Data Security System Access . The key steps in protecting sensitive data include automating visibility, controlling access policies and implementing ongoing monitoring to identify vulnerabilities and risks before. This concept encompasses the entire. Data security is the practice of protecting digital information from unauthorized access, corruption or theft throughout its entire lifecycle. Data security refers to the protective measures employed to secure data against unapproved access and to preserve data confidentiality, integrity, and availability. Data security is the practice of protecting digital data from unauthorized access, use or disclosure in a manner consistent with an organization’s. Access control involves two main processes: Authentication and authorization technology does the work of confirming a user’s credentials—whether a password, pin, biometrics, or security tokens—are correct, and. Authentication is the process of ensuring users are who they say they are. Data security refers to the measures taken to prevent unauthorized access to databases and computer systems, data breaches, or any.
from www.gdata.pt
This concept encompasses the entire. The key steps in protecting sensitive data include automating visibility, controlling access policies and implementing ongoing monitoring to identify vulnerabilities and risks before. Authentication is the process of ensuring users are who they say they are. Access control involves two main processes: Data security refers to the measures taken to prevent unauthorized access to databases and computer systems, data breaches, or any. Data security refers to the protective measures employed to secure data against unapproved access and to preserve data confidentiality, integrity, and availability. Data security is the practice of protecting digital information from unauthorized access, corruption or theft throughout its entire lifecycle. Data security is the practice of protecting digital data from unauthorized access, use or disclosure in a manner consistent with an organization’s. Authentication and authorization technology does the work of confirming a user’s credentials—whether a password, pin, biometrics, or security tokens—are correct, and.
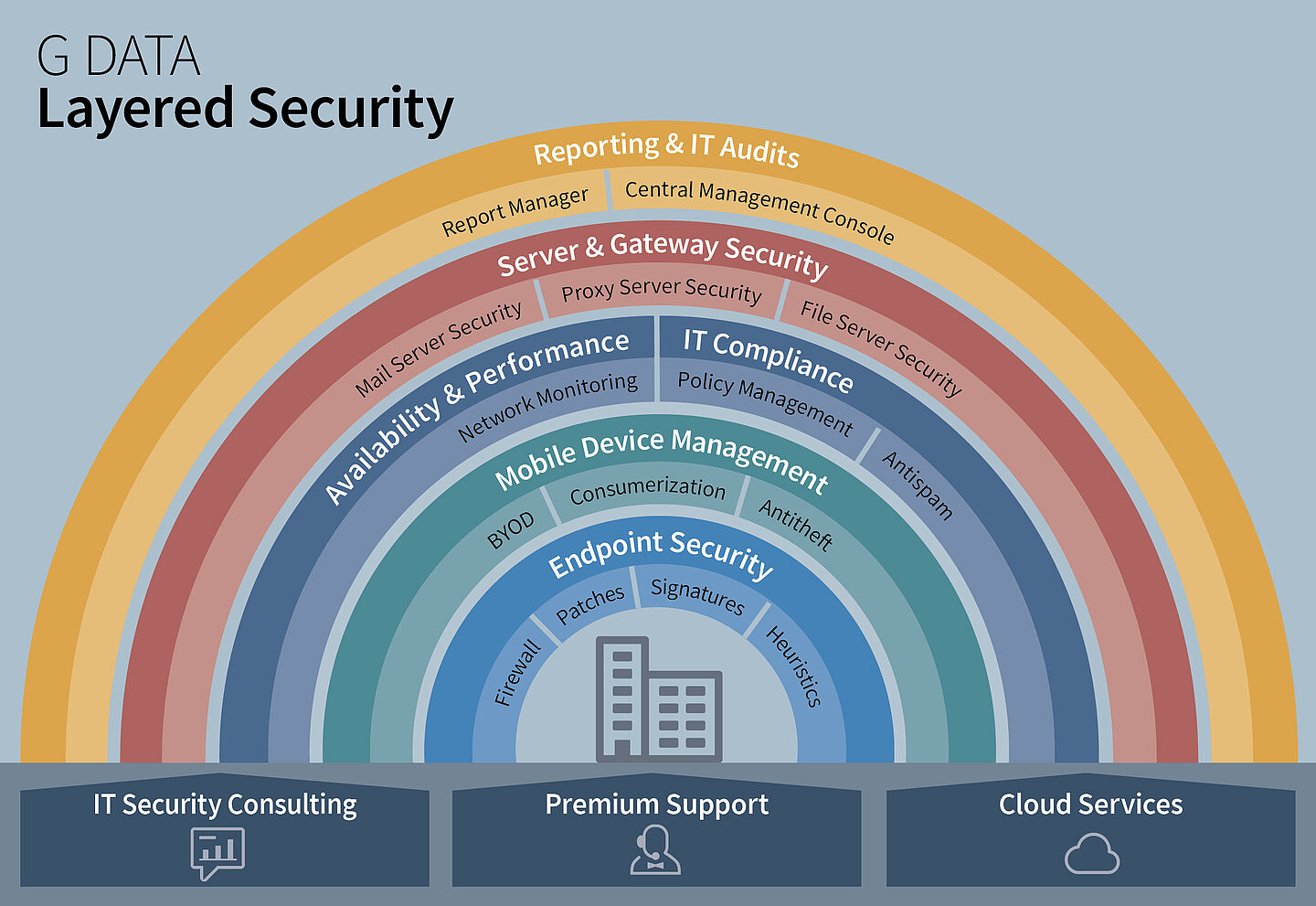
G DATA Layered Security thoroughly sophisticated IT security
Data Security System Access Data security refers to the protective measures employed to secure data against unapproved access and to preserve data confidentiality, integrity, and availability. Data security is the practice of protecting digital data from unauthorized access, use or disclosure in a manner consistent with an organization’s. Data security is the practice of protecting digital information from unauthorized access, corruption or theft throughout its entire lifecycle. Authentication is the process of ensuring users are who they say they are. Access control involves two main processes: This concept encompasses the entire. The key steps in protecting sensitive data include automating visibility, controlling access policies and implementing ongoing monitoring to identify vulnerabilities and risks before. Authentication and authorization technology does the work of confirming a user’s credentials—whether a password, pin, biometrics, or security tokens—are correct, and. Data security refers to the protective measures employed to secure data against unapproved access and to preserve data confidentiality, integrity, and availability. Data security refers to the measures taken to prevent unauthorized access to databases and computer systems, data breaches, or any.
