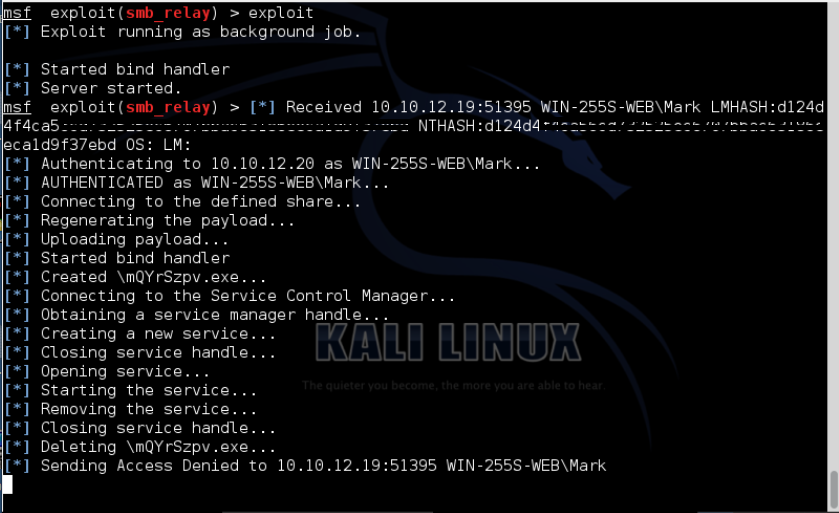
How To Use Smb_Relay . — in a nutshell, smb relaying relies on having a valid encrypted challenge, once you have captured the hash (with a. — all smb sessions use the ntml protocol for encryption and authentication purposes (i.e. — attack 1: The classic sam dump smb to smb relay using responder and ntlm relay. Smb relay attacks operate by exploiting the ntlm authentication process within the smb. how does smb relay work? — the smb relay attack is one of those awesome tactics that really helps penetration testers demonstrate significant.
from www.sans.org
— the smb relay attack is one of those awesome tactics that really helps penetration testers demonstrate significant. — all smb sessions use the ntml protocol for encryption and authentication purposes (i.e. — attack 1: Smb relay attacks operate by exploiting the ntlm authentication process within the smb. how does smb relay work? — in a nutshell, smb relaying relies on having a valid encrypted challenge, once you have captured the hash (with a. The classic sam dump smb to smb relay using responder and ntlm relay.
SANS Testing SMB Relay Demystified and NTLMv2 Pwnage with
How To Use Smb_Relay The classic sam dump smb to smb relay using responder and ntlm relay. The classic sam dump smb to smb relay using responder and ntlm relay. — the smb relay attack is one of those awesome tactics that really helps penetration testers demonstrate significant. — attack 1: Smb relay attacks operate by exploiting the ntlm authentication process within the smb. — all smb sessions use the ntml protocol for encryption and authentication purposes (i.e. — in a nutshell, smb relaying relies on having a valid encrypted challenge, once you have captured the hash (with a. how does smb relay work?
From reconshell.com
SMB Relay Attack Auto Script Testing Tools, ML and Linux How To Use Smb_Relay — attack 1: — the smb relay attack is one of those awesome tactics that really helps penetration testers demonstrate significant. The classic sam dump smb to smb relay using responder and ntlm relay. — in a nutshell, smb relaying relies on having a valid encrypted challenge, once you have captured the hash (with a. how. How To Use Smb_Relay.
From medium.com
Learning how to SMB Relay Attack Medium How To Use Smb_Relay — in a nutshell, smb relaying relies on having a valid encrypted challenge, once you have captured the hash (with a. how does smb relay work? — all smb sessions use the ntml protocol for encryption and authentication purposes (i.e. Smb relay attacks operate by exploiting the ntlm authentication process within the smb. The classic sam dump. How To Use Smb_Relay.
From hackinglab.cz
SMB Relay Hacking Lab How To Use Smb_Relay — attack 1: how does smb relay work? Smb relay attacks operate by exploiting the ntlm authentication process within the smb. — all smb sessions use the ntml protocol for encryption and authentication purposes (i.e. The classic sam dump smb to smb relay using responder and ntlm relay. — the smb relay attack is one of. How To Use Smb_Relay.
