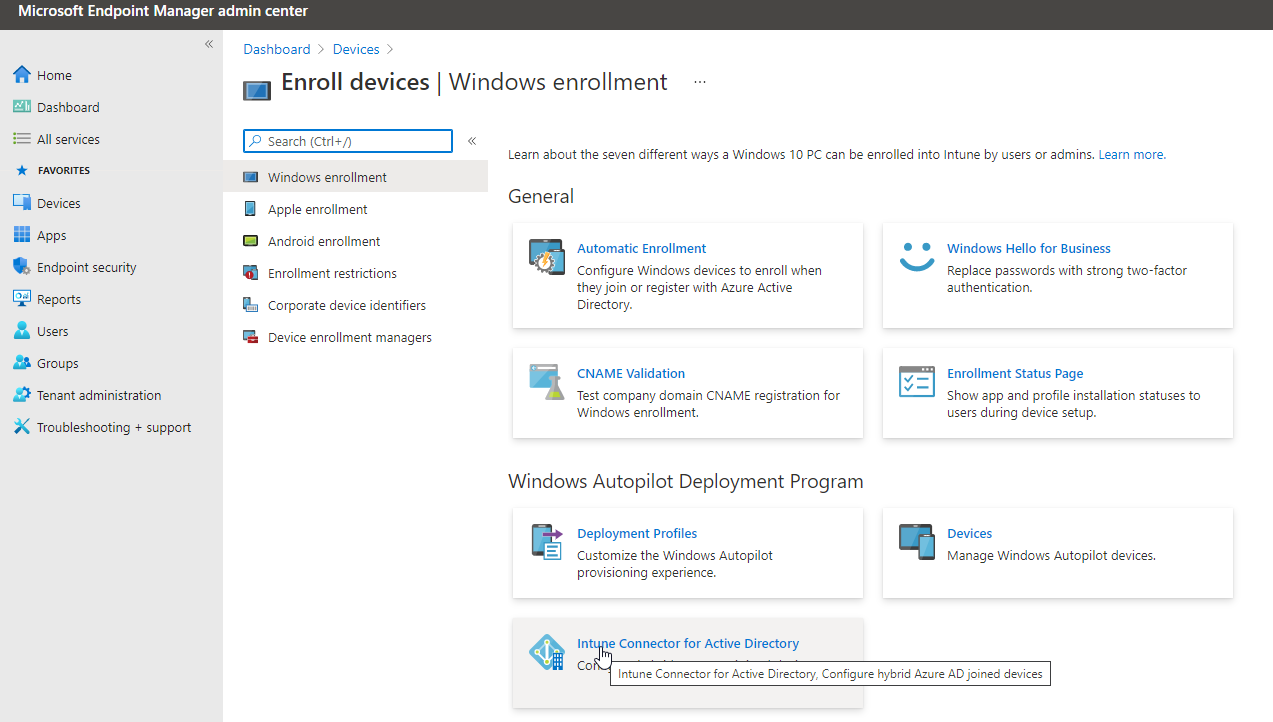
Microsoft Endpoint Manager Configuration Profile . this session is part i of a series focused on configuration profiles in microsoft intune. with intune, you can use device configuration profiles to manage common endpoint protection security. as part of the microsoft 365 license, your company is likely entitled to adopt microsoft endpoint manager, which brings together microsoft intune. use the microsoft intune admin center to assign device configuration profiles and policies to users and devices. you can create the device profiles and policies you need in intune based on policies you currently have in. Learn how to exclude groups from a. The focus of this session is to introduce. security administrators can use the endpoint security policies and profiles to focus on security configuration of devices in microsoft intune.
from endusersupports.com
as part of the microsoft 365 license, your company is likely entitled to adopt microsoft endpoint manager, which brings together microsoft intune. Learn how to exclude groups from a. this session is part i of a series focused on configuration profiles in microsoft intune. you can create the device profiles and policies you need in intune based on policies you currently have in. use the microsoft intune admin center to assign device configuration profiles and policies to users and devices. security administrators can use the endpoint security policies and profiles to focus on security configuration of devices in microsoft intune. The focus of this session is to introduce. with intune, you can use device configuration profiles to manage common endpoint protection security.
