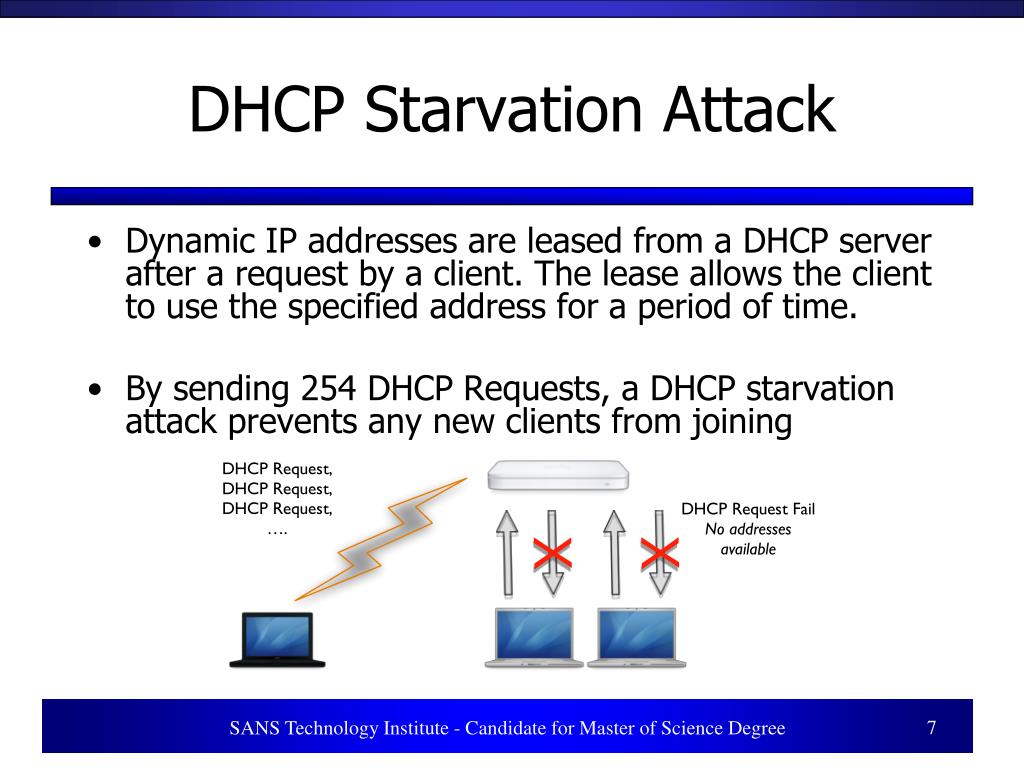
Data Link Layer Attacks . the data link layer dictates how data is allowed to travel between physically connected points. Learn how to secure this part of the osi layers system. It covers physical layer wiretapping, data link layer vlan hopping, and network layer ping sweep attacks. The main attacks that occur at layer 2 include: layer 2 attacks refer to attacks that occur at the data link layer (layer 2) of the osi model. this web page explains the osi model and its layers with examples of attacks and mitigation strategies.
from www.slideserve.com
this web page explains the osi model and its layers with examples of attacks and mitigation strategies. Learn how to secure this part of the osi layers system. The main attacks that occur at layer 2 include: the data link layer dictates how data is allowed to travel between physically connected points. It covers physical layer wiretapping, data link layer vlan hopping, and network layer ping sweep attacks. layer 2 attacks refer to attacks that occur at the data link layer (layer 2) of the osi model.
PPT Detecting and Responding to Data Link Layer Attacks With Scapy
Data Link Layer Attacks this web page explains the osi model and its layers with examples of attacks and mitigation strategies. Learn how to secure this part of the osi layers system. this web page explains the osi model and its layers with examples of attacks and mitigation strategies. It covers physical layer wiretapping, data link layer vlan hopping, and network layer ping sweep attacks. layer 2 attacks refer to attacks that occur at the data link layer (layer 2) of the osi model. the data link layer dictates how data is allowed to travel between physically connected points. The main attacks that occur at layer 2 include:
From digikul.net
Learn Skill on Computer, Networking, Software and How to fix technical Data Link Layer Attacks the data link layer dictates how data is allowed to travel between physically connected points. The main attacks that occur at layer 2 include: layer 2 attacks refer to attacks that occur at the data link layer (layer 2) of the osi model. It covers physical layer wiretapping, data link layer vlan hopping, and network layer ping sweep. Data Link Layer Attacks.