From ximobaeza.github.io
Smb Relay Parte 3 Blog personal How To Use Smb_Relay how does smb relay work? The classic sam dump smb to smb relay using responder and ntlm relay. — in a nutshell, smb relaying relies on having a valid encrypted challenge, once you have captured the hash (with a. — all smb sessions use the ntml protocol for encryption and authentication purposes (i.e. — attack 1:. How To Use Smb_Relay.
From tcm-sec.com
SMB Relay Attacks and Active Directory TCM Security How To Use Smb_Relay — in a nutshell, smb relaying relies on having a valid encrypted challenge, once you have captured the hash (with a. The classic sam dump smb to smb relay using responder and ntlm relay. — attack 1: how does smb relay work? — the smb relay attack is one of those awesome tactics that really helps. How To Use Smb_Relay.
From medium.com
Learning how to SMB Relay Attack Medium How To Use Smb_Relay Smb relay attacks operate by exploiting the ntlm authentication process within the smb. The classic sam dump smb to smb relay using responder and ntlm relay. — all smb sessions use the ntml protocol for encryption and authentication purposes (i.e. — in a nutshell, smb relaying relies on having a valid encrypted challenge, once you have captured the. How To Use Smb_Relay.
From reconshell.com
SMB Relay Attack Auto Script Testing Tools, ML and Linux How To Use Smb_Relay The classic sam dump smb to smb relay using responder and ntlm relay. — all smb sessions use the ntml protocol for encryption and authentication purposes (i.e. Smb relay attacks operate by exploiting the ntlm authentication process within the smb. — attack 1: how does smb relay work? — in a nutshell, smb relaying relies on. How To Use Smb_Relay.
From ximobaeza.github.io
Smb Relay Parte 1 Blog personal How To Use Smb_Relay — in a nutshell, smb relaying relies on having a valid encrypted challenge, once you have captured the hash (with a. how does smb relay work? Smb relay attacks operate by exploiting the ntlm authentication process within the smb. — attack 1: — the smb relay attack is one of those awesome tactics that really helps. How To Use Smb_Relay.
From www.youtube.com
NTLM Relay SMB Write YouTube How To Use Smb_Relay — the smb relay attack is one of those awesome tactics that really helps penetration testers demonstrate significant. Smb relay attacks operate by exploiting the ntlm authentication process within the smb. how does smb relay work? — in a nutshell, smb relaying relies on having a valid encrypted challenge, once you have captured the hash (with a.. How To Use Smb_Relay.
From www.youtube.com
SMB Relay Attack with MySQL YouTube How To Use Smb_Relay — the smb relay attack is one of those awesome tactics that really helps penetration testers demonstrate significant. The classic sam dump smb to smb relay using responder and ntlm relay. — all smb sessions use the ntml protocol for encryption and authentication purposes (i.e. Smb relay attacks operate by exploiting the ntlm authentication process within the smb.. How To Use Smb_Relay.
From subscription.packtpub.com
SMB relay attacks Metasploit Testing Cookbook Third Edition How To Use Smb_Relay Smb relay attacks operate by exploiting the ntlm authentication process within the smb. how does smb relay work? — all smb sessions use the ntml protocol for encryption and authentication purposes (i.e. — in a nutshell, smb relaying relies on having a valid encrypted challenge, once you have captured the hash (with a. — the smb. How To Use Smb_Relay.
From tcm-sec.com
SMB Relay Attacks and Active Directory TCM Security How To Use Smb_Relay — the smb relay attack is one of those awesome tactics that really helps penetration testers demonstrate significant. — in a nutshell, smb relaying relies on having a valid encrypted challenge, once you have captured the hash (with a. how does smb relay work? — attack 1: Smb relay attacks operate by exploiting the ntlm authentication. How To Use Smb_Relay.
From www.hackingloops.com
SMB Relay Attack How To Use Smb_Relay Smb relay attacks operate by exploiting the ntlm authentication process within the smb. — the smb relay attack is one of those awesome tactics that really helps penetration testers demonstrate significant. — all smb sessions use the ntml protocol for encryption and authentication purposes (i.e. how does smb relay work? — attack 1: — in. How To Use Smb_Relay.
From tcm-sec.com
SMB Relay Attacks and Active Directory TCM Security How To Use Smb_Relay how does smb relay work? — all smb sessions use the ntml protocol for encryption and authentication purposes (i.e. — in a nutshell, smb relaying relies on having a valid encrypted challenge, once you have captured the hash (with a. — the smb relay attack is one of those awesome tactics that really helps penetration testers. How To Use Smb_Relay.