From www.analyticsvidhya.com
What is Data Security? Threats, Risks and Solutions Data Security System Access Authentication is the process of ensuring users are who they say they are. The key steps in protecting sensitive data include automating visibility, controlling access policies and implementing ongoing monitoring to identify vulnerabilities and risks before. Authentication and authorization technology does the work of confirming a user’s credentials—whether a password, pin, biometrics, or security tokens—are correct, and. This concept encompasses. Data Security System Access.
From www.secureye.com
Access Control System Need Security for Every Organization Secureye Data Security System Access Data security is the practice of protecting digital data from unauthorized access, use or disclosure in a manner consistent with an organization’s. This concept encompasses the entire. Access control involves two main processes: Data security is the practice of protecting digital information from unauthorized access, corruption or theft throughout its entire lifecycle. Authentication is the process of ensuring users are. Data Security System Access.
From www.quality-assurance-solutions.com
Information Security Management System Data Security System Access Data security refers to the measures taken to prevent unauthorized access to databases and computer systems, data breaches, or any. Access control involves two main processes: The key steps in protecting sensitive data include automating visibility, controlling access policies and implementing ongoing monitoring to identify vulnerabilities and risks before. Data security is the practice of protecting digital information from unauthorized. Data Security System Access.
From www.conceptdraw.com
IT Security Solutions Data Security System Access Data security refers to the protective measures employed to secure data against unapproved access and to preserve data confidentiality, integrity, and availability. Authentication and authorization technology does the work of confirming a user’s credentials—whether a password, pin, biometrics, or security tokens—are correct, and. Data security is the practice of protecting digital data from unauthorized access, use or disclosure in a. Data Security System Access.
From www.collidu.com
Information Security System PowerPoint and Google Slides Template PPT Slides Data Security System Access Authentication and authorization technology does the work of confirming a user’s credentials—whether a password, pin, biometrics, or security tokens—are correct, and. Data security is the practice of protecting digital data from unauthorized access, use or disclosure in a manner consistent with an organization’s. Data security refers to the measures taken to prevent unauthorized access to databases and computer systems, data. Data Security System Access.