From networkwalks.com
Data Link Layer of OSI Model (Layer2) Network Walks Academy Data Link Layer Attacks The main attacks that occur at layer 2 include: It covers physical layer wiretapping, data link layer vlan hopping, and network layer ping sweep attacks. the data link layer dictates how data is allowed to travel between physically connected points. this web page explains the osi model and its layers with examples of attacks and mitigation strategies. . Data Link Layer Attacks.
From www.researchgate.net
(PDF) Detecting and Responding to Data Link Layer Attacks Data Link Layer Attacks It covers physical layer wiretapping, data link layer vlan hopping, and network layer ping sweep attacks. The main attacks that occur at layer 2 include: this web page explains the osi model and its layers with examples of attacks and mitigation strategies. the data link layer dictates how data is allowed to travel between physically connected points. Learn. Data Link Layer Attacks.
From techscience.com
CMC Free FullText Wireless Sensor Security Issues on Data Link Data Link Layer Attacks The main attacks that occur at layer 2 include: layer 2 attacks refer to attacks that occur at the data link layer (layer 2) of the osi model. It covers physical layer wiretapping, data link layer vlan hopping, and network layer ping sweep attacks. the data link layer dictates how data is allowed to travel between physically connected. Data Link Layer Attacks.
From www.slideserve.com
PPT Detecting and Responding to Data Link Layer Attacks With Scapy Data Link Layer Attacks Learn how to secure this part of the osi layers system. this web page explains the osi model and its layers with examples of attacks and mitigation strategies. The main attacks that occur at layer 2 include: layer 2 attacks refer to attacks that occur at the data link layer (layer 2) of the osi model. the. Data Link Layer Attacks.
From exonkuxev.blob.core.windows.net
Data Link Layer Summary at Christine Poyner blog Data Link Layer Attacks Learn how to secure this part of the osi layers system. It covers physical layer wiretapping, data link layer vlan hopping, and network layer ping sweep attacks. layer 2 attacks refer to attacks that occur at the data link layer (layer 2) of the osi model. this web page explains the osi model and its layers with examples. Data Link Layer Attacks.
From www.researchgate.net
Datalink layer attacks Download Scientific Diagram Data Link Layer Attacks layer 2 attacks refer to attacks that occur at the data link layer (layer 2) of the osi model. the data link layer dictates how data is allowed to travel between physically connected points. this web page explains the osi model and its layers with examples of attacks and mitigation strategies. Learn how to secure this part. Data Link Layer Attacks.
From www.hackercoolmagazine.com
DataLink layer attacks Hackercool Magazine Data Link Layer Attacks Learn how to secure this part of the osi layers system. layer 2 attacks refer to attacks that occur at the data link layer (layer 2) of the osi model. The main attacks that occur at layer 2 include: the data link layer dictates how data is allowed to travel between physically connected points. It covers physical layer. Data Link Layer Attacks.
From slidetodoc.com
Detecting and Responding to Data Link Layer Attacks Data Link Layer Attacks Learn how to secure this part of the osi layers system. the data link layer dictates how data is allowed to travel between physically connected points. The main attacks that occur at layer 2 include: layer 2 attacks refer to attacks that occur at the data link layer (layer 2) of the osi model. this web page. Data Link Layer Attacks.
From www.slideserve.com
PPT Detecting and Responding to Data Link Layer Attacks With Scapy Data Link Layer Attacks The main attacks that occur at layer 2 include: this web page explains the osi model and its layers with examples of attacks and mitigation strategies. It covers physical layer wiretapping, data link layer vlan hopping, and network layer ping sweep attacks. layer 2 attacks refer to attacks that occur at the data link layer (layer 2) of. Data Link Layer Attacks.
From slidetodoc.com
Detecting and Responding to Data Link Layer Attacks Data Link Layer Attacks It covers physical layer wiretapping, data link layer vlan hopping, and network layer ping sweep attacks. layer 2 attacks refer to attacks that occur at the data link layer (layer 2) of the osi model. this web page explains the osi model and its layers with examples of attacks and mitigation strategies. Learn how to secure this part. Data Link Layer Attacks.
From slidetodoc.com
Detecting and Responding to Data Link Layer Attacks Data Link Layer Attacks It covers physical layer wiretapping, data link layer vlan hopping, and network layer ping sweep attacks. the data link layer dictates how data is allowed to travel between physically connected points. Learn how to secure this part of the osi layers system. this web page explains the osi model and its layers with examples of attacks and mitigation. Data Link Layer Attacks.
From slidetodoc.com
Detecting and Responding to Data Link Layer Attacks Data Link Layer Attacks It covers physical layer wiretapping, data link layer vlan hopping, and network layer ping sweep attacks. The main attacks that occur at layer 2 include: layer 2 attacks refer to attacks that occur at the data link layer (layer 2) of the osi model. this web page explains the osi model and its layers with examples of attacks. Data Link Layer Attacks.
