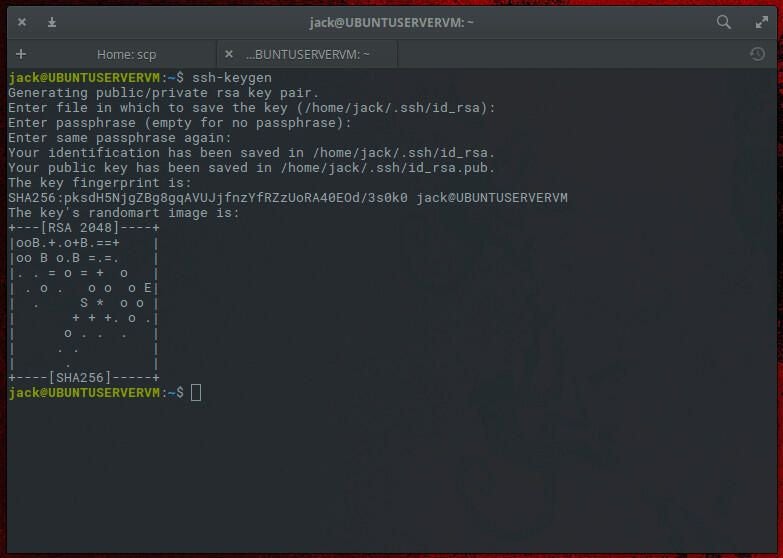
How To Use Secure Copy With Ssh Key Authentication . The scp (secure copy) command uses ssh to transfer data from one host to another and uses ssh’s same authentication and security. For security reasons, scp does not allow passwords to be included directly in the command. It uses the same authentication. The basic idea is to create a key pair on the. This tutorial explains how to use this popular command with numerous. To avoid this, or to automate file copying in scripts, public key authentication is usually used. The scp command or secure copy allows the secure transferring of files between the local host and the remote host or between two remote hosts. Instead, you should use ssh keys. Scp or secure copy securely transfers files between two hosts over the network using the ssh protocol. When transferring data with scp, both the files and. Scp uses the ssh protocol for encryption.
from www.techrepublic.com
For security reasons, scp does not allow passwords to be included directly in the command. To avoid this, or to automate file copying in scripts, public key authentication is usually used. When transferring data with scp, both the files and. The scp command or secure copy allows the secure transferring of files between the local host and the remote host or between two remote hosts. The scp (secure copy) command uses ssh to transfer data from one host to another and uses ssh’s same authentication and security. It uses the same authentication. Instead, you should use ssh keys. Scp or secure copy securely transfers files between two hosts over the network using the ssh protocol. This tutorial explains how to use this popular command with numerous. The basic idea is to create a key pair on the.
How to use SCP (secure copy) with ssh key authentication
How To Use Secure Copy With Ssh Key Authentication Scp uses the ssh protocol for encryption. To avoid this, or to automate file copying in scripts, public key authentication is usually used. The scp command or secure copy allows the secure transferring of files between the local host and the remote host or between two remote hosts. It uses the same authentication. Scp or secure copy securely transfers files between two hosts over the network using the ssh protocol. The scp (secure copy) command uses ssh to transfer data from one host to another and uses ssh’s same authentication and security. This tutorial explains how to use this popular command with numerous. When transferring data with scp, both the files and. Scp uses the ssh protocol for encryption. The basic idea is to create a key pair on the. Instead, you should use ssh keys. For security reasons, scp does not allow passwords to be included directly in the command.
From upcloud.com
How to use SSH keys for authentication UpCloud How To Use Secure Copy With Ssh Key Authentication The basic idea is to create a key pair on the. Instead, you should use ssh keys. The scp command or secure copy allows the secure transferring of files between the local host and the remote host or between two remote hosts. When transferring data with scp, both the files and. This tutorial explains how to use this popular command. How To Use Secure Copy With Ssh Key Authentication.
