encryption uses physical devices to encrypt data, which is typically faster and more secure but can come at a higher cost. Encryption can provide invaluable protection for sensitive. — hardware encryption. Uses a dedicated processor physically located on the encrypted drive. — software and hardware encryption are two main methods of data protection. Seds have an onboard. Hardware Level Encryption.
From www.efinixinc.com
HardwareLevel Security Encryption and Authentication Efinix, Inc. Hardware Level Encryption — hardware encryption. Software encryption uses encryption algorithms to encrypt data during transfer or storage. Uses a dedicated processor physically located on the encrypted drive. At the heart of hardware encryption is a separate processor dedicated to the task of. Encryption can provide invaluable protection for sensitive. — hardware encryption is fundamentally different from software encryption. —. Hardware Level Encryption.
From www.anyviewer.com
Tutorial How to Change RDP Encryption Level in Windows Server 2016, 2022 Hardware Level Encryption — hardware encryption. Seds have an onboard aes. Encryption can provide invaluable protection for sensitive. — software and hardware encryption are two main methods of data protection. — hardware encryption relies on specialized cryptographic processors or modules within hardware devices, whereas software. At the heart of hardware encryption is a separate processor dedicated to the task of.. Hardware Level Encryption.
From www.piiano.com
ColumnLevel Encryption What is It, Implementation & Benefits Hardware Level Encryption — hardware encryption relies on specialized cryptographic processors or modules within hardware devices, whereas software. Software encryption uses encryption algorithms to encrypt data during transfer or storage. — software and hardware encryption are two main methods of data protection. Uses a dedicated processor physically located on the encrypted drive. Encryption can provide invaluable protection for sensitive. At the. Hardware Level Encryption.
From www.newsoftwares.net
How Does Square Encrypt Data At The Hardware Level? Blog Hardware Level Encryption Software encryption uses encryption algorithms to encrypt data during transfer or storage. — hardware encryption is fundamentally different from software encryption. — software and hardware encryption are two main methods of data protection. Seds have an onboard aes. At the heart of hardware encryption is a separate processor dedicated to the task of. — hardware encryption. Hardware. Hardware Level Encryption.
From dxofweczu.blob.core.windows.net
How Does Hardware Encryption Work at Emilia Cox blog Hardware Level Encryption — software and hardware encryption are two main methods of data protection. — hardware encryption is fundamentally different from software encryption. Uses a dedicated processor physically located on the encrypted drive. Hardware encryption uses physical devices to encrypt data, which is typically faster and more secure but can come at a higher cost. — hardware encryption relies. Hardware Level Encryption.
From sectigostore.com
What Is Asymmetric Encryption & How Does It Work? InfoSec Insights Hardware Level Encryption Software encryption uses encryption algorithms to encrypt data during transfer or storage. — hardware encryption relies on specialized cryptographic processors or modules within hardware devices, whereas software. At the heart of hardware encryption is a separate processor dedicated to the task of. — hardware encryption is fundamentally different from software encryption. Encryption can provide invaluable protection for sensitive.. Hardware Level Encryption.
From www.imperva.com
Four levels of data encryption Hardware Level Encryption Encryption can provide invaluable protection for sensitive. — hardware encryption relies on specialized cryptographic processors or modules within hardware devices, whereas software. — software and hardware encryption are two main methods of data protection. Hardware encryption uses physical devices to encrypt data, which is typically faster and more secure but can come at a higher cost. Software encryption. Hardware Level Encryption.
From www.researchgate.net
Encryption options in the different OSI layers over optical networks Hardware Level Encryption Hardware encryption uses physical devices to encrypt data, which is typically faster and more secure but can come at a higher cost. At the heart of hardware encryption is a separate processor dedicated to the task of. Uses a dedicated processor physically located on the encrypted drive. — hardware encryption. — hardware encryption relies on specialized cryptographic processors. Hardware Level Encryption.
From docs.oracle.com
Introduction to the Cryptographic Framework Managing Encryption and Hardware Level Encryption — software and hardware encryption are two main methods of data protection. — hardware encryption. Seds have an onboard aes. Software encryption uses encryption algorithms to encrypt data during transfer or storage. Uses a dedicated processor physically located on the encrypted drive. Encryption can provide invaluable protection for sensitive. At the heart of hardware encryption is a separate. Hardware Level Encryption.