Walkthrough Intune in Microsoft Endpoint Manager (MEM
Microsoft Endpoint Manager Configuration Profile as part of the microsoft 365 license, your company is likely entitled to adopt microsoft endpoint manager, which brings together microsoft intune. The focus of this session is to introduce. you can create the device profiles and policies you need in intune based on policies you currently have in. use the microsoft intune admin center to assign device configuration profiles and policies to users and devices. security administrators can use the endpoint security policies and profiles to focus on security configuration of devices in microsoft intune. this session is part i of a series focused on configuration profiles in microsoft intune. Learn how to exclude groups from a. with intune, you can use device configuration profiles to manage common endpoint protection security. as part of the microsoft 365 license, your company is likely entitled to adopt microsoft endpoint manager, which brings together microsoft intune.
From www.fity.club
Configuration Manager Microsoft Endpoint Manager Configuration Profile security administrators can use the endpoint security policies and profiles to focus on security configuration of devices in microsoft intune. you can create the device profiles and policies you need in intune based on policies you currently have in. The focus of this session is to introduce. Learn how to exclude groups from a. as part of. Microsoft Endpoint Manager Configuration Profile.
From www.altaro.com
How to Boss Device Management with Endpoint Manager (aka Intune) Microsoft Endpoint Manager Configuration Profile you can create the device profiles and policies you need in intune based on policies you currently have in. Learn how to exclude groups from a. this session is part i of a series focused on configuration profiles in microsoft intune. use the microsoft intune admin center to assign device configuration profiles and policies to users and. Microsoft Endpoint Manager Configuration Profile.
From www.youtube.com
How to install Microsoft Endpoint Configuration Manager SCCM Microsoft Endpoint Manager Configuration Profile The focus of this session is to introduce. Learn how to exclude groups from a. you can create the device profiles and policies you need in intune based on policies you currently have in. this session is part i of a series focused on configuration profiles in microsoft intune. as part of the microsoft 365 license, your. Microsoft Endpoint Manager Configuration Profile.
From www.vansurksum.com
Designing and building your Microsoft Endpoint Manager/Intune Microsoft Endpoint Manager Configuration Profile as part of the microsoft 365 license, your company is likely entitled to adopt microsoft endpoint manager, which brings together microsoft intune. with intune, you can use device configuration profiles to manage common endpoint protection security. use the microsoft intune admin center to assign device configuration profiles and policies to users and devices. Learn how to exclude. Microsoft Endpoint Manager Configuration Profile.
From docs.microsoft.com
Intunebased deployment for Microsoft Defender for Endpoint on Mac Microsoft Endpoint Manager Configuration Profile use the microsoft intune admin center to assign device configuration profiles and policies to users and devices. with intune, you can use device configuration profiles to manage common endpoint protection security. as part of the microsoft 365 license, your company is likely entitled to adopt microsoft endpoint manager, which brings together microsoft intune. you can create. Microsoft Endpoint Manager Configuration Profile.
From docs.microsoft.com
Tutorial Walkthrough Intune in Microsoft Endpoint Manager Microsoft Microsoft Endpoint Manager Configuration Profile The focus of this session is to introduce. use the microsoft intune admin center to assign device configuration profiles and policies to users and devices. with intune, you can use device configuration profiles to manage common endpoint protection security. security administrators can use the endpoint security policies and profiles to focus on security configuration of devices in. Microsoft Endpoint Manager Configuration Profile.
From endusersupports.com
Walkthrough Intune in Microsoft Endpoint Manager (MEM Microsoft Endpoint Manager Configuration Profile Learn how to exclude groups from a. security administrators can use the endpoint security policies and profiles to focus on security configuration of devices in microsoft intune. you can create the device profiles and policies you need in intune based on policies you currently have in. use the microsoft intune admin center to assign device configuration profiles. Microsoft Endpoint Manager Configuration Profile.