From www.youtube.com
PublicKey Authentication SecureCRT to OpenSSH YouTube How To Use Secure Copy With Ssh Key Authentication The basic idea is to create a key pair on the. Scp uses the ssh protocol for encryption. Scp or secure copy securely transfers files between two hosts over the network using the ssh protocol. This tutorial explains how to use this popular command with numerous. When transferring data with scp, both the files and. Instead, you should use ssh. How To Use Secure Copy With Ssh Key Authentication.
From www.learnitguide.net
How to Use YubiKey for Secure SSH Authentication How To Use Secure Copy With Ssh Key Authentication The scp command or secure copy allows the secure transferring of files between the local host and the remote host or between two remote hosts. For security reasons, scp does not allow passwords to be included directly in the command. The basic idea is to create a key pair on the. Scp uses the ssh protocol for encryption. The scp. How To Use Secure Copy With Ssh Key Authentication.
From www.vrogue.co
Macos How To Copy Ssh Key A Step By Step Guide vrogue.co How To Use Secure Copy With Ssh Key Authentication The scp (secure copy) command uses ssh to transfer data from one host to another and uses ssh’s same authentication and security. For security reasons, scp does not allow passwords to be included directly in the command. The scp command or secure copy allows the secure transferring of files between the local host and the remote host or between two. How To Use Secure Copy With Ssh Key Authentication.
From spectralops.io
The complete guide to SSH keys in GitLab Spectral How To Use Secure Copy With Ssh Key Authentication This tutorial explains how to use this popular command with numerous. The scp command or secure copy allows the secure transferring of files between the local host and the remote host or between two remote hosts. To avoid this, or to automate file copying in scripts, public key authentication is usually used. Scp uses the ssh protocol for encryption. The. How To Use Secure Copy With Ssh Key Authentication.
From upcloud.com
How to use SSH keys for authentication UpCloud How To Use Secure Copy With Ssh Key Authentication Instead, you should use ssh keys. It uses the same authentication. To avoid this, or to automate file copying in scripts, public key authentication is usually used. The basic idea is to create a key pair on the. Scp or secure copy securely transfers files between two hosts over the network using the ssh protocol. The scp command or secure. How To Use Secure Copy With Ssh Key Authentication.
From phoenixnap.com
How Does SFTP Work? with FTP} How To Use Secure Copy With Ssh Key Authentication The scp command or secure copy allows the secure transferring of files between the local host and the remote host or between two remote hosts. Scp uses the ssh protocol for encryption. For security reasons, scp does not allow passwords to be included directly in the command. When transferring data with scp, both the files and. It uses the same. How To Use Secure Copy With Ssh Key Authentication.
From www.stackscale.com
SSH protocol usage, versions and implementations How To Use Secure Copy With Ssh Key Authentication This tutorial explains how to use this popular command with numerous. Scp or secure copy securely transfers files between two hosts over the network using the ssh protocol. It uses the same authentication. To avoid this, or to automate file copying in scripts, public key authentication is usually used. The basic idea is to create a key pair on the.. How To Use Secure Copy With Ssh Key Authentication.
From www.sectigo.com
SSH Key Pair Explained How SSH Private & Public Keys Work Sectigo How To Use Secure Copy With Ssh Key Authentication To avoid this, or to automate file copying in scripts, public key authentication is usually used. It uses the same authentication. Scp uses the ssh protocol for encryption. The basic idea is to create a key pair on the. The scp (secure copy) command uses ssh to transfer data from one host to another and uses ssh’s same authentication and. How To Use Secure Copy With Ssh Key Authentication.
From www.geeksforgeeks.org
Linux SSH Server (sshd) Configuration and Security Options With How To Use Secure Copy With Ssh Key Authentication This tutorial explains how to use this popular command with numerous. Scp or secure copy securely transfers files between two hosts over the network using the ssh protocol. When transferring data with scp, both the files and. Instead, you should use ssh keys. The basic idea is to create a key pair on the. For security reasons, scp does not. How To Use Secure Copy With Ssh Key Authentication.