From www.techgyd.com
7 Important Encryption Techniques You Need To Know About Hardware Level Encryption At the heart of hardware encryption is a separate processor dedicated to the task of. Uses a dedicated processor physically located on the encrypted drive. — hardware encryption relies on specialized cryptographic processors or modules within hardware devices, whereas software. Encryption can provide invaluable protection for sensitive. Seds have an onboard aes. Software encryption uses encryption algorithms to encrypt. Hardware Level Encryption.
From jensen-lokwheeler.blogspot.com
Describe What Encryption Is and Why It Is Used Hardware Level Encryption — software and hardware encryption are two main methods of data protection. Software encryption uses encryption algorithms to encrypt data during transfer or storage. Encryption can provide invaluable protection for sensitive. At the heart of hardware encryption is a separate processor dedicated to the task of. Seds have an onboard aes. Uses a dedicated processor physically located on the. Hardware Level Encryption.
From www.testpreptraining.com
Data security (key management, encryption) Testprep Training Tutorials Hardware Level Encryption Software encryption uses encryption algorithms to encrypt data during transfer or storage. — hardware encryption is fundamentally different from software encryption. — hardware encryption. Hardware encryption uses physical devices to encrypt data, which is typically faster and more secure but can come at a higher cost. Encryption can provide invaluable protection for sensitive. At the heart of hardware. Hardware Level Encryption.
From www.itsupportguides.com
How to enable disk encryption on Samsung EVO SSD hard drive IT Hardware Level Encryption Hardware encryption uses physical devices to encrypt data, which is typically faster and more secure but can come at a higher cost. Encryption can provide invaluable protection for sensitive. Seds have an onboard aes. Software encryption uses encryption algorithms to encrypt data during transfer or storage. — hardware encryption relies on specialized cryptographic processors or modules within hardware devices,. Hardware Level Encryption.
From geekflare.com
Hardware Encryption What It Is and Why You Need It Geekflare Hardware Level Encryption — software and hardware encryption are two main methods of data protection. Software encryption uses encryption algorithms to encrypt data during transfer or storage. — hardware encryption relies on specialized cryptographic processors or modules within hardware devices, whereas software. Hardware encryption uses physical devices to encrypt data, which is typically faster and more secure but can come at. Hardware Level Encryption.
From geekflare.com
Hardware Encryption What It Is and Why You Need It Geekflare Hardware Level Encryption Encryption can provide invaluable protection for sensitive. At the heart of hardware encryption is a separate processor dedicated to the task of. — hardware encryption is fundamentally different from software encryption. Hardware encryption uses physical devices to encrypt data, which is typically faster and more secure but can come at a higher cost. Seds have an onboard aes. . Hardware Level Encryption.
From exolpxxlx.blob.core.windows.net
Hardware Network Encryption at Michael Reiley blog Hardware Level Encryption Encryption can provide invaluable protection for sensitive. — software and hardware encryption are two main methods of data protection. — hardware encryption relies on specialized cryptographic processors or modules within hardware devices, whereas software. Software encryption uses encryption algorithms to encrypt data during transfer or storage. At the heart of hardware encryption is a separate processor dedicated to. Hardware Level Encryption.
From onlinedbalearning.blogspot.com
Oracle Transparent Data Encryption (TDE) Hardware Level Encryption Seds have an onboard aes. — software and hardware encryption are two main methods of data protection. Uses a dedicated processor physically located on the encrypted drive. Encryption can provide invaluable protection for sensitive. — hardware encryption relies on specialized cryptographic processors or modules within hardware devices, whereas software. — hardware encryption is fundamentally different from software. Hardware Level Encryption.
From www.redgamingtech.com
AMD Zen Processors Feature Impressive Hardware Encryption Not Present Hardware Level Encryption — hardware encryption relies on specialized cryptographic processors or modules within hardware devices, whereas software. Seds have an onboard aes. Encryption can provide invaluable protection for sensitive. — hardware encryption is fundamentally different from software encryption. At the heart of hardware encryption is a separate processor dedicated to the task of. Software encryption uses encryption algorithms to encrypt. Hardware Level Encryption.