From incas-training.de
Microsoft Endpoint Configuration Manager (MECM/ECM) Microsoft Endpoint Manager Configuration Profile you can create the device profiles and policies you need in intune based on policies you currently have in. this session is part i of a series focused on configuration profiles in microsoft intune. Learn how to exclude groups from a. use the microsoft intune admin center to assign device configuration profiles and policies to users and. Microsoft Endpoint Manager Configuration Profile.
From vnextgroup.com
Get started with Endpoint Management Journey Modern Security Microsoft Endpoint Manager Configuration Profile Learn how to exclude groups from a. as part of the microsoft 365 license, your company is likely entitled to adopt microsoft endpoint manager, which brings together microsoft intune. with intune, you can use device configuration profiles to manage common endpoint protection security. you can create the device profiles and policies you need in intune based on. Microsoft Endpoint Manager Configuration Profile.
From www.techrepublic.com
How to create a configuration profile in Microsoft Endpoint Manager Microsoft Endpoint Manager Configuration Profile with intune, you can use device configuration profiles to manage common endpoint protection security. use the microsoft intune admin center to assign device configuration profiles and policies to users and devices. The focus of this session is to introduce. this session is part i of a series focused on configuration profiles in microsoft intune. you can. Microsoft Endpoint Manager Configuration Profile.
From emm-blog.com
What’s new in version 2107 of Microsoft Endpoint Configuration Manager Microsoft Endpoint Manager Configuration Profile Learn how to exclude groups from a. use the microsoft intune admin center to assign device configuration profiles and policies to users and devices. as part of the microsoft 365 license, your company is likely entitled to adopt microsoft endpoint manager, which brings together microsoft intune. The focus of this session is to introduce. with intune, you. Microsoft Endpoint Manager Configuration Profile.
From endusersupports.com
Walkthrough Intune in Microsoft Endpoint Manager (MEM Microsoft Endpoint Manager Configuration Profile Learn how to exclude groups from a. with intune, you can use device configuration profiles to manage common endpoint protection security. as part of the microsoft 365 license, your company is likely entitled to adopt microsoft endpoint manager, which brings together microsoft intune. The focus of this session is to introduce. security administrators can use the endpoint. Microsoft Endpoint Manager Configuration Profile.
From www.techrepublic.com
How to create a configuration profile in Microsoft Endpoint Manager Microsoft Endpoint Manager Configuration Profile The focus of this session is to introduce. this session is part i of a series focused on configuration profiles in microsoft intune. with intune, you can use device configuration profiles to manage common endpoint protection security. security administrators can use the endpoint security policies and profiles to focus on security configuration of devices in microsoft intune.. Microsoft Endpoint Manager Configuration Profile.
From docs.informatica.com
Using Microsoft Endpoint Configuration Manager to Deploy the Installer Microsoft Endpoint Manager Configuration Profile as part of the microsoft 365 license, your company is likely entitled to adopt microsoft endpoint manager, which brings together microsoft intune. you can create the device profiles and policies you need in intune based on policies you currently have in. security administrators can use the endpoint security policies and profiles to focus on security configuration of. Microsoft Endpoint Manager Configuration Profile.
From www.graphenecloud.co.uk
Microsoft Endpoint Manager Managed Endpoint Graphene Cloud Microsoft Endpoint Manager Configuration Profile this session is part i of a series focused on configuration profiles in microsoft intune. security administrators can use the endpoint security policies and profiles to focus on security configuration of devices in microsoft intune. use the microsoft intune admin center to assign device configuration profiles and policies to users and devices. The focus of this session. Microsoft Endpoint Manager Configuration Profile.
From www.vembu.com
Microsoft Endpoint Manager Admin Center An Overview Microsoft Endpoint Manager Configuration Profile use the microsoft intune admin center to assign device configuration profiles and policies to users and devices. with intune, you can use device configuration profiles to manage common endpoint protection security. you can create the device profiles and policies you need in intune based on policies you currently have in. security administrators can use the endpoint. Microsoft Endpoint Manager Configuration Profile.