From blog.cpanel.com
Secure Your cPanel Server With SSH Keys And Public Key Cryptography How To Use Secure Copy With Ssh Key Authentication The scp (secure copy) command uses ssh to transfer data from one host to another and uses ssh’s same authentication and security. For security reasons, scp does not allow passwords to be included directly in the command. The basic idea is to create a key pair on the. The scp command or secure copy allows the secure transferring of files. How To Use Secure Copy With Ssh Key Authentication.
From p8t.net
SSH Keys All You Need to Know About Managing Them P8t How To Use Secure Copy With Ssh Key Authentication When transferring data with scp, both the files and. Instead, you should use ssh keys. This tutorial explains how to use this popular command with numerous. The basic idea is to create a key pair on the. The scp command or secure copy allows the secure transferring of files between the local host and the remote host or between two. How To Use Secure Copy With Ssh Key Authentication.
From www.vrogue.co
How To Use Ssh Keys For Authentication Tutorial Upclo vrogue.co How To Use Secure Copy With Ssh Key Authentication The scp (secure copy) command uses ssh to transfer data from one host to another and uses ssh’s same authentication and security. The basic idea is to create a key pair on the. Scp or secure copy securely transfers files between two hosts over the network using the ssh protocol. Instead, you should use ssh keys. Scp uses the ssh. How To Use Secure Copy With Ssh Key Authentication.
From www.hostinger.co.uk
SSH Tutorial What is SSH, Encryptions and Ports How To Use Secure Copy With Ssh Key Authentication The basic idea is to create a key pair on the. The scp (secure copy) command uses ssh to transfer data from one host to another and uses ssh’s same authentication and security. It uses the same authentication. Scp uses the ssh protocol for encryption. The scp command or secure copy allows the secure transferring of files between the local. How To Use Secure Copy With Ssh Key Authentication.
From www.padheye.com
ssh command in Linux with Examples How To Use Secure Copy With Ssh Key Authentication The scp (secure copy) command uses ssh to transfer data from one host to another and uses ssh’s same authentication and security. This tutorial explains how to use this popular command with numerous. To avoid this, or to automate file copying in scripts, public key authentication is usually used. The scp command or secure copy allows the secure transferring of. How To Use Secure Copy With Ssh Key Authentication.
From www.g2.com
How to Use SFTP to Safely and Quickly Send Files How To Use Secure Copy With Ssh Key Authentication When transferring data with scp, both the files and. Scp or secure copy securely transfers files between two hosts over the network using the ssh protocol. Scp uses the ssh protocol for encryption. The scp (secure copy) command uses ssh to transfer data from one host to another and uses ssh’s same authentication and security. This tutorial explains how to. How To Use Secure Copy With Ssh Key Authentication.
From topdev.vn
Hướng dẫn cài đặt SSH KEY cho server Linux TopDev How To Use Secure Copy With Ssh Key Authentication When transferring data with scp, both the files and. Scp uses the ssh protocol for encryption. The scp (secure copy) command uses ssh to transfer data from one host to another and uses ssh’s same authentication and security. The basic idea is to create a key pair on the. To avoid this, or to automate file copying in scripts, public. How To Use Secure Copy With Ssh Key Authentication.
From nhanvietluanvan.com
Macos How To Copy Ssh Key A StepByStep Guide How To Use Secure Copy With Ssh Key Authentication When transferring data with scp, both the files and. For security reasons, scp does not allow passwords to be included directly in the command. The basic idea is to create a key pair on the. To avoid this, or to automate file copying in scripts, public key authentication is usually used. Instead, you should use ssh keys. Scp uses the. How To Use Secure Copy With Ssh Key Authentication.