From www.lepide.com
Top 10 Data Security Measures Every Organization Should Have Data Security System Access The key steps in protecting sensitive data include automating visibility, controlling access policies and implementing ongoing monitoring to identify vulnerabilities and risks before. Data security refers to the measures taken to prevent unauthorized access to databases and computer systems, data breaches, or any. Data security is the practice of protecting digital data from unauthorized access, use or disclosure in a. Data Security System Access.
From www.itopstimes.com
Creating a multilayered security architecture for your databases ITOps Times Data Security System Access Data security refers to the protective measures employed to secure data against unapproved access and to preserve data confidentiality, integrity, and availability. Data security is the practice of protecting digital information from unauthorized access, corruption or theft throughout its entire lifecycle. Access control involves two main processes: This concept encompasses the entire. Authentication and authorization technology does the work of. Data Security System Access.
From slimkm.com
4 Key Data Security Features in Library Management System iSLIM Algorhythms Data Security System Access This concept encompasses the entire. Data security refers to the protective measures employed to secure data against unapproved access and to preserve data confidentiality, integrity, and availability. Authentication is the process of ensuring users are who they say they are. The key steps in protecting sensitive data include automating visibility, controlling access policies and implementing ongoing monitoring to identify vulnerabilities. Data Security System Access.
From integratedtechnics.com
Integrated Technics Integrated Security Solutions Data Security System Access This concept encompasses the entire. Data security is the practice of protecting digital data from unauthorized access, use or disclosure in a manner consistent with an organization’s. Authentication is the process of ensuring users are who they say they are. Data security is the practice of protecting digital information from unauthorized access, corruption or theft throughout its entire lifecycle. The. Data Security System Access.
From www.poweradmin.com
How to Determine What Data Privacy Security Controls Your Business Needs Network Wrangler Data Security System Access Authentication and authorization technology does the work of confirming a user’s credentials—whether a password, pin, biometrics, or security tokens—are correct, and. Data security is the practice of protecting digital information from unauthorized access, corruption or theft throughout its entire lifecycle. This concept encompasses the entire. Access control involves two main processes: Data security refers to the protective measures employed to. Data Security System Access.
From www.ir.com
Understanding Network Security Tools & Protection IR Data Security System Access Data security is the practice of protecting digital data from unauthorized access, use or disclosure in a manner consistent with an organization’s. Data security is the practice of protecting digital information from unauthorized access, corruption or theft throughout its entire lifecycle. This concept encompasses the entire. The key steps in protecting sensitive data include automating visibility, controlling access policies and. Data Security System Access.
From www.memcyco.com
Data Security Management What is it, and How to Get it Right Data Security System Access Data security refers to the measures taken to prevent unauthorized access to databases and computer systems, data breaches, or any. Data security is the practice of protecting digital data from unauthorized access, use or disclosure in a manner consistent with an organization’s. The key steps in protecting sensitive data include automating visibility, controlling access policies and implementing ongoing monitoring to. Data Security System Access.
From www.securenetconsulting.co.uk
Data Protection Data Security System Access Authentication and authorization technology does the work of confirming a user’s credentials—whether a password, pin, biometrics, or security tokens—are correct, and. Data security refers to the protective measures employed to secure data against unapproved access and to preserve data confidentiality, integrity, and availability. Data security is the practice of protecting digital data from unauthorized access, use or disclosure in a. Data Security System Access.
From colohouse.com
What Is Data Center Security? Four Ways to Ensure Your Data Is Protected Colohouse Data Security System Access This concept encompasses the entire. Data security refers to the protective measures employed to secure data against unapproved access and to preserve data confidentiality, integrity, and availability. Data security refers to the measures taken to prevent unauthorized access to databases and computer systems, data breaches, or any. Access control involves two main processes: Authentication and authorization technology does the work. Data Security System Access.
From backendless.com
8 Critical Database Security Best Practices To Keep Your Data Safe Data Security System Access Authentication and authorization technology does the work of confirming a user’s credentials—whether a password, pin, biometrics, or security tokens—are correct, and. Data security refers to the protective measures employed to secure data against unapproved access and to preserve data confidentiality, integrity, and availability. The key steps in protecting sensitive data include automating visibility, controlling access policies and implementing ongoing monitoring. Data Security System Access.
