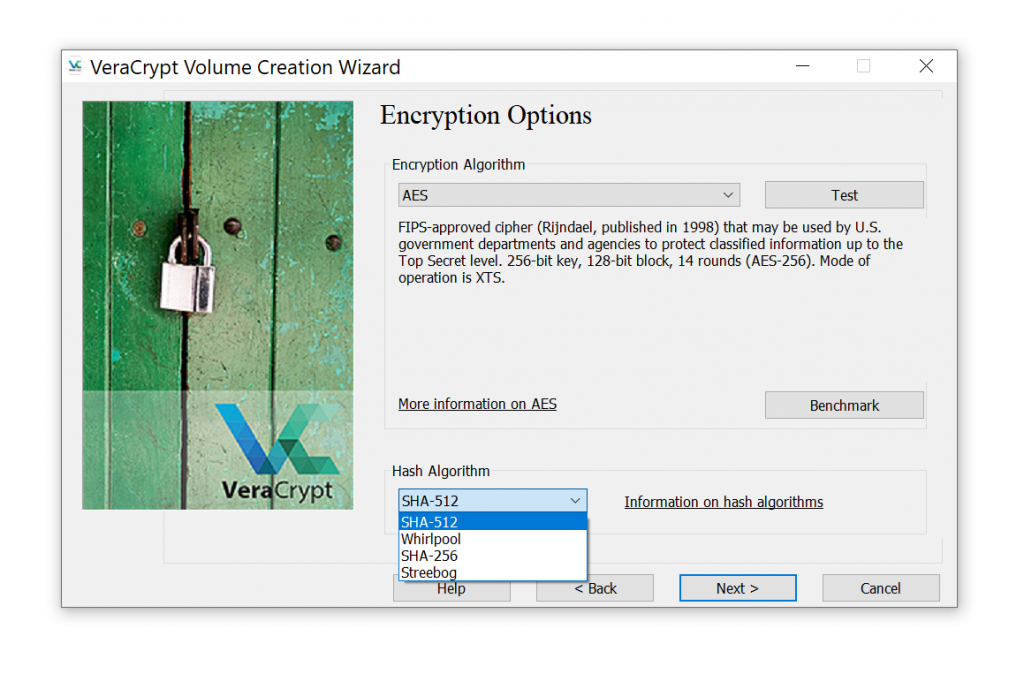
How To Find Veracrypt Container . Testcrypt is a first aid tool that you can use to recover your truecrypt/veracrypt volume. A veracrypt volume can reside in a file, which is also called container, in a partition or drive. All the files within the container are encrypted,. In this tutorial, we will choose the first option and create a veracrypt volume within a file. If a running pc was acquired with an authenticated session during the time the encrypted container is mounted, you may be. So ensure that you have access to a device with windows installed,. Veracrypt allows you to create a container inside a container. It is a windows tool. Into what veracrypt refers to as the “outer” container, you can place information that looks important, but in reality.
from blog.elcomsoft.com
So ensure that you have access to a device with windows installed,. A veracrypt volume can reside in a file, which is also called container, in a partition or drive. In this tutorial, we will choose the first option and create a veracrypt volume within a file. Into what veracrypt refers to as the “outer” container, you can place information that looks important, but in reality. It is a windows tool. All the files within the container are encrypted,. Testcrypt is a first aid tool that you can use to recover your truecrypt/veracrypt volume. Veracrypt allows you to create a container inside a container. If a running pc was acquired with an authenticated session during the time the encrypted container is mounted, you may be.
Breaking VeraCrypt containers blog
How To Find Veracrypt Container All the files within the container are encrypted,. Veracrypt allows you to create a container inside a container. Testcrypt is a first aid tool that you can use to recover your truecrypt/veracrypt volume. All the files within the container are encrypted,. In this tutorial, we will choose the first option and create a veracrypt volume within a file. A veracrypt volume can reside in a file, which is also called container, in a partition or drive. If a running pc was acquired with an authenticated session during the time the encrypted container is mounted, you may be. So ensure that you have access to a device with windows installed,. It is a windows tool. Into what veracrypt refers to as the “outer” container, you can place information that looks important, but in reality.
From help.inf.ed.ac.uk
Container encryption using Veracrypt Documentation How To Find Veracrypt Container Into what veracrypt refers to as the “outer” container, you can place information that looks important, but in reality. Testcrypt is a first aid tool that you can use to recover your truecrypt/veracrypt volume. In this tutorial, we will choose the first option and create a veracrypt volume within a file. Veracrypt allows you to create a container inside a. How To Find Veracrypt Container.
