Double Tag Vlan . double tagging attacks occur when threat actors add and modify tags on the ethernet frame. This approach enables the sending of packets through any vlan as the native untagged vlan on the trunk and takes advantage of several switches that process tags. There are two different methods to accomplish this: This type of attack takes advantage of the way that hardware on. This is when an information packet erroneously receives two or more vlan tags. vlan hopping is an attack where the attacker is able to send traffic from one vlan into another. It occurs when a single packet travels through a network and goes through multiple tagging. the basic concept behind all vlan hopping attacks is for an attacking host on a vlan to gain access to traffic on other vlans that.
from www.giga.de
It occurs when a single packet travels through a network and goes through multiple tagging. This approach enables the sending of packets through any vlan as the native untagged vlan on the trunk and takes advantage of several switches that process tags. This is when an information packet erroneously receives two or more vlan tags. vlan hopping is an attack where the attacker is able to send traffic from one vlan into another. the basic concept behind all vlan hopping attacks is for an attacking host on a vlan to gain access to traffic on other vlans that. double tagging attacks occur when threat actors add and modify tags on the ethernet frame. There are two different methods to accomplish this: This type of attack takes advantage of the way that hardware on.
VLAN was ist das? Und wie funktioniert es?
Double Tag Vlan This type of attack takes advantage of the way that hardware on. This is when an information packet erroneously receives two or more vlan tags. vlan hopping is an attack where the attacker is able to send traffic from one vlan into another. the basic concept behind all vlan hopping attacks is for an attacking host on a vlan to gain access to traffic on other vlans that. There are two different methods to accomplish this: This approach enables the sending of packets through any vlan as the native untagged vlan on the trunk and takes advantage of several switches that process tags. It occurs when a single packet travels through a network and goes through multiple tagging. This type of attack takes advantage of the way that hardware on. double tagging attacks occur when threat actors add and modify tags on the ethernet frame.
From www.ccdtt.com
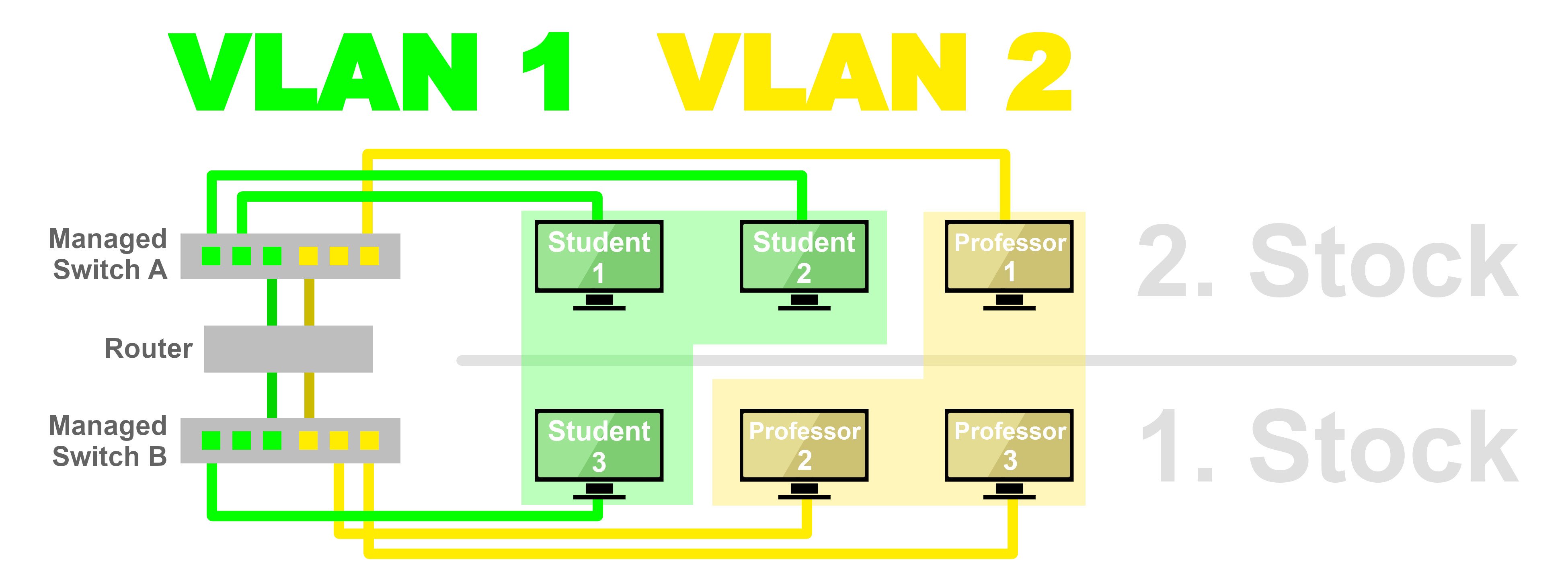
Vlan Hopping, Double Tagging, and STP Attacks CCDTT Security Double Tag Vlan the basic concept behind all vlan hopping attacks is for an attacking host on a vlan to gain access to traffic on other vlans that. double tagging attacks occur when threat actors add and modify tags on the ethernet frame. This approach enables the sending of packets through any vlan as the native untagged vlan on the trunk. Double Tag Vlan.