From www.synergyitcybersecurity.com
Identity and Access Management (IAM) in your Organization with MSP Data Security System Access Access control involves two main processes: Data security is the practice of protecting digital data from unauthorized access, use or disclosure in a manner consistent with an organization’s. This concept encompasses the entire. Data security is the practice of protecting digital information from unauthorized access, corruption or theft throughout its entire lifecycle. The key steps in protecting sensitive data include. Data Security System Access.
From www.vecteezy.com
Security system access data concept. Security of data access. Modern flat design for Banner Data Security System Access Data security is the practice of protecting digital data from unauthorized access, use or disclosure in a manner consistent with an organization’s. Authentication and authorization technology does the work of confirming a user’s credentials—whether a password, pin, biometrics, or security tokens—are correct, and. Data security refers to the protective measures employed to secure data against unapproved access and to preserve. Data Security System Access.
From www.tecservuk.com
Biometric Access Control Systems Security Solutions Tecserv UK Data Security System Access Data security refers to the measures taken to prevent unauthorized access to databases and computer systems, data breaches, or any. The key steps in protecting sensitive data include automating visibility, controlling access policies and implementing ongoing monitoring to identify vulnerabilities and risks before. Access control involves two main processes: Authentication is the process of ensuring users are who they say. Data Security System Access.
From www.springboard.com
How To an Information Security Analyst [9 Step Guide] Data Security System Access The key steps in protecting sensitive data include automating visibility, controlling access policies and implementing ongoing monitoring to identify vulnerabilities and risks before. Authentication is the process of ensuring users are who they say they are. This concept encompasses the entire. Data security refers to the protective measures employed to secure data against unapproved access and to preserve data confidentiality,. Data Security System Access.
From arisant.com
Keep Your Sensitive Data Secure in 2020 with These 5 Steps! Data Security System Access Data security refers to the measures taken to prevent unauthorized access to databases and computer systems, data breaches, or any. Data security is the practice of protecting digital information from unauthorized access, corruption or theft throughout its entire lifecycle. This concept encompasses the entire. Data security is the practice of protecting digital data from unauthorized access, use or disclosure in. Data Security System Access.
From jelvix.com
What Is Database Security Standards, Threats, Protection Data Security System Access Authentication is the process of ensuring users are who they say they are. This concept encompasses the entire. Access control involves two main processes: Data security refers to the protective measures employed to secure data against unapproved access and to preserve data confidentiality, integrity, and availability. Data security is the practice of protecting digital data from unauthorized access, use or. Data Security System Access.
From braxtongrant.com
Understanding Key Identity & Access Management Components Blog Data Security System Access Authentication is the process of ensuring users are who they say they are. Authentication and authorization technology does the work of confirming a user’s credentials—whether a password, pin, biometrics, or security tokens—are correct, and. The key steps in protecting sensitive data include automating visibility, controlling access policies and implementing ongoing monitoring to identify vulnerabilities and risks before. Data security is. Data Security System Access.
From www.smartva.net
Protecting Your Data Blockchain and Its Impact on Information Security Data Security System Access Data security is the practice of protecting digital information from unauthorized access, corruption or theft throughout its entire lifecycle. Authentication and authorization technology does the work of confirming a user’s credentials—whether a password, pin, biometrics, or security tokens—are correct, and. Data security refers to the measures taken to prevent unauthorized access to databases and computer systems, data breaches, or any.. Data Security System Access.
From www.csoonline.com
What is access control? A key component of data security CSO Online Data Security System Access This concept encompasses the entire. Data security is the practice of protecting digital data from unauthorized access, use or disclosure in a manner consistent with an organization’s. Authentication and authorization technology does the work of confirming a user’s credentials—whether a password, pin, biometrics, or security tokens—are correct, and. Authentication is the process of ensuring users are who they say they. Data Security System Access.
From www.scanvis-ai.com
Key elements of IoTenabled physical access control solutions for data center security Data Security System Access Data security refers to the protective measures employed to secure data against unapproved access and to preserve data confidentiality, integrity, and availability. Data security refers to the measures taken to prevent unauthorized access to databases and computer systems, data breaches, or any. Authentication and authorization technology does the work of confirming a user’s credentials—whether a password, pin, biometrics, or security. Data Security System Access.