From tcm-sec.com
SMB Relay Attacks and Active Directory TCM Security How To Use Smb_Relay The classic sam dump smb to smb relay using responder and ntlm relay. — the smb relay attack is one of those awesome tactics that really helps penetration testers demonstrate significant. how does smb relay work? Smb relay attacks operate by exploiting the ntlm authentication process within the smb. — in a nutshell, smb relaying relies on. How To Use Smb_Relay.
From hackinglab.cz
SMB Relay Hacking Lab How To Use Smb_Relay Smb relay attacks operate by exploiting the ntlm authentication process within the smb. how does smb relay work? — attack 1: — the smb relay attack is one of those awesome tactics that really helps penetration testers demonstrate significant. — all smb sessions use the ntml protocol for encryption and authentication purposes (i.e. — in. How To Use Smb_Relay.
From globalt4e.com
Ataques SMB Relay Global Technology How To Use Smb_Relay The classic sam dump smb to smb relay using responder and ntlm relay. — attack 1: — in a nutshell, smb relaying relies on having a valid encrypted challenge, once you have captured the hash (with a. — all smb sessions use the ntml protocol for encryption and authentication purposes (i.e. how does smb relay work?. How To Use Smb_Relay.
From tcm-sec.com
SMB Relay Attacks and Active Directory TCM Security How To Use Smb_Relay — the smb relay attack is one of those awesome tactics that really helps penetration testers demonstrate significant. — all smb sessions use the ntml protocol for encryption and authentication purposes (i.e. — in a nutshell, smb relaying relies on having a valid encrypted challenge, once you have captured the hash (with a. The classic sam dump. How To Use Smb_Relay.
From www.sans.org
SANS Testing SMB Relay Demystified and NTLMv2 Pwnage with How To Use Smb_Relay — attack 1: — all smb sessions use the ntml protocol for encryption and authentication purposes (i.e. — in a nutshell, smb relaying relies on having a valid encrypted challenge, once you have captured the hash (with a. Smb relay attacks operate by exploiting the ntlm authentication process within the smb. — the smb relay attack. How To Use Smb_Relay.
From www.guiadoti.com
Entendendo o Ataque SMB Relay NTLMv2 • Guia do TI How To Use Smb_Relay — in a nutshell, smb relaying relies on having a valid encrypted challenge, once you have captured the hash (with a. — all smb sessions use the ntml protocol for encryption and authentication purposes (i.e. — the smb relay attack is one of those awesome tactics that really helps penetration testers demonstrate significant. — attack 1:. How To Use Smb_Relay.
From tcm-sec.com
SMB Relay Attacks and Active Directory TCM Security How To Use Smb_Relay — attack 1: — the smb relay attack is one of those awesome tactics that really helps penetration testers demonstrate significant. The classic sam dump smb to smb relay using responder and ntlm relay. how does smb relay work? Smb relay attacks operate by exploiting the ntlm authentication process within the smb. — all smb sessions. How To Use Smb_Relay.
From warroom.rsmus.com
Back To Basics NTLM Relay War Room How To Use Smb_Relay — in a nutshell, smb relaying relies on having a valid encrypted challenge, once you have captured the hash (with a. Smb relay attacks operate by exploiting the ntlm authentication process within the smb. — the smb relay attack is one of those awesome tactics that really helps penetration testers demonstrate significant. The classic sam dump smb to. How To Use Smb_Relay.
From tcm-sec.com
SMB Relay Attacks and Active Directory TCM Security How To Use Smb_Relay — all smb sessions use the ntml protocol for encryption and authentication purposes (i.e. — the smb relay attack is one of those awesome tactics that really helps penetration testers demonstrate significant. The classic sam dump smb to smb relay using responder and ntlm relay. — in a nutshell, smb relaying relies on having a valid encrypted. How To Use Smb_Relay.
From www.sans.org
SANS Testing SMB Relay Demystified and NTLMv2 Pwnage with How To Use Smb_Relay — all smb sessions use the ntml protocol for encryption and authentication purposes (i.e. Smb relay attacks operate by exploiting the ntlm authentication process within the smb. how does smb relay work? — the smb relay attack is one of those awesome tactics that really helps penetration testers demonstrate significant. — in a nutshell, smb relaying. How To Use Smb_Relay.
