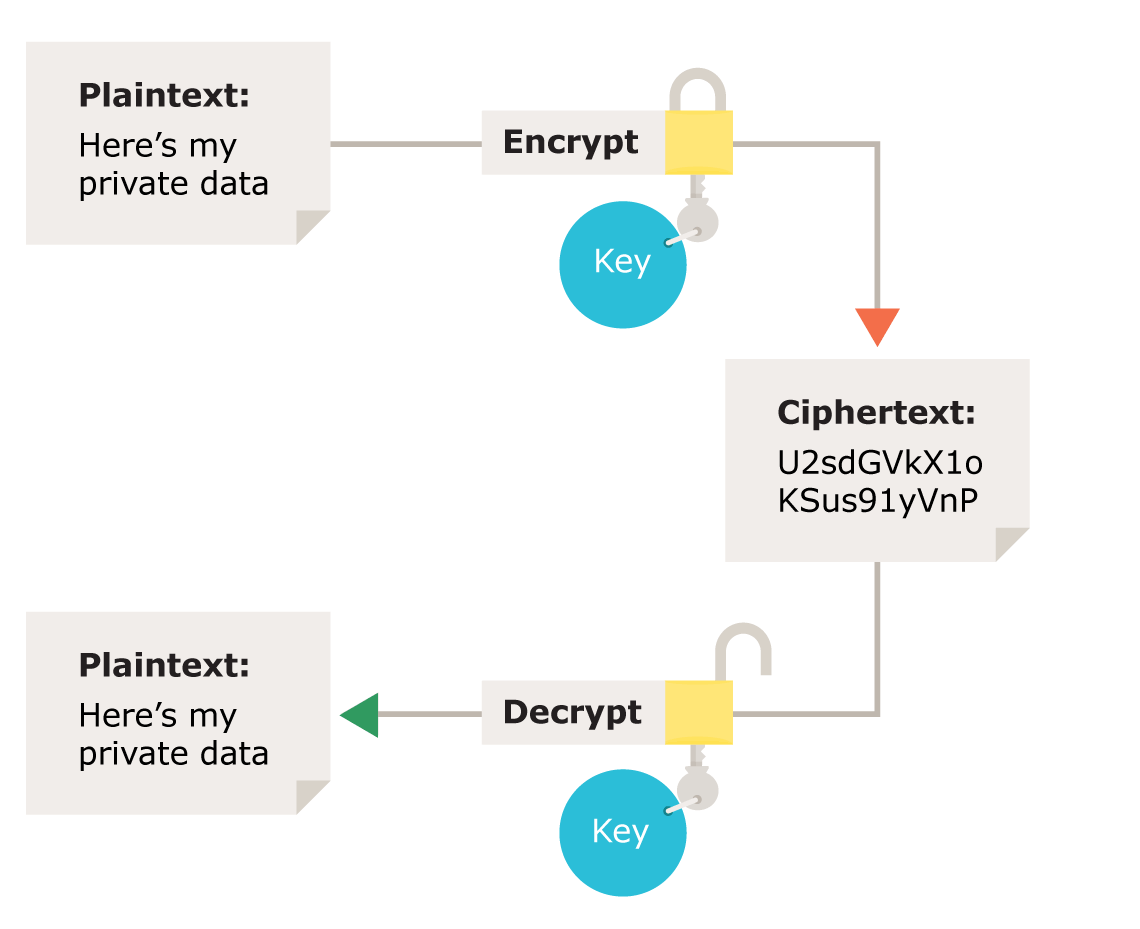
Salt Encryption Decryption . Tool to decrypt/encrypt md5 function automatically, decryption via a huge dictionary of potential passwords. This online tool helps you decrypt text or a file using aes. If an attacker does not know the. It supports various modes and padding schemes. This is an example of how to encrypt and decrypt using a salt. It would just make passwords longer. Tool to decrypt / encrypt with hash functions (md5, sha1, sha256, bcrypt, etc.) automatically (attack by brute/force + dictionary). A salt is a random number that is needed to access the encrypted data, along with the password. The salt is random data very often used in cryptography as.
from ico.org.uk
A salt is a random number that is needed to access the encrypted data, along with the password. Tool to decrypt / encrypt with hash functions (md5, sha1, sha256, bcrypt, etc.) automatically (attack by brute/force + dictionary). It would just make passwords longer. This online tool helps you decrypt text or a file using aes. It supports various modes and padding schemes. If an attacker does not know the. Tool to decrypt/encrypt md5 function automatically, decryption via a huge dictionary of potential passwords. The salt is random data very often used in cryptography as. This is an example of how to encrypt and decrypt using a salt.