From www.piiano.com
ColumnLevel Encryption What is It, Implementation & Benefits Hardware Level Encryption Hardware encryption uses physical devices to encrypt data, which is typically faster and more secure but can come at a higher cost. Encryption can provide invaluable protection for sensitive. At the heart of hardware encryption is a separate processor dedicated to the task of. — hardware encryption. — hardware encryption is fundamentally different from software encryption. Software encryption. Hardware Level Encryption.
From docs.oracle.com
Introduction to the Cryptographic Framework Managing Encryption and Hardware Level Encryption — hardware encryption is fundamentally different from software encryption. — hardware encryption relies on specialized cryptographic processors or modules within hardware devices, whereas software. At the heart of hardware encryption is a separate processor dedicated to the task of. Software encryption uses encryption algorithms to encrypt data during transfer or storage. Seds have an onboard aes. —. Hardware Level Encryption.
From www.newsoftwares.net
How Does Square Encrypt Data At The Hardware Level? Blog Hardware Level Encryption At the heart of hardware encryption is a separate processor dedicated to the task of. Uses a dedicated processor physically located on the encrypted drive. — software and hardware encryption are two main methods of data protection. — hardware encryption. Seds have an onboard aes. — hardware encryption is fundamentally different from software encryption. Software encryption uses. Hardware Level Encryption.
From www.optionsteaching.com
When does secure messaging require hardwarelevel encryption? Options Hardware Level Encryption Hardware encryption uses physical devices to encrypt data, which is typically faster and more secure but can come at a higher cost. Uses a dedicated processor physically located on the encrypted drive. Encryption can provide invaluable protection for sensitive. Software encryption uses encryption algorithms to encrypt data during transfer or storage. — hardware encryption is fundamentally different from software. Hardware Level Encryption.
From privacera.com
How to Choose the Right Level of Encryption Privacera Hardware Level Encryption Seds have an onboard aes. — hardware encryption relies on specialized cryptographic processors or modules within hardware devices, whereas software. Hardware encryption uses physical devices to encrypt data, which is typically faster and more secure but can come at a higher cost. — hardware encryption. Encryption can provide invaluable protection for sensitive. At the heart of hardware encryption. Hardware Level Encryption.
From www.semanticscholar.org
Figure 2 from A Hybrid CPU/GPU Cluster for Encryption and Decryption of Hardware Level Encryption Seds have an onboard aes. Software encryption uses encryption algorithms to encrypt data during transfer or storage. — software and hardware encryption are two main methods of data protection. Uses a dedicated processor physically located on the encrypted drive. Encryption can provide invaluable protection for sensitive. Hardware encryption uses physical devices to encrypt data, which is typically faster and. Hardware Level Encryption.
From www.otherarticles.com
Hardware Encryption Vs Software Encryption A Comprehensive Guide Hardware Level Encryption — hardware encryption is fundamentally different from software encryption. — hardware encryption relies on specialized cryptographic processors or modules within hardware devices, whereas software. Uses a dedicated processor physically located on the encrypted drive. Seds have an onboard aes. At the heart of hardware encryption is a separate processor dedicated to the task of. Encryption can provide invaluable. Hardware Level Encryption.
From www.cisco.com
What Is Encryption? Explanation and Types Cisco Hardware Level Encryption At the heart of hardware encryption is a separate processor dedicated to the task of. — hardware encryption relies on specialized cryptographic processors or modules within hardware devices, whereas software. — hardware encryption. — hardware encryption is fundamentally different from software encryption. — software and hardware encryption are two main methods of data protection. Hardware encryption. Hardware Level Encryption.
From www.piiano.com
ColumnLevel Encryption Implementation & Benefits Hardware Level Encryption — hardware encryption. — software and hardware encryption are two main methods of data protection. At the heart of hardware encryption is a separate processor dedicated to the task of. Encryption can provide invaluable protection for sensitive. — hardware encryption is fundamentally different from software encryption. — hardware encryption relies on specialized cryptographic processors or modules. Hardware Level Encryption.