From www.safensecurecyber.com
Using Veracrypt to create secure containers How To Find Veracrypt Container A veracrypt volume can reside in a file, which is also called container, in a partition or drive. If a running pc was acquired with an authenticated session during the time the encrypted container is mounted, you may be. Testcrypt is a first aid tool that you can use to recover your truecrypt/veracrypt volume. Into what veracrypt refers to as. How To Find Veracrypt Container.
From blog.elcomsoft.com
Breaking VeraCrypt containers blog How To Find Veracrypt Container Testcrypt is a first aid tool that you can use to recover your truecrypt/veracrypt volume. All the files within the container are encrypted,. In this tutorial, we will choose the first option and create a veracrypt volume within a file. So ensure that you have access to a device with windows installed,. A veracrypt volume can reside in a file,. How To Find Veracrypt Container.
From www.makeuseof.com
How to Use VeraCrypt’s Advanced Features to Secure Important Files How To Find Veracrypt Container Veracrypt allows you to create a container inside a container. All the files within the container are encrypted,. Into what veracrypt refers to as the “outer” container, you can place information that looks important, but in reality. So ensure that you have access to a device with windows installed,. In this tutorial, we will choose the first option and create. How To Find Veracrypt Container.
From linuxhint.com
How to install and use veracrypt on Ubuntu 22.04 How To Find Veracrypt Container Into what veracrypt refers to as the “outer” container, you can place information that looks important, but in reality. All the files within the container are encrypted,. It is a windows tool. If a running pc was acquired with an authenticated session during the time the encrypted container is mounted, you may be. Veracrypt allows you to create a container. How To Find Veracrypt Container.
From pastethis.to
The ultimate guide for veracrypt PasteThis.To How To Find Veracrypt Container It is a windows tool. A veracrypt volume can reside in a file, which is also called container, in a partition or drive. So ensure that you have access to a device with windows installed,. All the files within the container are encrypted,. If a running pc was acquired with an authenticated session during the time the encrypted container is. How To Find Veracrypt Container.
From www.funkyspacemonkey.com
A Quick Look At VeraCrypt Encryption Tool How To Find Veracrypt Container All the files within the container are encrypted,. Veracrypt allows you to create a container inside a container. Testcrypt is a first aid tool that you can use to recover your truecrypt/veracrypt volume. It is a windows tool. A veracrypt volume can reside in a file, which is also called container, in a partition or drive. In this tutorial, we. How To Find Veracrypt Container.
From www.makeuseof.com
How to Use VeraCrypt’s Advanced Features to Secure Important Files How To Find Veracrypt Container All the files within the container are encrypted,. Into what veracrypt refers to as the “outer” container, you can place information that looks important, but in reality. Testcrypt is a first aid tool that you can use to recover your truecrypt/veracrypt volume. So ensure that you have access to a device with windows installed,. If a running pc was acquired. How To Find Veracrypt Container.
From www.youtube.com
Verschlüsselung Veracrypt Container einhängen und Daten verschlüsseln How To Find Veracrypt Container If a running pc was acquired with an authenticated session during the time the encrypted container is mounted, you may be. Veracrypt allows you to create a container inside a container. All the files within the container are encrypted,. Testcrypt is a first aid tool that you can use to recover your truecrypt/veracrypt volume. So ensure that you have access. How To Find Veracrypt Container.
From www.youtube.com
Veracrypt Tutorial Encrypt Your Files and Folders FAST YouTube How To Find Veracrypt Container A veracrypt volume can reside in a file, which is also called container, in a partition or drive. It is a windows tool. Testcrypt is a first aid tool that you can use to recover your truecrypt/veracrypt volume. If a running pc was acquired with an authenticated session during the time the encrypted container is mounted, you may be. Veracrypt. How To Find Veracrypt Container.
From www.youtube.com
Create VeraCrypt (portable) Container & Secure your Files! 💯 YouTube How To Find Veracrypt Container If a running pc was acquired with an authenticated session during the time the encrypted container is mounted, you may be. In this tutorial, we will choose the first option and create a veracrypt volume within a file. All the files within the container are encrypted,. Into what veracrypt refers to as the “outer” container, you can place information that. How To Find Veracrypt Container.
From www.makeuseof.com
How to Encrypt a Windows System Drive With VeraCrypt How To Find Veracrypt Container If a running pc was acquired with an authenticated session during the time the encrypted container is mounted, you may be. Into what veracrypt refers to as the “outer” container, you can place information that looks important, but in reality. Testcrypt is a first aid tool that you can use to recover your truecrypt/veracrypt volume. Veracrypt allows you to create. How To Find Veracrypt Container.