From papehane.blogspot.com
VLAN HOPPING ATTACK Double Tag Vlan It occurs when a single packet travels through a network and goes through multiple tagging. double tagging attacks occur when threat actors add and modify tags on the ethernet frame. This type of attack takes advantage of the way that hardware on. There are two different methods to accomplish this: the basic concept behind all vlan hopping attacks. Double Tag Vlan.
From www.slideserve.com
PPT Chapter 3 Implementing VLAN Security PowerPoint Presentation Double Tag Vlan It occurs when a single packet travels through a network and goes through multiple tagging. the basic concept behind all vlan hopping attacks is for an attacking host on a vlan to gain access to traffic on other vlans that. vlan hopping is an attack where the attacker is able to send traffic from one vlan into another.. Double Tag Vlan.
From powercampus.de
VLANs und VLANTagging PowerCampus 01 Double Tag Vlan double tagging attacks occur when threat actors add and modify tags on the ethernet frame. This is when an information packet erroneously receives two or more vlan tags. vlan hopping is an attack where the attacker is able to send traffic from one vlan into another. the basic concept behind all vlan hopping attacks is for an. Double Tag Vlan.
From www.slideserve.com
PPT FineGrained VLAN Labeling drafteastlaketrillrbridgefine Double Tag Vlan double tagging attacks occur when threat actors add and modify tags on the ethernet frame. vlan hopping is an attack where the attacker is able to send traffic from one vlan into another. It occurs when a single packet travels through a network and goes through multiple tagging. There are two different methods to accomplish this: This type. Double Tag Vlan.
From ccna-200-301.online
LAN Attacks » CCNA 200301 Double Tag Vlan the basic concept behind all vlan hopping attacks is for an attacking host on a vlan to gain access to traffic on other vlans that. This type of attack takes advantage of the way that hardware on. vlan hopping is an attack where the attacker is able to send traffic from one vlan into another. double tagging. Double Tag Vlan.
From notsosecure.com
Exploiting VLAN Double Tagging NotSoSecure Double Tag Vlan This is when an information packet erroneously receives two or more vlan tags. This type of attack takes advantage of the way that hardware on. vlan hopping is an attack where the attacker is able to send traffic from one vlan into another. There are two different methods to accomplish this: It occurs when a single packet travels through. Double Tag Vlan.
From ccna-200-301.online
LAN Attacks » CCNA 200301 Double Tag Vlan the basic concept behind all vlan hopping attacks is for an attacking host on a vlan to gain access to traffic on other vlans that. double tagging attacks occur when threat actors add and modify tags on the ethernet frame. This is when an information packet erroneously receives two or more vlan tags. It occurs when a single. Double Tag Vlan.
From www.youtube.com
VLAN Double Tagging Prevention YouTube Double Tag Vlan It occurs when a single packet travels through a network and goes through multiple tagging. This is when an information packet erroneously receives two or more vlan tags. vlan hopping is an attack where the attacker is able to send traffic from one vlan into another. double tagging attacks occur when threat actors add and modify tags on. Double Tag Vlan.
From www.youtube.com
Double Tagging VLAN Hopping Attack Between Two Virtual Networks Double Tag Vlan This type of attack takes advantage of the way that hardware on. the basic concept behind all vlan hopping attacks is for an attacking host on a vlan to gain access to traffic on other vlans that. vlan hopping is an attack where the attacker is able to send traffic from one vlan into another. There are two. Double Tag Vlan.
From www.networkingsignal.com
VLAN Vs VRF Key Differences Double Tag Vlan double tagging attacks occur when threat actors add and modify tags on the ethernet frame. This type of attack takes advantage of the way that hardware on. It occurs when a single packet travels through a network and goes through multiple tagging. the basic concept behind all vlan hopping attacks is for an attacking host on a vlan. Double Tag Vlan.