From www.infosectrain.com
Common Security Attacks in the OSI Layer Model Data Link Layer Attacks the data link layer dictates how data is allowed to travel between physically connected points. It covers physical layer wiretapping, data link layer vlan hopping, and network layer ping sweep attacks. layer 2 attacks refer to attacks that occur at the data link layer (layer 2) of the osi model. this web page explains the osi model. Data Link Layer Attacks.
From www.slideserve.com
PPT Detecting and Responding to Data Link Layer Attacks With Scapy Data Link Layer Attacks the data link layer dictates how data is allowed to travel between physically connected points. Learn how to secure this part of the osi layers system. The main attacks that occur at layer 2 include: It covers physical layer wiretapping, data link layer vlan hopping, and network layer ping sweep attacks. this web page explains the osi model. Data Link Layer Attacks.
From www.researchgate.net
Analysis of attacks in the Data Link Layer Download Scientific Diagram Data Link Layer Attacks The main attacks that occur at layer 2 include: Learn how to secure this part of the osi layers system. It covers physical layer wiretapping, data link layer vlan hopping, and network layer ping sweep attacks. this web page explains the osi model and its layers with examples of attacks and mitigation strategies. layer 2 attacks refer to. Data Link Layer Attacks.
From www.pinterest.com
The OSI Model Explained in Easy Steps Data Link Layer Attacks Learn how to secure this part of the osi layers system. It covers physical layer wiretapping, data link layer vlan hopping, and network layer ping sweep attacks. The main attacks that occur at layer 2 include: layer 2 attacks refer to attacks that occur at the data link layer (layer 2) of the osi model. the data link. Data Link Layer Attacks.
From www.slideserve.com
PPT Detecting and Responding to Data Link Layer Attacks With Scapy Data Link Layer Attacks the data link layer dictates how data is allowed to travel between physically connected points. The main attacks that occur at layer 2 include: this web page explains the osi model and its layers with examples of attacks and mitigation strategies. Learn how to secure this part of the osi layers system. layer 2 attacks refer to. Data Link Layer Attacks.
From slidetodoc.com
Detecting and Responding to Data Link Layer Attacks Data Link Layer Attacks this web page explains the osi model and its layers with examples of attacks and mitigation strategies. Learn how to secure this part of the osi layers system. It covers physical layer wiretapping, data link layer vlan hopping, and network layer ping sweep attacks. layer 2 attacks refer to attacks that occur at the data link layer (layer. Data Link Layer Attacks.
From techscience.com
CMC Free FullText Wireless Sensor Security Issues on Data Link Data Link Layer Attacks It covers physical layer wiretapping, data link layer vlan hopping, and network layer ping sweep attacks. The main attacks that occur at layer 2 include: Learn how to secure this part of the osi layers system. this web page explains the osi model and its layers with examples of attacks and mitigation strategies. layer 2 attacks refer to. Data Link Layer Attacks.
From www.slideserve.com
PPT Detecting and Responding to Data Link Layer Attacks With Scapy Data Link Layer Attacks layer 2 attacks refer to attacks that occur at the data link layer (layer 2) of the osi model. Learn how to secure this part of the osi layers system. The main attacks that occur at layer 2 include: It covers physical layer wiretapping, data link layer vlan hopping, and network layer ping sweep attacks. the data link. Data Link Layer Attacks.
From heimdalsecurity.com
What Is a DDoS Attack? Distributed Denial of Service Data Link Layer Attacks layer 2 attacks refer to attacks that occur at the data link layer (layer 2) of the osi model. the data link layer dictates how data is allowed to travel between physically connected points. Learn how to secure this part of the osi layers system. It covers physical layer wiretapping, data link layer vlan hopping, and network layer. Data Link Layer Attacks.
From www.youtube.com
Sublayers of the Data Link Layer YouTube Data Link Layer Attacks Learn how to secure this part of the osi layers system. the data link layer dictates how data is allowed to travel between physically connected points. this web page explains the osi model and its layers with examples of attacks and mitigation strategies. It covers physical layer wiretapping, data link layer vlan hopping, and network layer ping sweep. Data Link Layer Attacks.
From slidetodoc.com
Detecting and Responding to Data Link Layer Attacks Data Link Layer Attacks this web page explains the osi model and its layers with examples of attacks and mitigation strategies. The main attacks that occur at layer 2 include: the data link layer dictates how data is allowed to travel between physically connected points. layer 2 attacks refer to attacks that occur at the data link layer (layer 2) of. Data Link Layer Attacks.