From docs.microsoft.com
Onboarding using Microsoft Endpoint Configuration Manager Windows Microsoft Endpoint Manager Configuration Profile Learn how to exclude groups from a. use the microsoft intune admin center to assign device configuration profiles and policies to users and devices. with intune, you can use device configuration profiles to manage common endpoint protection security. The focus of this session is to introduce. this session is part i of a series focused on configuration. Microsoft Endpoint Manager Configuration Profile.
From learn.microsoft.com
Set up and configure Microsoft Defender for Endpoint Plan 1 Microsoft Microsoft Endpoint Manager Configuration Profile you can create the device profiles and policies you need in intune based on policies you currently have in. use the microsoft intune admin center to assign device configuration profiles and policies to users and devices. The focus of this session is to introduce. with intune, you can use device configuration profiles to manage common endpoint protection. Microsoft Endpoint Manager Configuration Profile.
From learn.microsoft.com
Set up and configure Microsoft Defender for Endpoint Plan 1 Microsoft Microsoft Endpoint Manager Configuration Profile The focus of this session is to introduce. you can create the device profiles and policies you need in intune based on policies you currently have in. with intune, you can use device configuration profiles to manage common endpoint protection security. Learn how to exclude groups from a. security administrators can use the endpoint security policies and. Microsoft Endpoint Manager Configuration Profile.
From sccm.jp
Microsoft Endpoint Configuration Manager とは? Microsoft Endpoint Manager Configuration Profile security administrators can use the endpoint security policies and profiles to focus on security configuration of devices in microsoft intune. use the microsoft intune admin center to assign device configuration profiles and policies to users and devices. The focus of this session is to introduce. as part of the microsoft 365 license, your company is likely entitled. Microsoft Endpoint Manager Configuration Profile.
From www.msnloop.com
Microsoft Endpoint Configuration Manager 2207 est disponible MSNLoop Microsoft Endpoint Manager Configuration Profile with intune, you can use device configuration profiles to manage common endpoint protection security. The focus of this session is to introduce. security administrators can use the endpoint security policies and profiles to focus on security configuration of devices in microsoft intune. as part of the microsoft 365 license, your company is likely entitled to adopt microsoft. Microsoft Endpoint Manager Configuration Profile.
From www.thecybersecuritytimes.com
Guide to Microsoft Endpoint Manager A hybrid to Configuration Manager Microsoft Endpoint Manager Configuration Profile with intune, you can use device configuration profiles to manage common endpoint protection security. security administrators can use the endpoint security policies and profiles to focus on security configuration of devices in microsoft intune. Learn how to exclude groups from a. this session is part i of a series focused on configuration profiles in microsoft intune. . Microsoft Endpoint Manager Configuration Profile.
From www.silviodibenedetto.com
Microsoft Endpoint Configuration Manager Archives Silvio Di Benedetto Microsoft Endpoint Manager Configuration Profile with intune, you can use device configuration profiles to manage common endpoint protection security. as part of the microsoft 365 license, your company is likely entitled to adopt microsoft endpoint manager, which brings together microsoft intune. The focus of this session is to introduce. use the microsoft intune admin center to assign device configuration profiles and policies. Microsoft Endpoint Manager Configuration Profile.
From www.schneider.im
What is Microsoft Endpoint Manager and What Changed (2024) Microsoft Endpoint Manager Configuration Profile security administrators can use the endpoint security policies and profiles to focus on security configuration of devices in microsoft intune. this session is part i of a series focused on configuration profiles in microsoft intune. Learn how to exclude groups from a. with intune, you can use device configuration profiles to manage common endpoint protection security. . Microsoft Endpoint Manager Configuration Profile.
From sccm.jp
Microsoft Endpoint Configuration Manager とは? Microsoft Endpoint Manager Configuration Profile you can create the device profiles and policies you need in intune based on policies you currently have in. The focus of this session is to introduce. security administrators can use the endpoint security policies and profiles to focus on security configuration of devices in microsoft intune. as part of the microsoft 365 license, your company is. Microsoft Endpoint Manager Configuration Profile.