From sid-500.com
Cyber Security VLAN Double Tagging (Hopping) Attacks explained SID Double Tag Vlan It occurs when a single packet travels through a network and goes through multiple tagging. There are two different methods to accomplish this: This approach enables the sending of packets through any vlan as the native untagged vlan on the trunk and takes advantage of several switches that process tags. This is when an information packet erroneously receives two or. Double Tag Vlan.
From www.myshared.ru
Презентация на тему "MAD00558_jv". Скачать бесплатно и без регистрации. Double Tag Vlan double tagging attacks occur when threat actors add and modify tags on the ethernet frame. It occurs when a single packet travels through a network and goes through multiple tagging. vlan hopping is an attack where the attacker is able to send traffic from one vlan into another. This approach enables the sending of packets through any vlan. Double Tag Vlan.
From www.netme.co.il
VLAN Hopping Attack NetMe Double Tag Vlan double tagging attacks occur when threat actors add and modify tags on the ethernet frame. This is when an information packet erroneously receives two or more vlan tags. There are two different methods to accomplish this: This type of attack takes advantage of the way that hardware on. the basic concept behind all vlan hopping attacks is for. Double Tag Vlan.
From www.slideserve.com
PPT Cisco Security PowerPoint Presentation, free download ID1638167 Double Tag Vlan the basic concept behind all vlan hopping attacks is for an attacking host on a vlan to gain access to traffic on other vlans that. This is when an information packet erroneously receives two or more vlan tags. This type of attack takes advantage of the way that hardware on. vlan hopping is an attack where the attacker. Double Tag Vlan.
From notsosecure.com
Exploiting VLAN Double Tagging NotSoSecure Double Tag Vlan double tagging attacks occur when threat actors add and modify tags on the ethernet frame. This approach enables the sending of packets through any vlan as the native untagged vlan on the trunk and takes advantage of several switches that process tags. vlan hopping is an attack where the attacker is able to send traffic from one vlan. Double Tag Vlan.
From www.slideserve.com
PPT Securing Layer 2 Access PowerPoint Presentation, free download Double Tag Vlan This is when an information packet erroneously receives two or more vlan tags. This approach enables the sending of packets through any vlan as the native untagged vlan on the trunk and takes advantage of several switches that process tags. It occurs when a single packet travels through a network and goes through multiple tagging. the basic concept behind. Double Tag Vlan.
From www.youtube.com
Vlan Hopping, Double Tagging, and STP Attacks CCNA Security YouTube Double Tag Vlan double tagging attacks occur when threat actors add and modify tags on the ethernet frame. There are two different methods to accomplish this: This is when an information packet erroneously receives two or more vlan tags. It occurs when a single packet travels through a network and goes through multiple tagging. This approach enables the sending of packets through. Double Tag Vlan.
From www.youtube.com
GNS3 Talks Ostinato Packet Generator double tag 802.1Q frames for Double Tag Vlan vlan hopping is an attack where the attacker is able to send traffic from one vlan into another. This is when an information packet erroneously receives two or more vlan tags. the basic concept behind all vlan hopping attacks is for an attacking host on a vlan to gain access to traffic on other vlans that. There are. Double Tag Vlan.
From www.researchgate.net
(PDF) VLAN Double Tagging Attack Double Tag Vlan double tagging attacks occur when threat actors add and modify tags on the ethernet frame. There are two different methods to accomplish this: This type of attack takes advantage of the way that hardware on. This is when an information packet erroneously receives two or more vlan tags. This approach enables the sending of packets through any vlan as. Double Tag Vlan.
From www.youtube.com
Describe VLAN hopping, VLAN Double Tagging and STP Attacks YouTube Double Tag Vlan the basic concept behind all vlan hopping attacks is for an attacking host on a vlan to gain access to traffic on other vlans that. double tagging attacks occur when threat actors add and modify tags on the ethernet frame. It occurs when a single packet travels through a network and goes through multiple tagging. This is when. Double Tag Vlan.
From www.scribd.com
VLAN Double Tagging Attack PDF Transmission Control Protocol Double Tag Vlan There are two different methods to accomplish this: the basic concept behind all vlan hopping attacks is for an attacking host on a vlan to gain access to traffic on other vlans that. This approach enables the sending of packets through any vlan as the native untagged vlan on the trunk and takes advantage of several switches that process. Double Tag Vlan.
From www.youtube.com
🔵 VLAN DOUBLE TAGGING O ATAQUE (Parte 1) YouTube Double Tag Vlan the basic concept behind all vlan hopping attacks is for an attacking host on a vlan to gain access to traffic on other vlans that. This type of attack takes advantage of the way that hardware on. vlan hopping is an attack where the attacker is able to send traffic from one vlan into another. There are two. Double Tag Vlan.