From www.ssh.com
SSH keys authenticate users and hosts in SSH for SSO & M2M access. How To Use Secure Copy With Ssh Key Authentication For security reasons, scp does not allow passwords to be included directly in the command. When transferring data with scp, both the files and. To avoid this, or to automate file copying in scripts, public key authentication is usually used. The scp command or secure copy allows the secure transferring of files between the local host and the remote host. How To Use Secure Copy With Ssh Key Authentication.
From upcloud.com
How to use SSH keys for authentication UpCloud How To Use Secure Copy With Ssh Key Authentication To avoid this, or to automate file copying in scripts, public key authentication is usually used. Scp or secure copy securely transfers files between two hosts over the network using the ssh protocol. This tutorial explains how to use this popular command with numerous. Scp uses the ssh protocol for encryption. It uses the same authentication. Instead, you should use. How To Use Secure Copy With Ssh Key Authentication.
From www.hotzxgirl.com
Setting Up Sftp Only Access With Ssh Key Authentication On Centos Hot How To Use Secure Copy With Ssh Key Authentication To avoid this, or to automate file copying in scripts, public key authentication is usually used. The scp command or secure copy allows the secure transferring of files between the local host and the remote host or between two remote hosts. Instead, you should use ssh keys. It uses the same authentication. Scp uses the ssh protocol for encryption. The. How To Use Secure Copy With Ssh Key Authentication.
From linuxhint.com
How to Set Up SSH Keys on Ubuntu 20.04 How To Use Secure Copy With Ssh Key Authentication The scp (secure copy) command uses ssh to transfer data from one host to another and uses ssh’s same authentication and security. Scp or secure copy securely transfers files between two hosts over the network using the ssh protocol. The scp command or secure copy allows the secure transferring of files between the local host and the remote host or. How To Use Secure Copy With Ssh Key Authentication.
From support.cerberusftp.com
Configuring a user for SSH Public Key Authentication Cerberus Support How To Use Secure Copy With Ssh Key Authentication It uses the same authentication. The scp (secure copy) command uses ssh to transfer data from one host to another and uses ssh’s same authentication and security. The basic idea is to create a key pair on the. Instead, you should use ssh keys. Scp uses the ssh protocol for encryption. The scp command or secure copy allows the secure. How To Use Secure Copy With Ssh Key Authentication.
From howtowiki91.blogspot.com
Howto Ssh Howto Techno How To Use Secure Copy With Ssh Key Authentication The basic idea is to create a key pair on the. The scp (secure copy) command uses ssh to transfer data from one host to another and uses ssh’s same authentication and security. Scp or secure copy securely transfers files between two hosts over the network using the ssh protocol. Scp uses the ssh protocol for encryption. To avoid this,. How To Use Secure Copy With Ssh Key Authentication.
From orcacore.com
Using SCP to Transfer Files with SSH keys Ubuntu OrcaCore How To Use Secure Copy With Ssh Key Authentication To avoid this, or to automate file copying in scripts, public key authentication is usually used. The scp (secure copy) command uses ssh to transfer data from one host to another and uses ssh’s same authentication and security. For security reasons, scp does not allow passwords to be included directly in the command. This tutorial explains how to use this. How To Use Secure Copy With Ssh Key Authentication.
From www.youtube.com
Setup SFTP server in Windows using OpenSSH with public key How To Use Secure Copy With Ssh Key Authentication Scp uses the ssh protocol for encryption. This tutorial explains how to use this popular command with numerous. To avoid this, or to automate file copying in scripts, public key authentication is usually used. The scp command or secure copy allows the secure transferring of files between the local host and the remote host or between two remote hosts. The. How To Use Secure Copy With Ssh Key Authentication.
From interworks.com
How to Enable SSH Commands in Windows InterWorks How To Use Secure Copy With Ssh Key Authentication It uses the same authentication. When transferring data with scp, both the files and. Scp uses the ssh protocol for encryption. This tutorial explains how to use this popular command with numerous. The scp (secure copy) command uses ssh to transfer data from one host to another and uses ssh’s same authentication and security. The basic idea is to create. How To Use Secure Copy With Ssh Key Authentication.