From www.freepik.com
Premium Vector Data security system concept protected access control privacy data protection Data Security System Access This concept encompasses the entire. Data security is the practice of protecting digital data from unauthorized access, use or disclosure in a manner consistent with an organization’s. Authentication and authorization technology does the work of confirming a user’s credentials—whether a password, pin, biometrics, or security tokens—are correct, and. Data security refers to the protective measures employed to secure data against. Data Security System Access.
From www.alamy.com
Security System Access Password Data Network Surveillance Concept Stock Photo Alamy Data Security System Access The key steps in protecting sensitive data include automating visibility, controlling access policies and implementing ongoing monitoring to identify vulnerabilities and risks before. Data security is the practice of protecting digital data from unauthorized access, use or disclosure in a manner consistent with an organization’s. This concept encompasses the entire. Authentication and authorization technology does the work of confirming a. Data Security System Access.
From thecyphere.com
What Is Database Security? Security Best Practices & Tips Data Security System Access Data security refers to the protective measures employed to secure data against unapproved access and to preserve data confidentiality, integrity, and availability. The key steps in protecting sensitive data include automating visibility, controlling access policies and implementing ongoing monitoring to identify vulnerabilities and risks before. Authentication and authorization technology does the work of confirming a user’s credentials—whether a password, pin,. Data Security System Access.
From www.rechenberg.com.au
EKA CyberKeys convenient & secure access control Rechenberg Data Security System Access The key steps in protecting sensitive data include automating visibility, controlling access policies and implementing ongoing monitoring to identify vulnerabilities and risks before. Authentication and authorization technology does the work of confirming a user’s credentials—whether a password, pin, biometrics, or security tokens—are correct, and. Data security refers to the protective measures employed to secure data against unapproved access and to. Data Security System Access.
From www.gdata.pt
G DATA Layered Security thoroughly sophisticated IT security Data Security System Access Data security refers to the measures taken to prevent unauthorized access to databases and computer systems, data breaches, or any. This concept encompasses the entire. Data security is the practice of protecting digital data from unauthorized access, use or disclosure in a manner consistent with an organization’s. Data security is the practice of protecting digital information from unauthorized access, corruption. Data Security System Access.
From bbi-consultancy.com
Ensuring Enterprise Data Security Solutions Infographic 2019 Data Driven Digital Data Security System Access Data security refers to the protective measures employed to secure data against unapproved access and to preserve data confidentiality, integrity, and availability. Authentication is the process of ensuring users are who they say they are. Data security is the practice of protecting digital data from unauthorized access, use or disclosure in a manner consistent with an organization’s. This concept encompasses. Data Security System Access.
From cyberhoot.com
Access Control Mechanism CyberHoot Data Security System Access Authentication is the process of ensuring users are who they say they are. This concept encompasses the entire. Authentication and authorization technology does the work of confirming a user’s credentials—whether a password, pin, biometrics, or security tokens—are correct, and. The key steps in protecting sensitive data include automating visibility, controlling access policies and implementing ongoing monitoring to identify vulnerabilities and. Data Security System Access.
From www.collidu.com
Information Security Management System PowerPoint Presentation Slides PPT Template Data Security System Access This concept encompasses the entire. Data security refers to the measures taken to prevent unauthorized access to databases and computer systems, data breaches, or any. Access control involves two main processes: Data security refers to the protective measures employed to secure data against unapproved access and to preserve data confidentiality, integrity, and availability. Authentication and authorization technology does the work. Data Security System Access.
From cie-group.com
How to design an Access Control system Data Security System Access Access control involves two main processes: Data security is the practice of protecting digital data from unauthorized access, use or disclosure in a manner consistent with an organization’s. Data security refers to the measures taken to prevent unauthorized access to databases and computer systems, data breaches, or any. Authentication and authorization technology does the work of confirming a user’s credentials—whether. Data Security System Access.
From securenetworkers.com
Cyber Security Data Protection Business Technology Privacy concept Secure Networkers Data Security System Access Data security is the practice of protecting digital information from unauthorized access, corruption or theft throughout its entire lifecycle. The key steps in protecting sensitive data include automating visibility, controlling access policies and implementing ongoing monitoring to identify vulnerabilities and risks before. Access control involves two main processes: Authentication is the process of ensuring users are who they say they. Data Security System Access.