From ccna-200-301.online
LAN Attacks » CCNA 200301 Double Tag Vlan This is when an information packet erroneously receives two or more vlan tags. vlan hopping is an attack where the attacker is able to send traffic from one vlan into another. the basic concept behind all vlan hopping attacks is for an attacking host on a vlan to gain access to traffic on other vlans that. This type. Double Tag Vlan.
From www.claranet.com
Exploiting VLAN Double Tagging Cyber Security Double Tag Vlan This approach enables the sending of packets through any vlan as the native untagged vlan on the trunk and takes advantage of several switches that process tags. vlan hopping is an attack where the attacker is able to send traffic from one vlan into another. This type of attack takes advantage of the way that hardware on. the. Double Tag Vlan.
From www.youtube.com
ISP networks video 13 & Stacking VLANs Double Tagging Double Tag Vlan It occurs when a single packet travels through a network and goes through multiple tagging. This approach enables the sending of packets through any vlan as the native untagged vlan on the trunk and takes advantage of several switches that process tags. This is when an information packet erroneously receives two or more vlan tags. There are two different methods. Double Tag Vlan.
From networkengineering.stackexchange.com
cisco VLAN mapping on double to singletagged interface Network Double Tag Vlan There are two different methods to accomplish this: This type of attack takes advantage of the way that hardware on. the basic concept behind all vlan hopping attacks is for an attacking host on a vlan to gain access to traffic on other vlans that. vlan hopping is an attack where the attacker is able to send traffic. Double Tag Vlan.
From www.giga.de
VLAN was ist das? Und wie funktioniert es? Double Tag Vlan This type of attack takes advantage of the way that hardware on. vlan hopping is an attack where the attacker is able to send traffic from one vlan into another. There are two different methods to accomplish this: the basic concept behind all vlan hopping attacks is for an attacking host on a vlan to gain access to. Double Tag Vlan.
From www.slideserve.com
PPT Chapter 3 Implementing VLAN Security PowerPoint Presentation Double Tag Vlan This approach enables the sending of packets through any vlan as the native untagged vlan on the trunk and takes advantage of several switches that process tags. the basic concept behind all vlan hopping attacks is for an attacking host on a vlan to gain access to traffic on other vlans that. This type of attack takes advantage of. Double Tag Vlan.
From notsosecure.com
Exploiting VLAN Double Tagging NotSoSecure Double Tag Vlan It occurs when a single packet travels through a network and goes through multiple tagging. the basic concept behind all vlan hopping attacks is for an attacking host on a vlan to gain access to traffic on other vlans that. There are two different methods to accomplish this: This is when an information packet erroneously receives two or more. Double Tag Vlan.
From www.claranet.com
Exploiting VLAN Double Tagging Cyber Security Double Tag Vlan There are two different methods to accomplish this: the basic concept behind all vlan hopping attacks is for an attacking host on a vlan to gain access to traffic on other vlans that. This type of attack takes advantage of the way that hardware on. double tagging attacks occur when threat actors add and modify tags on the. Double Tag Vlan.
From www.slideserve.com
PPT AT8948 Switch for Service Providers Architecture and Switching Double Tag Vlan This type of attack takes advantage of the way that hardware on. This approach enables the sending of packets through any vlan as the native untagged vlan on the trunk and takes advantage of several switches that process tags. the basic concept behind all vlan hopping attacks is for an attacking host on a vlan to gain access to. Double Tag Vlan.
From www.youtube.com
VLAN Hopping Double Tagging Attack YouTube Double Tag Vlan It occurs when a single packet travels through a network and goes through multiple tagging. This is when an information packet erroneously receives two or more vlan tags. vlan hopping is an attack where the attacker is able to send traffic from one vlan into another. There are two different methods to accomplish this: This approach enables the sending. Double Tag Vlan.
From sid-500.com
VLAN Double Tagging Attacks Double Tag Vlan double tagging attacks occur when threat actors add and modify tags on the ethernet frame. vlan hopping is an attack where the attacker is able to send traffic from one vlan into another. This approach enables the sending of packets through any vlan as the native untagged vlan on the trunk and takes advantage of several switches that. Double Tag Vlan.
From www.slideserve.com
PPT Minimizing Service Loss and Data Theft PowerPoint Presentation Double Tag Vlan There are two different methods to accomplish this: vlan hopping is an attack where the attacker is able to send traffic from one vlan into another. double tagging attacks occur when threat actors add and modify tags on the ethernet frame. This approach enables the sending of packets through any vlan as the native untagged vlan on the. Double Tag Vlan.