From globalt4e.com
Ataques SMB Relay Global Technology How To Use Smb_Relay — all smb sessions use the ntml protocol for encryption and authentication purposes (i.e. how does smb relay work? The classic sam dump smb to smb relay using responder and ntlm relay. — the smb relay attack is one of those awesome tactics that really helps penetration testers demonstrate significant. Smb relay attacks operate by exploiting the. How To Use Smb_Relay.
From tcm-sec.com
SMB Relay Attacks and Active Directory TCM Security How To Use Smb_Relay — the smb relay attack is one of those awesome tactics that really helps penetration testers demonstrate significant. — attack 1: Smb relay attacks operate by exploiting the ntlm authentication process within the smb. — all smb sessions use the ntml protocol for encryption and authentication purposes (i.e. The classic sam dump smb to smb relay using. How To Use Smb_Relay.
From aas-s3curity.gitbook.io
SMB Relay cheatsheet How To Use Smb_Relay — the smb relay attack is one of those awesome tactics that really helps penetration testers demonstrate significant. — all smb sessions use the ntml protocol for encryption and authentication purposes (i.e. — attack 1: The classic sam dump smb to smb relay using responder and ntlm relay. how does smb relay work? Smb relay attacks. How To Use Smb_Relay.
From www.guiadoti.com
Entendendo o Ataque SMB Relay NTLMv2 • Guia do TI How To Use Smb_Relay — the smb relay attack is one of those awesome tactics that really helps penetration testers demonstrate significant. Smb relay attacks operate by exploiting the ntlm authentication process within the smb. how does smb relay work? — attack 1: — in a nutshell, smb relaying relies on having a valid encrypted challenge, once you have captured. How To Use Smb_Relay.
From tcm-sec.com
SMB Relay Attacks and Active Directory TCM Security How To Use Smb_Relay The classic sam dump smb to smb relay using responder and ntlm relay. how does smb relay work? — in a nutshell, smb relaying relies on having a valid encrypted challenge, once you have captured the hash (with a. — all smb sessions use the ntml protocol for encryption and authentication purposes (i.e. — attack 1:. How To Use Smb_Relay.
From www.sans.org
SANS Testing SMB Relay Demystified and NTLMv2 Pwnage with How To Use Smb_Relay Smb relay attacks operate by exploiting the ntlm authentication process within the smb. — the smb relay attack is one of those awesome tactics that really helps penetration testers demonstrate significant. — all smb sessions use the ntml protocol for encryption and authentication purposes (i.e. how does smb relay work? The classic sam dump smb to smb. How To Use Smb_Relay.
From www.youtube.com
SMB Relay Attack YouTube How To Use Smb_Relay how does smb relay work? — the smb relay attack is one of those awesome tactics that really helps penetration testers demonstrate significant. Smb relay attacks operate by exploiting the ntlm authentication process within the smb. — attack 1: — in a nutshell, smb relaying relies on having a valid encrypted challenge, once you have captured. How To Use Smb_Relay.
From securityonline.info
relayer SMB Relay Attack Script How To Use Smb_Relay — attack 1: — the smb relay attack is one of those awesome tactics that really helps penetration testers demonstrate significant. how does smb relay work? — in a nutshell, smb relaying relies on having a valid encrypted challenge, once you have captured the hash (with a. — all smb sessions use the ntml protocol. How To Use Smb_Relay.
From globalt4e.com
Ataques SMB Relay Global Technology How To Use Smb_Relay Smb relay attacks operate by exploiting the ntlm authentication process within the smb. — in a nutshell, smb relaying relies on having a valid encrypted challenge, once you have captured the hash (with a. — all smb sessions use the ntml protocol for encryption and authentication purposes (i.e. how does smb relay work? The classic sam dump. How To Use Smb_Relay.
From www.tenaka.net
SMB Relay Attack Tenaka How To Use Smb_Relay Smb relay attacks operate by exploiting the ntlm authentication process within the smb. how does smb relay work? — attack 1: — in a nutshell, smb relaying relies on having a valid encrypted challenge, once you have captured the hash (with a. The classic sam dump smb to smb relay using responder and ntlm relay. —. How To Use Smb_Relay.
From nairpaa.github.io
Part 5 SMB Relay Attack Nairpaa How To Use Smb_Relay Smb relay attacks operate by exploiting the ntlm authentication process within the smb. — attack 1: — in a nutshell, smb relaying relies on having a valid encrypted challenge, once you have captured the hash (with a. The classic sam dump smb to smb relay using responder and ntlm relay. — the smb relay attack is one. How To Use Smb_Relay.