Types of encryption ICO
Salt Encryption Decryption This is an example of how to encrypt and decrypt using a salt. A salt is a random number that is needed to access the encrypted data, along with the password. It would just make passwords longer. Tool to decrypt/encrypt md5 function automatically, decryption via a huge dictionary of potential passwords. This is an example of how to encrypt and decrypt using a salt. The salt is random data very often used in cryptography as. Tool to decrypt / encrypt with hash functions (md5, sha1, sha256, bcrypt, etc.) automatically (attack by brute/force + dictionary). It supports various modes and padding schemes. This online tool helps you decrypt text or a file using aes. If an attacker does not know the.
From 9to5answer.com
[Solved] how to implement sha 512,md5 and salt encryption 9to5Answer Salt Encryption Decryption It supports various modes and padding schemes. This is an example of how to encrypt and decrypt using a salt. The salt is random data very often used in cryptography as. A salt is a random number that is needed to access the encrypted data, along with the password. If an attacker does not know the. It would just make. Salt Encryption Decryption.
From medium.com
To Salt or Not To Salt? — Salting is not the only answer to securing Salt Encryption Decryption Tool to decrypt / encrypt with hash functions (md5, sha1, sha256, bcrypt, etc.) automatically (attack by brute/force + dictionary). A salt is a random number that is needed to access the encrypted data, along with the password. The salt is random data very often used in cryptography as. If an attacker does not know the. Tool to decrypt/encrypt md5 function. Salt Encryption Decryption.
From slideplayer.com
The OWASP Enterprise Security API ppt download Salt Encryption Decryption The salt is random data very often used in cryptography as. If an attacker does not know the. Tool to decrypt/encrypt md5 function automatically, decryption via a huge dictionary of potential passwords. This is an example of how to encrypt and decrypt using a salt. A salt is a random number that is needed to access the encrypted data, along. Salt Encryption Decryption.
From thecyphere.com
Difference Between Encryption And Hashing Salt Cryptography Salt Encryption Decryption This is an example of how to encrypt and decrypt using a salt. Tool to decrypt / encrypt with hash functions (md5, sha1, sha256, bcrypt, etc.) automatically (attack by brute/force + dictionary). It supports various modes and padding schemes. It would just make passwords longer. This online tool helps you decrypt text or a file using aes. Tool to decrypt/encrypt. Salt Encryption Decryption.
From cheapsslweb.com
Why Password Salt & Hash Make for Better Security? Salt Encryption Decryption If an attacker does not know the. A salt is a random number that is needed to access the encrypted data, along with the password. It would just make passwords longer. Tool to decrypt/encrypt md5 function automatically, decryption via a huge dictionary of potential passwords. Tool to decrypt / encrypt with hash functions (md5, sha1, sha256, bcrypt, etc.) automatically (attack. Salt Encryption Decryption.
From www.youtube.com
Custom Password Hash With Salt Key Password Encryption MVC Salt Encryption Decryption Tool to decrypt / encrypt with hash functions (md5, sha1, sha256, bcrypt, etc.) automatically (attack by brute/force + dictionary). A salt is a random number that is needed to access the encrypted data, along with the password. It would just make passwords longer. It supports various modes and padding schemes. This online tool helps you decrypt text or a file. Salt Encryption Decryption.
From slideplayer.com
Encryption 1way String Encryption Rainbows (a.k.a. Spectrums) ppt Salt Encryption Decryption This is an example of how to encrypt and decrypt using a salt. A salt is a random number that is needed to access the encrypted data, along with the password. If an attacker does not know the. Tool to decrypt/encrypt md5 function automatically, decryption via a huge dictionary of potential passwords. This online tool helps you decrypt text or. Salt Encryption Decryption.