From www.researchgate.net
(PDF) Using a Fuzzy Logic Controller to Thwart Data Link Layer Attacks Data Link Layer Attacks Learn how to secure this part of the osi layers system. It covers physical layer wiretapping, data link layer vlan hopping, and network layer ping sweep attacks. the data link layer dictates how data is allowed to travel between physically connected points. layer 2 attacks refer to attacks that occur at the data link layer (layer 2) of. Data Link Layer Attacks.
From www.stackscale.com
OSI model 7 layers & common security attacks Stackscale Data Link Layer Attacks the data link layer dictates how data is allowed to travel between physically connected points. this web page explains the osi model and its layers with examples of attacks and mitigation strategies. It covers physical layer wiretapping, data link layer vlan hopping, and network layer ping sweep attacks. Learn how to secure this part of the osi layers. Data Link Layer Attacks.
From www.siemxpert.com
What is OSI Model & Its Definition? Data Link Layer Attacks The main attacks that occur at layer 2 include: layer 2 attacks refer to attacks that occur at the data link layer (layer 2) of the osi model. It covers physical layer wiretapping, data link layer vlan hopping, and network layer ping sweep attacks. the data link layer dictates how data is allowed to travel between physically connected. Data Link Layer Attacks.
From www.slideserve.com
PPT Detecting and Responding to Data Link Layer Attacks With Scapy Data Link Layer Attacks this web page explains the osi model and its layers with examples of attacks and mitigation strategies. It covers physical layer wiretapping, data link layer vlan hopping, and network layer ping sweep attacks. The main attacks that occur at layer 2 include: the data link layer dictates how data is allowed to travel between physically connected points. . Data Link Layer Attacks.
From www.hackercoolmagazine.com
DataLink layer attacks Hackercool Magazine Data Link Layer Attacks It covers physical layer wiretapping, data link layer vlan hopping, and network layer ping sweep attacks. this web page explains the osi model and its layers with examples of attacks and mitigation strategies. Learn how to secure this part of the osi layers system. the data link layer dictates how data is allowed to travel between physically connected. Data Link Layer Attacks.
From mungfali.com
OSI Model Table Data Link Layer Attacks this web page explains the osi model and its layers with examples of attacks and mitigation strategies. Learn how to secure this part of the osi layers system. The main attacks that occur at layer 2 include: the data link layer dictates how data is allowed to travel between physically connected points. layer 2 attacks refer to. Data Link Layer Attacks.
From www.slideserve.com
PPT Detecting and Responding to Data Link Layer Attacks With Scapy Data Link Layer Attacks The main attacks that occur at layer 2 include: this web page explains the osi model and its layers with examples of attacks and mitigation strategies. layer 2 attacks refer to attacks that occur at the data link layer (layer 2) of the osi model. It covers physical layer wiretapping, data link layer vlan hopping, and network layer. Data Link Layer Attacks.
From deepai.org
CANflict Exploiting Peripheral Conflicts for DataLink Layer Attacks Data Link Layer Attacks this web page explains the osi model and its layers with examples of attacks and mitigation strategies. Learn how to secure this part of the osi layers system. The main attacks that occur at layer 2 include: It covers physical layer wiretapping, data link layer vlan hopping, and network layer ping sweep attacks. layer 2 attacks refer to. Data Link Layer Attacks.
From adroitacademy.com
What is the function of the Data Link layer Blog Adroit Information Data Link Layer Attacks this web page explains the osi model and its layers with examples of attacks and mitigation strategies. The main attacks that occur at layer 2 include: the data link layer dictates how data is allowed to travel between physically connected points. layer 2 attacks refer to attacks that occur at the data link layer (layer 2) of. Data Link Layer Attacks.
From slidetodoc.com
Detecting and Responding to Data Link Layer Attacks Data Link Layer Attacks Learn how to secure this part of the osi layers system. this web page explains the osi model and its layers with examples of attacks and mitigation strategies. It covers physical layer wiretapping, data link layer vlan hopping, and network layer ping sweep attacks. layer 2 attacks refer to attacks that occur at the data link layer (layer. Data Link Layer Attacks.
From www.minima.global
DDoS attacks and blockchain Dec 15, 2021 Data Link Layer Attacks layer 2 attacks refer to attacks that occur at the data link layer (layer 2) of the osi model. The main attacks that occur at layer 2 include: the data link layer dictates how data is allowed to travel between physically connected points. this web page explains the osi model and its layers with examples of attacks. Data Link Layer Attacks.