From www.niallbrady.com
Microsoft Endpoint Manager Configuration Manager Technical Preview Microsoft Endpoint Manager Configuration Profile The focus of this session is to introduce. with intune, you can use device configuration profiles to manage common endpoint protection security. this session is part i of a series focused on configuration profiles in microsoft intune. use the microsoft intune admin center to assign device configuration profiles and policies to users and devices. Learn how to. Microsoft Endpoint Manager Configuration Profile.
From www.steeves.net
Microsoft Endpoint Management ConfigMgr & Intune Licenses Combined Microsoft Endpoint Manager Configuration Profile use the microsoft intune admin center to assign device configuration profiles and policies to users and devices. with intune, you can use device configuration profiles to manage common endpoint protection security. security administrators can use the endpoint security policies and profiles to focus on security configuration of devices in microsoft intune. you can create the device. Microsoft Endpoint Manager Configuration Profile.
From www.niallbrady.com
Microsoft Endpoint Manager Configuration Manager Technical Preview Microsoft Endpoint Manager Configuration Profile with intune, you can use device configuration profiles to manage common endpoint protection security. Learn how to exclude groups from a. this session is part i of a series focused on configuration profiles in microsoft intune. you can create the device profiles and policies you need in intune based on policies you currently have in. security. Microsoft Endpoint Manager Configuration Profile.
From softtailor.de
Microsoft Endpoint Configuration Manager MECM Microsoft Endpoint Manager Configuration Profile Learn how to exclude groups from a. security administrators can use the endpoint security policies and profiles to focus on security configuration of devices in microsoft intune. this session is part i of a series focused on configuration profiles in microsoft intune. The focus of this session is to introduce. you can create the device profiles and. Microsoft Endpoint Manager Configuration Profile.
From docs.microsoft.com
Onboarding using Microsoft Endpoint Configuration Manager Microsoft Docs Microsoft Endpoint Manager Configuration Profile use the microsoft intune admin center to assign device configuration profiles and policies to users and devices. security administrators can use the endpoint security policies and profiles to focus on security configuration of devices in microsoft intune. as part of the microsoft 365 license, your company is likely entitled to adopt microsoft endpoint manager, which brings together. Microsoft Endpoint Manager Configuration Profile.
From techcommunity.microsoft.com
Update 2010 for Microsoft Endpoint Configuration Manager current branch Microsoft Endpoint Manager Configuration Profile Learn how to exclude groups from a. you can create the device profiles and policies you need in intune based on policies you currently have in. with intune, you can use device configuration profiles to manage common endpoint protection security. The focus of this session is to introduce. use the microsoft intune admin center to assign device. Microsoft Endpoint Manager Configuration Profile.
From msendpointmgr.com
New Administrative Templates UI in Microsoft Endpoint Manager Microsoft Endpoint Manager Configuration Profile you can create the device profiles and policies you need in intune based on policies you currently have in. this session is part i of a series focused on configuration profiles in microsoft intune. with intune, you can use device configuration profiles to manage common endpoint protection security. security administrators can use the endpoint security policies. Microsoft Endpoint Manager Configuration Profile.
From docs.microsoft.com
Onboarding mithilfe des Microsoft Endpoint Configuration Manager Microsoft Endpoint Manager Configuration Profile with intune, you can use device configuration profiles to manage common endpoint protection security. Learn how to exclude groups from a. The focus of this session is to introduce. this session is part i of a series focused on configuration profiles in microsoft intune. security administrators can use the endpoint security policies and profiles to focus on. Microsoft Endpoint Manager Configuration Profile.
From techlabs.blog
Customize Windows 11 Start menu layout with JSON file and Endpoint Microsoft Endpoint Manager Configuration Profile Learn how to exclude groups from a. security administrators can use the endpoint security policies and profiles to focus on security configuration of devices in microsoft intune. you can create the device profiles and policies you need in intune based on policies you currently have in. The focus of this session is to introduce. this session is. Microsoft Endpoint Manager Configuration Profile.