From www.youtube.com
PHP SHA1 Salt Encryption Tutorial YouTube Salt Encryption Decryption Tool to decrypt/encrypt md5 function automatically, decryption via a huge dictionary of potential passwords. Tool to decrypt / encrypt with hash functions (md5, sha1, sha256, bcrypt, etc.) automatically (attack by brute/force + dictionary). A salt is a random number that is needed to access the encrypted data, along with the password. This online tool helps you decrypt text or a. Salt Encryption Decryption.
From www.wallarm.com
Hashing vs Encryption vs Salting What’s The Difference? 🤷🏽♂️ Salt Encryption Decryption If an attacker does not know the. It would just make passwords longer. This is an example of how to encrypt and decrypt using a salt. Tool to decrypt/encrypt md5 function automatically, decryption via a huge dictionary of potential passwords. A salt is a random number that is needed to access the encrypted data, along with the password. Tool to. Salt Encryption Decryption.
From www.omnicybersecurity.com
What does salting the hash mean (and is it effective?) OmniCyber Security Salt Encryption Decryption A salt is a random number that is needed to access the encrypted data, along with the password. Tool to decrypt/encrypt md5 function automatically, decryption via a huge dictionary of potential passwords. This is an example of how to encrypt and decrypt using a salt. Tool to decrypt / encrypt with hash functions (md5, sha1, sha256, bcrypt, etc.) automatically (attack. Salt Encryption Decryption.
From ico.org.uk
Types of encryption ICO Salt Encryption Decryption A salt is a random number that is needed to access the encrypted data, along with the password. It supports various modes and padding schemes. This is an example of how to encrypt and decrypt using a salt. The salt is random data very often used in cryptography as. This online tool helps you decrypt text or a file using. Salt Encryption Decryption.
From thomashunter.name
Password Encryption, Hashing, Salting Explained Thomas Hunter II Salt Encryption Decryption It would just make passwords longer. Tool to decrypt / encrypt with hash functions (md5, sha1, sha256, bcrypt, etc.) automatically (attack by brute/force + dictionary). The salt is random data very often used in cryptography as. This is an example of how to encrypt and decrypt using a salt. Tool to decrypt/encrypt md5 function automatically, decryption via a huge dictionary. Salt Encryption Decryption.
From www.youtube.com
PYTHON Encrypt / decrypt data in python with salt YouTube Salt Encryption Decryption A salt is a random number that is needed to access the encrypted data, along with the password. This is an example of how to encrypt and decrypt using a salt. The salt is random data very often used in cryptography as. Tool to decrypt/encrypt md5 function automatically, decryption via a huge dictionary of potential passwords. This online tool helps. Salt Encryption Decryption.
From www.thesslstore.com
Password Salting A Savory Way to Secure Your Secrets Hashed Out by Salt Encryption Decryption If an attacker does not know the. This online tool helps you decrypt text or a file using aes. The salt is random data very often used in cryptography as. It would just make passwords longer. Tool to decrypt / encrypt with hash functions (md5, sha1, sha256, bcrypt, etc.) automatically (attack by brute/force + dictionary). This is an example of. Salt Encryption Decryption.
From us.norton.com
What is encryption? How it works + types of encryption Norton Salt Encryption Decryption Tool to decrypt/encrypt md5 function automatically, decryption via a huge dictionary of potential passwords. This is an example of how to encrypt and decrypt using a salt. If an attacker does not know the. It would just make passwords longer. The salt is random data very often used in cryptography as. It supports various modes and padding schemes. Tool to. Salt Encryption Decryption.
From www.youtube.com
006 What Are Encryption, Hashing And Salting Techniques How Does Salt Encryption Decryption Tool to decrypt / encrypt with hash functions (md5, sha1, sha256, bcrypt, etc.) automatically (attack by brute/force + dictionary). It supports various modes and padding schemes. It would just make passwords longer. If an attacker does not know the. The salt is random data very often used in cryptography as. This is an example of how to encrypt and decrypt. Salt Encryption Decryption.