From blog.elcomsoft.com
Breaking VeraCrypt containers blog How To Find Veracrypt Container So ensure that you have access to a device with windows installed,. Testcrypt is a first aid tool that you can use to recover your truecrypt/veracrypt volume. A veracrypt volume can reside in a file, which is also called container, in a partition or drive. Veracrypt allows you to create a container inside a container. If a running pc was. How To Find Veracrypt Container.
From computing.help.inf.ed.ac.uk
Container encryption using Veracrypt Documentation How To Find Veracrypt Container It is a windows tool. If a running pc was acquired with an authenticated session during the time the encrypted container is mounted, you may be. Into what veracrypt refers to as the “outer” container, you can place information that looks important, but in reality. A veracrypt volume can reside in a file, which is also called container, in a. How To Find Veracrypt Container.
From www.codingblatt.de
VeraCrypt Erstellung eines verschlüsselten Containers codingblatt.de How To Find Veracrypt Container If a running pc was acquired with an authenticated session during the time the encrypted container is mounted, you may be. Testcrypt is a first aid tool that you can use to recover your truecrypt/veracrypt volume. So ensure that you have access to a device with windows installed,. Veracrypt allows you to create a container inside a container. A veracrypt. How To Find Veracrypt Container.
From www.makeuseof.com
How to Encrypt a Windows System Drive With VeraCrypt How To Find Veracrypt Container All the files within the container are encrypted,. Testcrypt is a first aid tool that you can use to recover your truecrypt/veracrypt volume. Into what veracrypt refers to as the “outer” container, you can place information that looks important, but in reality. A veracrypt volume can reside in a file, which is also called container, in a partition or drive.. How To Find Veracrypt Container.
From govcracker.com
VeraHunter GovCracker Decrypta Technologies How To Find Veracrypt Container So ensure that you have access to a device with windows installed,. It is a windows tool. A veracrypt volume can reside in a file, which is also called container, in a partition or drive. Veracrypt allows you to create a container inside a container. In this tutorial, we will choose the first option and create a veracrypt volume within. How To Find Veracrypt Container.
From proprivacy.com
VeraCrypt & howto basics How To Find Veracrypt Container If a running pc was acquired with an authenticated session during the time the encrypted container is mounted, you may be. A veracrypt volume can reside in a file, which is also called container, in a partition or drive. Testcrypt is a first aid tool that you can use to recover your truecrypt/veracrypt volume. So ensure that you have access. How To Find Veracrypt Container.
From www.youtube.com
OSTIF Guide How to Use VeraCrypt Containers to Secure Your Data YouTube How To Find Veracrypt Container Testcrypt is a first aid tool that you can use to recover your truecrypt/veracrypt volume. If a running pc was acquired with an authenticated session during the time the encrypted container is mounted, you may be. All the files within the container are encrypted,. In this tutorial, we will choose the first option and create a veracrypt volume within a. How To Find Veracrypt Container.
From www.youtube.com
Extend VeraCrypt Container Size YouTube How To Find Veracrypt Container In this tutorial, we will choose the first option and create a veracrypt volume within a file. It is a windows tool. Testcrypt is a first aid tool that you can use to recover your truecrypt/veracrypt volume. All the files within the container are encrypted,. A veracrypt volume can reside in a file, which is also called container, in a. How To Find Veracrypt Container.
From itslinuxfoss.com
How to Install and Use VeraCrypt on Ubuntu 22.04 Its Linux FOSS How To Find Veracrypt Container If a running pc was acquired with an authenticated session during the time the encrypted container is mounted, you may be. All the files within the container are encrypted,. So ensure that you have access to a device with windows installed,. In this tutorial, we will choose the first option and create a veracrypt volume within a file. Veracrypt allows. How To Find Veracrypt Container.
From blog.sucuri.net
Using a VeraCrypt File Container to Encrypt Local site Files How To Find Veracrypt Container A veracrypt volume can reside in a file, which is also called container, in a partition or drive. Testcrypt is a first aid tool that you can use to recover your truecrypt/veracrypt volume. In this tutorial, we will choose the first option and create a veracrypt volume within a file. So ensure that you have access to a device with. How To Find Veracrypt Container.
From devsday.ru
How to install and use veracrypt on Ubuntu 22.04 DevsDay.ru How To Find Veracrypt Container Testcrypt is a first aid tool that you can use to recover your truecrypt/veracrypt volume. Veracrypt allows you to create a container inside a container. So ensure that you have access to a device with windows installed,. All the files within the container are encrypted,. If a running pc was acquired with an authenticated session during the time the encrypted. How To Find Veracrypt Container.
From www.ghacks.net
Installing VeraCrypt in GNU/Linux gHacks Tech News How To Find Veracrypt Container A veracrypt volume can reside in a file, which is also called container, in a partition or drive. In this tutorial, we will choose the first option and create a veracrypt volume within a file. So ensure that you have access to a device with windows installed,. Testcrypt is a first aid tool that you can use to recover your. How To Find Veracrypt Container.