From uwm-cloudblog.net
Managing SSH Key Pairs UWMilwaukee Cloud Computing How To Use Secure Copy With Ssh Key Authentication This tutorial explains how to use this popular command with numerous. The scp command or secure copy allows the secure transferring of files between the local host and the remote host or between two remote hosts. Scp or secure copy securely transfers files between two hosts over the network using the ssh protocol. Scp uses the ssh protocol for encryption.. How To Use Secure Copy With Ssh Key Authentication.
From www.geeksforgeeks.org
How to use SSH to connect to a remote server in Linux ssh Command How To Use Secure Copy With Ssh Key Authentication The basic idea is to create a key pair on the. To avoid this, or to automate file copying in scripts, public key authentication is usually used. This tutorial explains how to use this popular command with numerous. Scp uses the ssh protocol for encryption. Scp or secure copy securely transfers files between two hosts over the network using the. How To Use Secure Copy With Ssh Key Authentication.
From www.geeksforgeeks.org
How To Generate SSH Key With sshkeygen In Linux? How To Use Secure Copy With Ssh Key Authentication Scp or secure copy securely transfers files between two hosts over the network using the ssh protocol. Scp uses the ssh protocol for encryption. The scp (secure copy) command uses ssh to transfer data from one host to another and uses ssh’s same authentication and security. The basic idea is to create a key pair on the. This tutorial explains. How To Use Secure Copy With Ssh Key Authentication.
From upcloud.com
How to use SSH keys for authentication UpCloud How To Use Secure Copy With Ssh Key Authentication For security reasons, scp does not allow passwords to be included directly in the command. Scp uses the ssh protocol for encryption. It uses the same authentication. The basic idea is to create a key pair on the. The scp command or secure copy allows the secure transferring of files between the local host and the remote host or between. How To Use Secure Copy With Ssh Key Authentication.
From www.techrepublic.com
How to use SCP (secure copy) with ssh key authentication How To Use Secure Copy With Ssh Key Authentication Instead, you should use ssh keys. This tutorial explains how to use this popular command with numerous. Scp or secure copy securely transfers files between two hosts over the network using the ssh protocol. For security reasons, scp does not allow passwords to be included directly in the command. The scp (secure copy) command uses ssh to transfer data from. How To Use Secure Copy With Ssh Key Authentication.
From cyber.vumetric.com
How to Create and Copy SSH Keys with 2 Simple Commands (+Video Tutorial How To Use Secure Copy With Ssh Key Authentication When transferring data with scp, both the files and. The scp command or secure copy allows the secure transferring of files between the local host and the remote host or between two remote hosts. For security reasons, scp does not allow passwords to be included directly in the command. Scp uses the ssh protocol for encryption. It uses the same. How To Use Secure Copy With Ssh Key Authentication.
From sebastien.saunier.me
GitHub public key authentication Sébastien Saunier How To Use Secure Copy With Ssh Key Authentication Scp or secure copy securely transfers files between two hosts over the network using the ssh protocol. The basic idea is to create a key pair on the. To avoid this, or to automate file copying in scripts, public key authentication is usually used. Scp uses the ssh protocol for encryption. Instead, you should use ssh keys. It uses the. How To Use Secure Copy With Ssh Key Authentication.
From www.pinterest.com
How to Configure SSH Passwordless Login Authentication on Linux using How To Use Secure Copy With Ssh Key Authentication Scp uses the ssh protocol for encryption. When transferring data with scp, both the files and. It uses the same authentication. The basic idea is to create a key pair on the. The scp (secure copy) command uses ssh to transfer data from one host to another and uses ssh’s same authentication and security. This tutorial explains how to use. How To Use Secure Copy With Ssh Key Authentication.