From ah.moneyu.pl
Md5 salt decrypt Salt Encryption Decryption A salt is a random number that is needed to access the encrypted data, along with the password. If an attacker does not know the. This is an example of how to encrypt and decrypt using a salt. This online tool helps you decrypt text or a file using aes. Tool to decrypt/encrypt md5 function automatically, decryption via a huge. Salt Encryption Decryption.
From www.cisco.com
What Is Encryption? Explanation and Types Cisco Salt Encryption Decryption It would just make passwords longer. Tool to decrypt/encrypt md5 function automatically, decryption via a huge dictionary of potential passwords. This online tool helps you decrypt text or a file using aes. If an attacker does not know the. Tool to decrypt / encrypt with hash functions (md5, sha1, sha256, bcrypt, etc.) automatically (attack by brute/force + dictionary). This is. Salt Encryption Decryption.
From www.imgoinglive.com
Encrypt and Decrypt Tool Salt Encryption Decryption It would just make passwords longer. It supports various modes and padding schemes. The salt is random data very often used in cryptography as. If an attacker does not know the. Tool to decrypt / encrypt with hash functions (md5, sha1, sha256, bcrypt, etc.) automatically (attack by brute/force + dictionary). Tool to decrypt/encrypt md5 function automatically, decryption via a huge. Salt Encryption Decryption.
From www.comparitech.com
Encryption, hashing, salting What's the difference and how do they work Salt Encryption Decryption Tool to decrypt / encrypt with hash functions (md5, sha1, sha256, bcrypt, etc.) automatically (attack by brute/force + dictionary). A salt is a random number that is needed to access the encrypted data, along with the password. If an attacker does not know the. Tool to decrypt/encrypt md5 function automatically, decryption via a huge dictionary of potential passwords. It would. Salt Encryption Decryption.
From www.thesslstore.com
The difference between Encryption, Hashing and Salting Salt Encryption Decryption A salt is a random number that is needed to access the encrypted data, along with the password. It would just make passwords longer. Tool to decrypt/encrypt md5 function automatically, decryption via a huge dictionary of potential passwords. It supports various modes and padding schemes. The salt is random data very often used in cryptography as. If an attacker does. Salt Encryption Decryption.
From www.wallarm.com
Hashing vs Encryption vs Salting What’s The Difference? 🤷🏽♂️ Salt Encryption Decryption It supports various modes and padding schemes. Tool to decrypt/encrypt md5 function automatically, decryption via a huge dictionary of potential passwords. Tool to decrypt / encrypt with hash functions (md5, sha1, sha256, bcrypt, etc.) automatically (attack by brute/force + dictionary). The salt is random data very often used in cryptography as. This online tool helps you decrypt text or a. Salt Encryption Decryption.
From thecyphere.com
Difference Between Encryption And Hashing Salt Cryptography Salt Encryption Decryption Tool to decrypt / encrypt with hash functions (md5, sha1, sha256, bcrypt, etc.) automatically (attack by brute/force + dictionary). It supports various modes and padding schemes. This online tool helps you decrypt text or a file using aes. The salt is random data very often used in cryptography as. It would just make passwords longer. This is an example of. Salt Encryption Decryption.
From coderjony.com
CoderJony The difference between Encryption, Hashing & Salting Salt Encryption Decryption It would just make passwords longer. This online tool helps you decrypt text or a file using aes. Tool to decrypt/encrypt md5 function automatically, decryption via a huge dictionary of potential passwords. Tool to decrypt / encrypt with hash functions (md5, sha1, sha256, bcrypt, etc.) automatically (attack by brute/force + dictionary). It supports various modes and padding schemes. This is. Salt Encryption Decryption.
From sectigostore.com
What Is Asymmetric Encryption & How Does It Work? InfoSec Insights Salt Encryption Decryption It would just make passwords longer. The salt is random data very often used in cryptography as. If an attacker does not know the. Tool to decrypt/encrypt md5 function automatically, decryption via a huge dictionary of potential passwords. This is an example of how to encrypt and decrypt using a salt. This online tool helps you decrypt text or a. Salt Encryption Decryption.