From linuxhint.com
How to install and use veracrypt on Ubuntu 22.04 How To Find Veracrypt Container Veracrypt allows you to create a container inside a container. Into what veracrypt refers to as the “outer” container, you can place information that looks important, but in reality. So ensure that you have access to a device with windows installed,. Testcrypt is a first aid tool that you can use to recover your truecrypt/veracrypt volume. A veracrypt volume can. How To Find Veracrypt Container.
From www.youtube.com
Using VeraCrypt to create Encrypted Containers Windows Tutorial YouTube How To Find Veracrypt Container If a running pc was acquired with an authenticated session during the time the encrypted container is mounted, you may be. It is a windows tool. All the files within the container are encrypted,. A veracrypt volume can reside in a file, which is also called container, in a partition or drive. Into what veracrypt refers to as the “outer”. How To Find Veracrypt Container.
From www.youtube.com
Create And Open Hidden Veracrypt Container in AndroidOpen veracrypt How To Find Veracrypt Container In this tutorial, we will choose the first option and create a veracrypt volume within a file. Testcrypt is a first aid tool that you can use to recover your truecrypt/veracrypt volume. Veracrypt allows you to create a container inside a container. Into what veracrypt refers to as the “outer” container, you can place information that looks important, but in. How To Find Veracrypt Container.
From www.youtube.com
How to Open Encrypted Container (Veracrypt) YouTube How To Find Veracrypt Container Into what veracrypt refers to as the “outer” container, you can place information that looks important, but in reality. Veracrypt allows you to create a container inside a container. If a running pc was acquired with an authenticated session during the time the encrypted container is mounted, you may be. It is a windows tool. All the files within the. How To Find Veracrypt Container.
From www.youtube.com
VeraCrypt How To Move Encrypted Containers Google Drive YouTube How To Find Veracrypt Container So ensure that you have access to a device with windows installed,. Into what veracrypt refers to as the “outer” container, you can place information that looks important, but in reality. All the files within the container are encrypted,. If a running pc was acquired with an authenticated session during the time the encrypted container is mounted, you may be.. How To Find Veracrypt Container.
From averagelinuxuser.com
VeraCrypt 4 ways to encrypt a flash drive in Linux Average Linux User How To Find Veracrypt Container Veracrypt allows you to create a container inside a container. All the files within the container are encrypted,. Into what veracrypt refers to as the “outer” container, you can place information that looks important, but in reality. So ensure that you have access to a device with windows installed,. In this tutorial, we will choose the first option and create. How To Find Veracrypt Container.
From www.ghacks.net
Installing VeraCrypt in GNU/Linux gHacks Tech News How To Find Veracrypt Container It is a windows tool. Into what veracrypt refers to as the “outer” container, you can place information that looks important, but in reality. All the files within the container are encrypted,. Veracrypt allows you to create a container inside a container. So ensure that you have access to a device with windows installed,. Testcrypt is a first aid tool. How To Find Veracrypt Container.
From freecourseherounlocks.net
How to Create and Use a VeraCrypt Container How To Find Veracrypt Container Veracrypt allows you to create a container inside a container. All the files within the container are encrypted,. In this tutorial, we will choose the first option and create a veracrypt volume within a file. It is a windows tool. So ensure that you have access to a device with windows installed,. Into what veracrypt refers to as the “outer”. How To Find Veracrypt Container.
From freedom.press
Encryption toolkit for media makers A VeraCrypt guide How To Find Veracrypt Container So ensure that you have access to a device with windows installed,. If a running pc was acquired with an authenticated session during the time the encrypted container is mounted, you may be. Testcrypt is a first aid tool that you can use to recover your truecrypt/veracrypt volume. Into what veracrypt refers to as the “outer” container, you can place. How To Find Veracrypt Container.
From www.purdue.edu
Guidance Document VeraCrypt Installation and Use Office of Research How To Find Veracrypt Container Testcrypt is a first aid tool that you can use to recover your truecrypt/veracrypt volume. Veracrypt allows you to create a container inside a container. All the files within the container are encrypted,. In this tutorial, we will choose the first option and create a veracrypt volume within a file. So ensure that you have access to a device with. How To Find Veracrypt Container.
From anishmandal.in
Beginner Guide to VeraCrypt data encryption Free OpenSource tool How To Find Veracrypt Container All the files within the container are encrypted,. If a running pc was acquired with an authenticated session during the time the encrypted container is mounted, you may be. In this tutorial, we will choose the first option and create a veracrypt volume within a file. It is a windows tool. Into what veracrypt refers to as the “outer” container,. How To Find Veracrypt Container.