From www.xpress-vpn.com
Password Hashing and Salting Explained ExpressVPN Blog Salt Encryption Decryption The salt is random data very often used in cryptography as. If an attacker does not know the. A salt is a random number that is needed to access the encrypted data, along with the password. This online tool helps you decrypt text or a file using aes. It supports various modes and padding schemes. Tool to decrypt/encrypt md5 function. Salt Encryption Decryption.
From www.youtube.com
Encryption Hashing Encoding and Salting YouTube Salt Encryption Decryption If an attacker does not know the. It would just make passwords longer. The salt is random data very often used in cryptography as. This is an example of how to encrypt and decrypt using a salt. This online tool helps you decrypt text or a file using aes. It supports various modes and padding schemes. Tool to decrypt/encrypt md5. Salt Encryption Decryption.
From www.expressvpn.com
Password Hashing and Salting Explained ExpressVPN Blog Salt Encryption Decryption Tool to decrypt/encrypt md5 function automatically, decryption via a huge dictionary of potential passwords. This is an example of how to encrypt and decrypt using a salt. Tool to decrypt / encrypt with hash functions (md5, sha1, sha256, bcrypt, etc.) automatically (attack by brute/force + dictionary). This online tool helps you decrypt text or a file using aes. It would. Salt Encryption Decryption.
From www.youtube.com
Strong Password Encryption and Decryption (Salting, Hashing and Salt Encryption Decryption A salt is a random number that is needed to access the encrypted data, along with the password. This online tool helps you decrypt text or a file using aes. Tool to decrypt / encrypt with hash functions (md5, sha1, sha256, bcrypt, etc.) automatically (attack by brute/force + dictionary). It would just make passwords longer. If an attacker does not. Salt Encryption Decryption.
From rafalsblogblog.wordpress.com
Cyber Security Salt Encryption Decryption This is an example of how to encrypt and decrypt using a salt. This online tool helps you decrypt text or a file using aes. If an attacker does not know the. It would just make passwords longer. Tool to decrypt/encrypt md5 function automatically, decryption via a huge dictionary of potential passwords. A salt is a random number that is. Salt Encryption Decryption.
From thecyphere.com
Difference Between Encryption And Hashing Salt Cryptography Salt Encryption Decryption This online tool helps you decrypt text or a file using aes. The salt is random data very often used in cryptography as. This is an example of how to encrypt and decrypt using a salt. It supports various modes and padding schemes. Tool to decrypt/encrypt md5 function automatically, decryption via a huge dictionary of potential passwords. If an attacker. Salt Encryption Decryption.
From slideplayer.com
Authentication and Identification ppt download Salt Encryption Decryption If an attacker does not know the. Tool to decrypt/encrypt md5 function automatically, decryption via a huge dictionary of potential passwords. The salt is random data very often used in cryptography as. It would just make passwords longer. It supports various modes and padding schemes. A salt is a random number that is needed to access the encrypted data, along. Salt Encryption Decryption.
From www.researchgate.net
Classification of encryption First of all, encrypted data has been Salt Encryption Decryption Tool to decrypt / encrypt with hash functions (md5, sha1, sha256, bcrypt, etc.) automatically (attack by brute/force + dictionary). It would just make passwords longer. If an attacker does not know the. A salt is a random number that is needed to access the encrypted data, along with the password. Tool to decrypt/encrypt md5 function automatically, decryption via a huge. Salt Encryption Decryption.
From hackernoon.com
What devs need to know about Encoding / Encryption / Hashing / Salting Salt Encryption Decryption Tool to decrypt / encrypt with hash functions (md5, sha1, sha256, bcrypt, etc.) automatically (attack by brute/force + dictionary). This is an example of how to encrypt and decrypt using a salt. The salt is random data very often used in cryptography as. It would just make passwords longer. This online tool helps you decrypt text or a file using. Salt Encryption Decryption.
From www.youtube.com
Salted Password Scheme Applied Cryptography YouTube Salt Encryption Decryption Tool to decrypt / encrypt with hash functions (md5, sha1, sha256, bcrypt, etc.) automatically (attack by brute/force + dictionary). Tool to decrypt/encrypt md5 function automatically, decryption via a huge dictionary of potential passwords. This online tool helps you decrypt text or a file using aes. This is an example of how to encrypt and decrypt using a salt. The salt. Salt Encryption Decryption.